Datree is a CLI tool that supports Kubernetes admins in their roles by preventing developers from making errors in Kubernetes configurations that can cause clusters to fail in production. Our CLI tool is open source, enabling it to be supported by the Kubernetes community.
It’s far more effective than manual processes, such as sending an email to a slew of developers, begging them to set various limits, which likely falls on deaf ears because developers are already overwhelmed.
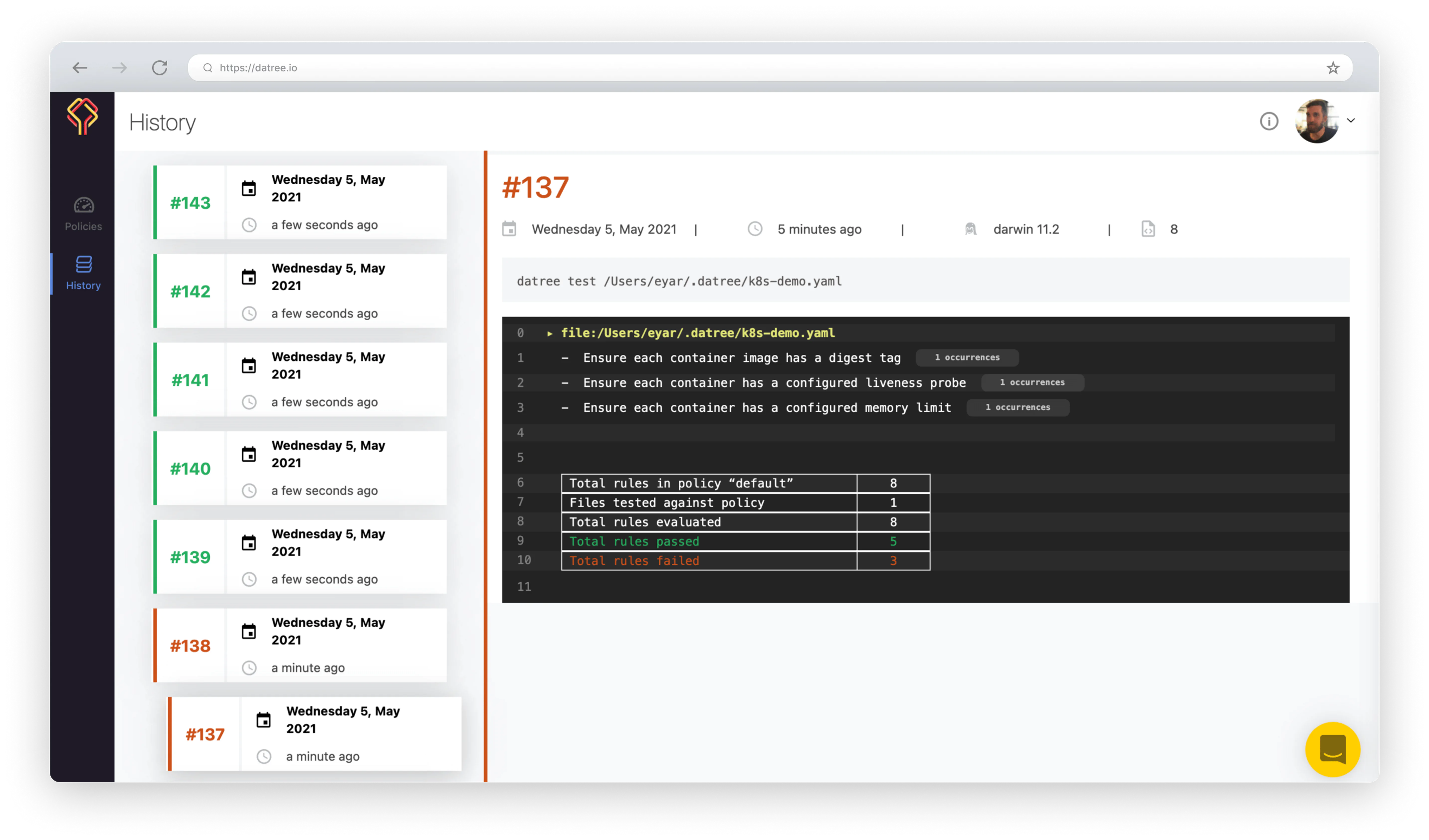
The CLI integration provides a policy enforcement solution for Kubernetes to run automatic checks on every code change for rule violations and misconfigurations. When rule violations are found, Datree produces an alert that guides the developer to fix the issue inside the CI process — or even earlier as a pre-commit hook — while explaining the reason behind the rule.
Linux & MacOS: curl https://get.datree.io | /bin/bash
Windows: iwr -useb https://get.datree.io/windows_install.ps1 | iex
Other installation options (Homebrew, Docker, etc.) can be found here
datree test [k8s-manifest-file]
...and voilà, you just ran your first invocation! 🥳

You can also checkout our interactive demo scenario on Katacoda without having to install anything on your machine.
Datree's Helm plugin can be accessed through the helm CLI, to provide a seamless experience to Helm users:
helm plugin install https://github.com/datreeio/helm-datree
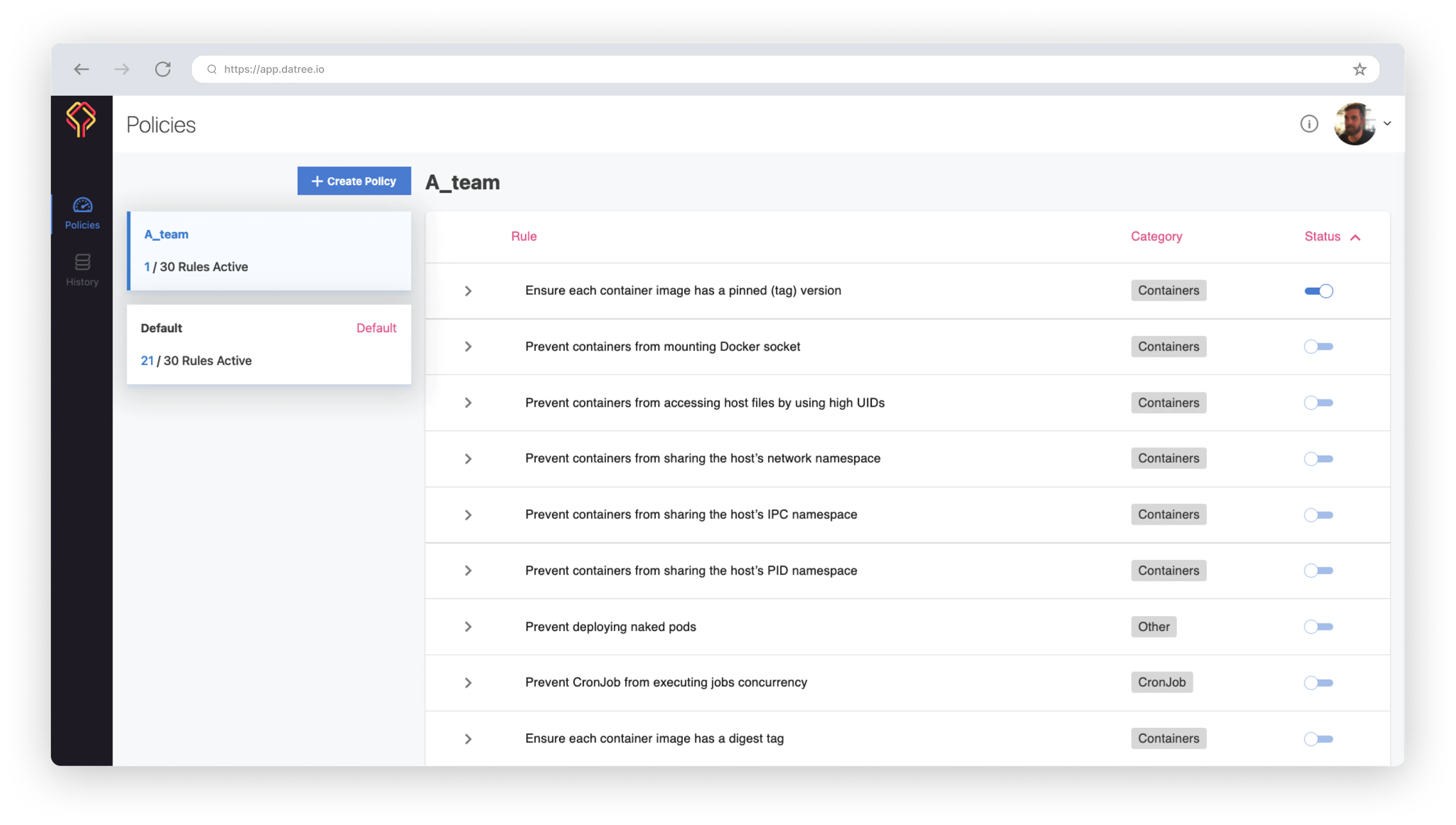
Every policy check will (also) validate your Kubernetes schema. In addition, there are 30 battle-tested rules for you to select to create your policy.
The policy rules cover a variety of Kubernetes resources and use cases:
- Workload
- CronJob
- Containers
- Networking
- Deprecation
- Others
In addition to our built-in rules, you can write any custom rule you wish, and then run them against your Kubernetes configurations to check for rule violations. The custom rule engine is based on JSON Schema.
Like any linter or static code analysis tool, Datree's command-line tool can be integrated with all CI/CD platforms to automatically scan every code change and provide feedback as part of the workflow. In the docs, you can find examples of some of the common CI/CD platforms.
If you run into any difficulties with CI/CD integrations, please join our community Slack channel or open an issue, and we'd be happy to guide you through it.
We do our best to maintain backward compatibility, but there may be breaking changes in the future to the command usage, flags, and configuration file formats. The CLI will output a warning message when a new version with breaking changes is detected. We encourage you to use Datree to test your Kubernetes manifests files and Helm charts, see what breaks, and contribute.