r=>{if(typeof r[e]=="undefined")return;let n=[r.location,e].join(":");return t.set(n,lunr.tokenizer.table=[]),r[e]}}function Re(t,e){let[r,n]=[new Set(t),new Set(e)];return[...new Set([...r].filter(i=>!n.has(i)))]}var U=class{constructor({config:e,docs:r,options:n}){let i=Oe(this.table=new Map);this.map=ie(r),this.options=n,this.index=lunr(function(){this.metadataWhitelist=["position"],this.b(0),e.lang.length===1&&e.lang[0]!=="en"?this.use(lunr[e.lang[0]]):e.lang.length>1&&this.use(lunr.multiLanguage(...e.lang)),this.tokenizer=ae,lunr.tokenizer.separator=new RegExp(e.separator),lunr.segmenter="TinySegmenter"in lunr?new lunr.TinySegmenter:void 0;let s=Re(["trimmer","stopWordFilter","stemmer"],e.pipeline);for(let o of e.lang.map(a=>a==="en"?lunr:lunr[a]))for(let a of s)this.pipeline.remove(o[a]),this.searchPipeline.remove(o[a]);this.ref("location");for(let[o,a]of Object.entries(e.fields))this.field(o,B(_({},a),{extractor:i(o)}));for(let o of r)this.add(o,{boost:o.boost})})}search(e){if(e=e.replace(new RegExp("\\p{sc=Han}+","gu"),s=>[...fe(s,this.index.invertedIndex)].join("* ")),e=ce(e),!e)return{items:[]};let r=le(e).filter(s=>s.presence!==lunr.Query.presence.PROHIBITED),n=this.index.search(e).reduce((s,{ref:o,score:a,matchData:u})=>{let c=this.map.get(o);if(typeof c!="undefined"){c=_({},c),c.tags&&(c.tags=[...c.tags]);let f=he(r,Object.keys(u.metadata));for(let l of this.index.fields){if(typeof c[l]=="undefined")continue;let m=[];for(let d of Object.values(u.metadata))typeof d[l]!="undefined"&&m.push(...d[l].position);if(!m.length)continue;let x=this.table.get([c.location,l].join(":")),v=Array.isArray(c[l])?q:oe;c[l]=v(c[l],x,m,l!=="text")}let g=+!c.parent+Object.values(f).filter(l=>l).length/Object.keys(f).length;s.push(B(_({},c),{score:a*(1+K(g,2)),terms:f}))}return s},[]).sort((s,o)=>o.score-s.score).reduce((s,o)=>{let a=this.map.get(o.location);if(typeof a!="undefined"){let u=a.parent?a.parent.location:a.location;s.set(u,[...s.get(u)||[],o])}return s},new Map);for(let[s,o]of n)if(!o.find(a=>a.location===s)){let a=this.map.get(s);o.push(B(_({},a),{score:0,terms:{}}))}let i;if(this.options.suggest){let s=this.index.query(o=>{for(let a of r)o.term(a.term,{fields:["title"],presence:lunr.Query.presence.REQUIRED,wildcard:lunr.Query.wildcard.TRAILING})});i=s.length?Object.keys(s[0].matchData.metadata):[]}return _({items:[...n.values()]},typeof i!="undefined"&&{suggest:i})}};var de;function Ie(t){return W(this,null,function*(){let e="../lunr";if(typeof parent!="undefined"&&"IFrameWorker"in parent){let n=ne("script[src]"),[i]=n.src.split("/worker");e=e.replace("..",i)}let r=[];for(let n of t.lang){switch(n){case"ja":r.push(`${e}/tinyseg.js`);break;case"hi":case"th":r.push(`${e}/wordcut.js`);break}n!=="en"&&r.push(`${e}/min/lunr.${n}.min.js`)}t.lang.length>1&&r.push(`${e}/min/lunr.multi.min.js`),r.length&&(yield importScripts(`${e}/min/lunr.stemmer.support.min.js`,...r))})}function Fe(t){return W(this,null,function*(){switch(t.type){case 0:return yield Ie(t.data.config),de=new U(t.data),{type:1};case 2:let e=t.data;try{return{type:3,data:de.search(e)}}catch(r){return console.warn(`Invalid query: ${e} \u2013 see https://bit.ly/2s3ChXG`),console.warn(r),{type:3,data:{items:[]}}}default:throw new TypeError("Invalid message type")}})}self.lunr=Y.default;Y.default.utils.warn=console.warn;addEventListener("message",t=>W(void 0,null,function*(){postMessage(yield Fe(t.data))}));})();
diff --git a/assets/project-icon.png b/assets/project-icon.png
new file mode 100644
index 00000000..297cba2b
Binary files /dev/null and b/assets/project-icon.png differ
diff --git a/assets/project-logo.png b/assets/project-logo.png
new file mode 100644
index 00000000..56bb7ed3
Binary files /dev/null and b/assets/project-logo.png differ
diff --git a/assets/projects/credo/credo-high-level-arch.png b/assets/projects/credo/credo-high-level-arch.png
new file mode 100644
index 00000000..3c222132
Binary files /dev/null and b/assets/projects/credo/credo-high-level-arch.png differ
diff --git a/assets/projects/fwos/Emergency_Relief_Event.png b/assets/projects/fwos/Emergency_Relief_Event.png
new file mode 100644
index 00000000..0a2f74a5
Binary files /dev/null and b/assets/projects/fwos/Emergency_Relief_Event.png differ
diff --git a/assets/projects/fwos/Farmworker_WalletOS_OSS_Project.png b/assets/projects/fwos/Farmworker_WalletOS_OSS_Project.png
new file mode 100644
index 00000000..af6db33c
Binary files /dev/null and b/assets/projects/fwos/Farmworker_WalletOS_OSS_Project.png differ
diff --git a/assets/stylesheets/main.12320a83.min.css b/assets/stylesheets/main.12320a83.min.css
new file mode 100644
index 00000000..b33c6902
--- /dev/null
+++ b/assets/stylesheets/main.12320a83.min.css
@@ -0,0 +1 @@
+@charset "UTF-8";html{-webkit-text-size-adjust:none;-moz-text-size-adjust:none;text-size-adjust:none;box-sizing:border-box}*,:after,:before{box-sizing:inherit}@media (prefers-reduced-motion){*,:after,:before{transition:none!important}}body{margin:0}a,button,input,label{-webkit-tap-highlight-color:transparent}a{color:inherit;text-decoration:none}hr{border:0;box-sizing:initial;display:block;height:.05rem;overflow:visible;padding:0}small{font-size:80%}sub,sup{line-height:1em}img{border-style:none}table{border-collapse:initial;border-spacing:0}td,th{font-weight:400;vertical-align:top}button{background:#0000;border:0;font-family:inherit;font-size:inherit;margin:0;padding:0}input{border:0;outline:none}:root{--md-primary-fg-color:#4051b5;--md-primary-fg-color--light:#5d6cc0;--md-primary-fg-color--dark:#303fa1;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3;--md-accent-fg-color:#526cfe;--md-accent-fg-color--transparent:#526cfe1a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-scheme=default]{color-scheme:light}[data-md-color-scheme=default] img[src$="#gh-dark-mode-only"],[data-md-color-scheme=default] img[src$="#only-dark"]{display:none}:root,[data-md-color-scheme=default]{--md-hue:225deg;--md-default-fg-color:#000000de;--md-default-fg-color--light:#0000008a;--md-default-fg-color--lighter:#00000052;--md-default-fg-color--lightest:#00000012;--md-default-bg-color:#fff;--md-default-bg-color--light:#ffffffb3;--md-default-bg-color--lighter:#ffffff4d;--md-default-bg-color--lightest:#ffffff1f;--md-code-fg-color:#36464e;--md-code-bg-color:#f5f5f5;--md-code-bg-color--light:#f5f5f5b3;--md-code-bg-color--lighter:#f5f5f54d;--md-code-hl-color:#4287ff;--md-code-hl-color--light:#4287ff1a;--md-code-hl-number-color:#d52a2a;--md-code-hl-special-color:#db1457;--md-code-hl-function-color:#a846b9;--md-code-hl-constant-color:#6e59d9;--md-code-hl-keyword-color:#3f6ec6;--md-code-hl-string-color:#1c7d4d;--md-code-hl-name-color:var(--md-code-fg-color);--md-code-hl-operator-color:var(--md-default-fg-color--light);--md-code-hl-punctuation-color:var(--md-default-fg-color--light);--md-code-hl-comment-color:var(--md-default-fg-color--light);--md-code-hl-generic-color:var(--md-default-fg-color--light);--md-code-hl-variable-color:var(--md-default-fg-color--light);--md-typeset-color:var(--md-default-fg-color);--md-typeset-a-color:var(--md-primary-fg-color);--md-typeset-del-color:#f5503d26;--md-typeset-ins-color:#0bd57026;--md-typeset-kbd-color:#fafafa;--md-typeset-kbd-accent-color:#fff;--md-typeset-kbd-border-color:#b8b8b8;--md-typeset-mark-color:#ffff0080;--md-typeset-table-color:#0000001f;--md-typeset-table-color--light:rgba(0,0,0,.035);--md-admonition-fg-color:var(--md-default-fg-color);--md-admonition-bg-color:var(--md-default-bg-color);--md-warning-fg-color:#000000de;--md-warning-bg-color:#ff9;--md-footer-fg-color:#fff;--md-footer-fg-color--light:#ffffffb3;--md-footer-fg-color--lighter:#ffffff73;--md-footer-bg-color:#000000de;--md-footer-bg-color--dark:#00000052;--md-shadow-z1:0 0.2rem 0.5rem #0000000d,0 0 0.05rem #0000001a;--md-shadow-z2:0 0.2rem 0.5rem #0000001a,0 0 0.05rem #00000040;--md-shadow-z3:0 0.2rem 0.5rem #0003,0 0 0.05rem #00000059}.md-icon svg{fill:currentcolor;display:block;height:1.2rem;width:1.2rem}body{-webkit-font-smoothing:antialiased;-moz-osx-font-smoothing:grayscale;--md-text-font-family:var(--md-text-font,_),-apple-system,BlinkMacSystemFont,Helvetica,Arial,sans-serif;--md-code-font-family:var(--md-code-font,_),SFMono-Regular,Consolas,Menlo,monospace}aside,body,input{font-feature-settings:"kern","liga";color:var(--md-typeset-color);font-family:var(--md-text-font-family)}code,kbd,pre{font-feature-settings:"kern";font-family:var(--md-code-font-family)}:root{--md-typeset-table-sort-icon:url('data:image/svg+xml;charset=utf-8,');--md-typeset-table-sort-icon--asc:url('data:image/svg+xml;charset=utf-8,');--md-typeset-table-sort-icon--desc:url('data:image/svg+xml;charset=utf-8,')}.md-typeset{-webkit-print-color-adjust:exact;color-adjust:exact;font-size:.8rem;line-height:1.6}@media print{.md-typeset{font-size:.68rem}}.md-typeset blockquote,.md-typeset dl,.md-typeset figure,.md-typeset ol,.md-typeset pre,.md-typeset ul{margin-bottom:1em;margin-top:1em}.md-typeset h1{color:var(--md-default-fg-color--light);font-size:2em;line-height:1.3;margin:0 0 1.25em}.md-typeset h1,.md-typeset h2{font-weight:300;letter-spacing:-.01em}.md-typeset h2{font-size:1.5625em;line-height:1.4;margin:1.6em 0 .64em}.md-typeset h3{font-size:1.25em;font-weight:400;letter-spacing:-.01em;line-height:1.5;margin:1.6em 0 .8em}.md-typeset h2+h3{margin-top:.8em}.md-typeset h4{font-weight:700;letter-spacing:-.01em;margin:1em 0}.md-typeset h5,.md-typeset h6{color:var(--md-default-fg-color--light);font-size:.8em;font-weight:700;letter-spacing:-.01em;margin:1.25em 0}.md-typeset h5{text-transform:uppercase}.md-typeset hr{border-bottom:.05rem solid var(--md-default-fg-color--lightest);display:flow-root;margin:1.5em 0}.md-typeset a{color:var(--md-typeset-a-color);word-break:break-word}.md-typeset a,.md-typeset a:before{transition:color 125ms}.md-typeset a:focus,.md-typeset a:hover{color:var(--md-accent-fg-color)}.md-typeset a:focus code,.md-typeset a:hover code{background-color:var(--md-accent-fg-color--transparent);color:var(--md-accent-fg-color)}.md-typeset a code{color:var(--md-typeset-a-color)}.md-typeset a.focus-visible{outline-color:var(--md-accent-fg-color);outline-offset:.2rem}.md-typeset code,.md-typeset kbd,.md-typeset pre{color:var(--md-code-fg-color);direction:ltr;font-variant-ligatures:none;transition:background-color 125ms}@media print{.md-typeset code,.md-typeset kbd,.md-typeset pre{white-space:pre-wrap}}.md-typeset code{background-color:var(--md-code-bg-color);border-radius:.1rem;-webkit-box-decoration-break:clone;box-decoration-break:clone;font-size:.85em;padding:0 .2941176471em;transition:color 125ms,background-color 125ms;word-break:break-word}.md-typeset code:not(.focus-visible){-webkit-tap-highlight-color:transparent;outline:none}.md-typeset pre{display:flow-root;line-height:1.4;position:relative}.md-typeset pre>code{-webkit-box-decoration-break:slice;box-decoration-break:slice;box-shadow:none;display:block;margin:0;outline-color:var(--md-accent-fg-color);overflow:auto;padding:.7720588235em 1.1764705882em;scrollbar-color:var(--md-default-fg-color--lighter) #0000;scrollbar-width:thin;touch-action:auto;word-break:normal}.md-typeset pre>code:hover{scrollbar-color:var(--md-accent-fg-color) #0000}.md-typeset pre>code::-webkit-scrollbar{height:.2rem;width:.2rem}.md-typeset pre>code::-webkit-scrollbar-thumb{background-color:var(--md-default-fg-color--lighter)}.md-typeset pre>code::-webkit-scrollbar-thumb:hover{background-color:var(--md-accent-fg-color)}.md-typeset kbd{background-color:var(--md-typeset-kbd-color);border-radius:.1rem;box-shadow:0 .1rem 0 .05rem var(--md-typeset-kbd-border-color),0 .1rem 0 var(--md-typeset-kbd-border-color),0 -.1rem .2rem var(--md-typeset-kbd-accent-color) inset;color:var(--md-default-fg-color);display:inline-block;font-size:.75em;padding:0 .6666666667em;vertical-align:text-top;word-break:break-word}.md-typeset mark{background-color:var(--md-typeset-mark-color);-webkit-box-decoration-break:clone;box-decoration-break:clone;color:inherit;word-break:break-word}.md-typeset abbr{cursor:help;text-decoration:none}.md-typeset [data-preview],.md-typeset abbr{border-bottom:.05rem dotted var(--md-default-fg-color--light)}.md-typeset small{opacity:.75}[dir=ltr] .md-typeset sub,[dir=ltr] .md-typeset sup{margin-left:.078125em}[dir=rtl] .md-typeset sub,[dir=rtl] .md-typeset sup{margin-right:.078125em}[dir=ltr] .md-typeset blockquote{padding-left:.6rem}[dir=rtl] .md-typeset blockquote{padding-right:.6rem}[dir=ltr] .md-typeset blockquote{border-left:.2rem solid var(--md-default-fg-color--lighter)}[dir=rtl] .md-typeset blockquote{border-right:.2rem solid var(--md-default-fg-color--lighter)}.md-typeset blockquote{color:var(--md-default-fg-color--light);margin-left:0;margin-right:0}.md-typeset ul{list-style-type:disc}.md-typeset ul[type]{list-style-type:revert-layer}[dir=ltr] .md-typeset ol,[dir=ltr] .md-typeset ul{margin-left:.625em}[dir=rtl] .md-typeset ol,[dir=rtl] .md-typeset ul{margin-right:.625em}.md-typeset ol,.md-typeset ul{padding:0}.md-typeset ol:not([hidden]),.md-typeset ul:not([hidden]){display:flow-root}.md-typeset ol ol,.md-typeset ul ol{list-style-type:lower-alpha}.md-typeset ol ol ol,.md-typeset ul ol ol{list-style-type:lower-roman}.md-typeset ol ol ol ol,.md-typeset ul ol ol ol{list-style-type:upper-alpha}.md-typeset ol ol ol ol ol,.md-typeset ul ol ol ol ol{list-style-type:upper-roman}.md-typeset ol[type],.md-typeset ul[type]{list-style-type:revert-layer}[dir=ltr] .md-typeset ol li,[dir=ltr] .md-typeset ul li{margin-left:1.25em}[dir=rtl] .md-typeset ol li,[dir=rtl] .md-typeset ul li{margin-right:1.25em}.md-typeset ol li,.md-typeset ul li{margin-bottom:.5em}.md-typeset ol li blockquote,.md-typeset ol li p,.md-typeset ul li blockquote,.md-typeset ul li p{margin:.5em 0}.md-typeset ol li:last-child,.md-typeset ul li:last-child{margin-bottom:0}[dir=ltr] .md-typeset ol li ol,[dir=ltr] .md-typeset ol li ul,[dir=ltr] .md-typeset ul li ol,[dir=ltr] .md-typeset ul li ul{margin-left:.625em}[dir=rtl] .md-typeset ol li ol,[dir=rtl] .md-typeset ol li ul,[dir=rtl] .md-typeset ul li ol,[dir=rtl] .md-typeset ul li ul{margin-right:.625em}.md-typeset ol li ol,.md-typeset ol li ul,.md-typeset ul li ol,.md-typeset ul li ul{margin-bottom:.5em;margin-top:.5em}[dir=ltr] .md-typeset dd{margin-left:1.875em}[dir=rtl] .md-typeset dd{margin-right:1.875em}.md-typeset dd{margin-bottom:1.5em;margin-top:1em}.md-typeset img,.md-typeset svg,.md-typeset video{height:auto;max-width:100%}.md-typeset img[align=left]{margin:1em 1em 1em 0}.md-typeset img[align=right]{margin:1em 0 1em 1em}.md-typeset img[align]:only-child{margin-top:0}.md-typeset figure{display:flow-root;margin:1em auto;max-width:100%;text-align:center;width:-moz-fit-content;width:fit-content}.md-typeset figure img{display:block;margin:0 auto}.md-typeset figcaption{font-style:italic;margin:1em auto;max-width:24rem}.md-typeset iframe{max-width:100%}.md-typeset table:not([class]){background-color:var(--md-default-bg-color);border:.05rem solid var(--md-typeset-table-color);border-radius:.1rem;display:inline-block;font-size:.64rem;max-width:100%;overflow:auto;touch-action:auto}@media print{.md-typeset table:not([class]){display:table}}.md-typeset table:not([class])+*{margin-top:1.5em}.md-typeset table:not([class]) td>:first-child,.md-typeset table:not([class]) th>:first-child{margin-top:0}.md-typeset table:not([class]) td>:last-child,.md-typeset table:not([class]) th>:last-child{margin-bottom:0}.md-typeset table:not([class]) td:not([align]),.md-typeset table:not([class]) th:not([align]){text-align:left}[dir=rtl] .md-typeset table:not([class]) td:not([align]),[dir=rtl] .md-typeset table:not([class]) th:not([align]){text-align:right}.md-typeset table:not([class]) th{font-weight:700;min-width:5rem;padding:.9375em 1.25em;vertical-align:top}.md-typeset table:not([class]) td{border-top:.05rem solid var(--md-typeset-table-color);padding:.9375em 1.25em;vertical-align:top}.md-typeset table:not([class]) tbody tr{transition:background-color 125ms}.md-typeset table:not([class]) tbody tr:hover{background-color:var(--md-typeset-table-color--light);box-shadow:0 .05rem 0 var(--md-default-bg-color) inset}.md-typeset table:not([class]) a{word-break:normal}.md-typeset table th[role=columnheader]{cursor:pointer}[dir=ltr] .md-typeset table th[role=columnheader]:after{margin-left:.5em}[dir=rtl] .md-typeset table th[role=columnheader]:after{margin-right:.5em}.md-typeset table th[role=columnheader]:after{content:"";display:inline-block;height:1.2em;-webkit-mask-image:var(--md-typeset-table-sort-icon);mask-image:var(--md-typeset-table-sort-icon);-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;transition:background-color 125ms;vertical-align:text-bottom;width:1.2em}.md-typeset table th[role=columnheader]:hover:after{background-color:var(--md-default-fg-color--lighter)}.md-typeset table th[role=columnheader][aria-sort=ascending]:after{background-color:var(--md-default-fg-color--light);-webkit-mask-image:var(--md-typeset-table-sort-icon--asc);mask-image:var(--md-typeset-table-sort-icon--asc)}.md-typeset table th[role=columnheader][aria-sort=descending]:after{background-color:var(--md-default-fg-color--light);-webkit-mask-image:var(--md-typeset-table-sort-icon--desc);mask-image:var(--md-typeset-table-sort-icon--desc)}.md-typeset__scrollwrap{margin:1em -.8rem;overflow-x:auto;touch-action:auto}.md-typeset__table{display:inline-block;margin-bottom:.5em;padding:0 .8rem}@media print{.md-typeset__table{display:block}}html .md-typeset__table table{display:table;margin:0;overflow:hidden;width:100%}@media screen and (max-width:44.984375em){.md-content__inner>pre{margin:1em -.8rem}.md-content__inner>pre code{border-radius:0}}.md-typeset .md-author{border-radius:100%;display:block;flex-shrink:0;height:1.6rem;overflow:hidden;position:relative;transition:color 125ms,transform 125ms;width:1.6rem}.md-typeset .md-author img{display:block}.md-typeset .md-author--more{background:var(--md-default-fg-color--lightest);color:var(--md-default-fg-color--lighter);font-size:.6rem;font-weight:700;line-height:1.6rem;text-align:center}.md-typeset .md-author--long{height:2.4rem;width:2.4rem}.md-typeset a.md-author{transform:scale(1)}.md-typeset a.md-author img{border-radius:100%;filter:grayscale(100%) opacity(75%);transition:filter 125ms}.md-typeset a.md-author:focus,.md-typeset a.md-author:hover{transform:scale(1.1);z-index:1}.md-typeset a.md-author:focus img,.md-typeset a.md-author:hover img{filter:grayscale(0)}.md-banner{background-color:var(--md-footer-bg-color);color:var(--md-footer-fg-color);overflow:auto}@media print{.md-banner{display:none}}.md-banner--warning{background-color:var(--md-warning-bg-color);color:var(--md-warning-fg-color)}.md-banner__inner{font-size:.7rem;margin:.6rem auto;padding:0 .8rem}[dir=ltr] .md-banner__button{float:right}[dir=rtl] .md-banner__button{float:left}.md-banner__button{color:inherit;cursor:pointer;transition:opacity .25s}.no-js .md-banner__button{display:none}.md-banner__button:hover{opacity:.7}html{font-size:125%;height:100%;overflow-x:hidden}@media screen and (min-width:100em){html{font-size:137.5%}}@media screen and (min-width:125em){html{font-size:150%}}body{background-color:var(--md-default-bg-color);display:flex;flex-direction:column;font-size:.5rem;min-height:100%;position:relative;width:100%}@media print{body{display:block}}@media screen and (max-width:59.984375em){body[data-md-scrolllock]{position:fixed}}.md-grid{margin-left:auto;margin-right:auto;max-width:61rem}.md-container{display:flex;flex-direction:column;flex-grow:1}@media print{.md-container{display:block}}.md-main{flex-grow:1}.md-main__inner{display:flex;height:100%;margin-top:1.5rem}.md-ellipsis{overflow:hidden;text-overflow:ellipsis}.md-toggle{display:none}.md-option{height:0;opacity:0;position:absolute;width:0}.md-option:checked+label:not([hidden]){display:block}.md-option.focus-visible+label{outline-color:var(--md-accent-fg-color);outline-style:auto}.md-skip{background-color:var(--md-default-fg-color);border-radius:.1rem;color:var(--md-default-bg-color);font-size:.64rem;margin:.5rem;opacity:0;outline-color:var(--md-accent-fg-color);padding:.3rem .5rem;position:fixed;transform:translateY(.4rem);z-index:-1}.md-skip:focus{opacity:1;transform:translateY(0);transition:transform .25s cubic-bezier(.4,0,.2,1),opacity 175ms 75ms;z-index:10}@page{margin:25mm}:root{--md-clipboard-icon:url('data:image/svg+xml;charset=utf-8,')}.md-clipboard{border-radius:.1rem;color:var(--md-default-fg-color--lightest);cursor:pointer;height:1.5em;outline-color:var(--md-accent-fg-color);outline-offset:.1rem;transition:color .25s;width:1.5em;z-index:1}@media print{.md-clipboard{display:none}}.md-clipboard:not(.focus-visible){-webkit-tap-highlight-color:transparent;outline:none}:hover>.md-clipboard{color:var(--md-default-fg-color--light)}.md-clipboard:focus,.md-clipboard:hover{color:var(--md-accent-fg-color)}.md-clipboard:after{background-color:currentcolor;content:"";display:block;height:1.125em;margin:0 auto;-webkit-mask-image:var(--md-clipboard-icon);mask-image:var(--md-clipboard-icon);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;width:1.125em}.md-clipboard--inline{cursor:pointer}.md-clipboard--inline code{transition:color .25s,background-color .25s}.md-clipboard--inline:focus code,.md-clipboard--inline:hover code{background-color:var(--md-accent-fg-color--transparent);color:var(--md-accent-fg-color)}:root{--md-code-select-icon:url('data:image/svg+xml;charset=utf-8,');--md-code-copy-icon:url('data:image/svg+xml;charset=utf-8,')}.md-typeset .md-code__content{display:grid}.md-code__nav{background-color:var(--md-code-bg-color--lighter);border-radius:.1rem;display:flex;gap:.2rem;padding:.2rem;position:absolute;right:.25em;top:.25em;transition:background-color .25s;z-index:1}:hover>.md-code__nav{background-color:var(--md-code-bg-color--light)}.md-code__button{color:var(--md-default-fg-color--lightest);cursor:pointer;display:block;height:1.5em;outline-color:var(--md-accent-fg-color);outline-offset:.1rem;transition:color .25s;width:1.5em}:hover>*>.md-code__button{color:var(--md-default-fg-color--light)}.md-code__button.focus-visible,.md-code__button:hover{color:var(--md-accent-fg-color)}.md-code__button--active{color:var(--md-default-fg-color)!important}.md-code__button:after{background-color:currentcolor;content:"";display:block;height:1.125em;margin:0 auto;-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;width:1.125em}.md-code__button[data-md-type=select]:after{-webkit-mask-image:var(--md-code-select-icon);mask-image:var(--md-code-select-icon)}.md-code__button[data-md-type=copy]:after{-webkit-mask-image:var(--md-code-copy-icon);mask-image:var(--md-code-copy-icon)}@keyframes consent{0%{opacity:0;transform:translateY(100%)}to{opacity:1;transform:translateY(0)}}@keyframes overlay{0%{opacity:0}to{opacity:1}}.md-consent__overlay{animation:overlay .25s both;-webkit-backdrop-filter:blur(.1rem);backdrop-filter:blur(.1rem);background-color:#0000008a;height:100%;opacity:1;position:fixed;top:0;width:100%;z-index:5}.md-consent__inner{animation:consent .5s cubic-bezier(.1,.7,.1,1) both;background-color:var(--md-default-bg-color);border:0;border-radius:.1rem;bottom:0;box-shadow:0 0 .2rem #0000001a,0 .2rem .4rem #0003;max-height:100%;overflow:auto;padding:0;position:fixed;width:100%;z-index:5}.md-consent__form{padding:.8rem}.md-consent__settings{display:none;margin:1em 0}input:checked+.md-consent__settings{display:block}.md-consent__controls{margin-bottom:.8rem}.md-typeset .md-consent__controls .md-button{display:inline}@media screen and (max-width:44.984375em){.md-typeset .md-consent__controls .md-button{display:block;margin-top:.4rem;text-align:center;width:100%}}.md-consent label{cursor:pointer}.md-content{flex-grow:1;min-width:0}.md-content__inner{margin:0 .8rem 1.2rem;padding-top:.6rem}@media screen and (min-width:76.25em){[dir=ltr] .md-sidebar--primary:not([hidden])~.md-content>.md-content__inner{margin-left:1.2rem}[dir=ltr] .md-sidebar--secondary:not([hidden])~.md-content>.md-content__inner,[dir=rtl] .md-sidebar--primary:not([hidden])~.md-content>.md-content__inner{margin-right:1.2rem}[dir=rtl] .md-sidebar--secondary:not([hidden])~.md-content>.md-content__inner{margin-left:1.2rem}}.md-content__inner:before{content:"";display:block;height:.4rem}.md-content__inner>:last-child{margin-bottom:0}[dir=ltr] .md-content__button{float:right}[dir=rtl] .md-content__button{float:left}[dir=ltr] .md-content__button{margin-left:.4rem}[dir=rtl] .md-content__button{margin-right:.4rem}.md-content__button{margin:.4rem 0;padding:0}@media print{.md-content__button{display:none}}.md-typeset .md-content__button{color:var(--md-default-fg-color--lighter)}.md-content__button svg{display:inline;vertical-align:top}[dir=rtl] .md-content__button svg{transform:scaleX(-1)}[dir=ltr] .md-dialog{right:.8rem}[dir=rtl] .md-dialog{left:.8rem}.md-dialog{background-color:var(--md-default-fg-color);border-radius:.1rem;bottom:.8rem;box-shadow:var(--md-shadow-z3);min-width:11.1rem;opacity:0;padding:.4rem .6rem;pointer-events:none;position:fixed;transform:translateY(100%);transition:transform 0ms .4s,opacity .4s;z-index:4}@media print{.md-dialog{display:none}}.md-dialog--active{opacity:1;pointer-events:auto;transform:translateY(0);transition:transform .4s cubic-bezier(.075,.85,.175,1),opacity .4s}.md-dialog__inner{color:var(--md-default-bg-color);font-size:.7rem}.md-feedback{margin:2em 0 1em;text-align:center}.md-feedback fieldset{border:none;margin:0;padding:0}.md-feedback__title{font-weight:700;margin:1em auto}.md-feedback__inner{position:relative}.md-feedback__list{display:flex;flex-wrap:wrap;place-content:baseline center;position:relative}.md-feedback__list:hover .md-icon:not(:disabled){color:var(--md-default-fg-color--lighter)}:disabled .md-feedback__list{min-height:1.8rem}.md-feedback__icon{color:var(--md-default-fg-color--light);cursor:pointer;flex-shrink:0;margin:0 .1rem;transition:color 125ms}.md-feedback__icon:not(:disabled).md-icon:hover{color:var(--md-accent-fg-color)}.md-feedback__icon:disabled{color:var(--md-default-fg-color--lightest);pointer-events:none}.md-feedback__note{opacity:0;position:relative;transform:translateY(.4rem);transition:transform .4s cubic-bezier(.1,.7,.1,1),opacity .15s}.md-feedback__note>*{margin:0 auto;max-width:16rem}:disabled .md-feedback__note{opacity:1;transform:translateY(0)}@media print{.md-feedback{display:none}}.md-footer{background-color:var(--md-footer-bg-color);color:var(--md-footer-fg-color)}@media print{.md-footer{display:none}}.md-footer__inner{justify-content:space-between;overflow:auto;padding:.2rem}.md-footer__inner:not([hidden]){display:flex}.md-footer__link{align-items:end;display:flex;flex-grow:0.01;margin-bottom:.4rem;margin-top:1rem;max-width:100%;outline-color:var(--md-accent-fg-color);overflow:hidden;transition:opacity .25s}.md-footer__link:focus,.md-footer__link:hover{opacity:.7}[dir=rtl] .md-footer__link svg{transform:scaleX(-1)}@media screen and (max-width:44.984375em){.md-footer__link--prev{flex-shrink:0}.md-footer__link--prev .md-footer__title{display:none}}[dir=ltr] .md-footer__link--next{margin-left:auto}[dir=rtl] .md-footer__link--next{margin-right:auto}.md-footer__link--next{text-align:right}[dir=rtl] .md-footer__link--next{text-align:left}.md-footer__title{flex-grow:1;font-size:.9rem;margin-bottom:.7rem;max-width:calc(100% - 2.4rem);padding:0 1rem;white-space:nowrap}.md-footer__button{margin:.2rem;padding:.4rem}.md-footer__direction{font-size:.64rem;opacity:.7}.md-footer-meta{background-color:var(--md-footer-bg-color--dark)}.md-footer-meta__inner{display:flex;flex-wrap:wrap;justify-content:space-between;padding:.2rem}html .md-footer-meta.md-typeset a{color:var(--md-footer-fg-color--light)}html .md-footer-meta.md-typeset a:focus,html .md-footer-meta.md-typeset a:hover{color:var(--md-footer-fg-color)}.md-copyright{color:var(--md-footer-fg-color--lighter);font-size:.64rem;margin:auto .6rem;padding:.4rem 0;width:100%}@media screen and (min-width:45em){.md-copyright{width:auto}}.md-copyright__highlight{color:var(--md-footer-fg-color--light)}.md-social{display:inline-flex;gap:.2rem;margin:0 .4rem;padding:.2rem 0 .6rem}@media screen and (min-width:45em){.md-social{padding:.6rem 0}}.md-social__link{display:inline-block;height:1.6rem;text-align:center;width:1.6rem}.md-social__link:before{line-height:1.9}.md-social__link svg{fill:currentcolor;max-height:.8rem;vertical-align:-25%}.md-typeset .md-button{border:.1rem solid;border-radius:.1rem;color:var(--md-primary-fg-color);cursor:pointer;display:inline-block;font-weight:700;padding:.625em 2em;transition:color 125ms,background-color 125ms,border-color 125ms}.md-typeset .md-button--primary{background-color:var(--md-primary-fg-color);border-color:var(--md-primary-fg-color);color:var(--md-primary-bg-color)}.md-typeset .md-button:focus,.md-typeset .md-button:hover{background-color:var(--md-accent-fg-color);border-color:var(--md-accent-fg-color);color:var(--md-accent-bg-color)}[dir=ltr] .md-typeset .md-input{border-top-left-radius:.1rem}[dir=ltr] .md-typeset .md-input,[dir=rtl] .md-typeset .md-input{border-top-right-radius:.1rem}[dir=rtl] .md-typeset .md-input{border-top-left-radius:.1rem}.md-typeset .md-input{border-bottom:.1rem solid var(--md-default-fg-color--lighter);box-shadow:var(--md-shadow-z1);font-size:.8rem;height:1.8rem;padding:0 .6rem;transition:border .25s,box-shadow .25s}.md-typeset .md-input:focus,.md-typeset .md-input:hover{border-bottom-color:var(--md-accent-fg-color);box-shadow:var(--md-shadow-z2)}.md-typeset .md-input--stretch{width:100%}.md-header{background-color:var(--md-primary-fg-color);box-shadow:0 0 .2rem #0000,0 .2rem .4rem #0000;color:var(--md-primary-bg-color);display:block;left:0;position:sticky;right:0;top:0;z-index:4}@media print{.md-header{display:none}}.md-header[hidden]{transform:translateY(-100%);transition:transform .25s cubic-bezier(.8,0,.6,1),box-shadow .25s}.md-header--shadow{box-shadow:0 0 .2rem #0000001a,0 .2rem .4rem #0003;transition:transform .25s cubic-bezier(.1,.7,.1,1),box-shadow .25s}.md-header__inner{align-items:center;display:flex;padding:0 .2rem}.md-header__button{color:currentcolor;cursor:pointer;margin:.2rem;outline-color:var(--md-accent-fg-color);padding:.4rem;position:relative;transition:opacity .25s;vertical-align:middle;z-index:1}.md-header__button:hover{opacity:.7}.md-header__button:not([hidden]){display:inline-block}.md-header__button:not(.focus-visible){-webkit-tap-highlight-color:transparent;outline:none}.md-header__button.md-logo{margin:.2rem;padding:.4rem}@media screen and (max-width:76.234375em){.md-header__button.md-logo{display:none}}.md-header__button.md-logo img,.md-header__button.md-logo svg{fill:currentcolor;display:block;height:1.2rem;width:auto}@media screen and (min-width:60em){.md-header__button[for=__search]{display:none}}.no-js .md-header__button[for=__search]{display:none}[dir=rtl] .md-header__button[for=__search] svg{transform:scaleX(-1)}@media screen and (min-width:76.25em){.md-header__button[for=__drawer]{display:none}}.md-header__topic{display:flex;max-width:100%;position:absolute;transition:transform .4s cubic-bezier(.1,.7,.1,1),opacity .15s;white-space:nowrap}.md-header__topic+.md-header__topic{opacity:0;pointer-events:none;transform:translateX(1.25rem);transition:transform .4s cubic-bezier(1,.7,.1,.1),opacity .15s;z-index:-1}[dir=rtl] .md-header__topic+.md-header__topic{transform:translateX(-1.25rem)}.md-header__topic:first-child{font-weight:700}[dir=ltr] .md-header__title{margin-left:1rem;margin-right:.4rem}[dir=rtl] .md-header__title{margin-left:.4rem;margin-right:1rem}.md-header__title{flex-grow:1;font-size:.9rem;height:2.4rem;line-height:2.4rem}.md-header__title--active .md-header__topic{opacity:0;pointer-events:none;transform:translateX(-1.25rem);transition:transform .4s cubic-bezier(1,.7,.1,.1),opacity .15s;z-index:-1}[dir=rtl] .md-header__title--active .md-header__topic{transform:translateX(1.25rem)}.md-header__title--active .md-header__topic+.md-header__topic{opacity:1;pointer-events:auto;transform:translateX(0);transition:transform .4s cubic-bezier(.1,.7,.1,1),opacity .15s;z-index:0}.md-header__title>.md-header__ellipsis{height:100%;position:relative;width:100%}.md-header__option{display:flex;flex-shrink:0;max-width:100%;transition:max-width 0ms .25s,opacity .25s .25s;white-space:nowrap}[data-md-toggle=search]:checked~.md-header .md-header__option{max-width:0;opacity:0;transition:max-width 0ms,opacity 0ms}.md-header__option>input{bottom:0}.md-header__source{display:none}@media screen and (min-width:60em){[dir=ltr] .md-header__source{margin-left:1rem}[dir=rtl] .md-header__source{margin-right:1rem}.md-header__source{display:block;max-width:11.7rem;width:11.7rem}}@media screen and (min-width:76.25em){[dir=ltr] .md-header__source{margin-left:1.4rem}[dir=rtl] .md-header__source{margin-right:1.4rem}}.md-meta{color:var(--md-default-fg-color--light);font-size:.7rem;line-height:1.3}.md-meta__list{display:inline-flex;flex-wrap:wrap;list-style:none;margin:0;padding:0}.md-meta__item:not(:last-child):after{content:"·";margin-left:.2rem;margin-right:.2rem}.md-meta__link{color:var(--md-typeset-a-color)}.md-meta__link:focus,.md-meta__link:hover{color:var(--md-accent-fg-color)}.md-draft{background-color:#ff1744;border-radius:.125em;color:#fff;display:inline-block;font-weight:700;padding-left:.5714285714em;padding-right:.5714285714em}:root{--md-nav-icon--prev:url('data:image/svg+xml;charset=utf-8,');--md-nav-icon--next:url('data:image/svg+xml;charset=utf-8,');--md-toc-icon:url('data:image/svg+xml;charset=utf-8,')}.md-nav{font-size:.7rem;line-height:1.3}.md-nav__title{color:var(--md-default-fg-color--light);display:block;font-weight:700;overflow:hidden;padding:0 .6rem;text-overflow:ellipsis}.md-nav__title .md-nav__button{display:none}.md-nav__title .md-nav__button img{height:100%;width:auto}.md-nav__title .md-nav__button.md-logo img,.md-nav__title .md-nav__button.md-logo svg{fill:currentcolor;display:block;height:2.4rem;max-width:100%;object-fit:contain;width:auto}.md-nav__list{list-style:none;margin:0;padding:0}.md-nav__link{align-items:flex-start;display:flex;gap:.4rem;margin-top:.625em;scroll-snap-align:start;transition:color 125ms}.md-nav__link--passed,.md-nav__link--passed code{color:var(--md-default-fg-color--light)}.md-nav__item .md-nav__link--active,.md-nav__item .md-nav__link--active code{color:var(--md-typeset-a-color)}.md-nav__link .md-ellipsis{position:relative}.md-nav__link .md-ellipsis code{word-break:normal}[dir=ltr] .md-nav__link .md-icon:last-child{margin-left:auto}[dir=rtl] .md-nav__link .md-icon:last-child{margin-right:auto}.md-nav__link .md-typeset{font-size:.7rem;line-height:1.3}.md-nav__link svg{fill:currentcolor;flex-shrink:0;height:1.3em;position:relative}.md-nav__link[for]:focus,.md-nav__link[for]:hover,.md-nav__link[href]:focus,.md-nav__link[href]:hover{color:var(--md-accent-fg-color);cursor:pointer}.md-nav__link[for]:focus code,.md-nav__link[for]:hover code,.md-nav__link[href]:focus code,.md-nav__link[href]:hover code{background-color:var(--md-accent-fg-color--transparent);color:var(--md-accent-fg-color)}.md-nav__link.focus-visible{outline-color:var(--md-accent-fg-color);outline-offset:.2rem}.md-nav--primary .md-nav__link[for=__toc]{display:none}.md-nav--primary .md-nav__link[for=__toc] .md-icon:after{background-color:currentcolor;display:block;height:100%;-webkit-mask-image:var(--md-toc-icon);mask-image:var(--md-toc-icon);width:100%}.md-nav--primary .md-nav__link[for=__toc]~.md-nav{display:none}.md-nav__container>.md-nav__link{margin-top:0}.md-nav__container>.md-nav__link:first-child{flex-grow:1;min-width:0}.md-nav__icon{flex-shrink:0}.md-nav__source{display:none}@media screen and (max-width:76.234375em){.md-nav--primary,.md-nav--primary .md-nav{background-color:var(--md-default-bg-color);display:flex;flex-direction:column;height:100%;left:0;position:absolute;right:0;top:0;z-index:1}.md-nav--primary .md-nav__item,.md-nav--primary .md-nav__title{font-size:.8rem;line-height:1.5}.md-nav--primary .md-nav__title{background-color:var(--md-default-fg-color--lightest);color:var(--md-default-fg-color--light);cursor:pointer;height:5.6rem;line-height:2.4rem;padding:3rem .8rem .2rem;position:relative;white-space:nowrap}[dir=ltr] .md-nav--primary .md-nav__title .md-nav__icon{left:.4rem}[dir=rtl] .md-nav--primary .md-nav__title .md-nav__icon{right:.4rem}.md-nav--primary .md-nav__title .md-nav__icon{display:block;height:1.2rem;margin:.2rem;position:absolute;top:.4rem;width:1.2rem}.md-nav--primary .md-nav__title .md-nav__icon:after{background-color:currentcolor;content:"";display:block;height:100%;-webkit-mask-image:var(--md-nav-icon--prev);mask-image:var(--md-nav-icon--prev);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;width:100%}.md-nav--primary .md-nav__title~.md-nav__list{background-color:var(--md-default-bg-color);box-shadow:0 .05rem 0 var(--md-default-fg-color--lightest) inset;overflow-y:auto;scroll-snap-type:y mandatory;touch-action:pan-y}.md-nav--primary .md-nav__title~.md-nav__list>:first-child{border-top:0}.md-nav--primary .md-nav__title[for=__drawer]{background-color:var(--md-primary-fg-color);color:var(--md-primary-bg-color);font-weight:700}.md-nav--primary .md-nav__title .md-logo{display:block;left:.2rem;margin:.2rem;padding:.4rem;position:absolute;right:.2rem;top:.2rem}.md-nav--primary .md-nav__list{flex:1}.md-nav--primary .md-nav__item{border-top:.05rem solid var(--md-default-fg-color--lightest)}.md-nav--primary .md-nav__item--active>.md-nav__link{color:var(--md-typeset-a-color)}.md-nav--primary .md-nav__item--active>.md-nav__link:focus,.md-nav--primary .md-nav__item--active>.md-nav__link:hover{color:var(--md-accent-fg-color)}.md-nav--primary .md-nav__link{margin-top:0;padding:.6rem .8rem}.md-nav--primary .md-nav__link svg{margin-top:.1em}.md-nav--primary .md-nav__link>.md-nav__link{padding:0}[dir=ltr] .md-nav--primary .md-nav__link .md-nav__icon{margin-right:-.2rem}[dir=rtl] .md-nav--primary .md-nav__link .md-nav__icon{margin-left:-.2rem}.md-nav--primary .md-nav__link .md-nav__icon{font-size:1.2rem;height:1.2rem;width:1.2rem}.md-nav--primary .md-nav__link .md-nav__icon:after{background-color:currentcolor;content:"";display:block;height:100%;-webkit-mask-image:var(--md-nav-icon--next);mask-image:var(--md-nav-icon--next);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;width:100%}[dir=rtl] .md-nav--primary .md-nav__icon:after{transform:scale(-1)}.md-nav--primary .md-nav--secondary .md-nav{background-color:initial;position:static}[dir=ltr] .md-nav--primary .md-nav--secondary .md-nav .md-nav__link{padding-left:1.4rem}[dir=rtl] .md-nav--primary .md-nav--secondary .md-nav .md-nav__link{padding-right:1.4rem}[dir=ltr] .md-nav--primary .md-nav--secondary .md-nav .md-nav .md-nav__link{padding-left:2rem}[dir=rtl] .md-nav--primary .md-nav--secondary .md-nav .md-nav .md-nav__link{padding-right:2rem}[dir=ltr] .md-nav--primary .md-nav--secondary .md-nav .md-nav .md-nav .md-nav__link{padding-left:2.6rem}[dir=rtl] .md-nav--primary .md-nav--secondary .md-nav .md-nav .md-nav .md-nav__link{padding-right:2.6rem}[dir=ltr] .md-nav--primary .md-nav--secondary .md-nav .md-nav .md-nav .md-nav .md-nav__link{padding-left:3.2rem}[dir=rtl] .md-nav--primary .md-nav--secondary .md-nav .md-nav .md-nav .md-nav .md-nav__link{padding-right:3.2rem}.md-nav--secondary{background-color:initial}.md-nav__toggle~.md-nav{display:flex;opacity:0;transform:translateX(100%);transition:transform .25s cubic-bezier(.8,0,.6,1),opacity 125ms 50ms}[dir=rtl] .md-nav__toggle~.md-nav{transform:translateX(-100%)}.md-nav__toggle:checked~.md-nav{opacity:1;transform:translateX(0);transition:transform .25s cubic-bezier(.4,0,.2,1),opacity 125ms 125ms}.md-nav__toggle:checked~.md-nav>.md-nav__list{-webkit-backface-visibility:hidden;backface-visibility:hidden}}@media screen and (max-width:59.984375em){.md-nav--primary .md-nav__link[for=__toc]{display:flex}.md-nav--primary .md-nav__link[for=__toc] .md-icon:after{content:""}.md-nav--primary .md-nav__link[for=__toc]+.md-nav__link{display:none}.md-nav--primary .md-nav__link[for=__toc]~.md-nav{display:flex}.md-nav__source{background-color:var(--md-primary-fg-color--dark);color:var(--md-primary-bg-color);display:block;padding:0 .2rem}}@media screen and (min-width:60em) and (max-width:76.234375em){.md-nav--integrated .md-nav__link[for=__toc]{display:flex}.md-nav--integrated .md-nav__link[for=__toc] .md-icon:after{content:""}.md-nav--integrated .md-nav__link[for=__toc]+.md-nav__link{display:none}.md-nav--integrated .md-nav__link[for=__toc]~.md-nav{display:flex}}@media screen and (min-width:60em){.md-nav{margin-bottom:-.4rem}.md-nav--secondary .md-nav__title{background:var(--md-default-bg-color);box-shadow:0 0 .4rem .4rem var(--md-default-bg-color);position:sticky;top:0;z-index:1}.md-nav--secondary .md-nav__title[for=__toc]{scroll-snap-align:start}.md-nav--secondary .md-nav__title .md-nav__icon{display:none}[dir=ltr] .md-nav--secondary .md-nav__list{padding-left:.6rem}[dir=rtl] .md-nav--secondary .md-nav__list{padding-right:.6rem}.md-nav--secondary .md-nav__list{padding-bottom:.4rem}[dir=ltr] .md-nav--secondary .md-nav__item>.md-nav__link{margin-right:.4rem}[dir=rtl] .md-nav--secondary .md-nav__item>.md-nav__link{margin-left:.4rem}}@media screen and (min-width:76.25em){.md-nav{margin-bottom:-.4rem;transition:max-height .25s cubic-bezier(.86,0,.07,1)}.md-nav--primary .md-nav__title{background:var(--md-default-bg-color);box-shadow:0 0 .4rem .4rem var(--md-default-bg-color);position:sticky;top:0;z-index:1}.md-nav--primary .md-nav__title[for=__drawer]{scroll-snap-align:start}.md-nav--primary .md-nav__title .md-nav__icon{display:none}[dir=ltr] .md-nav--primary .md-nav__list{padding-left:.6rem}[dir=rtl] .md-nav--primary .md-nav__list{padding-right:.6rem}.md-nav--primary .md-nav__list{padding-bottom:.4rem}[dir=ltr] .md-nav--primary .md-nav__item>.md-nav__link{margin-right:.4rem}[dir=rtl] .md-nav--primary .md-nav__item>.md-nav__link{margin-left:.4rem}.md-nav__toggle~.md-nav{display:grid;grid-template-rows:0fr;opacity:0;transition:grid-template-rows .25s cubic-bezier(.86,0,.07,1),opacity .25s,visibility 0ms .25s;visibility:collapse}.md-nav__toggle~.md-nav>.md-nav__list{overflow:hidden}.md-nav__toggle.md-toggle--indeterminate~.md-nav,.md-nav__toggle:checked~.md-nav{grid-template-rows:1fr;opacity:1;transition:grid-template-rows .25s cubic-bezier(.86,0,.07,1),opacity .15s .1s,visibility 0ms;visibility:visible}.md-nav__toggle.md-toggle--indeterminate~.md-nav{transition:none}.md-nav__item--nested>.md-nav>.md-nav__title{display:none}.md-nav__item--section{display:block;margin:1.25em 0}.md-nav__item--section:last-child{margin-bottom:0}.md-nav__item--section>.md-nav__link{font-weight:700}.md-nav__item--section>.md-nav__link[for]{color:var(--md-default-fg-color--light)}.md-nav__item--section>.md-nav__link:not(.md-nav__container){pointer-events:none}.md-nav__item--section>.md-nav__link .md-icon,.md-nav__item--section>.md-nav__link>[for]{display:none}[dir=ltr] .md-nav__item--section>.md-nav{margin-left:-.6rem}[dir=rtl] .md-nav__item--section>.md-nav{margin-right:-.6rem}.md-nav__item--section>.md-nav{display:block;opacity:1;visibility:visible}.md-nav__item--section>.md-nav>.md-nav__list>.md-nav__item{padding:0}.md-nav__icon{border-radius:100%;height:.9rem;transition:background-color .25s;width:.9rem}.md-nav__icon:hover{background-color:var(--md-accent-fg-color--transparent)}.md-nav__icon:after{background-color:currentcolor;border-radius:100%;content:"";display:inline-block;height:100%;-webkit-mask-image:var(--md-nav-icon--next);mask-image:var(--md-nav-icon--next);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;transition:transform .25s;vertical-align:-.1rem;width:100%}[dir=rtl] .md-nav__icon:after{transform:rotate(180deg)}.md-nav__item--nested .md-nav__toggle:checked~.md-nav__link .md-nav__icon:after,.md-nav__item--nested .md-toggle--indeterminate~.md-nav__link .md-nav__icon:after{transform:rotate(90deg)}.md-nav--lifted>.md-nav__list>.md-nav__item,.md-nav--lifted>.md-nav__title{display:none}.md-nav--lifted>.md-nav__list>.md-nav__item--active{display:block}.md-nav--lifted>.md-nav__list>.md-nav__item--active>.md-nav__link{background:var(--md-default-bg-color);box-shadow:0 0 .4rem .4rem var(--md-default-bg-color);margin-top:0;position:sticky;top:0;z-index:1}.md-nav--lifted>.md-nav__list>.md-nav__item--active>.md-nav__link:not(.md-nav__container){pointer-events:none}.md-nav--lifted>.md-nav__list>.md-nav__item--active.md-nav__item--section{margin:0}[dir=ltr] .md-nav--lifted>.md-nav__list>.md-nav__item>.md-nav:not(.md-nav--secondary){margin-left:-.6rem}[dir=rtl] .md-nav--lifted>.md-nav__list>.md-nav__item>.md-nav:not(.md-nav--secondary){margin-right:-.6rem}.md-nav--lifted>.md-nav__list>.md-nav__item>[for]{color:var(--md-default-fg-color--light)}.md-nav--lifted .md-nav[data-md-level="1"]{grid-template-rows:1fr;opacity:1;visibility:visible}[dir=ltr] .md-nav--integrated>.md-nav__list>.md-nav__item--active .md-nav--secondary{border-left:.05rem solid var(--md-primary-fg-color)}[dir=rtl] .md-nav--integrated>.md-nav__list>.md-nav__item--active .md-nav--secondary{border-right:.05rem solid var(--md-primary-fg-color)}.md-nav--integrated>.md-nav__list>.md-nav__item--active .md-nav--secondary{display:block;margin-bottom:1.25em;opacity:1;visibility:visible}.md-nav--integrated>.md-nav__list>.md-nav__item--active .md-nav--secondary>.md-nav__list{overflow:visible;padding-bottom:0}.md-nav--integrated>.md-nav__list>.md-nav__item--active .md-nav--secondary>.md-nav__title{display:none}}.md-pagination{font-size:.8rem;font-weight:700;gap:.4rem}.md-pagination,.md-pagination>*{align-items:center;display:flex;justify-content:center}.md-pagination>*{border-radius:.2rem;height:1.8rem;min-width:1.8rem;text-align:center}.md-pagination__current{background-color:var(--md-default-fg-color--lightest);color:var(--md-default-fg-color--light)}.md-pagination__link{transition:color 125ms,background-color 125ms}.md-pagination__link:focus,.md-pagination__link:hover{background-color:var(--md-accent-fg-color--transparent);color:var(--md-accent-fg-color)}.md-pagination__link:focus svg,.md-pagination__link:hover svg{color:var(--md-accent-fg-color)}.md-pagination__link.focus-visible{outline-color:var(--md-accent-fg-color);outline-offset:.2rem}.md-pagination__link svg{fill:currentcolor;color:var(--md-default-fg-color--lighter);display:block;max-height:100%;width:1.2rem}:root{--md-path-icon:url('data:image/svg+xml;charset=utf-8,')}.md-path{font-size:.7rem;margin:0 .8rem;overflow:auto;padding-top:1.2rem}.md-path:not([hidden]){display:block}@media screen and (min-width:76.25em){.md-path{margin:0 1.2rem}}.md-path__list{align-items:center;display:flex;gap:.2rem;list-style:none;margin:0;padding:0}.md-path__item:not(:first-child){display:inline-flex;gap:.2rem;white-space:nowrap}.md-path__item:not(:first-child):before{background-color:var(--md-default-fg-color--lighter);content:"";display:inline;height:.8rem;-webkit-mask-image:var(--md-path-icon);mask-image:var(--md-path-icon);width:.8rem}.md-path__link{align-items:center;color:var(--md-default-fg-color--light);display:flex}.md-path__link:focus,.md-path__link:hover{color:var(--md-accent-fg-color)}:root{--md-post-pin-icon:url('data:image/svg+xml;charset=utf-8,')}.md-post__back{border-bottom:.05rem solid var(--md-default-fg-color--lightest);margin-bottom:1.2rem;padding-bottom:1.2rem}@media screen and (max-width:76.234375em){.md-post__back{display:none}}[dir=rtl] .md-post__back svg{transform:scaleX(-1)}.md-post__authors{display:flex;flex-direction:column;gap:.6rem;margin:0 .6rem 1.2rem}.md-post .md-post__meta a{transition:color 125ms}.md-post .md-post__meta a:focus,.md-post .md-post__meta a:hover{color:var(--md-accent-fg-color)}.md-post__title{color:var(--md-default-fg-color--light);font-weight:700}.md-post--excerpt{margin-bottom:3.2rem}.md-post--excerpt .md-post__header{align-items:center;display:flex;gap:.6rem;min-height:1.6rem}.md-post--excerpt .md-post__authors{align-items:center;display:inline-flex;flex-direction:row;gap:.2rem;margin:0;min-height:2.4rem}[dir=ltr] .md-post--excerpt .md-post__meta .md-meta__list{margin-right:.4rem}[dir=rtl] .md-post--excerpt .md-post__meta .md-meta__list{margin-left:.4rem}.md-post--excerpt .md-post__content>:first-child{--md-scroll-margin:6rem;margin-top:0}.md-post>.md-nav--secondary{margin:1em 0}.md-pin{background:var(--md-default-fg-color--lightest);border-radius:1rem;margin-top:-.05rem;padding:.2rem}.md-pin:after{background-color:currentcolor;content:"";display:block;height:.6rem;margin:0 auto;-webkit-mask-image:var(--md-post-pin-icon);mask-image:var(--md-post-pin-icon);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;width:.6rem}.md-profile{align-items:center;display:flex;font-size:.7rem;gap:.6rem;line-height:1.4;width:100%}.md-profile__description{flex-grow:1}.md-content--post{display:flex}@media screen and (max-width:76.234375em){.md-content--post{flex-flow:column-reverse}}.md-content--post>.md-content__inner{min-width:0}@media screen and (min-width:76.25em){[dir=ltr] .md-content--post>.md-content__inner{margin-left:1.2rem}[dir=rtl] .md-content--post>.md-content__inner{margin-right:1.2rem}}@media screen and (max-width:76.234375em){.md-sidebar.md-sidebar--post{padding:0;position:static;width:100%}.md-sidebar.md-sidebar--post .md-sidebar__scrollwrap{overflow:visible}.md-sidebar.md-sidebar--post .md-sidebar__inner{padding:0}.md-sidebar.md-sidebar--post .md-post__meta{margin-left:.6rem;margin-right:.6rem}.md-sidebar.md-sidebar--post .md-nav__item{border:none;display:inline}.md-sidebar.md-sidebar--post .md-nav__list{display:inline-flex;flex-wrap:wrap;gap:.6rem;padding-bottom:.6rem;padding-top:.6rem}.md-sidebar.md-sidebar--post .md-nav__link{padding:0}.md-sidebar.md-sidebar--post .md-nav{height:auto;margin-bottom:0;position:static}}:root{--md-progress-value:0;--md-progress-delay:400ms}.md-progress{background:var(--md-primary-bg-color);height:.075rem;opacity:min(clamp(0,var(--md-progress-value),1),clamp(0,100 - var(--md-progress-value),1));position:fixed;top:0;transform:scaleX(calc(var(--md-progress-value)*1%));transform-origin:left;transition:transform .5s cubic-bezier(.19,1,.22,1),opacity .25s var(--md-progress-delay);width:100%;z-index:4}:root{--md-search-result-icon:url('data:image/svg+xml;charset=utf-8,')}.md-search{position:relative}@media screen and (min-width:60em){.md-search{padding:.2rem 0}}.no-js .md-search{display:none}.md-search__overlay{opacity:0;z-index:1}@media screen and (max-width:59.984375em){[dir=ltr] .md-search__overlay{left:-2.2rem}[dir=rtl] .md-search__overlay{right:-2.2rem}.md-search__overlay{background-color:var(--md-default-bg-color);border-radius:1rem;height:2rem;overflow:hidden;pointer-events:none;position:absolute;top:-1rem;transform-origin:center;transition:transform .3s .1s,opacity .2s .2s;width:2rem}[data-md-toggle=search]:checked~.md-header .md-search__overlay{opacity:1;transition:transform .4s,opacity .1s}}@media screen and (min-width:60em){[dir=ltr] .md-search__overlay{left:0}[dir=rtl] .md-search__overlay{right:0}.md-search__overlay{background-color:#0000008a;cursor:pointer;height:0;position:fixed;top:0;transition:width 0ms .25s,height 0ms .25s,opacity .25s;width:0}[data-md-toggle=search]:checked~.md-header .md-search__overlay{height:200vh;opacity:1;transition:width 0ms,height 0ms,opacity .25s;width:100%}}@media screen and (max-width:29.984375em){[data-md-toggle=search]:checked~.md-header .md-search__overlay{transform:scale(45)}}@media screen and (min-width:30em) and (max-width:44.984375em){[data-md-toggle=search]:checked~.md-header .md-search__overlay{transform:scale(60)}}@media screen and (min-width:45em) and (max-width:59.984375em){[data-md-toggle=search]:checked~.md-header .md-search__overlay{transform:scale(75)}}.md-search__inner{-webkit-backface-visibility:hidden;backface-visibility:hidden}@media screen and (max-width:59.984375em){[dir=ltr] .md-search__inner{left:0}[dir=rtl] .md-search__inner{right:0}.md-search__inner{height:0;opacity:0;overflow:hidden;position:fixed;top:0;transform:translateX(5%);transition:width 0ms .3s,height 0ms .3s,transform .15s cubic-bezier(.4,0,.2,1) .15s,opacity .15s .15s;width:0;z-index:2}[dir=rtl] .md-search__inner{transform:translateX(-5%)}[data-md-toggle=search]:checked~.md-header .md-search__inner{height:100%;opacity:1;transform:translateX(0);transition:width 0ms 0ms,height 0ms 0ms,transform .15s cubic-bezier(.1,.7,.1,1) .15s,opacity .15s .15s;width:100%}}@media screen and (min-width:60em){[dir=ltr] .md-search__inner{float:right}[dir=rtl] .md-search__inner{float:left}.md-search__inner{padding:.1rem 0;position:relative;transition:width .25s cubic-bezier(.1,.7,.1,1);width:11.7rem}}@media screen and (min-width:60em) and (max-width:76.234375em){[data-md-toggle=search]:checked~.md-header .md-search__inner{width:23.4rem}}@media screen and (min-width:76.25em){[data-md-toggle=search]:checked~.md-header .md-search__inner{width:34.4rem}}.md-search__form{background-color:var(--md-default-bg-color);box-shadow:0 0 .6rem #0000;height:2.4rem;position:relative;transition:color .25s,background-color .25s;z-index:2}@media screen and (min-width:60em){.md-search__form{background-color:#00000042;border-radius:.1rem;height:1.8rem}.md-search__form:hover{background-color:#ffffff1f}}[data-md-toggle=search]:checked~.md-header .md-search__form{background-color:var(--md-default-bg-color);border-radius:.1rem .1rem 0 0;box-shadow:0 0 .6rem #00000012;color:var(--md-default-fg-color)}[dir=ltr] .md-search__input{padding-left:3.6rem;padding-right:2.2rem}[dir=rtl] .md-search__input{padding-left:2.2rem;padding-right:3.6rem}.md-search__input{background:#0000;font-size:.9rem;height:100%;position:relative;text-overflow:ellipsis;width:100%;z-index:2}.md-search__input::placeholder{transition:color .25s}.md-search__input::placeholder,.md-search__input~.md-search__icon{color:var(--md-default-fg-color--light)}.md-search__input::-ms-clear{display:none}@media screen and (max-width:59.984375em){.md-search__input{font-size:.9rem;height:2.4rem;width:100%}}@media screen and (min-width:60em){[dir=ltr] .md-search__input{padding-left:2.2rem}[dir=rtl] .md-search__input{padding-right:2.2rem}.md-search__input{color:inherit;font-size:.8rem}.md-search__input::placeholder{color:var(--md-primary-bg-color--light)}.md-search__input+.md-search__icon{color:var(--md-primary-bg-color)}[data-md-toggle=search]:checked~.md-header .md-search__input{text-overflow:clip}[data-md-toggle=search]:checked~.md-header .md-search__input+.md-search__icon{color:var(--md-default-fg-color--light)}[data-md-toggle=search]:checked~.md-header .md-search__input::placeholder{color:#0000}}.md-search__icon{cursor:pointer;display:inline-block;height:1.2rem;transition:color .25s,opacity .25s;width:1.2rem}.md-search__icon:hover{opacity:.7}[dir=ltr] .md-search__icon[for=__search]{left:.5rem}[dir=rtl] .md-search__icon[for=__search]{right:.5rem}.md-search__icon[for=__search]{position:absolute;top:.3rem;z-index:2}[dir=rtl] .md-search__icon[for=__search] svg{transform:scaleX(-1)}@media screen and (max-width:59.984375em){[dir=ltr] .md-search__icon[for=__search]{left:.8rem}[dir=rtl] .md-search__icon[for=__search]{right:.8rem}.md-search__icon[for=__search]{top:.6rem}.md-search__icon[for=__search] svg:first-child{display:none}}@media screen and (min-width:60em){.md-search__icon[for=__search]{pointer-events:none}.md-search__icon[for=__search] svg:last-child{display:none}}[dir=ltr] .md-search__options{right:.5rem}[dir=rtl] .md-search__options{left:.5rem}.md-search__options{pointer-events:none;position:absolute;top:.3rem;z-index:2}@media screen and (max-width:59.984375em){[dir=ltr] .md-search__options{right:.8rem}[dir=rtl] .md-search__options{left:.8rem}.md-search__options{top:.6rem}}[dir=ltr] .md-search__options>.md-icon{margin-left:.2rem}[dir=rtl] .md-search__options>.md-icon{margin-right:.2rem}.md-search__options>.md-icon{color:var(--md-default-fg-color--light);opacity:0;transform:scale(.75);transition:transform .15s cubic-bezier(.1,.7,.1,1),opacity .15s}.md-search__options>.md-icon:not(.focus-visible){-webkit-tap-highlight-color:transparent;outline:none}[data-md-toggle=search]:checked~.md-header .md-search__input:valid~.md-search__options>.md-icon{opacity:1;pointer-events:auto;transform:scale(1)}[data-md-toggle=search]:checked~.md-header .md-search__input:valid~.md-search__options>.md-icon:hover{opacity:.7}[dir=ltr] .md-search__suggest{padding-left:3.6rem;padding-right:2.2rem}[dir=rtl] .md-search__suggest{padding-left:2.2rem;padding-right:3.6rem}.md-search__suggest{align-items:center;color:var(--md-default-fg-color--lighter);display:flex;font-size:.9rem;height:100%;opacity:0;position:absolute;top:0;transition:opacity 50ms;white-space:nowrap;width:100%}@media screen and (min-width:60em){[dir=ltr] .md-search__suggest{padding-left:2.2rem}[dir=rtl] .md-search__suggest{padding-right:2.2rem}.md-search__suggest{font-size:.8rem}}[data-md-toggle=search]:checked~.md-header .md-search__suggest{opacity:1;transition:opacity .3s .1s}[dir=ltr] .md-search__output{border-bottom-left-radius:.1rem}[dir=ltr] .md-search__output,[dir=rtl] .md-search__output{border-bottom-right-radius:.1rem}[dir=rtl] .md-search__output{border-bottom-left-radius:.1rem}.md-search__output{overflow:hidden;position:absolute;width:100%;z-index:1}@media screen and (max-width:59.984375em){.md-search__output{bottom:0;top:2.4rem}}@media screen and (min-width:60em){.md-search__output{opacity:0;top:1.9rem;transition:opacity .4s}[data-md-toggle=search]:checked~.md-header .md-search__output{box-shadow:var(--md-shadow-z3);opacity:1}}.md-search__scrollwrap{-webkit-backface-visibility:hidden;backface-visibility:hidden;background-color:var(--md-default-bg-color);height:100%;overflow-y:auto;touch-action:pan-y}@media (-webkit-max-device-pixel-ratio:1),(max-resolution:1dppx){.md-search__scrollwrap{transform:translateZ(0)}}@media screen and (min-width:60em) and (max-width:76.234375em){.md-search__scrollwrap{width:23.4rem}}@media screen and (min-width:76.25em){.md-search__scrollwrap{width:34.4rem}}@media screen and (min-width:60em){.md-search__scrollwrap{max-height:0;scrollbar-color:var(--md-default-fg-color--lighter) #0000;scrollbar-width:thin}[data-md-toggle=search]:checked~.md-header .md-search__scrollwrap{max-height:75vh}.md-search__scrollwrap:hover{scrollbar-color:var(--md-accent-fg-color) #0000}.md-search__scrollwrap::-webkit-scrollbar{height:.2rem;width:.2rem}.md-search__scrollwrap::-webkit-scrollbar-thumb{background-color:var(--md-default-fg-color--lighter)}.md-search__scrollwrap::-webkit-scrollbar-thumb:hover{background-color:var(--md-accent-fg-color)}}.md-search-result{color:var(--md-default-fg-color);word-break:break-word}.md-search-result__meta{background-color:var(--md-default-fg-color--lightest);color:var(--md-default-fg-color--light);font-size:.64rem;line-height:1.8rem;padding:0 .8rem;scroll-snap-align:start}@media screen and (min-width:60em){[dir=ltr] .md-search-result__meta{padding-left:2.2rem}[dir=rtl] .md-search-result__meta{padding-right:2.2rem}}.md-search-result__list{list-style:none;margin:0;padding:0;-webkit-user-select:none;user-select:none}.md-search-result__item{box-shadow:0 -.05rem var(--md-default-fg-color--lightest)}.md-search-result__item:first-child{box-shadow:none}.md-search-result__link{display:block;outline:none;scroll-snap-align:start;transition:background-color .25s}.md-search-result__link:focus,.md-search-result__link:hover{background-color:var(--md-accent-fg-color--transparent)}.md-search-result__link:last-child p:last-child{margin-bottom:.6rem}.md-search-result__more>summary{cursor:pointer;display:block;outline:none;position:sticky;scroll-snap-align:start;top:0;z-index:1}.md-search-result__more>summary::marker{display:none}.md-search-result__more>summary::-webkit-details-marker{display:none}.md-search-result__more>summary>div{color:var(--md-typeset-a-color);font-size:.64rem;padding:.75em .8rem;transition:color .25s,background-color .25s}@media screen and (min-width:60em){[dir=ltr] .md-search-result__more>summary>div{padding-left:2.2rem}[dir=rtl] .md-search-result__more>summary>div{padding-right:2.2rem}}.md-search-result__more>summary:focus>div,.md-search-result__more>summary:hover>div{background-color:var(--md-accent-fg-color--transparent);color:var(--md-accent-fg-color)}.md-search-result__more[open]>summary{background-color:var(--md-default-bg-color)}.md-search-result__article{overflow:hidden;padding:0 .8rem;position:relative}@media screen and (min-width:60em){[dir=ltr] .md-search-result__article{padding-left:2.2rem}[dir=rtl] .md-search-result__article{padding-right:2.2rem}}[dir=ltr] .md-search-result__icon{left:0}[dir=rtl] .md-search-result__icon{right:0}.md-search-result__icon{color:var(--md-default-fg-color--light);height:1.2rem;margin:.5rem;position:absolute;width:1.2rem}@media screen and (max-width:59.984375em){.md-search-result__icon{display:none}}.md-search-result__icon:after{background-color:currentcolor;content:"";display:inline-block;height:100%;-webkit-mask-image:var(--md-search-result-icon);mask-image:var(--md-search-result-icon);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;width:100%}[dir=rtl] .md-search-result__icon:after{transform:scaleX(-1)}.md-search-result .md-typeset{color:var(--md-default-fg-color--light);font-size:.64rem;line-height:1.6}.md-search-result .md-typeset h1{color:var(--md-default-fg-color);font-size:.8rem;font-weight:400;line-height:1.4;margin:.55rem 0}.md-search-result .md-typeset h1 mark{text-decoration:none}.md-search-result .md-typeset h2{color:var(--md-default-fg-color);font-size:.64rem;font-weight:700;line-height:1.6;margin:.5em 0}.md-search-result .md-typeset h2 mark{text-decoration:none}.md-search-result__terms{color:var(--md-default-fg-color);display:block;font-size:.64rem;font-style:italic;margin:.5em 0}.md-search-result mark{background-color:initial;color:var(--md-accent-fg-color);text-decoration:underline}.md-select{position:relative;z-index:1}.md-select__inner{background-color:var(--md-default-bg-color);border-radius:.1rem;box-shadow:var(--md-shadow-z2);color:var(--md-default-fg-color);left:50%;margin-top:.2rem;max-height:0;opacity:0;position:absolute;top:calc(100% - .2rem);transform:translate3d(-50%,.3rem,0);transition:transform .25s 375ms,opacity .25s .25s,max-height 0ms .5s}.md-select:focus-within .md-select__inner,.md-select:hover .md-select__inner{max-height:10rem;opacity:1;transform:translate3d(-50%,0,0);transition:transform .25s cubic-bezier(.1,.7,.1,1),opacity .25s,max-height 0ms}.md-select__inner:after{border-bottom:.2rem solid #0000;border-bottom-color:var(--md-default-bg-color);border-left:.2rem solid #0000;border-right:.2rem solid #0000;border-top:0;content:"";height:0;left:50%;margin-left:-.2rem;margin-top:-.2rem;position:absolute;top:0;width:0}.md-select__list{border-radius:.1rem;font-size:.8rem;list-style-type:none;margin:0;max-height:inherit;overflow:auto;padding:0}.md-select__item{line-height:1.8rem}[dir=ltr] .md-select__link{padding-left:.6rem;padding-right:1.2rem}[dir=rtl] .md-select__link{padding-left:1.2rem;padding-right:.6rem}.md-select__link{cursor:pointer;display:block;outline:none;scroll-snap-align:start;transition:background-color .25s,color .25s;width:100%}.md-select__link:focus,.md-select__link:hover{color:var(--md-accent-fg-color)}.md-select__link:focus{background-color:var(--md-default-fg-color--lightest)}.md-sidebar{align-self:flex-start;flex-shrink:0;padding:1.2rem 0;position:sticky;top:2.4rem;width:12.1rem}@media print{.md-sidebar{display:none}}@media screen and (max-width:76.234375em){[dir=ltr] .md-sidebar--primary{left:-12.1rem}[dir=rtl] .md-sidebar--primary{right:-12.1rem}.md-sidebar--primary{background-color:var(--md-default-bg-color);display:block;height:100%;position:fixed;top:0;transform:translateX(0);transition:transform .25s cubic-bezier(.4,0,.2,1),box-shadow .25s;width:12.1rem;z-index:5}[data-md-toggle=drawer]:checked~.md-container .md-sidebar--primary{box-shadow:var(--md-shadow-z3);transform:translateX(12.1rem)}[dir=rtl] [data-md-toggle=drawer]:checked~.md-container .md-sidebar--primary{transform:translateX(-12.1rem)}.md-sidebar--primary .md-sidebar__scrollwrap{bottom:0;left:0;margin:0;overflow:hidden;position:absolute;right:0;scroll-snap-type:none;top:0}}@media screen and (min-width:76.25em){.md-sidebar{height:0}.no-js .md-sidebar{height:auto}.md-header--lifted~.md-container .md-sidebar{top:4.8rem}}.md-sidebar--secondary{display:none;order:2}@media screen and (min-width:60em){.md-sidebar--secondary{height:0}.no-js .md-sidebar--secondary{height:auto}.md-sidebar--secondary:not([hidden]){display:block}.md-sidebar--secondary .md-sidebar__scrollwrap{touch-action:pan-y}}.md-sidebar__scrollwrap{scrollbar-gutter:stable;-webkit-backface-visibility:hidden;backface-visibility:hidden;margin:0 .2rem;overflow-y:auto;scrollbar-color:var(--md-default-fg-color--lighter) #0000;scrollbar-width:thin}.md-sidebar__scrollwrap::-webkit-scrollbar{height:.2rem;width:.2rem}.md-sidebar__scrollwrap:focus-within,.md-sidebar__scrollwrap:hover{scrollbar-color:var(--md-accent-fg-color) #0000}.md-sidebar__scrollwrap:focus-within::-webkit-scrollbar-thumb,.md-sidebar__scrollwrap:hover::-webkit-scrollbar-thumb{background-color:var(--md-default-fg-color--lighter)}.md-sidebar__scrollwrap:focus-within::-webkit-scrollbar-thumb:hover,.md-sidebar__scrollwrap:hover::-webkit-scrollbar-thumb:hover{background-color:var(--md-accent-fg-color)}@supports selector(::-webkit-scrollbar){.md-sidebar__scrollwrap{scrollbar-gutter:auto}[dir=ltr] .md-sidebar__inner{padding-right:calc(100% - 11.5rem)}[dir=rtl] .md-sidebar__inner{padding-left:calc(100% - 11.5rem)}}@media screen and (max-width:76.234375em){.md-overlay{background-color:#0000008a;height:0;opacity:0;position:fixed;top:0;transition:width 0ms .25s,height 0ms .25s,opacity .25s;width:0;z-index:5}[data-md-toggle=drawer]:checked~.md-overlay{height:100%;opacity:1;transition:width 0ms,height 0ms,opacity .25s;width:100%}}@keyframes facts{0%{height:0}to{height:.65rem}}@keyframes fact{0%{opacity:0;transform:translateY(100%)}50%{opacity:0}to{opacity:1;transform:translateY(0)}}:root{--md-source-forks-icon:url('data:image/svg+xml;charset=utf-8,');--md-source-repositories-icon:url('data:image/svg+xml;charset=utf-8,');--md-source-stars-icon:url('data:image/svg+xml;charset=utf-8,');--md-source-version-icon:url('data:image/svg+xml;charset=utf-8,')}.md-source{-webkit-backface-visibility:hidden;backface-visibility:hidden;display:block;font-size:.65rem;line-height:1.2;outline-color:var(--md-accent-fg-color);transition:opacity .25s;white-space:nowrap}.md-source:hover{opacity:.7}.md-source__icon{display:inline-block;height:2.4rem;vertical-align:middle;width:2rem}[dir=ltr] .md-source__icon svg{margin-left:.6rem}[dir=rtl] .md-source__icon svg{margin-right:.6rem}.md-source__icon svg{margin-top:.6rem}[dir=ltr] .md-source__icon+.md-source__repository{padding-left:2rem}[dir=rtl] .md-source__icon+.md-source__repository{padding-right:2rem}[dir=ltr] .md-source__icon+.md-source__repository{margin-left:-2rem}[dir=rtl] .md-source__icon+.md-source__repository{margin-right:-2rem}[dir=ltr] .md-source__repository{margin-left:.6rem}[dir=rtl] .md-source__repository{margin-right:.6rem}.md-source__repository{display:inline-block;max-width:calc(100% - 1.2rem);overflow:hidden;text-overflow:ellipsis;vertical-align:middle}.md-source__facts{display:flex;font-size:.55rem;gap:.4rem;list-style-type:none;margin:.1rem 0 0;opacity:.75;overflow:hidden;padding:0;width:100%}.md-source__repository--active .md-source__facts{animation:facts .25s ease-in}.md-source__fact{overflow:hidden;text-overflow:ellipsis}.md-source__repository--active .md-source__fact{animation:fact .4s ease-out}[dir=ltr] .md-source__fact:before{margin-right:.1rem}[dir=rtl] .md-source__fact:before{margin-left:.1rem}.md-source__fact:before{background-color:currentcolor;content:"";display:inline-block;height:.6rem;-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;vertical-align:text-top;width:.6rem}.md-source__fact:nth-child(1n+2){flex-shrink:0}.md-source__fact--version:before{-webkit-mask-image:var(--md-source-version-icon);mask-image:var(--md-source-version-icon)}.md-source__fact--stars:before{-webkit-mask-image:var(--md-source-stars-icon);mask-image:var(--md-source-stars-icon)}.md-source__fact--forks:before{-webkit-mask-image:var(--md-source-forks-icon);mask-image:var(--md-source-forks-icon)}.md-source__fact--repositories:before{-webkit-mask-image:var(--md-source-repositories-icon);mask-image:var(--md-source-repositories-icon)}.md-source-file{margin:1em 0}[dir=ltr] .md-source-file__fact{margin-right:.6rem}[dir=rtl] .md-source-file__fact{margin-left:.6rem}.md-source-file__fact{align-items:center;color:var(--md-default-fg-color--light);display:inline-flex;font-size:.68rem;gap:.3rem}.md-source-file__fact .md-icon{flex-shrink:0;margin-bottom:.05rem}[dir=ltr] .md-source-file__fact .md-author{float:left}[dir=rtl] .md-source-file__fact .md-author{float:right}.md-source-file__fact .md-author{margin-right:.2rem}.md-source-file__fact svg{width:.9rem}:root{--md-status:url('data:image/svg+xml;charset=utf-8,');--md-status--new:url('data:image/svg+xml;charset=utf-8,');--md-status--deprecated:url('data:image/svg+xml;charset=utf-8,');--md-status--encrypted:url('data:image/svg+xml;charset=utf-8,')}.md-status:after{background-color:var(--md-default-fg-color--light);content:"";display:inline-block;height:1.125em;-webkit-mask-image:var(--md-status);mask-image:var(--md-status);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;vertical-align:text-bottom;width:1.125em}.md-status:hover:after{background-color:currentcolor}.md-status--new:after{-webkit-mask-image:var(--md-status--new);mask-image:var(--md-status--new)}.md-status--deprecated:after{-webkit-mask-image:var(--md-status--deprecated);mask-image:var(--md-status--deprecated)}.md-status--encrypted:after{-webkit-mask-image:var(--md-status--encrypted);mask-image:var(--md-status--encrypted)}.md-tabs{background-color:var(--md-primary-fg-color);color:var(--md-primary-bg-color);display:block;line-height:1.3;overflow:auto;width:100%;z-index:3}@media print{.md-tabs{display:none}}@media screen and (max-width:76.234375em){.md-tabs{display:none}}.md-tabs[hidden]{pointer-events:none}[dir=ltr] .md-tabs__list{margin-left:.2rem}[dir=rtl] .md-tabs__list{margin-right:.2rem}.md-tabs__list{contain:content;display:flex;list-style:none;margin:0;overflow:auto;padding:0;scrollbar-width:none;white-space:nowrap}.md-tabs__list::-webkit-scrollbar{display:none}.md-tabs__item{height:2.4rem;padding-left:.6rem;padding-right:.6rem}.md-tabs__item--active .md-tabs__link{color:inherit;opacity:1}.md-tabs__link{-webkit-backface-visibility:hidden;backface-visibility:hidden;display:flex;font-size:.7rem;margin-top:.8rem;opacity:.7;outline-color:var(--md-accent-fg-color);outline-offset:.2rem;transition:transform .4s cubic-bezier(.1,.7,.1,1),opacity .25s}.md-tabs__link:focus,.md-tabs__link:hover{color:inherit;opacity:1}[dir=ltr] .md-tabs__link svg{margin-right:.4rem}[dir=rtl] .md-tabs__link svg{margin-left:.4rem}.md-tabs__link svg{fill:currentcolor;height:1.3em}.md-tabs__item:nth-child(2) .md-tabs__link{transition-delay:20ms}.md-tabs__item:nth-child(3) .md-tabs__link{transition-delay:40ms}.md-tabs__item:nth-child(4) .md-tabs__link{transition-delay:60ms}.md-tabs__item:nth-child(5) .md-tabs__link{transition-delay:80ms}.md-tabs__item:nth-child(6) .md-tabs__link{transition-delay:.1s}.md-tabs__item:nth-child(7) .md-tabs__link{transition-delay:.12s}.md-tabs__item:nth-child(8) .md-tabs__link{transition-delay:.14s}.md-tabs__item:nth-child(9) .md-tabs__link{transition-delay:.16s}.md-tabs__item:nth-child(10) .md-tabs__link{transition-delay:.18s}.md-tabs__item:nth-child(11) .md-tabs__link{transition-delay:.2s}.md-tabs__item:nth-child(12) .md-tabs__link{transition-delay:.22s}.md-tabs__item:nth-child(13) .md-tabs__link{transition-delay:.24s}.md-tabs__item:nth-child(14) .md-tabs__link{transition-delay:.26s}.md-tabs__item:nth-child(15) .md-tabs__link{transition-delay:.28s}.md-tabs__item:nth-child(16) .md-tabs__link{transition-delay:.3s}.md-tabs[hidden] .md-tabs__link{opacity:0;transform:translateY(50%);transition:transform 0ms .1s,opacity .1s}:root{--md-tag-icon:url('data:image/svg+xml;charset=utf-8,')}.md-typeset .md-tags:not([hidden]){display:inline-flex;flex-wrap:wrap;gap:.5em;margin-bottom:.75em;margin-top:-.125em}.md-typeset .md-tag{align-items:center;background:var(--md-default-fg-color--lightest);border-radius:2.4rem;display:inline-flex;font-size:.64rem;font-size:min(.8em,.64rem);font-weight:700;gap:.5em;letter-spacing:normal;line-height:1.6;padding:.3125em .78125em}.md-typeset .md-tag[href]{-webkit-tap-highlight-color:transparent;color:inherit;outline:none;transition:color 125ms,background-color 125ms}.md-typeset .md-tag[href]:focus,.md-typeset .md-tag[href]:hover{background-color:var(--md-accent-fg-color);color:var(--md-accent-bg-color)}[id]>.md-typeset .md-tag{vertical-align:text-top}.md-typeset .md-tag-shadow{opacity:.5}.md-typeset .md-tag-icon:before{background-color:var(--md-default-fg-color--lighter);content:"";display:inline-block;height:1.2em;-webkit-mask-image:var(--md-tag-icon);mask-image:var(--md-tag-icon);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;transition:background-color 125ms;vertical-align:text-bottom;width:1.2em}.md-typeset .md-tag-icon[href]:focus:before,.md-typeset .md-tag-icon[href]:hover:before{background-color:var(--md-accent-bg-color)}@keyframes pulse{0%{transform:scale(.95)}75%{transform:scale(1)}to{transform:scale(.95)}}:root{--md-annotation-bg-icon:url('data:image/svg+xml;charset=utf-8,');--md-annotation-icon:url('data:image/svg+xml;charset=utf-8,')}.md-tooltip{-webkit-backface-visibility:hidden;backface-visibility:hidden;background-color:var(--md-default-bg-color);border-radius:.1rem;box-shadow:var(--md-shadow-z2);color:var(--md-default-fg-color);font-family:var(--md-text-font-family);left:clamp(var(--md-tooltip-0,0rem) + .8rem,var(--md-tooltip-x),100vw + var(--md-tooltip-0,0rem) + .8rem - var(--md-tooltip-width) - 2 * .8rem);max-width:calc(100vw - 1.6rem);opacity:0;position:absolute;top:var(--md-tooltip-y);transform:translateY(-.4rem);transition:transform 0ms .25s,opacity .25s,z-index .25s;width:var(--md-tooltip-width);z-index:0}.md-tooltip--active{opacity:1;transform:translateY(0);transition:transform .25s cubic-bezier(.1,.7,.1,1),opacity .25s,z-index 0ms;z-index:2}.md-tooltip--inline{font-weight:700;-webkit-user-select:none;user-select:none;width:auto}.md-tooltip--inline:not(.md-tooltip--active){transform:translateY(.2rem) scale(.9)}.md-tooltip--inline .md-tooltip__inner{font-size:.5rem;padding:.2rem .4rem}[hidden]+.md-tooltip--inline{display:none}.focus-visible>.md-tooltip,.md-tooltip:target{outline:var(--md-accent-fg-color) auto}.md-tooltip__inner{font-size:.64rem;padding:.8rem}.md-tooltip__inner.md-typeset>:first-child{margin-top:0}.md-tooltip__inner.md-typeset>:last-child{margin-bottom:0}.md-annotation{font-style:normal;font-weight:400;outline:none;text-align:initial;vertical-align:text-bottom;white-space:normal}[dir=rtl] .md-annotation{direction:rtl}code .md-annotation{font-family:var(--md-code-font-family);font-size:inherit}.md-annotation:not([hidden]){display:inline-block;line-height:1.25}.md-annotation__index{border-radius:.01px;cursor:pointer;display:inline-block;margin-left:.4ch;margin-right:.4ch;outline:none;overflow:hidden;position:relative;-webkit-user-select:none;user-select:none;vertical-align:text-top;z-index:0}.md-annotation .md-annotation__index{transition:z-index .25s}@media screen{.md-annotation__index{width:2.2ch}[data-md-visible]>.md-annotation__index{animation:pulse 2s infinite}.md-annotation__index:before{background:var(--md-default-bg-color);-webkit-mask-image:var(--md-annotation-bg-icon);mask-image:var(--md-annotation-bg-icon)}.md-annotation__index:after,.md-annotation__index:before{content:"";height:2.2ch;-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;position:absolute;top:-.1ch;width:2.2ch;z-index:-1}.md-annotation__index:after{background-color:var(--md-default-fg-color--lighter);-webkit-mask-image:var(--md-annotation-icon);mask-image:var(--md-annotation-icon);transform:scale(1.0001);transition:background-color .25s,transform .25s}.md-tooltip--active+.md-annotation__index:after{transform:rotate(45deg)}.md-tooltip--active+.md-annotation__index:after,:hover>.md-annotation__index:after{background-color:var(--md-accent-fg-color)}}.md-tooltip--active+.md-annotation__index{animation-play-state:paused;transition-duration:0ms;z-index:2}.md-annotation__index [data-md-annotation-id]{display:inline-block}@media print{.md-annotation__index [data-md-annotation-id]{background:var(--md-default-fg-color--lighter);border-radius:2ch;color:var(--md-default-bg-color);font-weight:700;padding:0 .6ch;white-space:nowrap}.md-annotation__index [data-md-annotation-id]:after{content:attr(data-md-annotation-id)}}.md-typeset .md-annotation-list{counter-reset:xxx;list-style:none}.md-typeset .md-annotation-list li{position:relative}[dir=ltr] .md-typeset .md-annotation-list li:before{left:-2.125em}[dir=rtl] .md-typeset .md-annotation-list li:before{right:-2.125em}.md-typeset .md-annotation-list li:before{background:var(--md-default-fg-color--lighter);border-radius:2ch;color:var(--md-default-bg-color);content:counter(xxx);counter-increment:xxx;font-size:.8875em;font-weight:700;height:2ch;line-height:1.25;min-width:2ch;padding:0 .6ch;position:absolute;text-align:center;top:.25em}:root{--md-tooltip-width:20rem;--md-tooltip-tail:0.3rem}.md-tooltip2{-webkit-backface-visibility:hidden;backface-visibility:hidden;color:var(--md-default-fg-color);font-family:var(--md-text-font-family);opacity:0;pointer-events:none;position:absolute;top:calc(var(--md-tooltip-host-y) + var(--md-tooltip-y));transform:translateY(-.4rem);transform-origin:calc(var(--md-tooltip-host-x) + var(--md-tooltip-x)) 0;transition:transform 0ms .25s,opacity .25s,z-index .25s;width:100%;z-index:0}.md-tooltip2:before{border-left:var(--md-tooltip-tail) solid #0000;border-right:var(--md-tooltip-tail) solid #0000;content:"";display:block;left:clamp(1.5 * .8rem,var(--md-tooltip-host-x) + var(--md-tooltip-x) - var(--md-tooltip-tail),100vw - 2 * var(--md-tooltip-tail) - 1.5 * .8rem);position:absolute;z-index:1}.md-tooltip2--top:before{border-top:var(--md-tooltip-tail) solid var(--md-default-bg-color);bottom:calc(var(--md-tooltip-tail)*-1 + .025rem);filter:drop-shadow(0 1px 0 hsla(0,0%,0%,.05))}.md-tooltip2--bottom:before{border-bottom:var(--md-tooltip-tail) solid var(--md-default-bg-color);filter:drop-shadow(0 -1px 0 hsla(0,0%,0%,.05));top:calc(var(--md-tooltip-tail)*-1 + .025rem)}.md-tooltip2--active{opacity:1;transform:translateY(0);transition:transform .4s cubic-bezier(0,1,.5,1),opacity .25s,z-index 0ms;z-index:2}.md-tooltip2__inner{scrollbar-gutter:stable;background-color:var(--md-default-bg-color);border-radius:.1rem;box-shadow:var(--md-shadow-z2);left:clamp(.8rem,var(--md-tooltip-host-x) - .8rem,100vw - var(--md-tooltip-width) - .8rem);max-height:40vh;max-width:calc(100vw - 1.6rem);position:relative;scrollbar-width:thin}.md-tooltip2__inner::-webkit-scrollbar{height:.2rem;width:.2rem}.md-tooltip2__inner::-webkit-scrollbar-thumb{background-color:var(--md-default-fg-color--lighter)}.md-tooltip2__inner::-webkit-scrollbar-thumb:hover{background-color:var(--md-accent-fg-color)}[role=dialog]>.md-tooltip2__inner{font-size:.64rem;overflow:auto;padding:0 .8rem;pointer-events:auto;width:var(--md-tooltip-width)}[role=dialog]>.md-tooltip2__inner:after,[role=dialog]>.md-tooltip2__inner:before{content:"";display:block;height:.8rem;position:sticky;width:100%;z-index:10}[role=dialog]>.md-tooltip2__inner:before{background:linear-gradient(var(--md-default-bg-color),#0000 75%);top:0}[role=dialog]>.md-tooltip2__inner:after{background:linear-gradient(#0000,var(--md-default-bg-color) 75%);bottom:0}[role=tooltip]>.md-tooltip2__inner{font-size:.5rem;font-weight:700;left:clamp(.8rem,var(--md-tooltip-host-x) + var(--md-tooltip-x) - var(--md-tooltip-width)/2,100vw - var(--md-tooltip-width) - .8rem);max-width:min(100vw - 2 * .8rem,400px);padding:.2rem .4rem;-webkit-user-select:none;user-select:none;width:-moz-fit-content;width:fit-content}.md-tooltip2__inner.md-typeset>:first-child{margin-top:0}.md-tooltip2__inner.md-typeset>:last-child{margin-bottom:0}[dir=ltr] .md-top{margin-left:50%}[dir=rtl] .md-top{margin-right:50%}.md-top{background-color:var(--md-default-bg-color);border-radius:1.6rem;box-shadow:var(--md-shadow-z2);color:var(--md-default-fg-color--light);cursor:pointer;display:block;font-size:.7rem;outline:none;padding:.4rem .8rem;position:fixed;top:3.2rem;transform:translate(-50%);transition:color 125ms,background-color 125ms,transform 125ms cubic-bezier(.4,0,.2,1),opacity 125ms;z-index:2}@media print{.md-top{display:none}}[dir=rtl] .md-top{transform:translate(50%)}.md-top[hidden]{opacity:0;pointer-events:none;transform:translate(-50%,.2rem);transition-duration:0ms}[dir=rtl] .md-top[hidden]{transform:translate(50%,.2rem)}.md-top:focus,.md-top:hover{background-color:var(--md-accent-fg-color);color:var(--md-accent-bg-color)}.md-top svg{display:inline-block;vertical-align:-.5em}@keyframes hoverfix{0%{pointer-events:none}}:root{--md-version-icon:url('data:image/svg+xml;charset=utf-8,')}.md-version{flex-shrink:0;font-size:.8rem;height:2.4rem}[dir=ltr] .md-version__current{margin-left:1.4rem;margin-right:.4rem}[dir=rtl] .md-version__current{margin-left:.4rem;margin-right:1.4rem}.md-version__current{color:inherit;cursor:pointer;outline:none;position:relative;top:.05rem}[dir=ltr] .md-version__current:after{margin-left:.4rem}[dir=rtl] .md-version__current:after{margin-right:.4rem}.md-version__current:after{background-color:currentcolor;content:"";display:inline-block;height:.6rem;-webkit-mask-image:var(--md-version-icon);mask-image:var(--md-version-icon);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;width:.4rem}.md-version__alias{margin-left:.3rem;opacity:.7}.md-version__list{background-color:var(--md-default-bg-color);border-radius:.1rem;box-shadow:var(--md-shadow-z2);color:var(--md-default-fg-color);list-style-type:none;margin:.2rem .8rem;max-height:0;opacity:0;overflow:auto;padding:0;position:absolute;scroll-snap-type:y mandatory;top:.15rem;transition:max-height 0ms .5s,opacity .25s .25s;z-index:3}.md-version:focus-within .md-version__list,.md-version:hover .md-version__list{max-height:10rem;opacity:1;transition:max-height 0ms,opacity .25s}@media (hover:none),(pointer:coarse){.md-version:hover .md-version__list{animation:hoverfix .25s forwards}.md-version:focus-within .md-version__list{animation:none}}.md-version__item{line-height:1.8rem}[dir=ltr] .md-version__link{padding-left:.6rem;padding-right:1.2rem}[dir=rtl] .md-version__link{padding-left:1.2rem;padding-right:.6rem}.md-version__link{cursor:pointer;display:block;outline:none;scroll-snap-align:start;transition:color .25s,background-color .25s;white-space:nowrap;width:100%}.md-version__link:focus,.md-version__link:hover{color:var(--md-accent-fg-color)}.md-version__link:focus{background-color:var(--md-default-fg-color--lightest)}:root{--md-admonition-icon--note:url('data:image/svg+xml;charset=utf-8,');--md-admonition-icon--abstract:url('data:image/svg+xml;charset=utf-8,');--md-admonition-icon--info:url('data:image/svg+xml;charset=utf-8,');--md-admonition-icon--tip:url('data:image/svg+xml;charset=utf-8,');--md-admonition-icon--success:url('data:image/svg+xml;charset=utf-8,');--md-admonition-icon--question:url('data:image/svg+xml;charset=utf-8,');--md-admonition-icon--warning:url('data:image/svg+xml;charset=utf-8,');--md-admonition-icon--failure:url('data:image/svg+xml;charset=utf-8,');--md-admonition-icon--danger:url('data:image/svg+xml;charset=utf-8,');--md-admonition-icon--bug:url('data:image/svg+xml;charset=utf-8,');--md-admonition-icon--example:url('data:image/svg+xml;charset=utf-8,');--md-admonition-icon--quote:url('data:image/svg+xml;charset=utf-8,')}.md-typeset .admonition,.md-typeset details{background-color:var(--md-admonition-bg-color);border:.075rem solid #448aff;border-radius:.2rem;box-shadow:var(--md-shadow-z1);color:var(--md-admonition-fg-color);display:flow-root;font-size:.64rem;margin:1.5625em 0;padding:0 .6rem;page-break-inside:avoid;transition:box-shadow 125ms}@media print{.md-typeset .admonition,.md-typeset details{box-shadow:none}}.md-typeset .admonition:focus-within,.md-typeset details:focus-within{box-shadow:0 0 0 .2rem #448aff1a}.md-typeset .admonition>*,.md-typeset details>*{box-sizing:border-box}.md-typeset .admonition .admonition,.md-typeset .admonition details,.md-typeset details .admonition,.md-typeset details details{margin-bottom:1em;margin-top:1em}.md-typeset .admonition .md-typeset__scrollwrap,.md-typeset details .md-typeset__scrollwrap{margin:1em -.6rem}.md-typeset .admonition .md-typeset__table,.md-typeset details .md-typeset__table{padding:0 .6rem}.md-typeset .admonition>.tabbed-set:only-child,.md-typeset details>.tabbed-set:only-child{margin-top:0}html .md-typeset .admonition>:last-child,html .md-typeset details>:last-child{margin-bottom:.6rem}[dir=ltr] .md-typeset .admonition-title,[dir=ltr] .md-typeset summary{padding-left:2rem;padding-right:.6rem}[dir=rtl] .md-typeset .admonition-title,[dir=rtl] .md-typeset summary{padding-left:.6rem;padding-right:2rem}[dir=ltr] .md-typeset .admonition-title,[dir=ltr] .md-typeset summary{border-left-width:.2rem}[dir=rtl] .md-typeset .admonition-title,[dir=rtl] .md-typeset summary{border-right-width:.2rem}[dir=ltr] .md-typeset .admonition-title,[dir=ltr] .md-typeset summary{border-top-left-radius:.1rem}[dir=ltr] .md-typeset .admonition-title,[dir=ltr] .md-typeset summary,[dir=rtl] .md-typeset .admonition-title,[dir=rtl] .md-typeset summary{border-top-right-radius:.1rem}[dir=rtl] .md-typeset .admonition-title,[dir=rtl] .md-typeset summary{border-top-left-radius:.1rem}.md-typeset .admonition-title,.md-typeset summary{background-color:#448aff1a;border:none;font-weight:700;margin:0 -.6rem;padding-bottom:.4rem;padding-top:.4rem;position:relative}html .md-typeset .admonition-title:last-child,html .md-typeset summary:last-child{margin-bottom:0}[dir=ltr] .md-typeset .admonition-title:before,[dir=ltr] .md-typeset summary:before{left:.6rem}[dir=rtl] .md-typeset .admonition-title:before,[dir=rtl] .md-typeset summary:before{right:.6rem}.md-typeset .admonition-title:before,.md-typeset summary:before{background-color:#448aff;content:"";height:1rem;-webkit-mask-image:var(--md-admonition-icon--note);mask-image:var(--md-admonition-icon--note);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;position:absolute;top:.625em;width:1rem}.md-typeset .admonition-title code,.md-typeset summary code{box-shadow:0 0 0 .05rem var(--md-default-fg-color--lightest)}.md-typeset .admonition.note,.md-typeset details.note{border-color:#448aff}.md-typeset .admonition.note:focus-within,.md-typeset details.note:focus-within{box-shadow:0 0 0 .2rem #448aff1a}.md-typeset .note>.admonition-title,.md-typeset .note>summary{background-color:#448aff1a}.md-typeset .note>.admonition-title:before,.md-typeset .note>summary:before{background-color:#448aff;-webkit-mask-image:var(--md-admonition-icon--note);mask-image:var(--md-admonition-icon--note)}.md-typeset .note>.admonition-title:after,.md-typeset .note>summary:after{color:#448aff}.md-typeset .admonition.abstract,.md-typeset details.abstract{border-color:#00b0ff}.md-typeset .admonition.abstract:focus-within,.md-typeset details.abstract:focus-within{box-shadow:0 0 0 .2rem #00b0ff1a}.md-typeset .abstract>.admonition-title,.md-typeset .abstract>summary{background-color:#00b0ff1a}.md-typeset .abstract>.admonition-title:before,.md-typeset .abstract>summary:before{background-color:#00b0ff;-webkit-mask-image:var(--md-admonition-icon--abstract);mask-image:var(--md-admonition-icon--abstract)}.md-typeset .abstract>.admonition-title:after,.md-typeset .abstract>summary:after{color:#00b0ff}.md-typeset .admonition.info,.md-typeset details.info{border-color:#00b8d4}.md-typeset .admonition.info:focus-within,.md-typeset details.info:focus-within{box-shadow:0 0 0 .2rem #00b8d41a}.md-typeset .info>.admonition-title,.md-typeset .info>summary{background-color:#00b8d41a}.md-typeset .info>.admonition-title:before,.md-typeset .info>summary:before{background-color:#00b8d4;-webkit-mask-image:var(--md-admonition-icon--info);mask-image:var(--md-admonition-icon--info)}.md-typeset .info>.admonition-title:after,.md-typeset .info>summary:after{color:#00b8d4}.md-typeset .admonition.tip,.md-typeset details.tip{border-color:#00bfa5}.md-typeset .admonition.tip:focus-within,.md-typeset details.tip:focus-within{box-shadow:0 0 0 .2rem #00bfa51a}.md-typeset .tip>.admonition-title,.md-typeset .tip>summary{background-color:#00bfa51a}.md-typeset .tip>.admonition-title:before,.md-typeset .tip>summary:before{background-color:#00bfa5;-webkit-mask-image:var(--md-admonition-icon--tip);mask-image:var(--md-admonition-icon--tip)}.md-typeset .tip>.admonition-title:after,.md-typeset .tip>summary:after{color:#00bfa5}.md-typeset .admonition.success,.md-typeset details.success{border-color:#00c853}.md-typeset .admonition.success:focus-within,.md-typeset details.success:focus-within{box-shadow:0 0 0 .2rem #00c8531a}.md-typeset .success>.admonition-title,.md-typeset .success>summary{background-color:#00c8531a}.md-typeset .success>.admonition-title:before,.md-typeset .success>summary:before{background-color:#00c853;-webkit-mask-image:var(--md-admonition-icon--success);mask-image:var(--md-admonition-icon--success)}.md-typeset .success>.admonition-title:after,.md-typeset .success>summary:after{color:#00c853}.md-typeset .admonition.question,.md-typeset details.question{border-color:#64dd17}.md-typeset .admonition.question:focus-within,.md-typeset details.question:focus-within{box-shadow:0 0 0 .2rem #64dd171a}.md-typeset .question>.admonition-title,.md-typeset .question>summary{background-color:#64dd171a}.md-typeset .question>.admonition-title:before,.md-typeset .question>summary:before{background-color:#64dd17;-webkit-mask-image:var(--md-admonition-icon--question);mask-image:var(--md-admonition-icon--question)}.md-typeset .question>.admonition-title:after,.md-typeset .question>summary:after{color:#64dd17}.md-typeset .admonition.warning,.md-typeset details.warning{border-color:#ff9100}.md-typeset .admonition.warning:focus-within,.md-typeset details.warning:focus-within{box-shadow:0 0 0 .2rem #ff91001a}.md-typeset .warning>.admonition-title,.md-typeset .warning>summary{background-color:#ff91001a}.md-typeset .warning>.admonition-title:before,.md-typeset .warning>summary:before{background-color:#ff9100;-webkit-mask-image:var(--md-admonition-icon--warning);mask-image:var(--md-admonition-icon--warning)}.md-typeset .warning>.admonition-title:after,.md-typeset .warning>summary:after{color:#ff9100}.md-typeset .admonition.failure,.md-typeset details.failure{border-color:#ff5252}.md-typeset .admonition.failure:focus-within,.md-typeset details.failure:focus-within{box-shadow:0 0 0 .2rem #ff52521a}.md-typeset .failure>.admonition-title,.md-typeset .failure>summary{background-color:#ff52521a}.md-typeset .failure>.admonition-title:before,.md-typeset .failure>summary:before{background-color:#ff5252;-webkit-mask-image:var(--md-admonition-icon--failure);mask-image:var(--md-admonition-icon--failure)}.md-typeset .failure>.admonition-title:after,.md-typeset .failure>summary:after{color:#ff5252}.md-typeset .admonition.danger,.md-typeset details.danger{border-color:#ff1744}.md-typeset .admonition.danger:focus-within,.md-typeset details.danger:focus-within{box-shadow:0 0 0 .2rem #ff17441a}.md-typeset .danger>.admonition-title,.md-typeset .danger>summary{background-color:#ff17441a}.md-typeset .danger>.admonition-title:before,.md-typeset .danger>summary:before{background-color:#ff1744;-webkit-mask-image:var(--md-admonition-icon--danger);mask-image:var(--md-admonition-icon--danger)}.md-typeset .danger>.admonition-title:after,.md-typeset .danger>summary:after{color:#ff1744}.md-typeset .admonition.bug,.md-typeset details.bug{border-color:#f50057}.md-typeset .admonition.bug:focus-within,.md-typeset details.bug:focus-within{box-shadow:0 0 0 .2rem #f500571a}.md-typeset .bug>.admonition-title,.md-typeset .bug>summary{background-color:#f500571a}.md-typeset .bug>.admonition-title:before,.md-typeset .bug>summary:before{background-color:#f50057;-webkit-mask-image:var(--md-admonition-icon--bug);mask-image:var(--md-admonition-icon--bug)}.md-typeset .bug>.admonition-title:after,.md-typeset .bug>summary:after{color:#f50057}.md-typeset .admonition.example,.md-typeset details.example{border-color:#7c4dff}.md-typeset .admonition.example:focus-within,.md-typeset details.example:focus-within{box-shadow:0 0 0 .2rem #7c4dff1a}.md-typeset .example>.admonition-title,.md-typeset .example>summary{background-color:#7c4dff1a}.md-typeset .example>.admonition-title:before,.md-typeset .example>summary:before{background-color:#7c4dff;-webkit-mask-image:var(--md-admonition-icon--example);mask-image:var(--md-admonition-icon--example)}.md-typeset .example>.admonition-title:after,.md-typeset .example>summary:after{color:#7c4dff}.md-typeset .admonition.quote,.md-typeset details.quote{border-color:#9e9e9e}.md-typeset .admonition.quote:focus-within,.md-typeset details.quote:focus-within{box-shadow:0 0 0 .2rem #9e9e9e1a}.md-typeset .quote>.admonition-title,.md-typeset .quote>summary{background-color:#9e9e9e1a}.md-typeset .quote>.admonition-title:before,.md-typeset .quote>summary:before{background-color:#9e9e9e;-webkit-mask-image:var(--md-admonition-icon--quote);mask-image:var(--md-admonition-icon--quote)}.md-typeset .quote>.admonition-title:after,.md-typeset .quote>summary:after{color:#9e9e9e}:root{--md-footnotes-icon:url('data:image/svg+xml;charset=utf-8,')}.md-typeset .footnote{color:var(--md-default-fg-color--light);font-size:.64rem}[dir=ltr] .md-typeset .footnote>ol{margin-left:0}[dir=rtl] .md-typeset .footnote>ol{margin-right:0}.md-typeset .footnote>ol>li{transition:color 125ms}.md-typeset .footnote>ol>li:target{color:var(--md-default-fg-color)}.md-typeset .footnote>ol>li:focus-within .footnote-backref{opacity:1;transform:translateX(0);transition:none}.md-typeset .footnote>ol>li:hover .footnote-backref,.md-typeset .footnote>ol>li:target .footnote-backref{opacity:1;transform:translateX(0)}.md-typeset .footnote>ol>li>:first-child{margin-top:0}.md-typeset .footnote-ref{font-size:.75em;font-weight:700}html .md-typeset .footnote-ref{outline-offset:.1rem}.md-typeset [id^="fnref:"]:target>.footnote-ref{outline:auto}.md-typeset .footnote-backref{color:var(--md-typeset-a-color);display:inline-block;font-size:0;opacity:0;transform:translateX(.25rem);transition:color .25s,transform .25s .25s,opacity 125ms .25s;vertical-align:text-bottom}@media print{.md-typeset .footnote-backref{color:var(--md-typeset-a-color);opacity:1;transform:translateX(0)}}[dir=rtl] .md-typeset .footnote-backref{transform:translateX(-.25rem)}.md-typeset .footnote-backref:hover{color:var(--md-accent-fg-color)}.md-typeset .footnote-backref:before{background-color:currentcolor;content:"";display:inline-block;height:.8rem;-webkit-mask-image:var(--md-footnotes-icon);mask-image:var(--md-footnotes-icon);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;width:.8rem}[dir=rtl] .md-typeset .footnote-backref:before svg{transform:scaleX(-1)}[dir=ltr] .md-typeset .headerlink{margin-left:.5rem}[dir=rtl] .md-typeset .headerlink{margin-right:.5rem}.md-typeset .headerlink{color:var(--md-default-fg-color--lighter);display:inline-block;opacity:0;transition:color .25s,opacity 125ms}@media print{.md-typeset .headerlink{display:none}}.md-typeset .headerlink:focus,.md-typeset :hover>.headerlink,.md-typeset :target>.headerlink{opacity:1;transition:color .25s,opacity 125ms}.md-typeset .headerlink:focus,.md-typeset .headerlink:hover,.md-typeset :target>.headerlink{color:var(--md-accent-fg-color)}.md-typeset :target{--md-scroll-margin:3.6rem;--md-scroll-offset:0rem;scroll-margin-top:calc(var(--md-scroll-margin) - var(--md-scroll-offset))}@media screen and (min-width:76.25em){.md-header--lifted~.md-container .md-typeset :target{--md-scroll-margin:6rem}}.md-typeset h1:target,.md-typeset h2:target,.md-typeset h3:target{--md-scroll-offset:0.2rem}.md-typeset h4:target{--md-scroll-offset:0.15rem}.md-typeset div.arithmatex{overflow:auto}@media screen and (max-width:44.984375em){.md-typeset div.arithmatex{margin:0 -.8rem}.md-typeset div.arithmatex>*{width:min-content}}.md-typeset div.arithmatex>*{margin-left:auto!important;margin-right:auto!important;padding:0 .8rem;touch-action:auto}.md-typeset div.arithmatex>* mjx-container{margin:0!important}.md-typeset div.arithmatex mjx-assistive-mml{height:0}.md-typeset del.critic{background-color:var(--md-typeset-del-color)}.md-typeset del.critic,.md-typeset ins.critic{-webkit-box-decoration-break:clone;box-decoration-break:clone}.md-typeset ins.critic{background-color:var(--md-typeset-ins-color)}.md-typeset .critic.comment{-webkit-box-decoration-break:clone;box-decoration-break:clone;color:var(--md-code-hl-comment-color)}.md-typeset .critic.comment:before{content:"/* "}.md-typeset .critic.comment:after{content:" */"}.md-typeset .critic.block{box-shadow:none;display:block;margin:1em 0;overflow:auto;padding-left:.8rem;padding-right:.8rem}.md-typeset .critic.block>:first-child{margin-top:.5em}.md-typeset .critic.block>:last-child{margin-bottom:.5em}:root{--md-details-icon:url('data:image/svg+xml;charset=utf-8,')}.md-typeset details{display:flow-root;overflow:visible;padding-top:0}.md-typeset details[open]>summary:after{transform:rotate(90deg)}.md-typeset details:not([open]){box-shadow:none;padding-bottom:0}.md-typeset details:not([open])>summary{border-radius:.1rem}[dir=ltr] .md-typeset summary{padding-right:1.8rem}[dir=rtl] .md-typeset summary{padding-left:1.8rem}[dir=ltr] .md-typeset summary{border-top-left-radius:.1rem}[dir=ltr] .md-typeset summary,[dir=rtl] .md-typeset summary{border-top-right-radius:.1rem}[dir=rtl] .md-typeset summary{border-top-left-radius:.1rem}.md-typeset summary{cursor:pointer;display:block;min-height:1rem;overflow:hidden}.md-typeset summary.focus-visible{outline-color:var(--md-accent-fg-color);outline-offset:.2rem}.md-typeset summary:not(.focus-visible){-webkit-tap-highlight-color:transparent;outline:none}[dir=ltr] .md-typeset summary:after{right:.4rem}[dir=rtl] .md-typeset summary:after{left:.4rem}.md-typeset summary:after{background-color:currentcolor;content:"";height:1rem;-webkit-mask-image:var(--md-details-icon);mask-image:var(--md-details-icon);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;position:absolute;top:.625em;transform:rotate(0deg);transition:transform .25s;width:1rem}[dir=rtl] .md-typeset summary:after{transform:rotate(180deg)}.md-typeset summary::marker{display:none}.md-typeset summary::-webkit-details-marker{display:none}.md-typeset .emojione,.md-typeset .gemoji,.md-typeset .twemoji{--md-icon-size:1.125em;display:inline-flex;height:var(--md-icon-size);vertical-align:text-top}.md-typeset .emojione svg,.md-typeset .gemoji svg,.md-typeset .twemoji svg{fill:currentcolor;max-height:100%;width:var(--md-icon-size)}.md-typeset .lg,.md-typeset .xl,.md-typeset .xxl,.md-typeset .xxxl{vertical-align:text-bottom}.md-typeset .middle{vertical-align:middle}.md-typeset .lg{--md-icon-size:1.5em}.md-typeset .xl{--md-icon-size:2.25em}.md-typeset .xxl{--md-icon-size:3em}.md-typeset .xxxl{--md-icon-size:4em}.highlight .o,.highlight .ow{color:var(--md-code-hl-operator-color)}.highlight .p{color:var(--md-code-hl-punctuation-color)}.highlight .cpf,.highlight .l,.highlight .s,.highlight .s1,.highlight .s2,.highlight .sb,.highlight .sc,.highlight .si,.highlight .ss{color:var(--md-code-hl-string-color)}.highlight .cp,.highlight .se,.highlight .sh,.highlight .sr,.highlight .sx{color:var(--md-code-hl-special-color)}.highlight .il,.highlight .m,.highlight .mb,.highlight .mf,.highlight .mh,.highlight .mi,.highlight .mo{color:var(--md-code-hl-number-color)}.highlight .k,.highlight .kd,.highlight .kn,.highlight .kp,.highlight .kr,.highlight .kt{color:var(--md-code-hl-keyword-color)}.highlight .kc,.highlight .n{color:var(--md-code-hl-name-color)}.highlight .bp,.highlight .nb,.highlight .no{color:var(--md-code-hl-constant-color)}.highlight .nc,.highlight .ne,.highlight .nf,.highlight .nn{color:var(--md-code-hl-function-color)}.highlight .nd,.highlight .ni,.highlight .nl,.highlight .nt{color:var(--md-code-hl-keyword-color)}.highlight .c,.highlight .c1,.highlight .ch,.highlight .cm,.highlight .cs,.highlight .sd{color:var(--md-code-hl-comment-color)}.highlight .na,.highlight .nv,.highlight .vc,.highlight .vg,.highlight .vi{color:var(--md-code-hl-variable-color)}.highlight .ge,.highlight .gh,.highlight .go,.highlight .gp,.highlight .gr,.highlight .gs,.highlight .gt,.highlight .gu{color:var(--md-code-hl-generic-color)}.highlight .gd,.highlight .gi{border-radius:.1rem;margin:0 -.125em;padding:0 .125em}.highlight .gd{background-color:var(--md-typeset-del-color)}.highlight .gi{background-color:var(--md-typeset-ins-color)}.highlight .hll{background-color:var(--md-code-hl-color--light);box-shadow:2px 0 0 0 var(--md-code-hl-color) inset;display:block;margin:0 -1.1764705882em;padding:0 1.1764705882em}.highlight span.filename{background-color:var(--md-code-bg-color);border-bottom:.05rem solid var(--md-default-fg-color--lightest);border-top-left-radius:.1rem;border-top-right-radius:.1rem;display:flow-root;font-size:.85em;font-weight:700;margin-top:1em;padding:.6617647059em 1.1764705882em;position:relative}.highlight span.filename+pre{margin-top:0}.highlight span.filename+pre>code{border-top-left-radius:0;border-top-right-radius:0}.highlight [data-linenos]:before{background-color:var(--md-code-bg-color);box-shadow:-.05rem 0 var(--md-default-fg-color--lightest) inset;color:var(--md-default-fg-color--light);content:attr(data-linenos);float:left;left:-1.1764705882em;margin-left:-1.1764705882em;margin-right:1.1764705882em;padding-left:1.1764705882em;position:sticky;-webkit-user-select:none;user-select:none;z-index:3}.highlight code a[id]{position:absolute;visibility:hidden}.highlight code[data-md-copying]{display:initial}.highlight code[data-md-copying] .hll{display:contents}.highlight code[data-md-copying] .md-annotation{display:none}.highlighttable{display:flow-root}.highlighttable tbody,.highlighttable td{display:block;padding:0}.highlighttable tr{display:flex}.highlighttable pre{margin:0}.highlighttable th.filename{flex-grow:1;padding:0;text-align:left}.highlighttable th.filename span.filename{margin-top:0}.highlighttable .linenos{background-color:var(--md-code-bg-color);border-bottom-left-radius:.1rem;border-top-left-radius:.1rem;font-size:.85em;padding:.7720588235em 0 .7720588235em 1.1764705882em;-webkit-user-select:none;user-select:none}.highlighttable .linenodiv{box-shadow:-.05rem 0 var(--md-default-fg-color--lightest) inset}.highlighttable .linenodiv pre{color:var(--md-default-fg-color--light);text-align:right}.highlighttable .linenodiv span[class]{padding-right:.5882352941em}.highlighttable .code{flex:1;min-width:0}.linenodiv a{color:inherit}.md-typeset .highlighttable{direction:ltr;margin:1em 0}.md-typeset .highlighttable>tbody>tr>.code>div>pre>code{border-bottom-left-radius:0;border-top-left-radius:0}.md-typeset .highlight+.result{border:.05rem solid var(--md-code-bg-color);border-bottom-left-radius:.1rem;border-bottom-right-radius:.1rem;border-top-width:.1rem;margin-top:-1.125em;overflow:visible;padding:0 1em}.md-typeset .highlight+.result:after{clear:both;content:"";display:block}@media screen and (max-width:44.984375em){.md-content__inner>.highlight{margin:1em -.8rem}.md-content__inner>.highlight>.filename,.md-content__inner>.highlight>.highlighttable>tbody>tr>.code>div>pre>code,.md-content__inner>.highlight>.highlighttable>tbody>tr>.filename span.filename,.md-content__inner>.highlight>.highlighttable>tbody>tr>.linenos,.md-content__inner>.highlight>pre>code{border-radius:0}.md-content__inner>.highlight+.result{border-left-width:0;border-radius:0;border-right-width:0;margin-left:-.8rem;margin-right:-.8rem}}.md-typeset .keys kbd:after,.md-typeset .keys kbd:before{-moz-osx-font-smoothing:initial;-webkit-font-smoothing:initial;color:inherit;margin:0;position:relative}.md-typeset .keys span{color:var(--md-default-fg-color--light);padding:0 .2em}.md-typeset .keys .key-alt:before,.md-typeset .keys .key-left-alt:before,.md-typeset .keys .key-right-alt:before{content:"⎇";padding-right:.4em}.md-typeset .keys .key-command:before,.md-typeset .keys .key-left-command:before,.md-typeset .keys .key-right-command:before{content:"⌘";padding-right:.4em}.md-typeset .keys .key-control:before,.md-typeset .keys .key-left-control:before,.md-typeset .keys .key-right-control:before{content:"⌃";padding-right:.4em}.md-typeset .keys .key-left-meta:before,.md-typeset .keys .key-meta:before,.md-typeset .keys .key-right-meta:before{content:"◆";padding-right:.4em}.md-typeset .keys .key-left-option:before,.md-typeset .keys .key-option:before,.md-typeset .keys .key-right-option:before{content:"⌥";padding-right:.4em}.md-typeset .keys .key-left-shift:before,.md-typeset .keys .key-right-shift:before,.md-typeset .keys .key-shift:before{content:"⇧";padding-right:.4em}.md-typeset .keys .key-left-super:before,.md-typeset .keys .key-right-super:before,.md-typeset .keys .key-super:before{content:"❖";padding-right:.4em}.md-typeset .keys .key-left-windows:before,.md-typeset .keys .key-right-windows:before,.md-typeset .keys .key-windows:before{content:"⊞";padding-right:.4em}.md-typeset .keys .key-arrow-down:before{content:"↓";padding-right:.4em}.md-typeset .keys .key-arrow-left:before{content:"←";padding-right:.4em}.md-typeset .keys .key-arrow-right:before{content:"→";padding-right:.4em}.md-typeset .keys .key-arrow-up:before{content:"↑";padding-right:.4em}.md-typeset .keys .key-backspace:before{content:"⌫";padding-right:.4em}.md-typeset .keys .key-backtab:before{content:"⇤";padding-right:.4em}.md-typeset .keys .key-caps-lock:before{content:"⇪";padding-right:.4em}.md-typeset .keys .key-clear:before{content:"⌧";padding-right:.4em}.md-typeset .keys .key-context-menu:before{content:"☰";padding-right:.4em}.md-typeset .keys .key-delete:before{content:"⌦";padding-right:.4em}.md-typeset .keys .key-eject:before{content:"⏏";padding-right:.4em}.md-typeset .keys .key-end:before{content:"⤓";padding-right:.4em}.md-typeset .keys .key-escape:before{content:"⎋";padding-right:.4em}.md-typeset .keys .key-home:before{content:"⤒";padding-right:.4em}.md-typeset .keys .key-insert:before{content:"⎀";padding-right:.4em}.md-typeset .keys .key-page-down:before{content:"⇟";padding-right:.4em}.md-typeset .keys .key-page-up:before{content:"⇞";padding-right:.4em}.md-typeset .keys .key-print-screen:before{content:"⎙";padding-right:.4em}.md-typeset .keys .key-tab:after{content:"⇥";padding-left:.4em}.md-typeset .keys .key-num-enter:after{content:"⌤";padding-left:.4em}.md-typeset .keys .key-enter:after{content:"⏎";padding-left:.4em}:root{--md-tabbed-icon--prev:url('data:image/svg+xml;charset=utf-8,');--md-tabbed-icon--next:url('data:image/svg+xml;charset=utf-8,')}.md-typeset .tabbed-set{border-radius:.1rem;display:flex;flex-flow:column wrap;margin:1em 0;position:relative}.md-typeset .tabbed-set>input{height:0;opacity:0;position:absolute;width:0}.md-typeset .tabbed-set>input:target{--md-scroll-offset:0.625em}.md-typeset .tabbed-set>input.focus-visible~.tabbed-labels:before{background-color:var(--md-accent-fg-color)}.md-typeset .tabbed-labels{-ms-overflow-style:none;box-shadow:0 -.05rem var(--md-default-fg-color--lightest) inset;display:flex;max-width:100%;overflow:auto;scrollbar-width:none}@media print{.md-typeset .tabbed-labels{display:contents}}@media screen{.js .md-typeset .tabbed-labels{position:relative}.js .md-typeset .tabbed-labels:before{background:var(--md-default-fg-color);bottom:0;content:"";display:block;height:2px;left:0;position:absolute;transform:translateX(var(--md-indicator-x));transition:width 225ms,background-color .25s,transform .25s;transition-timing-function:cubic-bezier(.4,0,.2,1);width:var(--md-indicator-width)}}.md-typeset .tabbed-labels::-webkit-scrollbar{display:none}.md-typeset .tabbed-labels>label{border-bottom:.1rem solid #0000;border-radius:.1rem .1rem 0 0;color:var(--md-default-fg-color--light);cursor:pointer;flex-shrink:0;font-size:.64rem;font-weight:700;padding:.78125em 1.25em .625em;scroll-margin-inline-start:1rem;transition:background-color .25s,color .25s;white-space:nowrap;width:auto}@media print{.md-typeset .tabbed-labels>label:first-child{order:1}.md-typeset .tabbed-labels>label:nth-child(2){order:2}.md-typeset .tabbed-labels>label:nth-child(3){order:3}.md-typeset .tabbed-labels>label:nth-child(4){order:4}.md-typeset .tabbed-labels>label:nth-child(5){order:5}.md-typeset .tabbed-labels>label:nth-child(6){order:6}.md-typeset .tabbed-labels>label:nth-child(7){order:7}.md-typeset .tabbed-labels>label:nth-child(8){order:8}.md-typeset .tabbed-labels>label:nth-child(9){order:9}.md-typeset .tabbed-labels>label:nth-child(10){order:10}.md-typeset .tabbed-labels>label:nth-child(11){order:11}.md-typeset .tabbed-labels>label:nth-child(12){order:12}.md-typeset .tabbed-labels>label:nth-child(13){order:13}.md-typeset .tabbed-labels>label:nth-child(14){order:14}.md-typeset .tabbed-labels>label:nth-child(15){order:15}.md-typeset .tabbed-labels>label:nth-child(16){order:16}.md-typeset .tabbed-labels>label:nth-child(17){order:17}.md-typeset .tabbed-labels>label:nth-child(18){order:18}.md-typeset .tabbed-labels>label:nth-child(19){order:19}.md-typeset .tabbed-labels>label:nth-child(20){order:20}}.md-typeset .tabbed-labels>label:hover{color:var(--md-default-fg-color)}.md-typeset .tabbed-labels>label>[href]:first-child{color:inherit}.md-typeset .tabbed-labels--linked>label{padding:0}.md-typeset .tabbed-labels--linked>label>a{display:block;padding:.78125em 1.25em .625em}.md-typeset .tabbed-content{width:100%}@media print{.md-typeset .tabbed-content{display:contents}}.md-typeset .tabbed-block{display:none}@media print{.md-typeset .tabbed-block{display:block}.md-typeset .tabbed-block:first-child{order:1}.md-typeset .tabbed-block:nth-child(2){order:2}.md-typeset .tabbed-block:nth-child(3){order:3}.md-typeset .tabbed-block:nth-child(4){order:4}.md-typeset .tabbed-block:nth-child(5){order:5}.md-typeset .tabbed-block:nth-child(6){order:6}.md-typeset .tabbed-block:nth-child(7){order:7}.md-typeset .tabbed-block:nth-child(8){order:8}.md-typeset .tabbed-block:nth-child(9){order:9}.md-typeset .tabbed-block:nth-child(10){order:10}.md-typeset .tabbed-block:nth-child(11){order:11}.md-typeset .tabbed-block:nth-child(12){order:12}.md-typeset .tabbed-block:nth-child(13){order:13}.md-typeset .tabbed-block:nth-child(14){order:14}.md-typeset .tabbed-block:nth-child(15){order:15}.md-typeset .tabbed-block:nth-child(16){order:16}.md-typeset .tabbed-block:nth-child(17){order:17}.md-typeset .tabbed-block:nth-child(18){order:18}.md-typeset .tabbed-block:nth-child(19){order:19}.md-typeset .tabbed-block:nth-child(20){order:20}}.md-typeset .tabbed-block>.highlight:first-child>pre,.md-typeset .tabbed-block>pre:first-child{margin:0}.md-typeset .tabbed-block>.highlight:first-child>pre>code,.md-typeset .tabbed-block>pre:first-child>code{border-top-left-radius:0;border-top-right-radius:0}.md-typeset .tabbed-block>.highlight:first-child>.filename{border-top-left-radius:0;border-top-right-radius:0;margin:0}.md-typeset .tabbed-block>.highlight:first-child>.highlighttable{margin:0}.md-typeset .tabbed-block>.highlight:first-child>.highlighttable>tbody>tr>.filename span.filename,.md-typeset .tabbed-block>.highlight:first-child>.highlighttable>tbody>tr>.linenos{border-top-left-radius:0;border-top-right-radius:0;margin:0}.md-typeset .tabbed-block>.highlight:first-child>.highlighttable>tbody>tr>.code>div>pre>code{border-top-left-radius:0;border-top-right-radius:0}.md-typeset .tabbed-block>.highlight:first-child+.result{margin-top:-.125em}.md-typeset .tabbed-block>.tabbed-set{margin:0}.md-typeset .tabbed-button{align-self:center;border-radius:100%;color:var(--md-default-fg-color--light);cursor:pointer;display:block;height:.9rem;margin-top:.1rem;pointer-events:auto;transition:background-color .25s;width:.9rem}.md-typeset .tabbed-button:hover{background-color:var(--md-accent-fg-color--transparent);color:var(--md-accent-fg-color)}.md-typeset .tabbed-button:after{background-color:currentcolor;content:"";display:block;height:100%;-webkit-mask-image:var(--md-tabbed-icon--prev);mask-image:var(--md-tabbed-icon--prev);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;transition:background-color .25s,transform .25s;width:100%}.md-typeset .tabbed-control{background:linear-gradient(to right,var(--md-default-bg-color) 60%,#0000);display:flex;height:1.9rem;justify-content:start;pointer-events:none;position:absolute;transition:opacity 125ms;width:1.2rem}[dir=rtl] .md-typeset .tabbed-control{transform:rotate(180deg)}.md-typeset .tabbed-control[hidden]{opacity:0}.md-typeset .tabbed-control--next{background:linear-gradient(to left,var(--md-default-bg-color) 60%,#0000);justify-content:end;right:0}.md-typeset .tabbed-control--next .tabbed-button:after{-webkit-mask-image:var(--md-tabbed-icon--next);mask-image:var(--md-tabbed-icon--next)}@media screen and (max-width:44.984375em){[dir=ltr] .md-content__inner>.tabbed-set .tabbed-labels{padding-left:.8rem}[dir=rtl] .md-content__inner>.tabbed-set .tabbed-labels{padding-right:.8rem}.md-content__inner>.tabbed-set .tabbed-labels{margin:0 -.8rem;max-width:100vw;scroll-padding-inline-start:.8rem}[dir=ltr] .md-content__inner>.tabbed-set .tabbed-labels:after{padding-right:.8rem}[dir=rtl] .md-content__inner>.tabbed-set .tabbed-labels:after{padding-left:.8rem}.md-content__inner>.tabbed-set .tabbed-labels:after{content:""}[dir=ltr] .md-content__inner>.tabbed-set .tabbed-labels~.tabbed-control--prev{padding-left:.8rem}[dir=rtl] .md-content__inner>.tabbed-set .tabbed-labels~.tabbed-control--prev{padding-right:.8rem}[dir=ltr] .md-content__inner>.tabbed-set .tabbed-labels~.tabbed-control--prev{margin-left:-.8rem}[dir=rtl] .md-content__inner>.tabbed-set .tabbed-labels~.tabbed-control--prev{margin-right:-.8rem}.md-content__inner>.tabbed-set .tabbed-labels~.tabbed-control--prev{width:2rem}[dir=ltr] .md-content__inner>.tabbed-set .tabbed-labels~.tabbed-control--next{padding-right:.8rem}[dir=rtl] .md-content__inner>.tabbed-set .tabbed-labels~.tabbed-control--next{padding-left:.8rem}[dir=ltr] .md-content__inner>.tabbed-set .tabbed-labels~.tabbed-control--next{margin-right:-.8rem}[dir=rtl] .md-content__inner>.tabbed-set .tabbed-labels~.tabbed-control--next{margin-left:-.8rem}.md-content__inner>.tabbed-set .tabbed-labels~.tabbed-control--next{width:2rem}}@media screen{.md-typeset .tabbed-set>input:first-child:checked~.tabbed-labels>:first-child,.md-typeset .tabbed-set>input:nth-child(10):checked~.tabbed-labels>:nth-child(10),.md-typeset .tabbed-set>input:nth-child(11):checked~.tabbed-labels>:nth-child(11),.md-typeset .tabbed-set>input:nth-child(12):checked~.tabbed-labels>:nth-child(12),.md-typeset .tabbed-set>input:nth-child(13):checked~.tabbed-labels>:nth-child(13),.md-typeset .tabbed-set>input:nth-child(14):checked~.tabbed-labels>:nth-child(14),.md-typeset .tabbed-set>input:nth-child(15):checked~.tabbed-labels>:nth-child(15),.md-typeset .tabbed-set>input:nth-child(16):checked~.tabbed-labels>:nth-child(16),.md-typeset .tabbed-set>input:nth-child(17):checked~.tabbed-labels>:nth-child(17),.md-typeset .tabbed-set>input:nth-child(18):checked~.tabbed-labels>:nth-child(18),.md-typeset .tabbed-set>input:nth-child(19):checked~.tabbed-labels>:nth-child(19),.md-typeset .tabbed-set>input:nth-child(2):checked~.tabbed-labels>:nth-child(2),.md-typeset .tabbed-set>input:nth-child(20):checked~.tabbed-labels>:nth-child(20),.md-typeset .tabbed-set>input:nth-child(3):checked~.tabbed-labels>:nth-child(3),.md-typeset .tabbed-set>input:nth-child(4):checked~.tabbed-labels>:nth-child(4),.md-typeset .tabbed-set>input:nth-child(5):checked~.tabbed-labels>:nth-child(5),.md-typeset .tabbed-set>input:nth-child(6):checked~.tabbed-labels>:nth-child(6),.md-typeset .tabbed-set>input:nth-child(7):checked~.tabbed-labels>:nth-child(7),.md-typeset .tabbed-set>input:nth-child(8):checked~.tabbed-labels>:nth-child(8),.md-typeset .tabbed-set>input:nth-child(9):checked~.tabbed-labels>:nth-child(9){color:var(--md-default-fg-color)}.md-typeset .no-js .tabbed-set>input:first-child:checked~.tabbed-labels>:first-child,.md-typeset .no-js .tabbed-set>input:nth-child(10):checked~.tabbed-labels>:nth-child(10),.md-typeset .no-js .tabbed-set>input:nth-child(11):checked~.tabbed-labels>:nth-child(11),.md-typeset .no-js .tabbed-set>input:nth-child(12):checked~.tabbed-labels>:nth-child(12),.md-typeset .no-js .tabbed-set>input:nth-child(13):checked~.tabbed-labels>:nth-child(13),.md-typeset .no-js .tabbed-set>input:nth-child(14):checked~.tabbed-labels>:nth-child(14),.md-typeset .no-js .tabbed-set>input:nth-child(15):checked~.tabbed-labels>:nth-child(15),.md-typeset .no-js .tabbed-set>input:nth-child(16):checked~.tabbed-labels>:nth-child(16),.md-typeset .no-js .tabbed-set>input:nth-child(17):checked~.tabbed-labels>:nth-child(17),.md-typeset .no-js .tabbed-set>input:nth-child(18):checked~.tabbed-labels>:nth-child(18),.md-typeset .no-js .tabbed-set>input:nth-child(19):checked~.tabbed-labels>:nth-child(19),.md-typeset .no-js .tabbed-set>input:nth-child(2):checked~.tabbed-labels>:nth-child(2),.md-typeset .no-js .tabbed-set>input:nth-child(20):checked~.tabbed-labels>:nth-child(20),.md-typeset .no-js .tabbed-set>input:nth-child(3):checked~.tabbed-labels>:nth-child(3),.md-typeset .no-js .tabbed-set>input:nth-child(4):checked~.tabbed-labels>:nth-child(4),.md-typeset .no-js .tabbed-set>input:nth-child(5):checked~.tabbed-labels>:nth-child(5),.md-typeset .no-js .tabbed-set>input:nth-child(6):checked~.tabbed-labels>:nth-child(6),.md-typeset .no-js .tabbed-set>input:nth-child(7):checked~.tabbed-labels>:nth-child(7),.md-typeset .no-js .tabbed-set>input:nth-child(8):checked~.tabbed-labels>:nth-child(8),.md-typeset .no-js .tabbed-set>input:nth-child(9):checked~.tabbed-labels>:nth-child(9),.md-typeset [role=dialog] .tabbed-set>input:first-child:checked~.tabbed-labels>:first-child,.md-typeset [role=dialog] .tabbed-set>input:nth-child(10):checked~.tabbed-labels>:nth-child(10),.md-typeset [role=dialog] .tabbed-set>input:nth-child(11):checked~.tabbed-labels>:nth-child(11),.md-typeset [role=dialog] .tabbed-set>input:nth-child(12):checked~.tabbed-labels>:nth-child(12),.md-typeset [role=dialog] .tabbed-set>input:nth-child(13):checked~.tabbed-labels>:nth-child(13),.md-typeset [role=dialog] .tabbed-set>input:nth-child(14):checked~.tabbed-labels>:nth-child(14),.md-typeset [role=dialog] .tabbed-set>input:nth-child(15):checked~.tabbed-labels>:nth-child(15),.md-typeset [role=dialog] .tabbed-set>input:nth-child(16):checked~.tabbed-labels>:nth-child(16),.md-typeset [role=dialog] .tabbed-set>input:nth-child(17):checked~.tabbed-labels>:nth-child(17),.md-typeset [role=dialog] .tabbed-set>input:nth-child(18):checked~.tabbed-labels>:nth-child(18),.md-typeset [role=dialog] .tabbed-set>input:nth-child(19):checked~.tabbed-labels>:nth-child(19),.md-typeset [role=dialog] .tabbed-set>input:nth-child(2):checked~.tabbed-labels>:nth-child(2),.md-typeset [role=dialog] .tabbed-set>input:nth-child(20):checked~.tabbed-labels>:nth-child(20),.md-typeset [role=dialog] .tabbed-set>input:nth-child(3):checked~.tabbed-labels>:nth-child(3),.md-typeset [role=dialog] .tabbed-set>input:nth-child(4):checked~.tabbed-labels>:nth-child(4),.md-typeset [role=dialog] .tabbed-set>input:nth-child(5):checked~.tabbed-labels>:nth-child(5),.md-typeset [role=dialog] .tabbed-set>input:nth-child(6):checked~.tabbed-labels>:nth-child(6),.md-typeset [role=dialog] .tabbed-set>input:nth-child(7):checked~.tabbed-labels>:nth-child(7),.md-typeset [role=dialog] .tabbed-set>input:nth-child(8):checked~.tabbed-labels>:nth-child(8),.md-typeset [role=dialog] .tabbed-set>input:nth-child(9):checked~.tabbed-labels>:nth-child(9),.no-js .md-typeset .tabbed-set>input:first-child:checked~.tabbed-labels>:first-child,.no-js .md-typeset .tabbed-set>input:nth-child(10):checked~.tabbed-labels>:nth-child(10),.no-js .md-typeset .tabbed-set>input:nth-child(11):checked~.tabbed-labels>:nth-child(11),.no-js .md-typeset .tabbed-set>input:nth-child(12):checked~.tabbed-labels>:nth-child(12),.no-js .md-typeset .tabbed-set>input:nth-child(13):checked~.tabbed-labels>:nth-child(13),.no-js .md-typeset .tabbed-set>input:nth-child(14):checked~.tabbed-labels>:nth-child(14),.no-js .md-typeset .tabbed-set>input:nth-child(15):checked~.tabbed-labels>:nth-child(15),.no-js .md-typeset .tabbed-set>input:nth-child(16):checked~.tabbed-labels>:nth-child(16),.no-js .md-typeset .tabbed-set>input:nth-child(17):checked~.tabbed-labels>:nth-child(17),.no-js .md-typeset .tabbed-set>input:nth-child(18):checked~.tabbed-labels>:nth-child(18),.no-js .md-typeset .tabbed-set>input:nth-child(19):checked~.tabbed-labels>:nth-child(19),.no-js .md-typeset .tabbed-set>input:nth-child(2):checked~.tabbed-labels>:nth-child(2),.no-js .md-typeset .tabbed-set>input:nth-child(20):checked~.tabbed-labels>:nth-child(20),.no-js .md-typeset .tabbed-set>input:nth-child(3):checked~.tabbed-labels>:nth-child(3),.no-js .md-typeset .tabbed-set>input:nth-child(4):checked~.tabbed-labels>:nth-child(4),.no-js .md-typeset .tabbed-set>input:nth-child(5):checked~.tabbed-labels>:nth-child(5),.no-js .md-typeset .tabbed-set>input:nth-child(6):checked~.tabbed-labels>:nth-child(6),.no-js .md-typeset .tabbed-set>input:nth-child(7):checked~.tabbed-labels>:nth-child(7),.no-js .md-typeset .tabbed-set>input:nth-child(8):checked~.tabbed-labels>:nth-child(8),.no-js .md-typeset .tabbed-set>input:nth-child(9):checked~.tabbed-labels>:nth-child(9),[role=dialog] .md-typeset .tabbed-set>input:first-child:checked~.tabbed-labels>:first-child,[role=dialog] .md-typeset .tabbed-set>input:nth-child(10):checked~.tabbed-labels>:nth-child(10),[role=dialog] .md-typeset .tabbed-set>input:nth-child(11):checked~.tabbed-labels>:nth-child(11),[role=dialog] .md-typeset .tabbed-set>input:nth-child(12):checked~.tabbed-labels>:nth-child(12),[role=dialog] .md-typeset .tabbed-set>input:nth-child(13):checked~.tabbed-labels>:nth-child(13),[role=dialog] .md-typeset .tabbed-set>input:nth-child(14):checked~.tabbed-labels>:nth-child(14),[role=dialog] .md-typeset .tabbed-set>input:nth-child(15):checked~.tabbed-labels>:nth-child(15),[role=dialog] .md-typeset .tabbed-set>input:nth-child(16):checked~.tabbed-labels>:nth-child(16),[role=dialog] .md-typeset .tabbed-set>input:nth-child(17):checked~.tabbed-labels>:nth-child(17),[role=dialog] .md-typeset .tabbed-set>input:nth-child(18):checked~.tabbed-labels>:nth-child(18),[role=dialog] .md-typeset .tabbed-set>input:nth-child(19):checked~.tabbed-labels>:nth-child(19),[role=dialog] .md-typeset .tabbed-set>input:nth-child(2):checked~.tabbed-labels>:nth-child(2),[role=dialog] .md-typeset .tabbed-set>input:nth-child(20):checked~.tabbed-labels>:nth-child(20),[role=dialog] .md-typeset .tabbed-set>input:nth-child(3):checked~.tabbed-labels>:nth-child(3),[role=dialog] .md-typeset .tabbed-set>input:nth-child(4):checked~.tabbed-labels>:nth-child(4),[role=dialog] .md-typeset .tabbed-set>input:nth-child(5):checked~.tabbed-labels>:nth-child(5),[role=dialog] .md-typeset .tabbed-set>input:nth-child(6):checked~.tabbed-labels>:nth-child(6),[role=dialog] .md-typeset .tabbed-set>input:nth-child(7):checked~.tabbed-labels>:nth-child(7),[role=dialog] .md-typeset .tabbed-set>input:nth-child(8):checked~.tabbed-labels>:nth-child(8),[role=dialog] .md-typeset .tabbed-set>input:nth-child(9):checked~.tabbed-labels>:nth-child(9){border-color:var(--md-default-fg-color)}}.md-typeset .tabbed-set>input:first-child.focus-visible~.tabbed-labels>:first-child,.md-typeset .tabbed-set>input:nth-child(10).focus-visible~.tabbed-labels>:nth-child(10),.md-typeset .tabbed-set>input:nth-child(11).focus-visible~.tabbed-labels>:nth-child(11),.md-typeset .tabbed-set>input:nth-child(12).focus-visible~.tabbed-labels>:nth-child(12),.md-typeset .tabbed-set>input:nth-child(13).focus-visible~.tabbed-labels>:nth-child(13),.md-typeset .tabbed-set>input:nth-child(14).focus-visible~.tabbed-labels>:nth-child(14),.md-typeset .tabbed-set>input:nth-child(15).focus-visible~.tabbed-labels>:nth-child(15),.md-typeset .tabbed-set>input:nth-child(16).focus-visible~.tabbed-labels>:nth-child(16),.md-typeset .tabbed-set>input:nth-child(17).focus-visible~.tabbed-labels>:nth-child(17),.md-typeset .tabbed-set>input:nth-child(18).focus-visible~.tabbed-labels>:nth-child(18),.md-typeset .tabbed-set>input:nth-child(19).focus-visible~.tabbed-labels>:nth-child(19),.md-typeset .tabbed-set>input:nth-child(2).focus-visible~.tabbed-labels>:nth-child(2),.md-typeset .tabbed-set>input:nth-child(20).focus-visible~.tabbed-labels>:nth-child(20),.md-typeset .tabbed-set>input:nth-child(3).focus-visible~.tabbed-labels>:nth-child(3),.md-typeset .tabbed-set>input:nth-child(4).focus-visible~.tabbed-labels>:nth-child(4),.md-typeset .tabbed-set>input:nth-child(5).focus-visible~.tabbed-labels>:nth-child(5),.md-typeset .tabbed-set>input:nth-child(6).focus-visible~.tabbed-labels>:nth-child(6),.md-typeset .tabbed-set>input:nth-child(7).focus-visible~.tabbed-labels>:nth-child(7),.md-typeset .tabbed-set>input:nth-child(8).focus-visible~.tabbed-labels>:nth-child(8),.md-typeset .tabbed-set>input:nth-child(9).focus-visible~.tabbed-labels>:nth-child(9){color:var(--md-accent-fg-color)}.md-typeset .tabbed-set>input:first-child:checked~.tabbed-content>:first-child,.md-typeset .tabbed-set>input:nth-child(10):checked~.tabbed-content>:nth-child(10),.md-typeset .tabbed-set>input:nth-child(11):checked~.tabbed-content>:nth-child(11),.md-typeset .tabbed-set>input:nth-child(12):checked~.tabbed-content>:nth-child(12),.md-typeset .tabbed-set>input:nth-child(13):checked~.tabbed-content>:nth-child(13),.md-typeset .tabbed-set>input:nth-child(14):checked~.tabbed-content>:nth-child(14),.md-typeset .tabbed-set>input:nth-child(15):checked~.tabbed-content>:nth-child(15),.md-typeset .tabbed-set>input:nth-child(16):checked~.tabbed-content>:nth-child(16),.md-typeset .tabbed-set>input:nth-child(17):checked~.tabbed-content>:nth-child(17),.md-typeset .tabbed-set>input:nth-child(18):checked~.tabbed-content>:nth-child(18),.md-typeset .tabbed-set>input:nth-child(19):checked~.tabbed-content>:nth-child(19),.md-typeset .tabbed-set>input:nth-child(2):checked~.tabbed-content>:nth-child(2),.md-typeset .tabbed-set>input:nth-child(20):checked~.tabbed-content>:nth-child(20),.md-typeset .tabbed-set>input:nth-child(3):checked~.tabbed-content>:nth-child(3),.md-typeset .tabbed-set>input:nth-child(4):checked~.tabbed-content>:nth-child(4),.md-typeset .tabbed-set>input:nth-child(5):checked~.tabbed-content>:nth-child(5),.md-typeset .tabbed-set>input:nth-child(6):checked~.tabbed-content>:nth-child(6),.md-typeset .tabbed-set>input:nth-child(7):checked~.tabbed-content>:nth-child(7),.md-typeset .tabbed-set>input:nth-child(8):checked~.tabbed-content>:nth-child(8),.md-typeset .tabbed-set>input:nth-child(9):checked~.tabbed-content>:nth-child(9){display:block}:root{--md-tasklist-icon:url('data:image/svg+xml;charset=utf-8,');--md-tasklist-icon--checked:url('data:image/svg+xml;charset=utf-8,')}.md-typeset .task-list-item{list-style-type:none;position:relative}[dir=ltr] .md-typeset .task-list-item [type=checkbox]{left:-2em}[dir=rtl] .md-typeset .task-list-item [type=checkbox]{right:-2em}.md-typeset .task-list-item [type=checkbox]{position:absolute;top:.45em}.md-typeset .task-list-control [type=checkbox]{opacity:0;z-index:-1}[dir=ltr] .md-typeset .task-list-indicator:before{left:-1.5em}[dir=rtl] .md-typeset .task-list-indicator:before{right:-1.5em}.md-typeset .task-list-indicator:before{background-color:var(--md-default-fg-color--lightest);content:"";height:1.25em;-webkit-mask-image:var(--md-tasklist-icon);mask-image:var(--md-tasklist-icon);-webkit-mask-position:center;mask-position:center;-webkit-mask-repeat:no-repeat;mask-repeat:no-repeat;-webkit-mask-size:contain;mask-size:contain;position:absolute;top:.15em;width:1.25em}.md-typeset [type=checkbox]:checked+.task-list-indicator:before{background-color:#00e676;-webkit-mask-image:var(--md-tasklist-icon--checked);mask-image:var(--md-tasklist-icon--checked)}@media print{.giscus,[id=__comments]{display:none}}:root>*{--md-mermaid-font-family:var(--md-text-font-family),sans-serif;--md-mermaid-edge-color:var(--md-code-fg-color);--md-mermaid-node-bg-color:var(--md-accent-fg-color--transparent);--md-mermaid-node-fg-color:var(--md-accent-fg-color);--md-mermaid-label-bg-color:var(--md-default-bg-color);--md-mermaid-label-fg-color:var(--md-code-fg-color);--md-mermaid-sequence-actor-bg-color:var(--md-mermaid-label-bg-color);--md-mermaid-sequence-actor-fg-color:var(--md-mermaid-label-fg-color);--md-mermaid-sequence-actor-border-color:var(--md-mermaid-node-fg-color);--md-mermaid-sequence-actor-line-color:var(--md-default-fg-color--lighter);--md-mermaid-sequence-actorman-bg-color:var(--md-mermaid-label-bg-color);--md-mermaid-sequence-actorman-line-color:var(--md-mermaid-node-fg-color);--md-mermaid-sequence-box-bg-color:var(--md-mermaid-node-bg-color);--md-mermaid-sequence-box-fg-color:var(--md-mermaid-edge-color);--md-mermaid-sequence-label-bg-color:var(--md-mermaid-node-bg-color);--md-mermaid-sequence-label-fg-color:var(--md-mermaid-node-fg-color);--md-mermaid-sequence-loop-bg-color:var(--md-mermaid-node-bg-color);--md-mermaid-sequence-loop-fg-color:var(--md-mermaid-edge-color);--md-mermaid-sequence-loop-border-color:var(--md-mermaid-node-fg-color);--md-mermaid-sequence-message-fg-color:var(--md-mermaid-edge-color);--md-mermaid-sequence-message-line-color:var(--md-mermaid-edge-color);--md-mermaid-sequence-note-bg-color:var(--md-mermaid-label-bg-color);--md-mermaid-sequence-note-fg-color:var(--md-mermaid-edge-color);--md-mermaid-sequence-note-border-color:var(--md-mermaid-label-fg-color);--md-mermaid-sequence-number-bg-color:var(--md-mermaid-node-fg-color);--md-mermaid-sequence-number-fg-color:var(--md-accent-bg-color)}.mermaid{line-height:normal;margin:1em 0}.md-typeset .grid{grid-gap:.4rem;display:grid;grid-template-columns:repeat(auto-fit,minmax(min(100%,16rem),1fr));margin:1em 0}.md-typeset .grid.cards>ol,.md-typeset .grid.cards>ul{display:contents}.md-typeset .grid.cards>ol>li,.md-typeset .grid.cards>ul>li,.md-typeset .grid>.card{border:.05rem solid var(--md-default-fg-color--lightest);border-radius:.1rem;display:block;margin:0;padding:.8rem;transition:border .25s,box-shadow .25s}.md-typeset .grid.cards>ol>li:focus-within,.md-typeset .grid.cards>ol>li:hover,.md-typeset .grid.cards>ul>li:focus-within,.md-typeset .grid.cards>ul>li:hover,.md-typeset .grid>.card:focus-within,.md-typeset .grid>.card:hover{border-color:#0000;box-shadow:var(--md-shadow-z2)}.md-typeset .grid.cards>ol>li>hr,.md-typeset .grid.cards>ul>li>hr,.md-typeset .grid>.card>hr{margin-bottom:1em;margin-top:1em}.md-typeset .grid.cards>ol>li>:first-child,.md-typeset .grid.cards>ul>li>:first-child,.md-typeset .grid>.card>:first-child{margin-top:0}.md-typeset .grid.cards>ol>li>:last-child,.md-typeset .grid.cards>ul>li>:last-child,.md-typeset .grid>.card>:last-child{margin-bottom:0}.md-typeset .grid>*,.md-typeset .grid>.admonition,.md-typeset .grid>.highlight>*,.md-typeset .grid>.highlighttable,.md-typeset .grid>.md-typeset details,.md-typeset .grid>details,.md-typeset .grid>pre{margin-bottom:0;margin-top:0}.md-typeset .grid>.highlight>pre:only-child,.md-typeset .grid>.highlight>pre>code,.md-typeset .grid>.highlighttable,.md-typeset .grid>.highlighttable>tbody,.md-typeset .grid>.highlighttable>tbody>tr,.md-typeset .grid>.highlighttable>tbody>tr>.code,.md-typeset .grid>.highlighttable>tbody>tr>.code>.highlight,.md-typeset .grid>.highlighttable>tbody>tr>.code>.highlight>pre,.md-typeset .grid>.highlighttable>tbody>tr>.code>.highlight>pre>code{height:100%}.md-typeset .grid>.tabbed-set{margin-bottom:0;margin-top:0}@media screen and (min-width:45em){[dir=ltr] .md-typeset .inline{float:left}[dir=rtl] .md-typeset .inline{float:right}[dir=ltr] .md-typeset .inline{margin-right:.8rem}[dir=rtl] .md-typeset .inline{margin-left:.8rem}.md-typeset .inline{margin-bottom:.8rem;margin-top:0;width:11.7rem}[dir=ltr] .md-typeset .inline.end{float:right}[dir=rtl] .md-typeset .inline.end{float:left}[dir=ltr] .md-typeset .inline.end{margin-left:.8rem;margin-right:0}[dir=rtl] .md-typeset .inline.end{margin-left:0;margin-right:.8rem}}
\ No newline at end of file
diff --git a/assets/stylesheets/palette.ab4e12ef.min.css b/assets/stylesheets/palette.ab4e12ef.min.css
new file mode 100644
index 00000000..75aaf842
--- /dev/null
+++ b/assets/stylesheets/palette.ab4e12ef.min.css
@@ -0,0 +1 @@
+@media screen{[data-md-color-scheme=slate]{--md-default-fg-color:hsla(var(--md-hue),15%,90%,0.82);--md-default-fg-color--light:hsla(var(--md-hue),15%,90%,0.56);--md-default-fg-color--lighter:hsla(var(--md-hue),15%,90%,0.32);--md-default-fg-color--lightest:hsla(var(--md-hue),15%,90%,0.12);--md-default-bg-color:hsla(var(--md-hue),15%,14%,1);--md-default-bg-color--light:hsla(var(--md-hue),15%,14%,0.54);--md-default-bg-color--lighter:hsla(var(--md-hue),15%,14%,0.26);--md-default-bg-color--lightest:hsla(var(--md-hue),15%,14%,0.07);--md-code-fg-color:hsla(var(--md-hue),18%,86%,0.82);--md-code-bg-color:hsla(var(--md-hue),15%,18%,1);--md-code-bg-color--light:hsla(var(--md-hue),15%,18%,0.9);--md-code-bg-color--lighter:hsla(var(--md-hue),15%,18%,0.54);--md-code-hl-color:#2977ff;--md-code-hl-color--light:#2977ff1a;--md-code-hl-number-color:#e6695b;--md-code-hl-special-color:#f06090;--md-code-hl-function-color:#c973d9;--md-code-hl-constant-color:#9383e2;--md-code-hl-keyword-color:#6791e0;--md-code-hl-string-color:#2fb170;--md-code-hl-name-color:var(--md-code-fg-color);--md-code-hl-operator-color:var(--md-default-fg-color--light);--md-code-hl-punctuation-color:var(--md-default-fg-color--light);--md-code-hl-comment-color:var(--md-default-fg-color--light);--md-code-hl-generic-color:var(--md-default-fg-color--light);--md-code-hl-variable-color:var(--md-default-fg-color--light);--md-typeset-color:var(--md-default-fg-color);--md-typeset-a-color:var(--md-primary-fg-color);--md-typeset-kbd-color:hsla(var(--md-hue),15%,90%,0.12);--md-typeset-kbd-accent-color:hsla(var(--md-hue),15%,90%,0.2);--md-typeset-kbd-border-color:hsla(var(--md-hue),15%,14%,1);--md-typeset-mark-color:#4287ff4d;--md-typeset-table-color:hsla(var(--md-hue),15%,95%,0.12);--md-typeset-table-color--light:hsla(var(--md-hue),15%,95%,0.035);--md-admonition-fg-color:var(--md-default-fg-color);--md-admonition-bg-color:var(--md-default-bg-color);--md-footer-bg-color:hsla(var(--md-hue),15%,10%,0.87);--md-footer-bg-color--dark:hsla(var(--md-hue),15%,8%,1);--md-shadow-z1:0 0.2rem 0.5rem #0000000d,0 0 0.05rem #0000001a;--md-shadow-z2:0 0.2rem 0.5rem #00000040,0 0 0.05rem #00000040;--md-shadow-z3:0 0.2rem 0.5rem #0006,0 0 0.05rem #00000059;color-scheme:dark}[data-md-color-scheme=slate] img[src$="#gh-light-mode-only"],[data-md-color-scheme=slate] img[src$="#only-light"]{display:none}[data-md-color-scheme=slate][data-md-color-primary=pink]{--md-typeset-a-color:#ed5487}[data-md-color-scheme=slate][data-md-color-primary=purple]{--md-typeset-a-color:#c46fd3}[data-md-color-scheme=slate][data-md-color-primary=deep-purple]{--md-typeset-a-color:#a47bea}[data-md-color-scheme=slate][data-md-color-primary=indigo]{--md-typeset-a-color:#5488e8}[data-md-color-scheme=slate][data-md-color-primary=teal]{--md-typeset-a-color:#00ccb8}[data-md-color-scheme=slate][data-md-color-primary=green]{--md-typeset-a-color:#71c174}[data-md-color-scheme=slate][data-md-color-primary=deep-orange]{--md-typeset-a-color:#ff764d}[data-md-color-scheme=slate][data-md-color-primary=brown]{--md-typeset-a-color:#c1775c}[data-md-color-scheme=slate][data-md-color-primary=black],[data-md-color-scheme=slate][data-md-color-primary=blue-grey],[data-md-color-scheme=slate][data-md-color-primary=grey],[data-md-color-scheme=slate][data-md-color-primary=white]{--md-typeset-a-color:#5e8bde}[data-md-color-switching] *,[data-md-color-switching] :after,[data-md-color-switching] :before{transition-duration:0ms!important}}[data-md-color-accent=red]{--md-accent-fg-color:#ff1947;--md-accent-fg-color--transparent:#ff19471a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-accent=pink]{--md-accent-fg-color:#f50056;--md-accent-fg-color--transparent:#f500561a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-accent=purple]{--md-accent-fg-color:#df41fb;--md-accent-fg-color--transparent:#df41fb1a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-accent=deep-purple]{--md-accent-fg-color:#7c4dff;--md-accent-fg-color--transparent:#7c4dff1a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-accent=indigo]{--md-accent-fg-color:#526cfe;--md-accent-fg-color--transparent:#526cfe1a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-accent=blue]{--md-accent-fg-color:#4287ff;--md-accent-fg-color--transparent:#4287ff1a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-accent=light-blue]{--md-accent-fg-color:#0091eb;--md-accent-fg-color--transparent:#0091eb1a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-accent=cyan]{--md-accent-fg-color:#00bad6;--md-accent-fg-color--transparent:#00bad61a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-accent=teal]{--md-accent-fg-color:#00bda4;--md-accent-fg-color--transparent:#00bda41a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-accent=green]{--md-accent-fg-color:#00c753;--md-accent-fg-color--transparent:#00c7531a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-accent=light-green]{--md-accent-fg-color:#63de17;--md-accent-fg-color--transparent:#63de171a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-accent=lime]{--md-accent-fg-color:#b0eb00;--md-accent-fg-color--transparent:#b0eb001a;--md-accent-bg-color:#000000de;--md-accent-bg-color--light:#0000008a}[data-md-color-accent=yellow]{--md-accent-fg-color:#ffd500;--md-accent-fg-color--transparent:#ffd5001a;--md-accent-bg-color:#000000de;--md-accent-bg-color--light:#0000008a}[data-md-color-accent=amber]{--md-accent-fg-color:#fa0;--md-accent-fg-color--transparent:#ffaa001a;--md-accent-bg-color:#000000de;--md-accent-bg-color--light:#0000008a}[data-md-color-accent=orange]{--md-accent-fg-color:#ff9100;--md-accent-fg-color--transparent:#ff91001a;--md-accent-bg-color:#000000de;--md-accent-bg-color--light:#0000008a}[data-md-color-accent=deep-orange]{--md-accent-fg-color:#ff6e42;--md-accent-fg-color--transparent:#ff6e421a;--md-accent-bg-color:#fff;--md-accent-bg-color--light:#ffffffb3}[data-md-color-primary=red]{--md-primary-fg-color:#ef5552;--md-primary-fg-color--light:#e57171;--md-primary-fg-color--dark:#e53734;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=pink]{--md-primary-fg-color:#e92063;--md-primary-fg-color--light:#ec417a;--md-primary-fg-color--dark:#c3185d;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=purple]{--md-primary-fg-color:#ab47bd;--md-primary-fg-color--light:#bb69c9;--md-primary-fg-color--dark:#8c24a8;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=deep-purple]{--md-primary-fg-color:#7e56c2;--md-primary-fg-color--light:#9574cd;--md-primary-fg-color--dark:#673ab6;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=indigo]{--md-primary-fg-color:#4051b5;--md-primary-fg-color--light:#5d6cc0;--md-primary-fg-color--dark:#303fa1;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=blue]{--md-primary-fg-color:#2094f3;--md-primary-fg-color--light:#42a5f5;--md-primary-fg-color--dark:#1975d2;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=light-blue]{--md-primary-fg-color:#02a6f2;--md-primary-fg-color--light:#28b5f6;--md-primary-fg-color--dark:#0287cf;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=cyan]{--md-primary-fg-color:#00bdd6;--md-primary-fg-color--light:#25c5da;--md-primary-fg-color--dark:#0097a8;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=teal]{--md-primary-fg-color:#009485;--md-primary-fg-color--light:#26a699;--md-primary-fg-color--dark:#007a6c;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=green]{--md-primary-fg-color:#4cae4f;--md-primary-fg-color--light:#68bb6c;--md-primary-fg-color--dark:#398e3d;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=light-green]{--md-primary-fg-color:#8bc34b;--md-primary-fg-color--light:#9ccc66;--md-primary-fg-color--dark:#689f38;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=lime]{--md-primary-fg-color:#cbdc38;--md-primary-fg-color--light:#d3e156;--md-primary-fg-color--dark:#b0b52c;--md-primary-bg-color:#000000de;--md-primary-bg-color--light:#0000008a}[data-md-color-primary=yellow]{--md-primary-fg-color:#ffec3d;--md-primary-fg-color--light:#ffee57;--md-primary-fg-color--dark:#fbc02d;--md-primary-bg-color:#000000de;--md-primary-bg-color--light:#0000008a}[data-md-color-primary=amber]{--md-primary-fg-color:#ffc105;--md-primary-fg-color--light:#ffc929;--md-primary-fg-color--dark:#ffa200;--md-primary-bg-color:#000000de;--md-primary-bg-color--light:#0000008a}[data-md-color-primary=orange]{--md-primary-fg-color:#ffa724;--md-primary-fg-color--light:#ffa724;--md-primary-fg-color--dark:#fa8900;--md-primary-bg-color:#000000de;--md-primary-bg-color--light:#0000008a}[data-md-color-primary=deep-orange]{--md-primary-fg-color:#ff6e42;--md-primary-fg-color--light:#ff8a66;--md-primary-fg-color--dark:#f4511f;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=brown]{--md-primary-fg-color:#795649;--md-primary-fg-color--light:#8d6e62;--md-primary-fg-color--dark:#5d4037;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3}[data-md-color-primary=grey]{--md-primary-fg-color:#757575;--md-primary-fg-color--light:#9e9e9e;--md-primary-fg-color--dark:#616161;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3;--md-typeset-a-color:#4051b5}[data-md-color-primary=blue-grey]{--md-primary-fg-color:#546d78;--md-primary-fg-color--light:#607c8a;--md-primary-fg-color--dark:#455a63;--md-primary-bg-color:#fff;--md-primary-bg-color--light:#ffffffb3;--md-typeset-a-color:#4051b5}[data-md-color-primary=light-green]:not([data-md-color-scheme=slate]){--md-typeset-a-color:#72ad2e}[data-md-color-primary=lime]:not([data-md-color-scheme=slate]){--md-typeset-a-color:#8b990a}[data-md-color-primary=yellow]:not([data-md-color-scheme=slate]){--md-typeset-a-color:#b8a500}[data-md-color-primary=amber]:not([data-md-color-scheme=slate]){--md-typeset-a-color:#d19d00}[data-md-color-primary=orange]:not([data-md-color-scheme=slate]){--md-typeset-a-color:#e68a00}[data-md-color-primary=white]{--md-primary-fg-color:hsla(var(--md-hue),0%,100%,1);--md-primary-fg-color--light:hsla(var(--md-hue),0%,100%,0.7);--md-primary-fg-color--dark:hsla(var(--md-hue),0%,0%,0.07);--md-primary-bg-color:hsla(var(--md-hue),0%,0%,0.87);--md-primary-bg-color--light:hsla(var(--md-hue),0%,0%,0.54);--md-typeset-a-color:#4051b5}[data-md-color-primary=white] .md-button{color:var(--md-typeset-a-color)}[data-md-color-primary=white] .md-button--primary{background-color:var(--md-typeset-a-color);border-color:var(--md-typeset-a-color);color:hsla(var(--md-hue),0%,100%,1)}@media screen and (min-width:60em){[data-md-color-primary=white] .md-search__form{background-color:hsla(var(--md-hue),0%,0%,.07)}[data-md-color-primary=white] .md-search__form:hover{background-color:hsla(var(--md-hue),0%,0%,.32)}[data-md-color-primary=white] .md-search__input+.md-search__icon{color:hsla(var(--md-hue),0%,0%,.87)}}@media screen and (min-width:76.25em){[data-md-color-primary=white] .md-tabs{border-bottom:.05rem solid #00000012}}[data-md-color-primary=black]{--md-primary-fg-color:hsla(var(--md-hue),15%,9%,1);--md-primary-fg-color--light:hsla(var(--md-hue),15%,9%,0.54);--md-primary-fg-color--dark:hsla(var(--md-hue),15%,9%,1);--md-primary-bg-color:hsla(var(--md-hue),15%,100%,1);--md-primary-bg-color--light:hsla(var(--md-hue),15%,100%,0.7);--md-typeset-a-color:#4051b5}[data-md-color-primary=black] .md-button{color:var(--md-typeset-a-color)}[data-md-color-primary=black] .md-button--primary{background-color:var(--md-typeset-a-color);border-color:var(--md-typeset-a-color);color:hsla(var(--md-hue),0%,100%,1)}[data-md-color-primary=black] .md-header{background-color:hsla(var(--md-hue),15%,9%,1)}@media screen and (max-width:59.984375em){[data-md-color-primary=black] .md-nav__source{background-color:hsla(var(--md-hue),15%,11%,.87)}}@media screen and (max-width:76.234375em){html [data-md-color-primary=black] .md-nav--primary .md-nav__title[for=__drawer]{background-color:hsla(var(--md-hue),15%,9%,1)}}@media screen and (min-width:76.25em){[data-md-color-primary=black] .md-tabs{background-color:hsla(var(--md-hue),15%,9%,1)}}
\ No newline at end of file
diff --git a/governance/alternate-policy/index.html b/governance/alternate-policy/index.html
new file mode 100644
index 00000000..8fcd2a33
--- /dev/null
+++ b/governance/alternate-policy/index.html
@@ -0,0 +1,4544 @@
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+ Alternate Policy - Technical Advisory Council
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+TAC Alternate Policy
+A TAC voting member may designate an alternate for a specific meeting, and must notify the chair in advance of the meeting. The TAC voting member is responsible for ensuring that the named alternate has enough information to represent the TAC voting member in all matters that will be covered in the meeting. The named alternate will participate in any votes that occur during the meeting for which they were named an alternate, and their vote will count as if it were cast by the TAC voting member.
+
+
Warning
+
If a TAC voting member regularly names an alternate and
+
+- is a TAC Premier Sponsor Representative, then that TAC voting member should consider whether they should replace themselves with the alternate, or
+- is a TAC "At Large" Representative, then that TAC voting member should consider whether they should resign.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
\ No newline at end of file
diff --git a/governance/archiving-inactive-repositories/index.html b/governance/archiving-inactive-repositories/index.html
new file mode 100644
index 00000000..fee00609
--- /dev/null
+++ b/governance/archiving-inactive-repositories/index.html
@@ -0,0 +1,4540 @@
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+ Inactive Repositories - Technical Advisory Council
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Archiving Inactive Repositories
+OpenWallet Foundation very much appreciates the contributions of the community; however, it is important to archive source repositories that have become inactive in order to ensure that others in the community are not using code or reporting issues on a repository that is not being maintained.
+Any repository that has not had a release for 12 months or that has had no commits for 6 months may be archived.
+Projects will be notified via a PR in the appropriate repository, as well as a notice in the project appropriate Discord channel and mailing list, if they exist.
+Generally speaking if the project's maintainers request to keep the repository active, the request will be honored. However if the repository has a lot of out of date dependencies, particulaly ones relating to security vulnerabilites, this request may not be honored.
+A request by the project's maintainers to un-archive a repository for the purposes of active contribution will be honored, unless the project is in an emeritus stage. In those cases the project lifecycle issues will need to be resolved first.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+OpenWallet Foundation Charter
+Exhibit B
+The OpenWallet Foundation Charter
+Linux Foundation Europe
+Effective May 22, 2023
+
+
+-
+
Mission and Scope of the OpenWallet Foundation.
+The purpose of the OpenWallet Foundation (the “OWF”) is to support various open source, open data and/or other open projects relating to or supporting development of digital wallets, including infrastructure and support initiatives related thereto (each such project, a “Technical Project”) , in accordance with the provisions of this Charter. The governance of each Technical Project is as set forth in the charter for that Technical Project.
+The OWF aims to enable entities to transact securely, and in a privacy enhancing fashion, in- person and on-line where attributes stored in, and managed by, the wallet. The OWF will:
+
+- develop and maintain open source code for wallets to enable and ensure wallet interoperability,
+- advocate for the adoption of the interoperable digital wallet technology, and
+- collaborate with Standards Development Organizations (SDOs) in the development and proliferation of open standards related to digital wallets
+
+The OWF will not publish a publicly available wallet (including into any application stores).
+The OWF supports the Technical Projects. The OWF operates under the guidance of the Governing Board of the OWF (the “Governing Board”) and Linux Foundation Europe (the “LFEU”) as may be consistent with Linux Foundation Europe’s tax-exempt status.
+The Governing Board manages the OWF. The Governing Board may establish other committees and other working groups (collectively, and including the Technical Advisory Council, “Committees”) which will report to the Governing Board.
+
+-
+
Sponsorship.
+
+- The OWF will be composed of Premier, General and Associate Sponsors (each, a “Sponsor” and, collectively, the “Sponsors”) in Good Standing. All Sponsors must be current Sponsors of LFEU (at any level) to participate in the OWF as a Sponsor. All sponsors in the OWF, enjoy the privileges and undertake the obligations described in this Charter, as from time-to-time amended by the Governing Board, with the approval of LFEU. During the term of their sponsorship, all Participants will comply with all such policies as the LFEU Board of Directors and/or the OWF may adopt with notice to Sponsors.
+- Premier Sponsors will be entitled to appoint a representative to the Governing Board and any Committee.
+- General Sponsors, acting as a class, will be entitled to annually elect one representative to the Governing Board for every ten General Sponsors, up to a maximum of three total representatives, provided that there will always be at least one General Sponsor representative, even if there are less than ten General Sponsors. The Governing Board determines the General Sponsor representative election process.
+- The Associate Sponsor category of sponsorship is limited to Associate Sponsors of LFEU. The Governing Board may set additional criteria for sponsoring the OWF as an Associate Sponsor. If the Associate Sponsor is itself a membership or participation organization, Associate Sponsorship in the OWF does not confer any privileges or rights to the members or participants of the Associate Sponsor.
+- Sponsors will be entitled to:
+- participate in OWF general meetings, initiatives, events and any other activities; and
+- identify themselves as sponsors of the OWF supporting the OWF community.
+
+
+
+
+-
+
Governing Board
+
+-
+
The Governing Board voting members will consist of:
+
+- one representative appointed by each Premier Sponsor;
+- the TAC Representative (as defined below), or, in the absence of a chair and with the approval of the Governing Board, any active contributor to a Technical Project so designated by the TAC (such chair or designee the “TAC Representative”); and
+- the elected General Sponsor representative or representatives.
+
+
+-
+
The Governing Board will also include nonvoting members consisting of the GAC Representative (defined in Section 4) and Associate Representative.
+
+- The Associate Representative will be chosen based on their efforts and potential to advance the OWF mission. The Associate Representative will be selected by the Governing Board voting representatives through a process determined by the Governing Board.
+
+
+-
+
Only one Sponsor that is part of a group of Related Companies (as defined in Section 7) may appoint, or nominate for a sponsorship class election, a representative on the Governing Board. No single Sponsor, company or set of Related Companies will be entitled to: (i) appoint or nominate for sponsorship class election more than one representative for the Governing Board, or (ii) have more than two representatives on the Governing Board.
+
+- The only path to two representatives from the same group of Related Companies that will be acceptable will be for one Sponsor to appoint or nominate a representative to the Governing Board and have another of its employees, or an employee of one of its Related Companies, serve as the TAC Representative on the Governing Board.
+
+
+-
+
Conduct of Meetings
+
+- Governing Board meetings will be limited to the Governing Board
+representatives, the Outreach Committee Chair, invited guests and OWF staff.
+- Governing Board meetings follow the requirements for quorum and voting outlined in this Charter. The Governing Board may decide whether to allow named representatives (one per Sponsor per Governing Board and per Committee) to attend as an alternate.
+- The Governing Board meetings will be private unless decided otherwise by the Governing Board. The Governing Board may invite guests to participate in consideration of specific Governing Board topics (but such guests may not participate in any vote on any matter before the Governing Board).
+
+
+-
+
Officers
+
+- The officers (“Officers”) of the OWF as of the first meeting of the Governing Board will be a Chairperson (“Chair”) and a Treasurer. Additional Officer positions may be created by the Governing Board.
+- The Chair will preside over meetings of the Governing Board, manage any day-to-day operational decisions, and will submit minutes for Governing Board approval.
+- The Treasurer will assist in the preparation of budgets for Governing Board approval, monitor expenses against the budget and authorize expenditures approved in the budget.
+
+
+-
+
The Governing Board will be responsible for overall oversight of the OWF, including:
+
+- approve a budget directing the use of funds raised by the OWF from all sources of sponsorship or other revenue, including to pay for the hiring of OWF leadership and staff;
+- vet and select a qualified leadership team to run the day-to-day management activities of the organization and evaluate the performance of the team;
+- provide feedback and input to the OWF leadership team responsible for planning and managing the day-to-day operation of the OWF;
+- maintain, if desired, a guiding principles document;
+- nominate and elect Officers of the OWF;
+- supervise and support the leadership team on OWF business and community outreach matters;
+- work with the LFEU on any legal matters that arise;
+- adopt and maintain policies or rules and procedures for the OWF (subject to LFEU’s approval);
+- establish advisory bodies, committees, programs or councils to resolve any particular matter or in support of the mission of the OWF and/or its Technical Projects including in support of end-users and ambassadors for the project any Technical Project;
+- establish any OWF conformance programs for its trademarks and solicit input (including testing tools) if deemed necessary from the applicable oversight body of any Technical Project for defining and administering any programs related to conformance with such Technical Project (each, a “Conformance Program”);
+- publish use cases, user stories, websites and priorities to help inform the ecosystem and technical community;
+- approve procedures for the nomination and election of any representative of the General Sponsors to the Governing Board and any Officer or other positions created by the Governing Board; and
+- vote on all decisions or matters coming before the Governing Board.
+
+
+
+
+-
+
Government Advisory Council
+
+- The Government Advisory Council (the “GAC”) will provide the OWF advice from government entities approved to participate by the Governing Board. Members of the GAC must be national governments, multinational governmental organizations and treaty organizations, or public authorities. Each may appoint one representative and one alternate representative to the GAC. There are no fees to participate in the GAC.
+- The GAC will provide advice to OWF on issues of public policy, and especially where there may be an interaction between OWF's activities and national policies, laws or international agreements.
+- The Governing Board may appoint a chairperson of the GAC or delegate responsibility for selecting a chairperson to the GAC. The GAC chairperson or another person chosen by the GAC chairperson will serve as the “GAC Representative” responsible for reporting progress back to the Governing Board and interfacing with the TAC. The GAC Representative may attend meetings of the Governing Board and TAC as a non-voting member.
+
+
+-
+
Technical Advisory Council
+
+-
+
The role of the TAC is to facilitate communication and collaboration among the Technical Projects. The TAC will be responsible for:
+
+- maintaining an overall strategic vision for technical collaboration and coordinating collaboration among Technical Projects, including development of an overall technical vision for the community;
+- making recommendations to the Budget Committee of resource priorities for Technical Projects;
+- electing annually a chairperson to preside over meetings, set the agenda for meetings, ensure meeting minutes are taken and who will also serve on the Governing Board as the TAC’s representative (the “TAC Representative”);
+- creating, maintaining and amending project lifecycle procedures and processes, deciding where Technical Projects fall within that lifecycle;
+- determining when a technical project should be admitted as a Technical Project or any Technical Project should be considered a TAC Project; and
+- such other matters related to the technical role of the TAC as may be communicated to the TAC by the Governing Board.
+
+
+-
+
The voting members of the TAC consist of:
+
+- one representative appointed by each Premier Sponsor;
+- up to two “at large” representatives appointed by vote of the TAC; and
+- one representative appointed by the technical oversight body (e.g., a technical steering committee) of each TAC Project (as defined herein).
+
+
+-
+
TAC meetings are intended to be open to observe by Sponsors, contributors to any TAC Project and others in the general public interested in the OpenWallet Foundation. The TAC may decide whether to allow named representatives (one per voting member) to attend as an alternate.
+
+- At the start of the OWF, “TAC Projects” are those Technical Projects listed as having voting representatives on the TAC on the Directed Fund’s web site. Thereafter, any Technical Project can become a TAC Project through the approval of the Technical Project’s technical oversight body and the TAC (by a two-third’s vote). The TAC may approve and modify a project lifecycle policy that will address the incubation, archival and other stages of TAC Projects.
+- The TAC representatives will elect a chair to preside over meetings, ensure minutes are taken and drive the TAC agenda with input from the TAC representatives.
+
+
+-
+
Voting
+
+- Quorum for Governing Board and Committee meetings will require at least fifty percent of the voting representatives. If advance notice of the meeting has been given per normal means and timing, the Governing Board may continue to meet even if quorum is not met, but will be prevented from making any decisions at the meeting.
+- Ideally decisions will be made based on consensus. If, however, any decision requires a vote to move forward, the representatives of the Governing Board or Committee, as applicable, will vote on a one vote per voting representative basis.
+- Except as provided in Section 14.a. or elsewhere in this Charter, decisions by vote at a meeting will require a simple majority vote, provided quorum is met. Except as provided in Section 14.a. or elsewhere in this Charter, decisions by electronic vote without a meeting will require a majority of all voting representatives.
+- In the event of a tied vote with respect to an action that cannot be resolved by the Governing Board, the Chair may refer the matter to the LFEU for assistance in reaching a decision. If there is a tied vote in any Committee that cannot be resolved, the matter may be referred to the Governing Board.
+
+
+-
+
Subsidiaries and Related Companies
+
+-
+
Definitions:
+
+- “Subsidiaries” means any entity in which a Sponsor owns, directly or indirectly, more than fifty percent of the voting securities or participation interests of the entity in question;
+- “Related Company” means any entity which controls or is controlled by a Sponsor or which, together with a Sponsor, is under the common control of a third party, in each case where such control results from ownership, either directly or indirectly, of more than fifty percent of the voting securities or participation interests of the entity in question; and
+- “Related Companies” are entities that are each a Related Company of a Sponsor.
+
+
+-
+
Only the legal entity which has executed a Project Sponsorship Agreement and its Subsidiaries will be entitled to enjoy the rights and privileges of such sponsorship; provided, however, that such Sponsor and its Subsidiaries will be treated together as a single Sponsor.
+
+- If a Sponsor is itself a foundation, association, consortium, open source project, membership organization, participation organization, user group or other entity that has members or sponsors, then the rights and privileges granted to such Sponsor will extend only to the employee-representatives of such Sponsor, and not to its members or sponsors, unless otherwise approved by the Governing Board in a specific case.
+- OWF sponsorship is non-transferable, non-salable and non-assignable, except a Sponsor may transfer its current sponsorship privileges and obligations to a successor of substantially all of its business or assets, whether by merger, sale or otherwise; provided that the transferee agrees to be bound by this Charter and the Bylaws and policies required by LFEU sponsorship.
+
+
+-
+
Good Standing
+
+- Linux Foundation Europe’s Good Standing Policy is available at https://linuxfoundation.eu/policies and will apply to all Sponsors of this OWF.
+
+
+-
+
Trademarks
+
+- Any trademarks relating to the OWF or any Technical Project, including without limitation any mark relating to any conformance program, must be transferred to and held by LFEU or an entity in LFEU’s control and available for use pursuant to LFEU’s trademark usage policy, available at https://linuxfoundation.eu/policies.
+
+
+-
+
Antitrust Guidelines
+
+- All Sponsors must abide by Linux Foundation Europe’s Antitrust Policy available at https://linuxfoundation.eu/policies.
+- All Sponsors must encourage open participation from any organization able to meet the sponsorship requirements, regardless of competitive interests. Put another way, the Governing Board will not seek to exclude any Sponsor based on any criteria, requirements or reasons other than those that are reasonable and applied on a non- discriminatory basis to all Sponsors.
+
+
+-
+
Budget
+
+- The Governing Board will approve an annual budget and never commit to spend in excess of funds raised. The budget and the purposes to which it is applied must be consistent with both (a) the non-profit and tax-exempt mission of LFEU and (b) the goals of any Technical Project.
+- LFEU will provide the Governing Board with regular reports of spend levels against the budget. Under no circumstances will LFEU have any expectation or obligation to undertake an action on behalf of the OWF or otherwise related to the OWF that is not covered in full by funds raised by the OWF.
+- In the event an unbudgeted or otherwise unfunded obligation arises related to the OWF, LFEU will coordinate with the Governing Board to address gap funding requirements.
+
+
+-
+
General & Administrative Expenses
+
+- LFEU will have custody of and final authority over the usage of any fees, funds, and other cash receipts.
+- A General & Administrative (G&A) fee will be applied by LFEU to funds raised to cover sponsorship records, finance, accounting, and human resources operations. The G&A fee will be 9% of the OWF’s first EUR 1,000,000 of gross receipts each year and 6% of the OWF’s gross receipts each year over EUR 1,000,000.
+
+
+-
+
General Rules and Operations.
+The OWF activities must:
+
+- engage in the work of the project in a professional manner consistent with maintaining a cohesive community, while also maintaining the goodwill and esteem of LFEU in the open source community;
+- respect the rights of all trademark owners, including any branding and usage guidelines;
+- engage or coordinate with LFEU on all outreach, website and marketing activities regarding the OWF or on behalf of any Technical Project that invoke or associate the name of any Technical Project or LFEU; and
+- operate under such rules and procedures as may be approved by the Governing Board and confirmed by LFEU.
+
+
+-
+
Amendments
+
+- This Charter may be amended by a two-thirds vote of the entire Governing Board, subject to approval by LFEU.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+ Code of Conduct
+
+The TAC may adopt a code of conduct (“CoC”) for the Project, which is subject to approval by LF Europe. In the event that a Project-specific CoC has not been approved, the LF Europe Code of Conduct listed at http://lfeurope.be/policies will apply for all Collaborators in the Project.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Common Repository Structure
+OpenWallet Foundation projects are required to maintain a standard set of files in each repository. This document describes the required and recommended files.
+Required Files with Specified Content
+Repositories MUST have these files with the specific content in the linked files, or a file with a link to the specified content with minimal exposition. These files MUST be at the root of the repository.
+
+-
+
LICENSE
+
+
Info
+
All code within the OpenWallet Foundation should be licensed under Apache 2.0. Exceptions can be made by the OpenWallet Foundation Governing Board.
+
+-
+
CODE_OF_CONDUCT.md
+
+SECURITY.md
+Required Files with Variable Content
+Repositories MUST have these files. Named files MUST be at the root of the repository, and may have format suffixes such as .md, .rst, or .txt.
+
+README - A description of the project that contains information or links to information such as:
+- A reference to the Apache license (required).
+- The current and important past releases
+- Documentation for developers and users
+
+MAINTAINERS - A list of all current maintainers with contact info. A separate document covers the specifics.CONTRIBUTING - Directions on how to contribute code to the project, or a link to a page with that information.CHANGELOG - A human readable list of recent changes. Changes should at least include the current release. This file may be maintainer curated or mechanically produced.- Continuous Integration / Continuous Delivery (CICD) configurations - Configurations needed to run CICD on OpenWallet Foundation provided systems (e.g., .github/workflows).
+
+Recommended
+Repositories SHOULD have these files. Named files SHOULD be at the root of the repository
+
+Prohibited
+Repositories MUST NOT have these files
+
+- Executable binaries and shared library files built by code in the repository. This includes
.exe, .dll, .so, .a and .dylib files not otherwise part of a third party library.
+
+Credits
+This document is based on the Hyperledger Foundation's Common Respository Structure guideline.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Content Plan
+This document provides details about the different channels that we have within the OpenWallet Foundation and what we expect each to be used for.
+
+
+
+ Channel |
+ What |
+ Roles |
+
+
+
+ Discord |
+ - Real-Time Communication: Chat services facilitate real-time, synchronous communication among users. Messages are sent and received instantly, enabling quick exchanges and conversations.
- Interactive Collaboration: Chat services are well-suited for interactive collaboration, allowing users to engage in live discussions, share files, collaborate on documents, and even conduct video calls in some cases.
|
+ Staff: Administers, creates new channels, and moderates Community: Sends messages and monitors |
+
+
+ Mailing Lists |
+ - Asynchronous Communication: Mailing lists are primarily used for asynchronous communication. Users send messages to a central email address, which are then distributed to all subscribers. Subscribers can read and respond to messages at their convenience.
- Broadcasting Information: Mailing lists are effective for broadcasting information to a group of subscribers. They are commonly used for announcements, discussions, and sharing updates within a community or organization.
- Archiving: Mailing lists typically archive messages, allowing subscribers to access past discussions and reference previous communications. This archival feature can be valuable for maintaining a record of conversations and facilitating knowledge sharing.
|
+ Staff: Administers, creates new lists, and moderates Community: Sends messages and monitors |
+
+
+ GitHub |
+ - Project-Based Source Code and User Documentation: Any source code for projects should utilize GitHub. GitHub pages should be used for hosting user documentation.
- TAC Governance Documentation and Other Relevant Information: Governance documentation for the TAC must be version controlled. As such, GitHub is the appropriate place to store this information in addition to other relevant TAC materials. Currently https://tac.openwallet.foundation is generated from markdown files in GitHub.
- SIG or Task Force Deliverables: A separate repo can be set up for SIGs and Task Forces so that they can have versioned control support for their deliverables.
|
+ Staff: Administers, creates new repos and teams Maintainers: Reviews and handles issues and pull requests Community: Use source,create issues, fork code, and contribute |
+
+
+ Website |
+ - Blogs
- Announcements
- Native content
- Events and Conferences
|
+ Staff: Administers and determines contents Community: Visit and contribute blog posts |
+
+
+ Wiki |
+ - Project Meeting Minutes
- SIG Meeting Minutes
- Task Force Meeting Minutes
- Collaborative Editing
|
+ Staff: Administers and creates new spaces Community: Creates and edits pages |
+
+
+ LFX Meetings (Zoom) |
+ - Project, SIG, and TAC meetings: All project, SIG, and TAC meetings must be held using LFX meetings. This ensures that a recording of the meeting is captured and available for people to catch up on what they may have missed. Send an email to operations@openwallet.foundation to get your meetings scheduled.
|
+ Staff: Administers and creates new meetings Community: Attends meetings and listen to recordings |
+
+
+ YouTube |
+ - Community meeting recordings
- Webinar recordings
- Event recordings
|
+ Staff: Administers and adds videos and playlists Community: Watch videos |
+
+
+ Social Media |
+ - Posts about activities and events that the community may be interested in
- Posts to announce new projects, SIGs, Task Forces, blog posts
|
+ Staff: Administers and posts content Community: Reads content |
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Overview
+This document outlines the process for publishing deliverables in the OpenWallet Foundation technical community. These deliverables will be created by task forces, special interest groups, or projects. The types of deliverables they can create depend on their goals,
+objectives, and scope. Here are some examples:
+
+- Reports: Summarize findings or recommendations. These might be formal or informal.
+- Action Plans: Outline the steps necessary to address a particular challenge or problem. These plans might include specific tasks, timelines, and responsible individuals.
+- Recommendations: Provide guidance or proposals for solving problems, improving processes, or addressing gaps.
+- Guidelines: Outline best practices or procedures for a specific industry, domain, or project.
+- Templates and Tools: Serve as a starting point for creating new content and help users complete tasks, solve problems, or achieve specific goals frameworks that can be used by others.
+- Whitepapers: Provide detailed analysis, data, or insights to help others understand a particular issue or opportunity. These are typically in-depth reports on complex topics.
+- Case Studies: Illustrate the impact of real-world examples or hypothetical scenarios, including recommendations or findings.
+- Frameworks and Models: Describe how to approach a particular problem or challange through conceptual frameworks, models, or architectures.
+- Surveys and Research Reports: Gather data or validate hypotheses via surveys, interviews, or research studies, culminating in reports summarizing findings.
+- Best Practices and Playbooks: Outline best practices for specific scenarios, industries, or processes, providing guidance on how to navigate complex situations.
+- Metrics and KPIs: Determine how to measure progress toward goals or track the effectiveness of initiatives.
+- Process Improvements: Identify areas for process improvement and develop new procedures, workflows, or tools to streamline operations or enhance efficiency.
+- Training and Education Materials: Equip others with the knowledge and skills needed to tackle a specific challenge. Might include items such as curricula, tutorials, or guides.
+- Scoping Documents: Outline the scope, objectives, and deliverables of a project, ensuring everyone is on the same page.
+- Lessons Learned Reports: Summarize learnings, what worked well, and what didn't.
+
+Process
+There are three stages of an OWF deliverable -- draft, review, and released.
+flowchart
+ d[Draft]
+ r[Review]
+ c{Ready for Release?}
+ v[Released]
+
+ d -->|Submission| r
+ r --> c
+ c -->|Make Changes| d
+ c -->|Create Release| v
+A deliverable begins as a "draft" and retains this status until submitted to the community for review. At this point, the deliverable will be considered to be in the "review" stage and retains this status until the review period has ended. After the review period has ended, the task force, special interest group, or project will determine if the deliverable is ready for release. If the task force, special interest group, or project chooses to make changes, the deliverable will return to a "draft" stage where they can address the concerns of the community. The task force, special interest group, or project can also determine that the deliverable is ready for release. In which case, a "released" version can be created. See required contents for more information on what should be included within a "released" deliverable.
+Draft
+During the "draft" stage, the deliverable is being prepared by the task force, special interest group, or project. This includes writing the technical content and ensuring that it meets the standards of the OWF technical community. If there are any concerns about the technical content that cannot be addressed by consensus of the task force, special interest group, or project members, then the community may address these concerns during the "review" stage.
+Submission
+The task force, special interest group, or project lead may submit a version of their deliverable to the community for review. They can do this by sending an email to the TAC mailing list. The email should include the following information:
+
+- A brief description of the deliverable.
+- A link to the deliverable. Ideally, this should be a link to a pull request that contains the version of the deliverable where people in the community will be able to provide their feedback.
+- A link to the task force, special interest group, or project that submitted the deliverable.
+
+Review
+The applicable period to review a submitted deliverable will be no shorter than four weeks. The community will make reasonable efforts to provide feedback on the submitted version during the review period and provide any critical comments or objections, with sufficient specificity for the task force, special interest group, or project members to respond and, if required, to facilitate resolution.
+
+
Info
+
Comments and feedback can be provided by anyone in the OWF community.
+
Ready for Release
+After the applicable review period has elapsed, the task force, special interest group, or project members can review the feedback received and determine if the deliverable is ready for review. If the task force, special interest group, or project chooses to make changes, the deliverable will return to a "draft" stage where they can address the concerns of the community. The task force, special interest group, or project can also determine that the deliverable is ready for release. In which case, a "released" version can be created.
+Released
+The task force, special interest group, or project should ensure that the required contents are included in any release.
+Required Contents
+Copyright Notice
+
+
Important
+
If the deliverable originated from an external entity that has already provided a copyright notice, there is no need to replace that notice.
+
The copyright notice must be included in all versions of the deliverable. The copyright notice should include the OpenWallet Foundation as well as the year of publication.
+
+
Quote
+
Copyright © 2024 OpenWallet Foundation.
+
License Notice
+The license notice must be included in all versions of the deliverable. The license notice should include a reference to the CC-BY-4.0 license.
+
+Disclaimer
+A disclaimer should be included in all versions of the deliverable. The disclaimer should include the following text:
+
+
Quote
+
These materials are a deliverable of the OWF community. If you have concerns or suggestions regarding the content, please file a pull request.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Elections
+Electing a Chair
+
+
From the OWF Charter
+
The TAC is responsible for ... electing annually a chairperson to preside over meetings, set the agenda for meetings, ensure meeting minutes are taken and who will also serve on the Governing Board as the TAC’s representative (the “TAC Representative”).
+
The TAC voting members (as defined by the charter) will elect a chair on a yearly basis. Only TAC voting members are eligible to run for the TAC chair seat. Electing a chair will be completed through the voting process outlined below. If the TAC chair must leave their position during their term or is otherwise unable to fulfill their duties, they should submit a resignation and allow the TAC to fill the vacancy using the process outlined below.
+Electing a Vice Chair
+The TAC voting members (as defined by the charter) will elect a vice chair on a yearly basis. Only TAC voting members are eligible to run for the TAC vice chair seat. Electing a vice chair will be held in conjunction with the chair election using the voting process outlined below. The person with the second highest number of votes will serve as the vice chair. If the TAC vice chair must leave their position during their term or is otherwise unable to fulfill their duties, they should submit a resignation and allow the TAC to fill the vacancy using the process outlined below.
+Electing "At Large" Representatives
+
+
Implied from the OWF Charter
+
The TAC is responsible for ... appointing up to two "at large" representatives to the TAC.
+
The TAC voting members (as defined by the charter) can appoint up to two "at large" representatives to the TAC. The election process for "at large" representatives will occur on a yearly basis. Members of the community can nominate themselves for the position. Alternatively, a TAC voting member can nominate a member of the community; however, the nominee must actively affirm their candidacy. Electing "at large" representatives will be completed through the voting process outlined below. If the "at large" representative must leave their position during their term or is otherwise unable to fulfill their duties, they should submit a resignation. "At large" vacancies will be handled using the process outlined below.
+Voting Process
+
+Voting occurs by a time-limited Helios Voting ballot.
+Voting Schedule
+The following is the default timeline for voting. The times can be adjusted to avoid weekends and holidays, but it is essential that the final schedule be published in advance and adhered to.
+
+- Call for nominations: Noon PT, E-16 days
+- End of call for nominations: Noon PT, E-9 days
+- A ballot will be distributed on: E-7 days
+- The election will be completed on: Noon PT, E-day and election results are announced
+
+
+
Nominations
+
Nominees should outline their qualifications and provide a statement explaining why they would be a good choice for the seat.
+
Vacancies
+TAC Chair Vacancy
+Should the TAC Chair seat become vacant, the vacancy will be filled by the vice chair who will serve the remainder of the original term.
+TAC Vice Chair Vacancy
+Should the TAC Vice Chair seat become vacant, the vacancy will be filled by using the voting process outlined above and the replacement will serve the remainder of the original term.
+TAC "At Large" Representative Vacancy
+Should a TAC "at large" representative seat become vacant, the vacancy will be filled at the next indicative election, by electing a person for a full new term, not by serving out the vacant term.
+
+
Why?
+
A TAC "at large" vacancy is not filled immediately because the charter does not specify a lower limit for TAC "at large" representatives; it only specifies an upper limit.
+
Should a TAC premier sponsor representative seat become vacant, the premier sponsor will immediately appoint a new representative.
+TAC Project Representative Vacancy
+Should a TAC Project representative seat become vacant, the technical oversight body (e.g., a technical steering committee) for the TAC project will immediately appoint a new representative.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Governing Documents
+The following are the governing documents used by the OpenWallet Foundation's Technical Advisory Council.
+Foundation Governance
+The OpenWallet Foundation is governed by the following documents, of which the Technical Advisory Council follows:
+
+Technical Advisory Council Governance
+The Technical Advisory Council is governed with the following documents:
+
+Project Requirements
+The Technical Advisory Council has created the following requirements for projects:
+
+Project Resources
+The Technical Advisory Council offers the following services and tooling to projects:
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Maintainer Inactivity Policy
+
+
Note
+
This policy applies to projects that do not have an explicit maintainer inactivity policy. Where a project has an established and functioning policy, only that project's policy will apply.
+
OpenWallet Foundation very much appreciates the contributions of all maintainers but removing write privileges is in the interest of an orderly and secure project.
+Activity can be code contributions, code reviews, issue reporting, or any other such activity trackable by GitHub attributed to a OpenWallet Foundation repository.
+When a maintainer has not had any activity in a particular project for three months they will receive a notification informing them of the inactivity policies. The means and manner of notification (email, github mentions, etc.) will be at the discretion of the TAC Chair or who the TAC Chair designates.
+When a maintainer has not had any activity in a particular project for six months a proposal will be opened up to move the maintainer from active status to emeritus status. A member of the TAC or a OpenWallet Foundation staff member will open this proposal. Any permissions to approve pull requests or commit code and any other such privileges associated with maintainer status will be removed.
+The proposal will be in the form of a pull request (PR) to the relevant project repositories updating their maintainer lists. The inactive maintainer will be notified of this via an "at" @ mention in the PR. The PR will be open for at least one week to allow time for the project and maintainer to comment.
+Inactive maintainers who express an intent to continue contributing may request a three-month extension. This request shall be made in the pull request updating their active maintainer status. Typically, only one such extension will be granted.
+Maintainers who have been moved to emeritus status may return to active status when their activity within the project resumes and the current maintainers of the project approve their reactivation.
+An OpenWallet Foundation Foundation staff member will provide a report (or maintain an automated means to generate a report) of the most recent GitHub tracked actions for contributors at regular intervals to the TAC. It will be the TAC's responsibility to act on the data.
+Credits
+This document is based on the Hyperledger Foundation's Inactivity policy
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+MAINTAINERS.md File Contents
+All OpenWallet Foundation projects MUST have a MAINTAINERS file (MAINTAINERS.md or MAINTAINERS.rst) at the top-level directory of the source code. This document will provide specifics on what to include in the MAINTAINERS file.
+List of Project Maintainers
+The first thing that MUST be included in the MAINTAINERS file is a list of the project's maintainers, both active and emeritus.
+It is recommended that the lists be sorted alphabetically and contain the maintainers name, GitHub ID, LFID, Chat ID, Email, Company Affiliation, and Scope.
+
+
Important
+
+- The email for a maintainer MUST be specified and be a reliable mechanism to contact the maintainer.
+- Scope is dependent on the project and may not exist for a given project. Scope could be the whole project, a specific repository, specific directories in a repository, or high-level description of responsibility (e.g., Documentation).
+
+
The following shows the suggested format for the information:
+
+
Example
+
Active Maintainers
+
+
+
+| Maintainer |
+GitHub ID |
+LFID |
+Email |
+Chat ID |
+Company Affiliation |
+Scope |
+
+
+
+
+ |
+ |
+ |
+ |
+ |
+ |
+ |
+
+
+
+
Emeritus Maintainers
+
+
+
+| Maintainer |
+GitHub ID |
+LFID |
+Email |
+Chat ID |
+Company Affiliation |
+Scope |
+
+
+
+
+ |
+ |
+ |
+ |
+ |
+ |
+ |
+
+
+
+
What Does Being a Maintainer Entail
+The MAINTAINERS file SHOULD contain information about the different types of maintainers that exist (whole project, repo, part of repo) and what their duties are (e.g., maintainers calls, quarterly reports, code reviews, issue cleansing).
+How to Become a Maintainer
+The MAINTAINERS file SHOULD contain information about how to become a maintainer for the project. This section SHOULD list specific information about what is required. Information that SHOULD be included in this section:
+
+- What is required before someone can be considered to become a maintainer
+- Consider whether there should be different requirements based on the scope (whole project, repo, part of repo) of maintainership
+- Whether sponsorship by an existing maintainer is required
+- How maintainers are proposed to the community. A number of open source projects require that a PR be done against the
MAINTAINERS file to make this proposal
+- How many maintainers must approve the proposed maintainer. This should include information about what happens if someone vetoes the proposal
+- How long the existing maintainers have to respond to the proposal
+
+How Maintainers are Removed or Moved to Emeritus Status
+The MAINTAINERS file SHOULD contain information about how a maintainer is removed from the list of active maintainers. Information that SHOULD be included in this section:
+
+- What are the reasons a maintainer would be removed from the list of active maintainers
+- How this is proposed; similar to the way in which maintainers are added, one way to do this is via a PR against the
MAINTAINERS file
+- How an emeritus maintainer becomes active again
+
+Credits
+This document is based on the Hyperledger Foundation's MAINTAINERS guideline.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+OpenWallet Foundation (OWF) provides a number of paid developer tools for projects. Below, we list the ones that our projects currently have access to and are supported by the OWF staff. We emphasize that just because a tool is not on this list does not mean projects cannot use it; it just means that the project maintainers may have to support it themselves and may need to pay for the tooling. The Governing Board has final say over the budget for tooling and its support.
+OWF recommends the following tools that should be optimal for most projects:
+
+-
+
Technical Documentation: markdown, GitHub pages, and Material for MkDocs.
+
+-
+
Informal documentation and details (e.g. meeting notes, meeting agendas, long-term planning documentation, etc.): GitHub
+
+-
+
CI: GitHub Actions
+
+-
+
Artifact Storage: GitHub Packages
+
+-
+
Communication: Discord
+
+-
+
Bug Tracking: GitHub Issues and GitHub Projects
+
+-
+
Mailing Lists: Groups.io
+
+-
+
Meetings: Zoom via LFX Meetings
+
+
+Finally we emphasize that this list does not cover security-related tools or services.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Project and Lab Services
+This document provides details about what resources are available for OpenWallet Foundation projects and labs. If there are any questions about anything on the document or if you'd like to leverage any of these resources for your project or lab, feel free to reach out to community-architects at openwallet dot foundation.
+
+
+
+| Service |
+Lab |
+Growth Project |
+Impact Project |
+
+
+
+
+| Infrastructure |
+ |
+ |
+ |
+
+
+| Github repos |
+Yes |
+Yes |
+Yes |
+
+
+| Chat channel |
+Yes |
+Yes |
+Yes |
+
+
+| Mailing list |
+Optional |
+Yes |
+Yes |
+
+
+| Paid tooling |
+Yes (with some restrictions at the discretion of OpenWallet Foundation staff) |
+Yes |
+Yes |
+
+
+| Marketing |
+ |
+ |
+ |
+
+
+| Access to OpenWallet Foundation's channels (social, newsletters, blogs, meetups, etc) |
+Yes (with some restrictions at the discretion of the Marketing lead) |
+Yes |
+Yes |
+
+
+| Page on the OpenWallet Foundation site |
+ |
+Yes |
+Yes |
+
+
+| Creation of an official project name and logo |
+ |
+Yes |
+Yes |
+
+
+| Coordinate promotion of major project milestones and releases |
+ |
+Yes |
+Yes |
+
+
+| Option to create a Twitter account |
+ |
+Yes |
+Yes |
+
+
+| Priority placement on site |
+ |
+ |
+Yes |
+
+
+| Swag (stickers and potentially other items with the project logo) |
+ |
+ |
+Yes |
+
+
+| Onboarding New Users and Contributors |
+ |
+ |
+ |
+
+
+| Able to take part in OpenWallet Foundation's annual Mentorship program |
+TBD |
+TBD |
+TBD |
+
+
+| Able to have project/lab featured in a contribution campaign |
+Yes (at the discretion of OpenWallet Foundation staff) |
+TBD |
+TBD |
+
+
+| Workshops |
+ |
+ |
+Yes |
+
+
+| Documentation and Translation support |
+TBD |
+TBD |
+TBD |
+
+
+| Training/Certification |
+ |
+ |
+ |
+
+
+| LF created training course |
+ |
+Yes (at the discretion of LF Training) |
+Yes (at the discretion of LF Training) |
+
+
+| LF created certification |
+ |
+ |
+Yes (at the discretion of LF Training) |
+
+
+| Other |
+ |
+ |
+ |
+
+
+| License scanning |
+ |
+Yes |
+Yes |
+
+
+| Security audits |
+ |
+Not usually (although this can be done at the discretion of staff) |
+Yes (at the discretion of OpenWallet Foundation staff) |
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Project Annual Review Process
+Overview
+The TAC will undertake an annual review of all OpenWallet Foundation projects. This annual review will include an assessment as to whether:
+
+- each Lab is active
+- each Growth Stage project is making adequate progress towards the Impact Stage
+- each Impact Stage project is maintaining progress to remain at the Impact Stage
+
+Reviews will start on the yearly anniversary of the project being accepted or moving to a new stage. The review will include a set of recommendations for each project to improve and/or recommendation to move a project across stages.
+Projects can be provided with an extension of time in their current stage (up to the discretion of the TAC).
+The project lifecycle contains Acceptance Criteria for moving a project to a new stage.
+Filing an Annual Review
+OpenWallet Foundation staff will notify the project maintainers when the project review is due.
+Project maintainers are responsible for agreeing between them who will complete the annual review. One of the maintainers should create the review in GitHub under openwallet-foundation/tac/docs/projects/reviews.
+
+- Raise a PR titled [Project name] [year] Annual Review (e.g., Amazing Project 2024 Annual Review)
+- The PR should include a file called
<year>-<project name>-annual.md (e.g., 2024-amazingproj-annual.md) with the contents described below
+- Send an email to the TAC mailing list so that the community knows the PR is there and can comment on it
+
+If your annual review is not submitted within two months of notification, we will take this as a sign that the project is not under active maintenance and the TAC is likely to decide to archive the project and move it to Emeritus status.
+
+
Success
+
If a project has genuinely stalled we can save everyone’s time and effort by archiving it.
+
Annual Review Contents
+Your annual review should answer the following questions:
+
+- Include information about your project's contributions and activity. We will be looking for signs of consistent or increasing contribution activity. Please feel free to add commentary to add colour to the numbers and graphs we will see on Insights.
+- How many maintainers do you have, and which organisations are they from? (Feel free to link to an existing MAINTAINERS file if appropriate.)
+- What do you know about adoption, and how has this changed since your last review or since being accepted into OWF? If you can list companies that are adopters of your project, please do so. (Feel free to link to an existing ADOPTERS file if appropriate.
+- How has the project performed against its goals since the last review? (We won't penalize you if your goals changed for good reasons.)
+- What are the current goals of the project? For example, are you working on major new features? Or are you concentrating on adoption or documentation?
+- How can the OpenWallet Foundation help you achieve your upcoming goals?
+- Do you think that your project meets the criteria for another stage (see Project Lifecycle Acceptance Criteria for the different stages)?
+
+A template has been provided for your use.
+Annual Review by the TAC
+Annual reviews are performed in order to check in with projects, ascertain their progress, and address any outstanding questions.
+
+- A TAC representative volunteers to lead the review once the project files a PR.
+- The assigned TAC member reviews the content of the PR and analyzes the project for community health indicators, their findings are placed within a thread in the private TAC channel for discussion.
+- findings should highlight important facts about the project that could influence the TACs decision around the future of the project, its current stage, and path to other stages, etc.
+- the thread should always include whether the project's view of themselves is accurate and the ask of the TAC is reasonable to assist the project moving forward.
+
+
+- The project's maintainers are invited to the public TAC meeting to engage in TAC led discussion around the project. Project maintainers are not obligated to attend.
+- The assigned TAC member provides a summary of the project and leverages the thread's content as the basis of discussion.
+- discussion typically focuses on what is going well with the project and areas to improve.
+
+
+- The project's maintainers are invited to use this time to voice any concerns and requests for help they may have that are not captured in the PR (or highlight asks within the PR).
+- At the conclusion of the public meeting, the TAC votes to approve the annual review. Should a concern be registered on a project, the vote will be held separately.
+- After the meeting wraps up, the assigned TAC member may summarize the discussion on the PR in the form of a comment to document information for the project and community.
+
+Review Outcomes
+The outcome of the annual review is either:
+
+Credits
+Ideas were taken from CNCF's Sandbox Annual Review Process.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Project Lifecycle
+Overview
+This governance policy describes how an open source project can formally join the OpenWallet Foundation via the Project Proposal Process and how an existing project within the OpenWallet Foundation can move through the lifecycle via the Project Stage Change Proposal Process. It describes the Stages a project may be admitted under and what the criteria and expectations are for a given stage, as well as the acceptance criteria for a project to move from one stage to another. It also describes the Annual Review Process through which those changes will be evaluated and made.
+Project progression - movement from one stage to another - allows projects to participate at the level that is most appropriate for them given where they are in their lifecycle. Regardless of stage, all OpenWallet Foundation projects benefit from a deepened alignment with existing projects, and access to mentorship, support, and Foundation resources.
+
+Project Proposal Process
+Introduction
+This governance policy sets forth the proposal process for projects to be accepted into the OpenWallet Foundation. The process is the same for both existing projects which seek to move into the OpenWallet Foundation and new projects to be formed within the OpenWallet Foundation.
+Project Proposal Requirements
+Projects must be formally proposed via GitHub. Project proposals submitted to the OpenWallet Foundation should provide the following information to the best of their ability:
+
+- name of project
+- preferred maturity level (see stages below)
+- project description (what it does, why it is valuable, origin and history)
+- statement on alignment with the OpenWallet Foundation mission
+- link to current Code of Conduct (if one is adopted already)
+- sponsor from the TAC, if identified (a sponsor helps mentor projects)
+- project license (OSI-approved permissive open source licenses, Apache 2.0 by default)
+- source control (OpenWallet Foundation GitHub by default)
+- issue tracker (OpenWallet Foundation GitHub by default)
+- external dependencies (including licenses)
+- release methodology and mechanics
+- names of initial maintainers, if different from those submitting proposal
+- existing financial sponsorship (if exists)
+- infrastructure needs or requests (OpenWallet Foundation provides a set of services for projects and labs. Please note which of these you will utilize and what else is required)
+
+Project Acceptance Process
+
+- Impact stage and Growth stage projects are required to present their proposal at a TAC meeting. Labs will be reviewed and approved directly via the project proposal PR. Labs may present at a TAC meeting if they would like to gain visibility from other community members, and the proposer should note this in the proposal.
+-
+
The TAC may ask for changes to bring the project into better alignment with the OpenWallet Foundation (adding a governance document to a repository or adopting a Code of Conduct, for example).
+
+
Warning
+
The project will need to make these changes in order to progress further.
+
+-
+
Impact stage and Growth stage projects are accepted via a two-thirds supermajority vote of the TAC. Labs are accepted via a simple majority of the TAC.
+
+- Satisfaction of the requirements of the initial stage of the project. The TAC will determine the appropriate initial stage for the project. The project can apply for a different stage via the review process.
+- If the project is accepted by the TAC, a project charter and contribution agreement (if necessary) can be obtained by completing this form. Here is sample project charter that you can review. A collaboration agreement is needed for existing projects and provides an agreement to transfer the project name, trademarks, and electronic account assets (github repo, social media accounts, domain names, etc.) to Linux Foundation Europe for the benefit of the OpenWallet Foundation.
+
+Project Stage Change Proposal Process
+Introduction
+This governance policy sets forth the proposal process for projects within the OpenWallet Foundation that are seeking to move to another stage in the project lifecycle.
+Proposal Process
+The project's current proposal located in Project Proposals GitHub Repository must be updated via a PR. The project proposal should be updated to reflect the latest template, as well as any updates to the sections to reflect why the project should be considered for a new stage.
+Project Stage Change Acceptance Process
+The same acceptance project outlined above will be used for projects wishing to change lifecycle stage.
+Stages
+Every OpenWallet Foundation project has an associated maturity level. Proposed projects should state their preferred maturity level.
+All projects may attend TAC meetings and contribute work regardless of their stage.
+flowchart
+ p[Proposal]
+ subgraph as[Active Stages]
+ l[Labs]
+ g[Growth]
+ i[Impact]
+ end
+ subgraph is[Inactive Stages]
+ e[Emeritus]
+ end
+ p --> as
+ l <--> g
+ l <--> i
+ g <--> i
+ as --> is
+Labs
+Definition
+Labs are those which the TAC believes are, or have the potential to be, important to the ecosystem of Technical Projects or the open wallet ecosystem as a whole. They may be early-stage code just getting started, or they may be long-established projects with minimal resource needs. The Labs stage provides a beneficial, neutral home for these projects in order to foster collaborative development and provide a path to deeper alignment with other OpenWallet Foundation projects via the project lifecycle process.
+Examples
+
+- Experimental code that is designed to extend one or more OpenWallet Foundation projects with functionality or interoperability libraries.
+- Independent code that fits within the Foundation's mission and provides potential to meet an unfulfilled need.
+- Code commissioned or sanctioned by the OpenWallet Foundation.
+- Any code that intends to join the Growth or later stages in the future and wishes to lay the foundation for that transition.
+
+Expectations
+End users should evaluate Labs with care, as this stage does not set requirements for community size, governance, or production readiness. Labs will receive minimal support from the Foundation. Labs will be reviewed on an annual basis; they may also request a status review by submitting a report to the TAC.
+Acceptance Criteria
+To be considered for the Labs Stage, the project must meet the following requirements:
+
+Upon acceptance, Labs must list their status prominently on their website/README (e.g., PROJECT, an OpenWallet Foundation Lab).
+Growth Stage
+Definition
+The Growth Stage is for projects that are interested in reaching the Impact Stage, and have identified a growth plan for doing so. Growth Stage projects will receive mentorship from the TAC and are expected to actively develop their community of contributors, governance, project documentation, roadmap, and other variables identified in the growth plan that factor into broad success and adoption.
+In order to support their active development, projects in the Growth stage have a higher level of access to Foundation resources, which will be agreed upon and reviewed on a yearly basis. A project's progress toward its growth plan goals will be reviewed on a yearly basis, and the TAC may ask the project to move to the Labs stage if progress on the plan drops off or stalls.
+Examples
+
+- Projects that are on their way or very likely to become Growth or Impact projects.
+- Projects that have developed new growth targets or other community metrics for success.
+- Projects that are looking to create a lifecycle plan (maintainership succession, contributor programs, version planning, etc.).
+- Projects that need more active support from the Foundation or TAC mentorship in order to reach their goals.
+
+Expectations
+Projects in the Growth stage are generally expected to move out of the Growth stage within two years. Depending on their growth plans, projects may cycle through Labs, Growth, or Impact stage as needed.
+Acceptance Criteria
+To be considered for Growth Stage, the project must meet the Labs requirements as well as the following:
+
+- A presentation at the meeting of the TAC.
+- 2 TAC sponsors to champion the project and provide mentorship as needed.
+- Development of a growth plan, to be done in conjunction with their project mentor(s) at the TAC.
+- Development of a project roadmap that provides differentiated features and capabilities and the timeframe for completion.
+- Document that it is being used successfully in either proof of concepts or pilots by at least two independent end users which, in the TAC’s judgment, are of adequate quality and scope.
+- Demonstrate a substantial ongoing flow of commits and merged contributions.
+- Demonstrate that the current level of community participation is sufficient to meet the goals outlined in the growth plan and roadmap.
+- Since these metrics can vary significantly depending on the type, scope and size of a project, the TAC has final judgment over the level of activity that is adequate to meet these criteria.
+- Demonstrates how this project differs from existing projects in the Growth and Impact stages.
+- Receive a two-thirds supermajority vote of the TAC to move to Growth Stage.
+
+Upon acceptance, Growth projects must list their status prominently on their website/README (e.g., PROJECT, an OpenWallet Foundation Project).
+Impact Stage
+Definition
+The Impact Stage is for projects that have reached their growth goals and are now on a sustaining cycle of development, maintenance, and long-term support. Impact Stage projects are used commonly in enterprise production environments and have large, well-established project communities.
+Examples
+
+- Projects that have publicly documented release cycles and plans for Long Term Support ("LTS").
+- Projects that have themselves become platforms for other projects.
+- Projects that are able to attract a healthy number of committers on the basis of its production usefulness (not simply 'developer popularity').
+- Projects that have several, high-profile or well known end-user implementations.
+
+Expectations
+Impact Stage projects are expected to participate actively in TAC proceedings, and as such have a binding vote on TAC matters requiring a formal vote, such as the election of a TAC representative. They receive ongoing financial and marketing support from the Foundation, and are expected to cross promote the Foundation along with their activities.
+Acceptance Criteria
+To move from Labs or Growth status, or for a new project to join as an Impact project, a project must meet the Growth stage criteria plus:
+
+- Have a defined governing body of at least 5 or more members (owners and core maintainers), of which no more than one-third is affiliated with the same employer. In the case there are 5 governing members, 2 may be from the same employer.
+- Have a documented and publicly accessible description of the project's governance, decision-making, and release processes.
+- Have a healthy number of maintainers from at least two organizations. A maintainer is defined as someone with the commit bit; i.e., someone who can accept contributions to some or all of the project.
+- Have a Code of Conduct in a form acceptable to the OpenWallet Foundation.
+- Explicitly define a project governance and maintainer process. This is preferably laid out in a
GOVERNANCE.md file and references a CONTRIBUTING.md and MAINTAINERS.md file showing the current and emeritus maintainers (see MAINTAINERS.md File Contents for more information).
+- Document that it is being used successfully in production by at least two independent end users which, in the TAC’s judgment, are of adequate quality and scope.
+- Have a public list of project adopters for at least the primary repo (e.g.,
ADOPTERS.md or logos on the project website).
+- Have a good standing with respect to security.
+- Other metrics as defined by the applying Project during the application process in cooperation with the TAC.
+- Receive a supermajority vote from the TAC to move to Impact stage. Projects can move directly from Labs to Impact, if they can demonstrate sufficient maturity and have met all requirements.
+
+Upon acceptance, Impact projects must list their status prominently on their website/README (e.g., PROJECT, an OpenWallet Foundation Project).
+Emeritus Stage
+Definition
+Emeritus projects are projects which the maintainers feel have reached or are nearing end-of-life. Emeritus projects have contributed to the ecosystem, but are not necessarily recommended for modern development as there may be more actively maintained choices. The Foundation appreciates the contributions of these projects and their communities, and the role they have played in moving the ecosystem forward.
+Examples
+
+- Projects that are "complete" by the maintainers' standards.
+- Projects that do not plan to release major versions in the future.
+
+Expectations
+Projects in this stage are not in active development. Their maintainers may infrequently monitor their repositories, and may only push updates to address security issues, if at all. Emeritus projects should clearly state their status and what any user or contributor should expect in terms of response or support. If there is an alternative project the maintainers recommend, it should be listed as well. The Foundation will continue to hold the IP and any trademarks and domains, but the project does not draw on Foundation resources.
+Acceptance Criteria
+Projects may be granted Emeritus status via a two-thirds vote from the TAC and with approval from project ownership. In cases where there is a lack of project ownership, only a two-thirds vote from the TAC is required.
+Upon acceptance, Emeritus projects must list their status prominently on their website/README.
+
+
Info
+
If members of the community would like to re-active a project that has been granted Emeritus status, the community must start the lifecycle over again by submitting a new proposal to the TAC.
+
Annual Review Process
+Each project will undergo an annual review process to determine whether projects are in the stage that accurately reflects their needs and goals.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Release Taxonomy
+
+Releases at OpenWallet Foundation must be done according to the SemVer taxonomy. In addition to the semantic versioning scheme, where we use MAJOR.MINOR.PATCH numbering, following the established guidance given in the semver specification, it is also strongly encouraged that projects should use the following tags, as permitted by semver:
+
+preview
+Not feature complete, but most functionality is implemented. Any missing functionality that is committed to the production release is identified, and there are specific people working on those features. Not heavily performance tuned, but performance testing has started with the first few hotspots identified and perhaps even addressed. No highest priority issues are in an open state. First-level developer documentation provided to help new developers with the learning curve.
+alpha
+Feature complete, for all features committed to the production release. Ready for Proof of Concept-level deployments. Performance can be characterized in a predictable way, so that basic PoC's can be done within the bounds of published expectations. APIs are documented. First attempts at end-user documentation have been made. Developer documentation is further advanced. No highest priority issues are in an open state.
+beta
+Feature complete for all features committed to the production release, perhaps with optional features when safe to add. Ready for Pilot-level engagements. Performance is very well characterized and active optimizations are being done, with a target set for the Production release. No highest priority or high priority bugs are in an open state. Developer documentation is complete; end-user documentation is mostly done.
+rcN
+For a forthcoming production release, we will prepare multiple candidate releases intended to be heavily tested by the community. As we cycle through resolving uncovered issues, we will issue another when no remaining highest or high priority issues remain, and repeat until we feel confident in releasing a production release, with no qualifier. e.g. 1.0.
+Credits
+This document is based on the Hyperledger Foundation's Release Taxonomy policy.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Roles and Responsibilities
+Technical Advisory Council
+The OpenWallet Foundation charter states that the TAC is responsible for:
+
+
Quote
+
+- maintaining an overall strategic vision for technical collaboration and coordinating collaboration among Technical Projects, including development of an overall technical vision for the community;
+- making recommendations to the Budget Committee of resource priorities for Technical Projects;
+- electing annually a chairperson to preside over meetings, set the agenda for meetings, ensure meeting minutes are taken and who will also serve on the Governing Board as the TAC’s representative (the “TAC Representative”);
+- creating, maintaining and amending project lifecycle procedures and processes, deciding where Technical Projects fall within that lifecycle;
+- determining when a technical project should be admitted as a Technical Project or any Technical Project should be considered a TAC Project; and
+- such other matters related to the technical role of the TAC as may be communicated to the TAC by the Governing Board.
+
+
TAC Members
+TAC members are expected to:
+
+- Subscribe to the TAC mailing list and the OpenWallet Github organization to stay aware of the TAC related updates and issues
+- Regularly participate in the TAC meetings
+- Bring up and help resolve any issues related to the needs of the OpenWallet technical community
+- Participate in, and optionally chair, the Task Forces set up by the TAC to address specific issues
+- Act as stewards for OpenWallet Foundation promoting and helping grow the organization and its activities by engaging of their own accord in activities such as posting on social media, responding to questions raised in forums, helping new community members find their way around, and giving talks at conferences on OpenWallet Foundation related topics
+- Participate in the appointment and election of "at large" representatives
+
+TAC Chair
+The TAC chair has the following additional responsibilities:
+
+- Running the TAC meetings, such as the TAC calls per the agreed upon schedule. This includes: setting up and publishing an agenda, running the meeting, and ensuring any outcome is duly recorded
+- Representing the TAC, and more broadly the OpenWallet Foundation technical community, on the Governing Board, and giving updates to the Governing Board on TAC activities
+
+TAC Vice Chair
+The TAC vice chair has the following additional responsibilities:
+
+- Running the TAC meetings when the TAC Chair is unable, including setting up and publishing an agenda and ensuring any outcome is duly recorded
+- Helping to marshall people who want to talk during a meeting
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+PROJECT Security Policy
+Instructions
+The following is the best practices template security vulnerability disclosure
+policy for OpenWallet Foundation's projects. Please copy the text below, place it into the SECURITY.md file for the primary repository of your project,
+and adjust it as necessary for your project. Notably:
+
+- Remove this "Instructions" section.
+- Replace PROJECT in the title of this page with the name of your project.
+- Populate the Security Team section with maintainers who have agreed to be on the security team.
+- See the "Alternative" notes in the OpenWallet Foundation's security vulnerability disclosure policy document for how the "best practices" in this document can be changed to meet the needs of your project while still adhering to the OpenWallet Foundation's policies.
+
+Once your project's security vulnerability disclosure policy document is
+published, place a copy of it into each of your project's repositories
+(or link to the main repository's SECURITY.md).
+About this Document
+This document document defines how security vulnerability reporting is handled
+in this project. The approach aligns with the OpenWallet Foundation's security
+vulnerability disclosure policy. Please review that document to understand
+the basis of the security reporting for this project
+This policy borrows heavily from the recommendations of the OpenSSF
+Vulnerability Disclosure working group. For up-to-date information on the latest
+recommendations related to vulnerability disclosures, please visit the GitHub
+of that working group.
+If you are already familiar with what a security vulnerability disclosure policy
+is and are ready to report a vulnerability, please jump to Report
+Intakes.
+What Is a Vulnerability Disclosure Policy?
+No piece of software is perfect. All software (at least, all software of a
+certain size and complexity) has bugs. In open source development, members of
+the community or the public find bugs and report them to the project. A
+vulnerability disclosure policy explains how this process functions from the
+perspective of the project.
+This vulnerability disclosure policy explains the rules and guidelines for
+this project. It is intended to act as both a reference for
+outsiders–including both bug reporters and those looking for information on the
+project’s security practices–as well as a set of rules that maintainers and
+contributors have agreed to follow.
+Report Intakes
+This project uses the following mechanism to submit security
+vulnerabilities. While the security team members will do their best to
+respond to bugs disclosed in all possible ways, it is encouraged for bug
+finders to report through the following approved channel:
+
+Security Team
+The current security team is:
+
+
+
+| Name |
+Email ID |
+Chat ID |
+Area/Specialty |
+
+
+
+
+| <> |
+<> |
+<> |
+<> |
+
+
+| <> |
+<> |
+<> |
+<> |
+
+
+| <> |
+<> |
+<> |
+<> |
+
+
+
+The security team for this project must include at least three project
+Maintainers that agree to carry out the following duties and responsibilities.
+Members are added and removed from the team via approved Pull Requests to this
+repository. For additional background into the role of the security team, see
+the People Infrastructure section of the OpenWallet Foundation's security vulnerability disclosure policy.
+Responsibilities:
+
+-
+
Acknowledge receipt of the issue (see Report Intakes) to the reporter within 2 business days.
+
+-
+
Assess the issue. Engage with the reporter to ask any outstanding questions about the report and how to reproduce it. If the report is not considered a vulnerability, then the reporter should be informed and this process can be halted. If the report is still a regular bug (just not a security vulnerability), the reporter should be informed (if necessary) of the regular process for reporting bugs.
+
+-
+
Some issues may require more time and resources to correct. If a
+particular report is more complex, discuss an embargo period with the reporter.
+The embargo period should be negotiated with the reporter and must not be
+longer than 90 days.
+
+-
+
Create a patch for the issue (see Private Patch Deployment
+Infrastructure).
+
+-
+
Request a CVE for the issue (see CNA/CVE Reporting).
+
+-
+
Decide the date of public release.
+
+-
+
If applicable, notify members of the embargo list of the upcoming patch
+and release, as described above.
+
+-
+
Cut a new (software) release in which the bug is fixed.
+
+-
+
Publicly disclose the issue within 48 hours after the release (see GitHub Security Advisories).
+
+
+Discussion Forum
+Discussions about each reported vulnerability are carried out in the
+private GitHub security advisory about the vulnerability.
+If necessary, a private channel specific to the issue may be created on the
+OpenWallet Foundation's Discord server with invited participants added to the
+discussion.
+CNA/CVE Reporting
+This project maintains a list of Common Vulnerabilities and Exposures
+(CVE) and uses GitHub as its CVE numbering authority (CNA) for issuing
+CVEs.
+Embargo List
+This project maintains a private embargo list. If you wish to be added to
+the embargo list for a project, please email the [OpenWallet Foundation's
+security list], including the project name and reason for being added to the
+embargo list. Requests will be assessed by the security team in conjunction
+with the appropriate OpenWallet Foundation staff, and a decision will be made
+whether to accommodate the request.
+GitHub Security Advisories
+This project uses GitHub security advisories and the GitHub security process for handling security vulnerabilities.
+Private Patch Deployment Infrastructure
+In creating patches and new releases that address security vulnerabilities,
+this project uses the private development features of GitHub for security
+vulnerabilities. GitHub has extensive
+documentation
+about these features.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Security Vulnerability Disclosure Policy
+This document outlines the OpenWallet Foundation's security vulnerability
+disclosure policy
+that all OpenWallet Foundation projects MUST follow. The associated
+security template file is a "best practices" security vulnerability
+disclosure policy that project Maintainers SHOULD use for
+publishing the security policy and procedures for their project by copying the
+file into their project repositories and updating it according to the
+instructions in the document. This document includes the "best practices" text,
+and defines how project Maintainers can use alternatives to the best practices
+for their project. A project's resulting
+alternative policy MUST adhere to the OpenWallet Foundation's security
+vulnerability disclosure policy.
+All project repositories MUST have a published security vulnerability
+disclosure policy or have link to a common policy document for the project.
+In rare cases, a repository within a project MAY have a policy different
+from the project, as long as the repository policy also adheres to this
+OpenWallet Foundation's security vulnerability disclosure policy.
+About This Document
+This policy borrows heavily from the recommendations of the OpenSSF
+Vulnerability Disclosure working group. For up-to-date information on the latest
+recommendations related to vulnerability disclosures, please visit the GitHub
+of that working group.
+In each of the document's sections, and in the associated
+security template, the current OpenWallet Foundation's "best practices" are
+defined.
+
+
Alternative
+
Alternatives that a project may use exist for some sections and are contained in these "Alternative boxes". When projects vary from the current OpenWallet Foundation's best practices, the documented alternatives MUST adhere to this policy.
+
What Is a Vulnerability Disclosure Policy?
+No piece of software is perfect. All software (at least, all software of a
+certain size and complexity) has bugs. In open source development, members of
+the community or the public find bugs and report them to the project. A
+vulnerability disclosure policy explains how this process functions from the
+perspective of the project.
+This vulnerability disclosure policy explains the rules and guidelines for
+OpenWallet Foundation's projects. It is intended to act as both a reference for
+outsiders–including both bug reporters and those looking for information on the
+project’s security practices–as well as a set of rules that maintainers and
+contributors have agreed to follow.
+Vulnerability Disclosure Process and Associated Rules
+All OpenWallet Foundation's projects, including this project, follow the
+associated process
+and rules for vulnerability disclosures. We note that this outline is derived
+from the OpenSSF maintainers guide.
+Each project will have a security team. The security team
+will be comprised of maintainers or contributors to the project who are
+knowledgeable about security and is responsible for responding to and
+helping to fix security vulnerabilities.
+The security team for this project will do the following for each reported vulnerability:
+
+-
+
Acknowledge receipt of the issue (see Report Intakes) to the reporter within 2 business days.
+
+-
+
Assess the issue. Engage with the reporter to ask any outstanding questions about the report and how to reproduce it. If the report is not considered a vulnerability, then the reporter should be informed and this process can be halted. If the report is still a regular bug (just not a security vulnerability), the reporter should be informed (if necessary) of the regular process for reporting bugs.
+
+-
+
Some issues may require more time and resources to correct. If a
+particular report is more complex, discuss an embargo period with the reporter.
+The embargo period should be negotiated with the reporter and must not be
+longer than 90 days.
+
+-
+
Create a patch for the issue (see Private Patch Deployment
+Infrastructure).
+
+-
+
Request a CVE for the issue (see CNA/CVE Reporting).
+
+-
+
Decide the date of public release.
+
+-
+
If applicable, notify members of the embargo list of the upcoming patch
+and release, as described above.
+
+-
+
Cut a new (software) release in which the bug is fixed.
+
+-
+
Publicly disclose the issue within 48 hours after the release (see GitHub Security Advisories).
+
+
+Report Intakes
+OpenWallet Foundation's projects use the following mechanism to submit security
+vulnerabilities. While the security team members will do their best to
+respond to bugs disclosed in all possible ways, it is encouraged for bug
+finders to report through the following approved channel:
+
+
+Alternative
+Projects MAY publish in their security policy that they accept security vulnerability disclosures via other mechanism. The policy MUST document the necessary details in using the alternate reporting mechanism(s). Projects MUST accept reports via the recommended GitHub security vulnerability process.
+
+“People” Infrastructure
+This section details the required basic vulnerability disclosure infrastructure
+for all OpenWallet Foundation's projects. There are quite a few necessary
+pieces of infrastructure, and we go through them in detail here.
+Security Team
+Projects MUST have a security response team of at
+least three maintainers. This response team shall be set up BEFORE incidents
+happen so that people know who to contact and how to contact them when an
+emergency issue arises. It can be difficult to track down someone with unique
+knowledge (e.g. in a particular area of cryptography) who is capable of
+fixing a problem in a short period of time.
+
+-
+
Each security team member will be a member of
+any OpenWallet Foundation-wide security infrastructure.
+
+-
+
If a project has specialized code related to certain aspects of security
+or cryptography (e.g. consensus algorithms or cryptographic algorithms), then
+a corresponding specialist should be on the response team (e.g. someone
+knowledgeable in consensus or cryptography, respectively). If a specialist
+is not on the team, then the individual who is responsible for contacting or
+engaging the specialists should be designated in their stead. We emphasize
+that projects should have access to specialists in an area for which they
+maintain code while recognizing that it may not be practical for these experts
+to be on the response team.
+
+
+Each project/repository must have a table in the security document listing the
+team members in the following format.
+
+
+
+| Name |
+Email ID |
+Chat ID |
+Area/Specialty |
+
+
+
+
+| <> |
+<> |
+<> |
+<> |
+
+
+| <> |
+<> |
+<> |
+<> |
+
+
+| <> |
+<> |
+<> |
+<> |
+
+
+
+Discussion Forum
+Discussions about each reported vulnerability SHOULD be carried out in the
+private GitHub security advisory about the vulnerability. If necessary, a private
+channel specific to the issue MAY be created on the OpenWallet Foundation's
+Discord server with invited participants added to the discussion.
+
+Alternative
+Projects MAY document on their security policy that they use other forums for private discussion forums for approved maintainers and security team participants to discuss vulnerabilities. If other forum(s) are used, details about them MUST be included.
+
+CNA/CVE Reporting
+OpenWallet Foundation's projects maintain a list of Common Vulnerabilities and Exposures
+(CVE) and use GitHub as its CVE numbering authority (CNA) for issuing
+CVEs.
+
+Alternative
+A project MAY document in its security policy that it uses a different CVE numbering authority. For example, the project might add the following text to this section of their security policy document:
+This project uses the following CNA(s) in the following situations:
+1. `CNA_1`: `situation_1, can just state “default” if only one CNA`
+2. `CNA_2`: `situation_2`
+
+Embargo List
+An embargo list is a list of known, trusted entities that run
+large deployments of a given OpenWallet Foundation's project. These
+entities are notified ahead of time when important security patches are
+incoming to minimize potential security risks to large deployments of
+projects. Embargo lists are maintained by the security team for a given project/repository.
+Parties are on an embargo list for (usually) one of two reasons,
+because they can either help fix the problem (perhaps through testing a fix at
+scale) or they need extra time to help prepare their ecosystem to roll out
+fixes quickly. Approval is not given lightly: project leadership
+(maintainers) must be convinced that institutions on the list “need to know"
+about issues in advance.
+Participation in an embargo list should not be taken lightly. List members
+are expected to respect the materials shared through it and not disclose any
+information to unauthorized parties until the public disclosure date.
+Institutions are on this list because their presence helps the project and its
+users; if their actions do not help the project and its users, they can expect
+to be removed from the list.
+The list itself is private in order to make it slightly more difficult for
+attackers with vulnerabilities to find systems to attack. Entities may be
+added to the embargo list by a majority vote of the project security response
+team and should request to join the embargo list by contacting one or more of
+the members of the security response team. If there is an issue about embargo
+list membership where an entity feels like they are being dealt with unfairly
+by the security response team, then they are encouraged to bring up the issue
+in front of the OpenWallet Foundation's TAC, who can act as moderators.
+OpenWallet Foundation's projects maintain private embargo lists. If you wish to be added to
+the embargo list for a project, please email the [OpenWallet Foundation's
+security list], including the
+project name and reason for being added to the embargo list. Requests will be
+assessed by the respective OpenWallet Foundation's security team in conjunction with the
+appropriate OpenWallet Foundation staff, and a decision will be made to accommodate or not
+the request.
+
+Alternative
+Projects MAY choose to document in their security document that they do not have an embargo list. The reason for not having an embargo list SHOULD be included when a project chooses not to have an embargo list.
+
+GitHub Security Advisories
+OpenWallet Foundation's projects use GitHub
+security advisories and the GitHub security process for
+handling security vulnerabilities. In particular, this best practice is strongly recommended
+for projects that do not have a large number of security experts as the
+features serve as a nice set of guardrails to help make sure that things are
+done correctly.
+
+Alternative
+Projects MAY document in their security policy document that they use a security advisory mechanism other than GitHub to publish their disclosures. The alternate mechanism MUST be documented sufficiently for users to understand how to monitor the security advisories published by the project.
+
+Private Patch Deployment Infrastructure
+Patches to fix OpenWallet Foundation's project security vulnerabilities are typically
+developed without public visibility by using the private development features of
+GitHub. Projects with maintainers that are not familiar with these capabilities
+are encouraged to contact the OpenWallet Foundation Community Architects to learn more.
+
+Alternative
+Projects MAY document in their security policy document that they do use a service other than GitHub for private patch deployment infrastructure, or that they don't use any private patch deployment infrastructure at all. In either case, the document MUST include the details of what is used instead.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Special Interest Group
+A special interest group (SIG) under the Technical Advisory Council (TAC) is a group with a shared interest in advancing a specific area of knowledge, learning, or technology related to the mission of the OpenWallet Foundation where members cooperate to affect or to produce solutions within their particular field. Unlike a task force, SIGs are typically long running and may or may not produce any deliverables. A SIG can be created by anyone in the OpenWallet Foundation community and must be proposed to and approved by the TAC.
+Propose a Special Interest Group
+To propose a special interest group, create an issue in the TAC GitHub repository using the Special Interest Group template. The issue should be named "Special Interest Group Proposal: \<name of special interest group>". The issue should include the following information:
+
+- Introduction/background material
+- Objectives of the special interest group
+- List of deliverables or work products (optional)
+- Leader(s)
+- Initial participant list
+
+Approval Process
+The TAC will review the special interest group proposal first by providing comments in the issue and secondly by bringing the special interest group proposal to a discussion and vote in a TAC meeting.
+The decision of the vote will be documented in the issue. If the special interest group is approved, a discussion channel in Discord will be created. In addition, we will work with the OpenWallet Foundation operations team to schedule a meeting on the OpenWallet Foundation calendar. If necessary, a GitHub repository and/or mailing list will also be created at the request of the special interest group leader(s).
+Special Interest Group Procedures
+The special interest group can decide on the mechanism for running the SIG. Meeting minutes and a log of decisions that have been made should be kept for ensuring continuity of the special interest group. The special interest group should update the issue to reflect where the meeting notes and log of decisions is kept or use the issue directly to capture this information.
+Reporting on Special Interest Group Activities
+Every quarter the special interest group leader should report on the activities of the SIG at a TAC meeting. This will ensure that the SIG is still active and that there is still value in hosting the special interest group. Please see the schedule for when these updates should occur.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+OpenWallet Foundation TAC composition
+Current Composition
+
+
+
+| Member (alphabetical by first name) |
+Representing |
+
+
+
+
+| David Zeuthen |
+Google |
+
+
+| Jaehoon (Ace) Shim |
+At Large |
+
+
+| Pete Cooling |
+Visa |
+
+
+| Rolson Quadras |
+Gen |
+
+
+| Stavros Kounis (vice chair) |
+At Large |
+
+
+| Stephen Curran |
+Impact (ACA-Py) |
+
+
+| Tracy Kuhrt (chair) |
+Accenture |
+
+
+| Wenjing Chu |
+FutureWei Technologies |
+
+
+
+History
+2023-03-08
+
+- Tracy Kuhrt is running unopposed for TAC Chair
+- Composition
+- Accenture - Tracy Kuhrt
+- Futurewei - Wenjing Chu
+- Gen Digital - Drummond Reed
+- Visa - Marie Austenaa
+
+
+
+2023-04-05
+
+- TAC "at large" election results
+- Jeremie Miller
+- Stavros Kounis
+
+
+
+2023-06-28
+
+- Pete Cooling was introduced as Visa's TAC voting representative.
+
+2023-08-09
+
+- RESOLVED: That Stavros Kounis is hereby confirmed and approved as the TAC Vice Chair
+
+2023-09-06
+
+- We welcomed David Zeuthen, Google premier member representative
+
+2023-10-18
+
+- Mike Varley will represent Gen Digital moving forward.
+
+2024-04-03
+
+- TAC "at large" election results
+- Ace Shim
+- Stavros Kounis
+
+
+
+2024-04-17
+
+- Chair/Vice Chair Results
+- Stavros, vice chair
+- Tracy, chair
+
+
+
+2024-05-15
+
+- Rolson Quadras will represent Gen Digital moving forward
+
+2024-10-02
+
+- Stephen Curran was welcomed as the ACA-Py project representative
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Task Force
+A task force is a group that is focused on a task with limited scope and fixed time to complete. Unlike a special interest group, a task force will have a specific set of deliverables or work products that it will create and be limited in time to completion. A task force can be created by anyone in the OpenWallet Foundation community and must be proposed to and approved by the TAC.
+Propose a Task Force
+To propose a task force, create an issue in the TAC GitHub repository. The issue should be named "Task Force Proposal: \<name of task force>". The issue should include the following information:
+
+- Introduction/background material
+- Objectives of the task force
+- List of deliverables or work products
+- Time to complete (no more than 6 months)
+- Leader(s)
+- Initial participant list
+
+Approval Process
+The TAC will review the task force proposal first by providing comments in the issue and secondly by bringing the task force proposal to a discussion and vote in a TAC meeting.
+The decision of the vote will be documented in the issue. If the task force is approved, a discussion channel in Discord will be created. In addition, we will work with the OpenWallet Foundation operations team to schedule a meeting on the OpenWallet Foundation calendar. If necessary, a GitHub repository and/or mailing list will also be created at the request of the task force leader(s).
+Task Force Procedures
+The task force can decide on the mechanism for creating the deliverables. Meeting minutes and a log of decisions that have been made should be kept for ensuring continuity of the task force. The task force should update the issue to reflect where the meeting notes and log of decisions is kept or use the issue directly to capture this information.
+Reporting on Task Force Completion of Deliverables
+Upon completion of the task force's deliverables, the task force should arrange a time with the TAC chair to present the deliverables at a TAC meeting. This can be accomplished by sending an email to the TAC mailing list at tac@lists.openwallet.foundation.
+Requesting an Extension on Completion Date
+If the task force is not able to complete the deliverables by the specified completion date, then the leader of the task force should arrange a time with the TAC chair to discuss the extension at a TAC meeting. This discussion should include information on the current status, the delays, and the expected updates to the schedule. This can be accomplished by sending an email to the TAC mailing list at tac@lists.openwallet.foundation.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+ Home
+
+Welcome to the OpenWallet Foundation's (OWF) Technical Advisory Council (TAC) website. Here you will find:
+
+
+-
+
What is the TAC
+
+Learn more about the Technical Advisory Council's role, responsibilities, and voting members
+
+-
+
Governing Documents
+
+Review the OpenWallet Foundation TAC Governing Documents
+
+-
+
TAC Meetings
+
+See meeting invite details and meeting notes from past meetings
+
+-
+
Projects
+
+Explore the OpenWallet Foundation Projects
+
+-
+
Special Interest Groups
+
+Join an OpenWallet Foundation Special Interest Groups (SIGs)
+
+-
+
Task Forces
+
+Work on an OpenWallet Foundation Task Forces
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-03-08
+
+Agenda
+
+- Welcome and intros of TAC
+- Reminder of TAC Charter
+- TAC Chair election
+- TAC "at large" seats
+- Call for code from the Community
+- Open Discussion and Next Steps
+
+Recording
+
+Actions
+
+Minutes
+
+- TAC Charter
+
+- TAC Chair Election
+- Tracy Kuhrt is running unopposed – will move to email vote to formalize
+
+
+- Composition
+- Accenture - Tracy Kuhrt
+- Futurewei - Wenjing Chu
+- Gen Digital - Drummond Reed
+- Visa - Marie Austenaa
+- “at large” representative #1 appointed by vote of the TAC
+- “at large” representative #2 appointed by vote of the TAC
+- one representative appointed by the technical oversight body (e.g., a technical steering committee) of each TAC Project
+
+
+- Call for Code
+
+- Governance rules
+
+- Open Discussion
+- The Governing Board met yesterday and appointed Daniel Goldscheider as Interim Executive Director. Daniel introduced himself and provided his thoughts on the future of OWF.
+- A suggestion was made for a landscape review. A comment was made that that work has begun here.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-03-22
+
+Agenda
+
+Links
+
+Action Items
+
+- Conduct an email vote for the Governance documents approval and adoption.
+- Conduct an email vote for the TAC "at large" schedule and process.
+- Todd to confirm whether the TAC can create an alternate policy or whether the Governing Board will need to update the charter to reflect.
+- Tracy to create a pull request to update the project proposal template to include links to the mission and project lifecycle.
+- Create a GitHub organization (openwallet-foundation-labs) to host incoming labs.
+
+Minutes
+
+- No comments on the TAC Governance documents. Will conduct an email vote to adopt.
+- Discussed TAC "at large" election process. Will conduct an email vote to adopt.
+- Reviewed project proposal process and instructions and went through the template. Two suggested changes:
+- Include a link to the mission.
+- Include a link to the project lifecycle for stage information.
+
+
+- Next steps
+- Create a labs organization (openwallet-foundation-labs) to host any lab proposals.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-04-05
+
+Agenda
+
+- Review action items from last meeting
+- TAC "at large" election results
+- Architecture SIG update
+- Call for code from the community
+- Open discussion and next steps
+
+Links
+
+Action Items
+
+- Tracy to rename the architecture-task-force GitHub repo to architecture-sig - completed
+- Jenn to rename the meeting invite for the Outside Architecture Special Interest Group to reflect that the name should be the Architecture SIG
+- Jenn to add Stavros to the TAC meeting invite - completed
+- Jenn to add Jeremie to the TAC meeting invite
+- Create a GitHub organization (openwallet-foundation-labs) to host incoming labs
+
+Meeting Minutes
+
+- Review action items from last meeting
+- Conduct an email vote for the Governance documents approval and adoption - results 3 TAC members voted in favor; 1 TAC member abstained
+- Conduct an email vote for the TAC "at large" schedule and process - results 3 TAC members voted in favor; 1 TAC member abstained
+- Todd to confirm whether the TAC can create an alternate policy or whether the Governing Board will need to update the charter to reflect - currently no policy for TAC alternates; if we want this, we would need to present this to the GB to get a charter update
+- The TAC would like to recommend that the board create an alternate policy for the TAC.
+- The language will be similar to the following "A TAC member can designate an alternate for a specific meeting, and has to notify the chair in advance."
+
+
+- Tracy to create a pull request to update the project proposal template to include links to the mission and project lifecycle - pull request created and merged
+- Create a GitHub organization (openwallet-foundation-labs) to host incoming labs - not yet completed
+
+
+- TAC "at large" election results
+- Jeremie Miller
+- Stavros Kounis
+
+
+- Architecture SIG update
+
+- Call for code from the community
+- Next steps
+- Discussion regarding the upcoming conference season, including IIW, EIC, and others.
+- Suggestion was made to create an OpenWallet Foundation event calendar.
+- Next meeting is April 19, 2023.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-04-19
+
+Agenda
+
+- Review action items from last meeting
+- Priorities
+- Internet Identity Workshop (IIW) updates
+- Call for code from the community
+- Open discussion and next steps
+
+Links
+
+Action Items
+
+- Document process for creating a task force - pull request
+
+Meeting Minutes
+
+- Review action items from last meeting
+- Tracy to rename the architecture-task-force GitHub repo to architecture-sig - completed
+- Jenn to rename the meeting invite for the Outside Architecture Special Interest Group to reflect that the name should be the Architecture SIG - completed
+- Jenn to add Stavros to the TAC meeting invite - completed
+- Jenn to add Jeremie to the TAC meeting invite - completed
+- Create a GitHub organization (openwallet-foundation-labs) to host incoming labs - completed
+
+
+- Priorities
+- Projects
+- Pipeline of projects
+- Getting a method of tracking and accessing projects
+- Rule book / guide on the evaluation process and criteria for new projects
+- Technical Focus
+- Cloud based, edge based, and hybrid wallets
+- Common components for wallets
+- Specific components for money, identity, and object wallets
+
+
+
+
+- Collaboration between OWF and European Commission
+- Tracking changes in the next European Digital Identity Wallet Architecture and Reference Framework (ARF) and making sure it lines up with OWF thinking
+- Maintaining dialog and exploring alignment
+
+
+
+
+- Internet Identity Workshop (IIW) updates
+- Topics on digital wallets, credentials, and interoperability
+- Sessions on EUDI and the ARF
+- A number of OpenWallet topics will be discussed on day 2 and 3
+- Discussions about the Linux Foundation Trust umbrella
+
+
+- Call for code from the community
+- Completing the assessment framework may allow people to better understand what type of projects should be considered for contribution
+
+
+- Next steps
+- Next meeting is May 3, 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-05-03
+
+Agenda
+
+- Review action items from last meeting
+- Welcome new TAC member
+- Task Force Proposal
+- Assessment Framework - How do we want to assess incoming projects?
+- Call for code from the community
+- Open discussion and next steps
+
+Links
+
+Action Items
+
+- Update Task Force process to include information on optional mailing lists and capturing meeting notes -- commit -- completed
+- Create process for Special Interest Groups similar to Task Force process and cross link the two processes together
+
+Meeting Minutes
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-05-17
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+Meeting Minutes
+
+-
+
Review action items from last meeting
+
+- Update Task Force process to include information on optional mailing lists and capturing meeting notes -- commit -- completed
+- Create process for Special Interest Groups similar to Task Force process and cross link the two processes together -- PR -- completed
+
+
+-
+
New lab proposals
+
+
+-
+
Special Interest Group process proposal
+
+- RESOLVED: That the special interest group (SIG) process documented in this pull request and rendered on this page and using this issue template is hereby confirmed, approved, and adopted.
+- Unanimously approved by the present TAC voting members.
+
+
+-
+
OID4VCI and OID4VP Due Diligence Task Force
+
+- Support exists for this task force, but we ran out of time to conclude the discussion.
+- Request for comments on OID4VCI and OID4VP Due Diligence Task Force proposal and +1 if you are interested in participating.
+- Hakan will update to reflect comments so that we can bring this to a vote at the next TAC meeting.
+
+
+-
+
Call for code from the community
+
+-
+
Next steps
+
+- Next meeting is May 31, 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-05-31
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+Meeting Minutes
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-06-14
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+Meeting Minutes
+
+-
+
Announcements
+
+
+-
+
Review action items from last meeting
+
+
+-
+
TAC Alternates Policy
+
+- RESOLVED: That the TAC Alternates Policy is hereby confirmed, approved, and adopted.
+- Unanimously approved by the present TAC voting members.
+
+
+
+
+-
+
Call for code from the community
+
+- A question was asked whether we were tracking a wishlist for potential projects
+- In general, we are looking for projects that fit with the vision of the OpenWallet Foundation. Those that are focused on wallet engine related to identity, money, and objects
+- We previously were capturing potential code projects using this Google sheet
+
+
+- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+
+
+-
+
Open discussion and next steps
+
+- Relative to the Credential Format Comparison SIG, the ToIP Foundation has just started a task force on the same thing for credential exchange protocols. See this spreadsheet
+- David Alexander will present on wallets and personal data stores at the next meeting and we will discuss further
+
+- Next meeting is June 28, 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-06-28
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC. Kickoff meeting planned for July 7th.
+- OID4VC Due Diligence task force will meet weekly on Wednesdays at 5pm CEST.
+- Pete Cooling was introduced as Visa's TAC voting representative.
+
+
+-
+
Review action items from last meeting
+
+
+-
+
Vice chair seat and responsibilities
+
+- RESOLVED: That the Vice Chair Seat and Responsibilities is hereby confirmed, approved, and adopted.
+- Unanimously approved by the present TAC voting members.
+- Voting schedule
+- Call for nominations: June 28
+- End of call for nominations: July 5, Noon PT
+- A ballot will be distributed on: July 5 by end of day PT
+- The election will be completed on: July 11, Noon PT
+- Election results are announced at the July 12 meeting
+
+
+- If you would like to submit your nomination for TAC Vice Chair, please create an issue at https://github.com/openwallet-foundation/tac/issues
+- Title of issue: [NOMINATION]: 2023 Vice Chair - Name
+- Include a short bio, outline your qualifications, and provide a statement explaining why you would be a good choice for the seat
+
+
+
+
+
+
+-
+
Wallets and personal data stores
+
+
+-
+
Call for code from the community
+
+- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+
+
+-
+
Open discussion and next steps
+
+- Next meeting is July 12, 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-07-12
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC
+
+- OID4VC Due Diligence task force will meet weekly on Wednesdays at 5pm CEST
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific
+- Invitation to fully remote ISO/IEC JTC 1/SC 17 18013-7 Interoperability Event
+- For Associate non-profit members of the OpenWallet Foundation: voting is now open to select the Associate Representative for the Governing Board. Please email operations@openwallet.foundation if you have any questions about your organization's participation in this vote.
+
+
+-
+
Review action items from last meeting
+
+
+-
+
Vice Chair
+
+- RESOLVED: That the voting schedule for vice chair is hereby revised, approved, and adopted as specified.
+- Revised voting schedule
+- Call for nominations: July 12
+- End of call for nominations: August 2, Noon PT
+- A ballot will be distributed on: August 2 by end of day PT
+- The election will be completed on: August 8, Noon PT
+- Election results are announced at the August 9 meeting
+
+
+- Unanimously approved by the present TAC voting members.
+
+
+
+
+-
+
Farmworker Wallet OS project proposal
+
+- Video shared on Discord
+- Question asking for clarification of the scope of the contribution
+- Concerns raised about the licensing terms of the generated output from Mendix
+- Mendix does not make any intellectual property claims on the output
+
+
+- Question raised about the proposed license that will need to be run past LF legal and the Governing Board
+- Need to consider naming of the repos to ensure that it allows people to determine that they are part of the same project
+- Question raised about the difference between the Aries SDK proposed to be part of this project and the one in Hyperledger
+- The one in this project is a wrapper around the SDK in Hyperledger that can be used by Mendix developers
+
+
+- Continue conversation on the pull request
+
+
+-
+
Call for code from the community
+
+- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+
+
+-
+
Open discussion and next steps
+
+- Next meeting is July 26, 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-07-26
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Develop list of budget line items needed by the TAC
+- Work with Jorge on the item of whether aries-sdk-mendix makes sense within Hyperledger
+
+Meeting Minutes
+
+-
+
Announcements
+
+
+-
+
Review action items from last meeting
+
+
+-
+
Materials for MkDocs Insiders version
+
+- RESOLVED: That the TAC recommends to the Governing Board the sponsorship of Material for MkDocs to obtain access to the Insiders Version is hereby confirmed, approved, and adopted.
+- Proposed resolution was not voted on. It was suggested that we develop a proposal that would include other tools that the technical community would need to limit the number of requests to the Governing Board.
+
+
+
+
+-
+
Farmworker Wallet OS project proposal
+
+- Discussion items
+- Code of Conduct
+- plan to change to use OWF’s CoC
+- we may need to consider changing the template since it asks for the current CoC
+
+
+- License
+- change to use Apache 2.0 license
+
+
+- Project Governance
+- no change needed at this point
+
+
+- Repo names
+- Discussion was had to make sure that we are prefixing repo names with the project name to ensure that it is easy for someone to find all repos associated with a single project
+
+
+- Interoperable roadmap
+- No limit on what will be supported
+
+
+- Hosting Aries-specific stuff at OWF
+- TAC considers wrappers of other projects to be better suited to be included with the parent project
+- Tracy to work with Jorge on creating a lab proposal for Hyperledger for the Aries-specific wrappers
+- Jorge to update proposal to reflect the above recommendation
+
+
+
+
+
+
+-
+
Call for code from the community
+
+- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+
+
+-
+
Open discussion and next steps
+
+- Next meeting is August 9, 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-08-09
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Continue to work on budget line items
+- Jorge to update code of conduct on Farmworker Wallet OS proposal -- completed
+- Create repositories for the Farmworker Wallet OS Lab
+- Share document with governance best practices -- completed
+
+- Comment on OWF Project Guidance - all
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC
+- OID4VC Due Diligence task force will meet weekly on Tuesdays at 5pm CEST
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific
+- sd-jwt-python source is now available
+
+
+-
+
Review action items from last meeting
+
+
+-
+
Farmworker Wallet OS project proposal
+
+- RESOLVED: That the Farmworker Wallet OS lab is hereby confirmed, approved, and adopted.
+- Unanimously approved by the present TAC voting members.
+
+
+
+
+-
+
Budget Request to Governing Board
+
+
+-
+
Vice Chair
+
+- RESOLVED: That Stavros Kounis is hereby confirmed and approved as the TAC Vice Chair
+- Approved by the present TAC voting members with Stavros abstaining.
+
+
+
+
+-
+
Call for code from the community
+
+- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- Question asked about code proposal that depends on Aries/Bifold and whether that could be submitted to OWF?
+- If the project is only dependent on Aries/Bifold, then it can be submitted to OWF.
+- If, however the project is a wrapper of Aries/Bifold, then that should probably be submitted to Hyperledger.
+
+
+- Question about project governance best practices and whether we could document these best practices for new projects.
+- OWF Project Guidance -- this document assumes a fairly mature project that consists of a technical steering committee and maintainers for the project. Please comment and add your thoughts/suggestions.
+- In addition, we can look at Hyperledger's Project Best Practices for additional thoughts on guiding OpenWallet Foundation projects.
+
+
+
+
+-
+
Open discussion and next steps
+
+- Next meeting is August 23, 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-08-23
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC
+- OID4VC Due Diligence task force will meet weekly on Tuesdays at 5pm CEST
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific
+- Farmworker Wallet OS repositories created
+- Project pages created for each approved project on the TAC website
+- Slide deck available covering the OWF Project Proposal Process
+
+
+-
+
Review action items from last meeting
+
+- Continue to work on budget line items -- all
+- Jorge to update code of conduct on Farmworker Wallet OS proposal -- completed
+- Create repositories for the Farmworker Wallet OS Lab -- completed
+- Share document with governance best practices -- completed
+- Comment on OWF Project Guidance - all
+
+
+-
+
Budget Request to Governing Board
+
+- Sponsorship of Material for MkDocs to obtain access to the Insiders Version at $125/month to support the TAC website
+- Wiki
+- Options:
+- Dokuwiki is currently included in our current LFIT budget
+- Confluence would be an additional $800/month
+- Continue utilizing GitHub wiki
+- Update the TAC website as necessary
+
+
+- Discussion:
+- Confluence is nice to allow for the ability to search across the entire foundation
+- Consider the migration costs
+- Confluence has a lot of nice features that GitHub wiki and Dokuwiki do not have
+- It is easier to bring markdown files into Confluence than to export to markdown
+- Most documentation for projects will be captured within projects as markdown files and hosted using something like ReadTheDocs.io or GitHub Pages
+- We do not currently have anyone that is asking for Confluence
+- If we sponsor Material for Mkdocs insiders version, then all OpenWallet Foundation projects will be able to utilize
+
+
+- Outcome: We will postpone asking for budget until we have a need
+
+
+- License Scanning
+- Another project within the Linux Foundation cost is $65,000/year
+- We should ask for this as it allows us to remain compliant with the open licenses
+
+
+- Package Hosting - GitHub? ghcr.io? Is there a package hosting solution for all technologies that exists?
+- ghcr.io (GitHub Packages) is free for all public GitHub repositories – recommend we start there
+- Support for Package Registries
+- The only thing that we have currently that is not supported by GitHub Packages is Python
+
+
+- Playground/Sandbox Hosting
+- We do not yet have a price for this, but following are some of the things that we could see needing a sandbox
+- Accessing server-side APIs
+- Deployment of server-based reference wallet
+- Interop testing
+- Reference implementation of data objects that a wallet contain - example VC issuance and verification
+
+
+- Harm mentioned that he has some information on the infrastructure costs for hosting the European Interoperability Test Bed, which was presented to the architecture SIG on March 27, 2023. Harm will provide information on these costs
+- Harm is also interested in bringing the Interoperability Test Bed as a project to the OWF
+
+
+- DevSecOps
+- The Linux Foundation is recommending that projects use GH Actions
+- Automated security/code scanning
+- SonarQube - Static code analysis
+
+
+
+
+-
+
OWF Project Governance Guidance
+
+- Request to review, add comments and feedback
+- David Alexander recommended that we include information about momentum and duty of care and working across the foundation
+- Stavros asked if a TSC is required for projects
+- No, a TSC is not mandatory. The idea is that if a project gets big enough where all the maintainers cannot get together easily and make decisions, more governance framework is needed, and this is the way to go in that case.
+- As such, we should make sure that this document provides the right level of guidance for projects at different stages in their lifecycle
+
+
+
+
+-
+
Call for code from the community
+
+- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- Next time we meet, we will be reviewing the VC-API prject proposal
+
+
+-
+
Open discussion and next steps
+
+- Next meeting is September 6, 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-09-06
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Create recommendation for governing board for licenses that are compatible with Apache 2.0 to be approved -- Tracy
+- Update PR to answer questions asked during the meeting -- John
+- Determine if Energy Web Foundation is willing to relicense VC-API -- John
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC (next call September 13)
+- OID4VC Due Diligence task force will meet bi-weekly on Tuesdays at 5pm CEST (next call September 12)
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call September 11)
+
+
+-
+
Review action items from last meeting
+
+
+-
+
Welcome new TAC member
+
+- We welcomed David Zeuthen, Google premier member representative
+
+
+-
+
VC-API Project Proposal
+
+- How does this codebase relate to the energywebfoundation/ssi?
+- Does this proposal refer to the ssi repository OR only to work under the /vc-api path?
+- The intention is to bring over only the /vc-api path. We could consider whether it makes sense to bring over the other application, but it would require a separate proposal.
+
+
+- Are there dependencies or references to any implementation outside this folder that need attention if it is the latter?
+- Refer to the "Source Control" section of the proposal for information on what the dependencies are for the VC-API
+
+
+- Could we prepare a list of all the single repositories the vc-api needs and will be part of this proposal? I would also suggest supplementing this list with the purpose of these additional repos and their relationship/dependencies to vc-api.
+- This is captured in the "Source Control" section of the proposal.
+
+
+- For licensing purposes, will we leave related repositories in the organization they currently are? Should we expect a licensing conflict in this case?
+- John will follow up on the license with Energy Web Foundation.
+
+
+- What referenced tutorials and documentation will moved from energywebfoundation GitHub organization to the OWF?
+- Yes, we can move the tutorials and documentation into OWF.
+
+
+
+
+- Is this project an implementation of a VC API server or also client/wallet libraries?
+
+- Is this project based on the latest version of the CCG VC API? Does it already implement the full community report?
+- It implements the latest published version of the CCG VC API. It may be missing one or two endpoints. I don't think that we have implemented derived presentation.
+
+
+- Which credential formats and signature formats are supported?
+- Those that are supported by SpruceID's DIDKit
+
+
+- How have you tested interop?
+- We have not yet tested interop. The testing that we have done is with the available test suites.
+
+
+- What will be the prefix for this project?
+- We need to determine a way in which projects can be separated if they implement the same specification. Project prefixes are a way to do this and will allow us to trademark them in the future.
+
+
+- License
+- John to follow up with Energy Web Foundation about the possibility or re-licensing
+- Develop recommendation for the OWF governing board on licenses that are compatible with Apache 2.0
+
+
+- Missing DCO on existing repository
+
+
+-
+
Call for code from the community
+
+- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+
+
+-
+
Open discussion and next steps
+
+- Next meeting is September 20, 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-09-20
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Review, comment, and add feedback to the Wallet Framework .NET project proposal - all
+- Review, comment, and add feedback to the Intellectual Property Proposal - all
+- Digital Wallet and Agent Overview SIG
+- Create Discord channel - Tracy
+- Add information to the TAC website regarding the SIG - Tracy
+- Add link to the above to the OpenWallet Foundation GitHub Profile - Tracy
+- Work with Maaike on infrastructure requirements (repo, mailing list) - Tracy/Maaike
+
+
+- Anti-Correlation and Anti-Profiling SIG
+- Create Discord channel - Tracy
+- Add information to the TAC website regarding the SIG - Tracy
+- Add link to the above to the OpenWallet Foundation GitHub Profile - Tracy
+- Work with Andy on infrastructure requirements (repo, mailing list) - Tracy/Andy
+
+
+- Conduct email vote for VC-API project approval - Tracy - completed
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC (next call September 27)
+- OID4VC Due Diligence task force will meet bi-weekly on Tuesdays at 5pm CEST (next call September 26)
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call September 25)
+- New Project Proposal - Wallet Framework .NET - Please review
+- Suggested Future Project - Support the Apple pass format
+
+
+-
+
Review action items from last meeting
+
+- Review, comment, and add feedback to OWF Project Governance Guidance by October 4th - all
+- Review, comment, and add feedback to VC-API project proposal - all
+- Provide infrastructure costs for the European Interoperability Test Bed - Harm Jan Arendshorst
+- Create recommendation for governing board for intellectual property policy -- Tracy -- completed
+- Update VC-API PR to answer questions asked during the meeting -- John – completed
+- Determine if Energy Web Foundation is willing to relicense VC-API -- John – completed
+
+
+-
+
SIG Proposal - SSI Wallet and Agent Overviews
+
+
+-
+
SIG Proposal - Anti-Correlation and Anti-Profiling
+
+
+-
+
VC-API Project Proposal
+
+- Discussion
+- RESOLVED: That the VC-API lab is hereby confirmed, approved, and adopted.
+- Since we did not have enough TAC voting members to meet the ⅔ supermajority vote, we will conduct an email vote.
+
+
+
+
+-
+
Intellectual Property Policy
+
+- Apache 2.0 for source code
+- CC-BY-4.0 for documentation
+- Allowed Third Party License Policy
+- RESOLVED: That the proposed Intellectual Property Policy will be forwarded to the Governing Board for consideration.
+- Please review and provide your feedback
+- We will vote on this next time we meet
+
+
+
+
+-
+
Call for code from the community
+
+- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+
+
+-
+
Open discussion and next steps
+
+- Next meeting is October 4, 2023
+- Discussed whether to move to weekly meetings to support influx of project proposals. It was determined that we could be more efficient on these calls if we commented on the PRs when they are submitted to get questions answered that may delay the vote.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-10-04
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Conduct email vote on the Intellectual Property Policy
+- Add project page for the Wallet Framework .NET project
+- Work with Sebastian to transfer Wallet Framework .NET project code to OWF
+- Review, comment, and add feedback to Android Identity Library project proposal - all
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CEST on alternate weeks to the TAC (next call October 11)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CEST (next call October 24)
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call October 16)
+- Please submit any code proposals using the process defined at openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up.
+- Pre-IIW Developer Face-to-Face October 9
+
+
+-
+
Review action items from last meeting
+
+
+-
+
Project Proposal - Wallet Framework .NET
+
+- RESOLVED: That the Wallet Framework .NET proposal is hereby confirmed, approved, and adopted.
+- Unanimously approved by the present TAC voting members.
+
+
+
+
+-
+
Project Proposal - Android Identity Library
+
+
+-
+
Intellectual Property Policy
+
+- Apache 2.0 for source code
+- CC-BY-4.0 for documentation
+- Allowed Third Party License Policy
+- Open Standards and Specifications
+- RESOLVED: That the proposed Intellectual Property Policy will be forwarded to the Governing Board for consideration.
+
+
+
+-
+
Open discussion and next steps
+
+- Discussion regarding conflict of the Safe Wallet SIG with other meetings
+- Standing agenda items that we might want to add:
+- Socialization of what others in the community are doing
+- Project, SIG, Task Force updates
+
+
+- Next meeting is October 20 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-10-18
+
+Agenda
+
+- Announcements
+- Review action items from last meeting
+- Welcome new TAC member (hold for next meeting)
+- Legal Discussion - Project Charters
+- Project Proposal - Android Identity Library
+- Project Proposal: SD-JWT JS
+- Open discussion and next steps
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Update project proposal template to make it easier for people to understand what the TAC is expecting for answers related to each question -- Tracy
+- Update project lifecycle to reflect project charters -- Tracy
+- Document the desire for OWF to utilize permissive licenses in the project lifecycle -- Tracy
+- Review, comment, and add feedback to SD-JWT JS lab proposal -- all
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call October 30)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CEST (next call October 24)
+- Safe Wallet SIG meets weekly on Tuesdays at 8am US/Pacific (next call October 24)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CEST on alternate weeks to the TAC (next call October 25)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CEST on alternate weeks to the TAC (next meeting October 26)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up.
+
+
+-
+
Review action items from last meeting
+
+- Conduct email vote on the Intellectual Property Policy – completed
+- Add project page for the Wallet Framework .NET project – completed
+- Work with Sebastian to transfer Wallet Framework .NET project code to OWF – completed
+- Review, comment, and add feedback to Android Identity Library project proposal - all
+- Provide infrastructure costs for the European Interoperability Test Bed - Harm Jan Arendshorst
+
+
+-
+
Welcome New TAC Member
+
+- Mike Varley will represent Gen Digital moving forward.
+- Hold for next meeting as Mike could not attend today.
+
+
+-
+
Legal Discussion
+
+- Discuss project charters
+- Sample charter
+- Intake form
+- Copyleft vs. Permissive licenses (LF allows any OSI license. The OWF can decide on whether they only want permissive license.)
+
+
+
+
+-
+
Project Proposal - Android Identity Library
+
+
+-
+
Project Proposal - SD-JWT JS
+
+- RESOLVED: That the SD-JWT JS lab proposal is hereby confirmed, approved, and adopted.
+
+
+
+-
+
Open discussion and next steps
+
+- David Alexander suggested that the OpenWallet Foundation work closely with MyData.
+- Next meeting is November 1, 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-11-01
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Update "permissive license" to "OSI-approved permissive license" in the project lifecycle and template PRs
+- Update Paid Tooling PR to reflect other requests require the Governing Board approval
+- Onboarding SD-JWT JS lab
+- Create sd-jwt-js repo in OpenWallet Foundation Labs GitHub
+- Create sd-jwt-js Discord channel
+- Complete intake form to create project charter
+
+
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call November 6)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CEST (next call November 7)
+- Safe Wallet SIG meets weekly on Tuesdays at 8am US/Pacific (next call November 7)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CEST on alternate weeks to the TAC (next call November 8)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CEST on the same weeks as the TAC (next meeting November 2)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up.
+
+
+-
+
Review action items from last meeting
+
+- Update project proposal template to make it easier for people to understand what the TAC is expecting for answers related to each question -- Tracy -- completed
+- Update project lifecycle to reflect project charters -- Tracy -- completed
+- Document the desire for OWF to utilize permissive licenses in the project lifecycle -- Tracy -- completed
+- Review, comment, and add feedback to SD-JWT JS lab proposal -- all
+- Work with John Henderson to transfer VC-API project to OpenWallet Foundation Labs
+- Work with David Zeuthen to transfer Android Identity Library project to OpenWallet Foundation Labs
+
+
+-
+
Welcome New TAC Member
+
+- Mike Varley will represent Gen Digital moving forward.
+
+
+-
+
Resolution: SD-JWT JS Project Proposal
+
+- RESOLVED: That the SD-JWT JS lab proposal is hereby confirmed, approved, and adopted.
+- APPROVED with six yea, one absent
+
+
+
+
+-
+
Resolution: SD-JWT Rust Project Proposal
+
+
+-
+
Resolution: Proposal Process Updates
+
+
+-
+
Resolution: Project Services and Paid Tooling
+
+
+-
+
Open discussion and next steps
+
+- Next meeting is November 15, 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-11-15
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Onboarding SD-JWT Rust lab
+- Create sd-jwt-rust repo in OpenWallet Foundation Labs GitHub
+- Create sd-jwt-rust Discord channel
+- Complete intake form to create project charter -- follow up with LF Legal on status
+
+
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call November 27; skipping week of US Thanksgiving)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call November 21)
+- Safe Wallet SIG meets weekly on Tuesdays at 8am US/Pacific (next call November 21)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call November 22)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting November 16)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up.
+- SIG quarterly updates will begin in January 2024
+
+
+-
+
Review action items from last meeting
+
+- Update "permissive license" to "OSI-approved permissive license" in the project lifecycle and template PRs – completed and merged (lifecycle PR 69 and template PR 22)
+- Update Paid Tooling PR to reflect other requests require the Governing Board approval – completed and merged
+- Onboarding SD-JWT JS lab
+- Create sd-jwt-js repo in OpenWallet Foundation Labs GitHub – completed
+- Create sd-jwt-js Discord channel – completed (#sd-jwt-js)
+- Complete intake form to create project charter
+
+
+- Work with John Henderson to transfer VC-API project to OpenWallet Foundation Labs
+- Work with David Zeuthen to transfer Android Identity Library project to OpenWallet Foundation Labs
+- Working on name of the project
+- David has been working with the downstream dependencies to make them aware of changes that will be coming
+
+
+
+
+-
+
Task Force Update: OID4VC Due Diligence
+
+- Update Slide Deck
+- Discussion about whether this task force should become a SIG
+- At this time, we will leave this as a task force
+- The task force members will decide on the expanded time that is needed
+- At some point in the future, this may become an OID4VC Implementers SIG
+
+
+
+
+-
+
Resolution: SD-JWT Rust Project Proposal
+
+- RESOLVED: That the SD-JWT Rust lab proposal is hereby confirmed, approved, and adopted.
+- Unanimously approved by the present TAC voting members.
+
+
+
+
+-
+
Resolution: SD-JWT .NET Project Proposal
+
+
+-
+
Open discussion and next steps
+
+- Next meeting is November 29, 2023
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-11-29
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Onboard SD-JWT .NET
+- Transfer sd-jwt-dotnet repo to OpenWallet Foundation Labs GitHub
+- Create sd-jwt-dotnet Discord channel
+- Follow up with LF Legal on project intake form
+
+
+- Onboard Agent Framework JavaScript
+- Transfer repos to OpenWallet Foundation Labs GitHub
+- Create agent-framework-js Discord channel
+- Follow up with LF Legal on project intake form
+
+
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call December 4)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call December 5)
+- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call December 5)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call December 6)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting November 30)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- SIG quarterly updates will begin in January 2024
+
+
+-
+
Review action items from last meeting
+
+- Onboarding SD-JWT Rust lab
+- Create sd-jwt-rust repo in OpenWallet Foundation Labs GitHub – completed
+- Create sd-jwt-rust Discord channel – completed (#sd-jwt-rust)
+- Complete intake form to create project charter -- follow up with LF Legal on status
+
+
+- Work with John Henderson to transfer VC-API project to OpenWallet Foundation Labs
+- Work with David Zeuthen to transfer Android Identity Library project to OpenWallet Foundation Labs
+
+
+-
+
Resolution: SD-JWT .NET Project Proposal
+
+- RESOLVED: That the SD-JWT .NET lab proposal is hereby confirmed, approved, and adopted.
+- Approved by role call vote; 7 aye, 0 nay, 0 abstain
+
+
+-
+
Resolution: Agent Framework JavaScript Project Proposal
+
+- RESOLVED: That the Agent Framework JavaScript Project proposal is hereby confirmed, approved, and adopted.
+- Stavros Kounis agreed to be the second sponsor to bring the project in at growth stage
+- Approved by role call vote; 7 aye, 0 nay, 0 abstain
+
+
+-
+
Open discussion and next steps
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2023-12-13
+
+Agenda
+
+- Announcements
+- Review action items from last meeting
+- Moving to LFX Meetings
+- Resolution: Add Schedule for Quarterly SIG Updates
+- 2023 Retrospective
+- Open discussion and next steps
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Create Vulnerability Disclosure Policy
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call January 8)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call December 19)
+- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call December 19)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call December 20)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting December 14)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+
+
+-
+
Review action items from last meeting
+
+- Onboard SD-JWT .NET – completed
+- Transfer sd-jwt-dotnet repo to OpenWallet Foundation Labs GitHub – completed
+- Create sd-jwt-dotnet Discord channel – completed
+- Follow up with LF Legal on project intake form – completed
+
+
+- Onboard Agent Framework JavaScript – completed
+- Transfer repos to OpenWallet Foundation GitHub – completed
+- Create agent-framework-js Discord channel – completed
+- Follow up with LF Legal on project intake form – completed
+
+
+- Work with John Henderson to transfer VC-API project to OpenWallet Foundation Labs – in progress
+- Work with David Zeuthen to transfer Android Identity Library project to OpenWallet Foundation Labs – completed
+
+
+-
+
Moving to LFX Meetings
+
+
+-
+
Resolution: Add Schedule for Quarterly SIG Updates
+
+
+-
+
2023 Retrospective
+
+- Reviewed accomplishments
+- Also include in the accomplishments the face-to-face and the discussion with LF Legal on project charters
+
+
+- Retrospective
+- Shoutouts?
+- Google for hosting us at our face-to-face in Mountain View
+- Tracy for leading meetings
+- SIG and Task Force leaders
+
+
+- What went well?
+- Good structure on the TAC
+- Opportunity to collaborate
+- Consistency of how TAC meetings are managed and the access to the information needed so that you can do prep
+- Transparency
+- Inclusiveness
+- Team spirit
+- Advocacy
+- Provided confidence to move from being a consumer of open source to actually publishing open source at OWF
+- Learning process of what's involved in open source has been incredibly useful
+- Collaboration
+- Donation
+- Strong community engagement
+- Support OpenWallet has received in terms of projects, sponsors and Governmental Advisory Council members
+
+
+- What could we do differently next year?
+- Include voting members on the agenda and let people know who can vote at these meetings
+
+
+- Recommendations for next year
+- List of events for next year -- include in the #events channel on Discord
+- Creating a resource of slides that others have presented at conferences to present OWF
+- Challenge: helping projects grow within the OWF
+- Challenge: helping projects collaborate and work with one another
+- Engaging with the EUDI and bringing projects into OWF
+- Interoperability is a topic for us to focus on next year. Not just for the same protocols, but also across protocols. SIDI is also something that we should work closely with
+- Publish a white paper documenting our overall architectural considerations for open wallets (started already in the Architecture SIG)
+- Engaging with Trust Over IP
+
+
+
+
+
+
+-
+
Open discussion and next steps
+
+- Vulnerability Disclosure Policy
+- Look at creating this next year
+- Resources:
+
+
+
+- Next meeting is January 10, 2024
+- Architecture SIG Quarterly Update
+- Using LFX Meetings
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-01-10
+
+Agenda
+
+- Announcements
+- Review action items from last meeting
+- Architecture SIG Update
+- Discuss Drafted Vulnerability Disclosure Policy
+- Goals for 2024 (time permitting)
+- Open discussion and next steps
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- List of TAC goals from other LF projects - Brian
+- Update Vulnerability Disclosure Pull Request - Tracy
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call January 15)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call January 17)
+- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call January 16)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call January 17)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting January 11)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+
+
+-
+
Review action items from last meeting
+
+- Work with John Henderson to transfer VC-API project to OpenWallet Foundation Labs – completed
+- Create Vulnerability Disclosure Policy – drafted
+
+
+-
+
Architecture SIG Update
+
+- See Architecture SIG Q1 2024 Update for the answers to the following questions:
+- What is the Architecture SIG?
+- What has the Architecture SIG accomplished?
+- What is next for the Architecture SIG?
+- Where can I get information on the Architecture SIG?
+- How do I participate in the Architecture SIG?
+
+
+- Discussion on how the Architecture SIG should work with projects
+- In general, people see the role of the architecture SIG as a group that provides information on the state of the digital wallet architectues that can be used to provide insight into projects that may be missing from the OWF and in the long term a place that will help projects work more closely together.
+
+
+
+
+-
+
Discuss Drafted Vulnerability Disclosure Policy
+
+- Discuss pull request
+- Rework to consider the following audiences: reporters, people using the code, and maintainers
+- Separate out standard text from project-specific text
+
+
+-
+
Goals for 2024
+
+- What specific goals does the TAC have for 2024?
+- Brian suggested looking at what other TAC goals have been
+- Information for new submitters
+- Updates on existing projects
+
+
+
+
+-
+
Open discussion and next steps
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-01-24
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call January 29)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call January 30)
+- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call January 30)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call January 31)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting January 25)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+
+
+-
+
Review action items from last meeting
+
+- List of TAC goals from other LF projects – Brian
+- Other projects at the LF only have a responsiblities list with the main goal of the TAC, TOC, or TSC to successfully carry out these responsibilities
+- Hyperledger Foundation has been putting together goals for the last couple of years (2023 Goals, 2024 Goals)
+
+
+- Update Vulnerability Disclosure Policy – drafted
+
+
+-
+
Project Proposal: Multi-format VC for iOS
+
+
+-
+
Discuss Vulnerability Disclosure Policy
+
+
+-
+
Elections
+
+
+-
+
Goals for 2024
+
+- What specific goals does the TAC have for 2024?
+
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting February 7, 2024
+- Credential Format Comparison SIG Update
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-02-07
+
+Agenda
+
+- Announcements
+- Review action items from last meeting
+- Credential Format Comparison SIG Update
+- Open discussion and next steps
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Sean to work with Mirko on a blog post on the Credential Format Comparison SIG
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call February 12)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call February 13)
+- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call February 13)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call February 14)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting February 8)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+
+
+-
+
Review action items from last meeting
+
+
+-
+
Credential Format Comparison SIG Update
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting February 21, 2024
+- Digital Wallets and Agents Overview SIG Update
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-02-21
+
+Agenda
+
+- Announcements
+- Review action items from last meeting
+- Digital Wallets and Agents Overviews SIG Update
+- Bifold Project Proposal
+- Project Promotion Process
+- Open discussion and next steps
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Create a PR against the project lifecycle to include information on transitioning through the lifecycle stages -- Tracy
+- Work with Bifold to onboard project into OWF
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call February 26)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call February 27)
+- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call February 27)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call February 28)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting February 22)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+
+
+-
+
Review action items from last meeting
+
+- Sean to work with Mirko on a blog post on the Credential Format Comparison SIG – in progress
+
+
+-
+
Digital Wallets and Agents Overviews SIG Update
+
+- Information included in the slides on the work that is being done.
+
+
+-
+
Bifold Project Proposal
+
+- RESOLVED: That the Bifold project proposal is hereby confirmed, approved, and adopted as a growth project.
+- Wenjing volunteered to be second sponsor for the project
+- Jeremie motion; Wenjing seconded; Unanimously approved
+
+
+
+
+-
+
Project Promotion Process
+
+- Our current project lifecycle does not clearly outline the steps necessary for projects to progress in the lifecycle.
+- Suggested changes to the lifecycle to create a PR to update the original project proposal to include the new stage and other information relevant to meet the proposed stage’s criteria.
+- Upside: This process is similar to the original project proposal process.
+- Possible Downside: This will overwrite the original proposal but might not be a concern given the history in GitHub on the file.
+- If we do a PR to the original proposal, we will need to make sure that we can have links to the previous versions that were approved.
+- We can possibly do this via the project pages by adding a new section
+- Action: Tracy to create a PR to provide details on what this will look like.
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting March 6, 2024
+- Safe Wallet SIG Update
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-03-06
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Create discussion item to continue discussion on Wallet Stacks - Tracy -- completed
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call March 11)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call March 12)
+- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call March 12)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call March 13)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting March 7)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- Reminder: Elections are coming up starting March 20, 2024; we will be accepting TAC “at large” nominations
+- Join the OpenWallet Foundation for our 1 year anniversary webinar on March 14, 9am PDT / 1700 CET / 9:30pm IST https://zoom.us/webinar/register/WN_MiUSaLFgQFOhVdTBMtlLuA#/registration
+
+
+-
+
Review action items from last meeting
+
+- Create a PR against the project lifecycle to include information on transitioning through the lifecycle stages – complete
+- Work with Bifold to onboard project into OWF – completed
+
+
+-
+
Safe Wallet SIG Update
+
+- Information included in the slides on the updates.
+
+
+-
+
OWF Wallet Stacks
+
+
+-
+
Project Promotion Process
+
+- RESOLVED: That the project promotion process is hereby confirmed, approved, and adopted.
+- Moved to the next meeting
+- Request that TAC members review the PR and provide any feedback
+
+
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting March 20 2024
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-03-20
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Determine way to get the sample project charter more visible on the website.
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call March 25)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call March 26)
+- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call March 26)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call March 27)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting March 21)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+
+
+-
+
Review action items from last meeting
+
+- Create discussion item to continue discussion on Wallet Stacks - Tracy -- completed
+
+
+-
+
Project Promotion Process
+
+- RESOLVED: That the project promotion process is hereby confirmed, approved, and adopted.
+- Motion - David Z; Seconded - Jeremie M
+- Unanimously approved
+
+
+
+
+-
+
TAC “At Large” Nomination Process
+
+- Submit nominations via a GitHub issue at 2024 "At Large" Nomination
+- Title of issue: [NOMINATION]: 2024 “at large” Name
+- Include a short bio, outline your qualifications, and provide a statement explaining why you would be a good choice for the seat
+
+
+-
+
TAC "At Large" Voting Schedule
+
+- 2024-03-20 Nomination Period Begins
+- 2024-03-27 Noon PT Nomination Period Ends
+- 2024-03-27 Helios Voting Ballot Distributed to Existing TAC Members
+- 2024-04-02 Noon PT Voting Ends
+- 2024-04-02 Results Announced on the TAC mailing list
+- 2024-04-03 New “at large” representatives begin their term
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting April 3 2024
+- Architecture SIG Q2 Update
+
+
+- Question asked about the OWF Developer Day on April 15 - should have more details early next week
+- Question asked about making it easier to find the sample project charter on the TAC website
+- Question asked about how to get sponsors for the SD-JWT JavaScript project to move to Growth - reach out to the TAC members (individually, on the #tac Discord channel, or on the TAC mailing list)
+- Question asked about how to find out what was going on in the community and how to get involved:
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-04-03
+
+Agenda
+
+- Announcements
+- Review action items from last meeting
+- Welcome New “At Large” Representatives
+- Architecture SIG Q2 Update
+- TAC Chair/Vice Chair Nomination Process and Voting Schedule
+- Wiki Update
+- The Wallet Stack (and next steps)
+- Open discussion and next steps
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Create a content plan for where stuff should live and who should control the content
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call April 8)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call April 9)
+- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call April 9)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call April 10)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting April 4)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- Jorge Flores (Co-Founder & CTO of Entidad) and Jesus Torres (Co-Founder & CEO of Entidad): How an Aries digital trust ecosystem helped distribute $60M USD (& counting) to essential workers - Presenting at the Hyperledger Identity Special Interest Group on Thursday, April 4 @ 3PM UTC, 8AM PDT, 9AM MDT, 11AM EDT. Join on Zoom: https://zoom.us/j/93003523877?pwd=Q3VvMnJ1N0lSUEZSc283SmFGRk9SQT09
+- IIW Planning discussion taking place on Discord in the #iiw-planning channel
+- EIC Planning discussions taking place on Discord in the #eic-planning channel
+
+
+-
+
Review action items from last meeting
+
+- Determine way to get the sample project charter more visible on the website -- completed
+
+
+-
+
Welcome New “At Large” Representatives
+
+- Thank you to all the nominees.
+- Welcome back, Stavros!
+- Welcome, Ace!
+- Thank you for your service, Jeremie!
+
+
+-
+
Architecture SIG Q2 Update
+
+
+-
+
TAC Chair/Vice Chair Nomination Process
+
+- Only TAC voting members are eligible to run for the TAC chair and vice chair seats
+- Electing a vice chair will be held in conjunction with the chair election; the person with the second highest number of votes will serve as the vice chair
+- Submit nominations via a GitHub issue at 2024 Chair/Vice Chair Nomination
+- Title of issue: [NOMINATION]: 2024 Chair/Vice Chair Name
+- Include a short bio, outline your qualifications, and provide a statement explaining why you would be a good choice for the seat
+- See Elections for more information
+
+
+-
+
TAC Chair/Vice Chair Voting Schedule
+
+- 2024-04-03 Nomination Period Begins
+- 2024-04-10 Noon PT Nomination Period Ends
+- 2024-04-10 Helios Voting Ballot Distributed to Existing TAC Members
+- 2024-04-16 Noon PT Voting Ends
+- 2024-04-16 Results Announced on the TAC mailing list
+- 2024-04-17 New Chair and Vice Chair begin their term
+
+
+-
+
Wiki Update
+
+- https://wiki.openwallet.foundation
+- Discussion about content plan. Where should information live? Who is responsible for changes?
+- TAC website makes sense for things that the TAC is responsible for
+- The maintainers should be responsible for project information
+- The LF Staff is responsible for the openwallet.foundation website content
+
+
+-
+
The Wallet Stack (and next steps)
+
+- Formation of a Secure Hardware SIG
+- Looking for interested parties
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting April 17, 2024
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-04-17
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Set up new lab eudi-wallet-kit-react-native
+- Discord channel
+- GitHub repo
+
+
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call April 22)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call April 23)
+- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call April 23)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call April 24)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting April 18)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- EIC Planning discussions taking place on Discord in the #eic-planning channel
+- The Hyperledger Identity SIG (ID SIG) recently hosted Jorge and Jesus from Entidad for "How The Aries Digital Trust Ecosystem Helped Distribute $60M USD (and counting) to Essential Workers. You can check out the recording on YouTube.
+- Michel Sahli is our GAC representative
+
+
+-
+
Review action items from last meeting
+
+- Create a content plan for where stuff should live and who should control the content -- in progress
+
+
+-
+
Chair/Vice Chair Results
+
+- Thank you to all nominees
+- Stavros, vice chair
+- Tracy, chair
+
+
+-
+
Project Proposal: React Native Kit for EUDI Wallet Reference Implementation
+
+
+-
+
OWF Naming Policy Update
+
+- Reviewed Project Naming Policy
+- Request that the community provide suggested edits and comments
+- After incoming feedback, Sean will work with the LF Staff prior to bringing back to the TAC for approval
+
+
+-
+
Content Plan
+
+- Quickly reviewed Content Plan
+- Request that the community provide suggested edits and comments
+- Determine where source of truth is for certain items, like the project list
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting May 1, 2024
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-05-01
+
+Agenda
+
+- Announcements
+- Review action items from last meeting
+- Credential Format Comparison SIG Q2 Update
+- Content Plan
+- Reference Architecture contribution
+- Open discussion and next steps
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Update Content Plan PR to include links
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call May 6)
+- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call May 7)
+- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call May 7)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call May 8)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting May 2)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- EIC Planning discussions taking place on Discord in the #eic-planning channel
+
+
+-
+
Review action items from last meeting
+
+- Set up new lab eudi-wallet-kit-react-native - complete
+
+
+
+-
+
Content Plan
+
+- RESOLVED: That the Content Plan is hereby confirmed, approved, and adopted.
+- Wenjing motion; Rolson seconded
+- Unanimously approved by the present TAC voting members
+
+
+
+
+-
+
Reference Architecture Contribution
+
+- Pull Request (Rendered version)
+- Proposed next steps:
+- Input from community - please provide comments on the PR
+- Add a heatmap that maps our current projects to the technology capabilities
+
+
+- David Z is concerned that the whitepaper may conflict with existing guidance
+- Request that a list of existing guidance be provided in the PR so that we may validate that the reference architecture whitepaper does not conflict with existing guidance
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting May 15 2024
+- Digital Wallet and Agent Overviews SIG Update
+- OID4VC Due Diligence task force update
+- Project Proposal: Library for OpenID4BLE
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-05-15
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Onboard OpenID4BLE Library lab
+- Onboard Trust Spanning Protocol lab
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call June 3)
+- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call June 4)
+- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call June 5)
+- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting May 30)
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- EIC Planning discussions taking place on Discord in the #eic-planning channel
+
+
+-
+
Welcome new TAC member
+
+- Rolson Quadras will represent Gen Digital moving forward
+- Thank you Mike Varley for your service
+
+
+-
+
Review action items from last meeting
+
+- Update Content Plan PR to include links - completed
+
+
+-
+
Project Proposal: OpenId4BLE Library
+
+- Recommended that project come in at Labs stage
+- Recommended that project move to GitHub issues (to be completed in 3-6 months)
+- Recommended that project use Discord for communication instead of Slack
+- Discussed governance and diversity of maintainers
+- RESOLVED: That the OpenId4BLE Library lab proposal is hereby confirmed, approved, and adopted.
+- Stavros motioned; David seconded
+- Unanimously approved by the present TAC voting members.
+
+
+
+
+-
+
Project Proposal: Trust Spanning Protocol
+
+- Discussed the need for language bindings that can be used by OWF projects. Recommendation is to implement the language bindings in conjunction with the projects that will use it to ensure correctness.
+- Research needs to be done on the license of https://github.com/dalek-cryptography/curve25519-dalek and whether an alternate implementation is needed
+- RESOLVED: That the Trust Spanning Protocol lab proposal is hereby confirmed, approved, and adopted.
+- Stavros motioned; Rolson seconded
+- Unanimously approved by the present TAC voting members.
+
+
+
+
+-
+
Project Annual Reviews
+
+
+-
+
OID4VC Due Diligence Task Force Update
+
+- Torsten provided an update on the OID4VC Due Diligence task force and recommended closing the task force as it has accomplished its goals.
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting May 29, 2024
+- Digital Wallet and Agent Overviews SIG Update
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-05-29
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Onboard Credhub project
+- Create Discord channel
+- Transfer repo
+- Create project page
+
+
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- EIC Planning discussions taking place on Discord in the #eic-planning channel
+- If you are interested in participating in the architecture SIG calls, we have a when2meet survey out there to find a new meeting time
+- EUDI Architecture Reference Framework v1.4 published
+- OpenWallet Foundation is hosting two workshops -- one for OpenID Connect for VCI and one for OpenID Connect for VP -- on June 10th and June 12th. Please be on the lookout for registration links coming soon
+
+
+-
+
Review action items from last meeting
+
+- Onboard OpenID4BLE Library lab
+- Created Discord channel (#tuvali) - completed
+- Need to transfer repo (Issue #151) - in progress
+- Working on project page (PR #149) - in progress
+
+
+- Onboard Trust Spanning Protocol lab
+- Created Discord channel (#tsp) - completed
+- Need to transfer repo (Issue #150) - in progress
+- Working on project page (PR #149) - in progress
+
+
+
+
+-
+
Project Proposal: credhub
+
+- RESOLVED: That the credhub lab proposal is hereby confirmed, approved, and adopted.
+- Stavros motioned; Wenjing seconded
+- Unanimously approved
+
+
+
+
+-
+
Project Annual Reviews
+
+
+-
+
Digital Wallet and Agent Overviews SIG Update
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting June 12, 2024
+- SD-JWT Python Annual Review
+- SD-JWT Kotlin Annual Review
+- Safe Wallet SIG Update
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-06-12
+
+Agenda
+
+- Announcements
+- Review action items from last meeting
+- Project Proposal: mdl.js
+- Project Annual Reviews
+
+- Safe Wallet SIG Update
+- Open discussion and next steps
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Onboard mdl.js
+- Reach out to Fabian regarding new maintainership - Sean/Torsten
+- File PR against openwallet-foundation-labs/governance to update maintainership for sd-jwt-kotlin - Ace
+
+Meeting Minutes
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-06-26
+
+Agenda
+
+- Announcements
+- Review action items from last meeting
+- Project Annual Reviews
+- SD-JWT Kotlin Annual Review
+
+
+- Discuss approval process for SIG output
+- TAC Goals 2024
+- Open discussion and next steps
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Reach out to Fabian regarding new maintainership of sd-jwt-kotlin - Sean
+- Document process for SIG output approvals
+- Create a presentations Drive folder for uploading OWF presentations from the community - Sean
+- Create a page on the TAC site as an index for the presentations in the above Drive folder - Tracy
+
+Meeting Minutes
+
+-
+
Announcements
+
+
+-
+
Review action items from last meeting
+
+- Onboard mdl.js - completed
+
+- Reach out to Fabian regarding new maintainership - Sean/Torsten
+- File PR against openwallet-foundation-labs/governance to update maintainership for sd-jwt-kotlin - Ace - completed
+
+
+-
+
Project Annual Reviews
+
+- SD-JWT Kotlin Annual Review - On hold until conversation with Fabian
+
+
+-
+
Discuss Approval Process for SIG output
+
+- Discussed the need for documenting and understanding the ambition of the SIG during the initial proposal process. Will the SIG want to publish documents that represent the views of the OWF, the views of the entire wallet ecosystem, or some other level
+- Anything that is published from OWF SIGs will be presumed to speak on behalf of the OWF.
+- Document types of approvals that have been obtained by the document. Example from OIDF
+- Best practice is to include a "Terms of Use" section in the output. See Terms of Use section in ToIP document for an example
+
+
+-
+
Review TAC Goals 2024
+
+- Discussed the TAC Goals for 2024.
+- List of events for next year -- include in the #events channel on Discord
+- This has been pretty opportunistic so far
+
+
+- Creating a resource of slides that others have presented at conferences to present OWF
+- Discussed creating a Drive folder for the community to upload their presentation along with an index on the TAC website for people to update with information about the presentations uploaded.
+
+
+- Challenge: helping projects collaborate and work with one another
+- Identify projects with similar goals and bring the projects together in a group to discuss opportunities for collaboration and interoperability testing.
+- Understanding which projects use each other.
+- Newsletter similar to Hyperledger's /dev/weekly newsletters
+
+
+- Engaging with the EUDI and bringing projects into OWF
+- Hosted workshop with EUDI
+
+
+- Interoperability is a topic for us to focus on next year. Not just for the same protocols, but also across protocols.
+- Discussed possibility of holding Inter-op-athons.
+- Torsten mentioned that it would be good for OWF to work with the OID4VP/VC conformance test teams.
+- Wenjing mentioned that interoperability is more than just at the protocol level, we should also be thinking about global interoperability.
+- Should consider an interopability landscape assessment.
+
+
+- Publish a white paper documenting our overall architectural considerations for open wallets (started already in the Architecture SIG)
+
+
+
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting July 10, 2024
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-07-10
+
+Agenda
+
+- Announcements
+- Update on Safe Wallet SIG whitepaper
+- Review action items from last meeting
+- Project Annual Reviews
+- SD-JWT Kotlin Annual Review
+
+
+- Publishing Papers in the OWF Community
+- Architecture SIG Update
+- Open discussion and next steps
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+Meeting Minutes
+
+-
+
Announcements
+
+
+-
+
Update on Safe Wallet SIG Update
+
+- The Safe Wallet SIG has taken another pass at the document and made some significant changes from the v1.0 release that was shared last week. As such, the plan is to:
+- Once the SafeWallet SIG members approve their changes a final version will be created on GitHub for the TAC members to review/comment.
+- SafeWallet SIG members will join the TAC Call on Wednesday, July 24th to discuss the future of the SIG and field questions from the TAC.
+
+
+
+
+-
+
Review action items from last meeting
+
+- Reach out to Fabian regarding new maintainership of sd-jwt-kotlin - completed Ace has reached out and confirmed transition
+- Document process for SIG output approvals - drafted
+- Create a presentations Drive folder for uploading OWF presentations from the community - Sean - completed
+- Create a page on the TAC site as an index for the presentations in the above Drive folder - Tracy
+
+
+-
+
Project Annual Reviews
+
+- SD-JWT Kotlin Annual Review (if available) - PR just submitted; move discussion to next meeting
+- Initial discussion about whether sd-jwt-kotlin will be a mirror of the EUDI or a fork. Concern that we may cause fragmentation if we become a fork. If we are a mirror, why should this remain in OWF?
+- Discussion will continue on the PR and when we meet next
+
+
+
+
+-
+
Publishing Papers in the OWF Community
+
+- RESOLVED: That the Papers Lifecycle governance document is hereby confirmed, approved, and adopted. Vote not conducted this week
+- Discussion regarding whether this is making OWF an SDO - no, it is not. Based on our expectation, SIGs and task forces will produce deliverables. This will ensure that people have the opportunity to review and discuss these deliverables prior to TAC approval.
+- Question and discussion on whether OpenWallet Foundation should publish papers.
+- Comment about ensuring that there is a workflow behind the process to ensure that papers review, approval, and publishing can be appropriately scheduled into the backlog.
+- In general, there is support from non-TAC voting members about the process adding clarity on expectations for SIGs and task forces.
+- Action: TAC members to review process and provide feedback for asynchronous discussion and move vote to next meeting
+
+
+
+
+-
+
Architecture SIG Update
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting July 24, 2024
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-07-24
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+Meeting Minutes
+
+-
+
Announcements
+
+
+-
+
Review action items from last meeting
+
+
+-
+
Project Proposal:
+
+- RESOLVED: That the Begin Wallet Core proposal is hereby confirmed, approved, and adopted.
+- TAC recommended that this be accepted as a lab
+- Discussion ensued regarding looking at the acceptance criteria for Growth projects
+- Discussion also about whether we should combine the openwallet-foundation-labs and openwallet-foundation organizations in GitHub
+- Action: Take the above two discussions offline in an email on the TAC mailing list
+- Wenjing motioned; David seconded
+- Unanimously approved
+
+
+
+
+-
+
Credential Format Comparison SIG Q3 Update
+
+- Mirko requested guidance in moving this SIG forward as there is little participation
+- Possible suggestions:
+- Move SIG to meet monthly
+- Recruit co-chair
+- Determine incentives that might help others to participate
+- Creating good first issues or help wanted issues to help others know where they might participate
+- Working closely with OIX and OIDC who is also doing similar work
+
+
+
+
+-
+
Safe Wallet SIG Deliverable - MOVED TO NEXT MEETING
+
+
+-
+
Publishing Deliverables in the OWF Community - MOVED TO NEXT MEETING
+
+
+-
+
Project Annual Reviews - MOVED TO NEXT MEETING
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting August 7, 2024
+- Safe Wallet SIG Deliverable
+- Publishing Deliverables in the OWF Community
+- Project Annual Reviews
+- Digital Wallet and Agent Overviews SIG update
+
+
+- TAC Meeting August 21, 2024
+- Farmworker Wallet OS Project Annual Review
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-08-07
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Verifiable Credentials Wallet lab onboarding - Sean
+- Update Deliverables Lifecycle PR to remove need for TAC approval - Tracy
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- Safe Wallet SIG Ask Me Anything webinar in two weeks; Sean will provide details on Discord
+- Architecture SIG is taking a break for August and will start up again after the US Labor Day holiday in September
+
+
+-
+
Review action items from last meeting
+
+
+-
+
Project Proposal: Verifiable Credential Wallet
+
+
+-
+
Remove Intake Form Requirement for Proposals
+
+- RESOLVED: That the following PRs that remove the intake form requirement are hereby confirmed, approved, and adopted.
+
+
+
+-
+
Publishing Deliverables in the OWF Community
+
+- RESOLVED: That the Deliverables Lifecycle governance document is hereby confirmed, approved, and adopted.
+- No vote taken
+- Agreed to remove the need for TAC approval
+- Agreed that there needs to be a review period for the community to provide feedback
+- Discussed whether the current disclaimer is enough
+- Requested that folks add suggested text to the PR
+
+
+
+
+-
+
Digital Wallets and Agents Overview SIG Update
+
+
+-
+
Project Annual Reviews - MOVED TO NEXT MEETING
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting August 21, 2024
+- Publishing Deliverables in the OWF Community
+- Project Annual Reviews
+- SD-JWT Kotlin Annual Review
+- Farmworker Wallet OS Project Annual Review
+
+
+- Digital Wallet and Agent Overviews SIG update
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-08-21
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Create plan for the future of the Credential Formats Comparison SIG and the Digital Wallets and Agents Overview SIG - Mirko
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- Safe Wallet SIG Ask Me Anything webinar in two weeks; Sean will provide details on Discord
+
+
+-
+
Review action items from last meeting
+
+
+-
+
Digital Wallets and Agents Overview SIG Update
+
+- Still getting pull requests for new wallets
+- Low participation in the bi-weekly meetings
+- Possibly combine this SIG with the Credential Format Comparison SIG
+- Need to socialize the overview matrix to a wider audience
+- Look for ways to involve the projects and possibly to provide ownership of an entry to those that create the wallet
+- Adding a comment at the top of the matrix that says that this is volunteer-maintained and you can add your own wallet
+- Creation of short videos (what this is, how you can contribute)
+- Next step: Mirko will work with others offline to come up with a plan and bring it back to the TAC on possibly merging the SIGs
+
+
+-
+
Project Annual Reviews
+
+- SD-JWT Kotlin Annual Review - MOVED TO NEXT MEETING
+- Farmworker Wallet OS
+- Jorge provided an overview of the progress that the community is making
+- Wenjing asked if there was anything that the TAC or the OWF organization could provide
+- Having people in the community use the project even if only for testing purposes
+- Webinar, workshop, or meetup to allow for a presentation of how to get the project up and running
+
+
+- RESOLVED: That the Farmworker Wallet OS annual review is hereby confirmed, approved, and adopted.
+- Wenjing motioned; David seconded
+- 4 approved; 1 abstained
+
+
+
+
+
+
+-
+
Publishing Deliverables in the OWF Community
+
+- RESOLVED: That the Deliverables Lifecycle governance document is hereby confirmed, approved, and adopted.
+- No vote taken
+- Changes since we last spoke:
+- Removed the need for TAC approval, but kept the community review period
+- Removed Terms of Usage section (already covered by the CC-by-4.0 text)
+- Added a “Non-Representative” Disclaimer section
+
+
+- Discussed the concerns of the Safe Wallet SIG members that the "Non-Representative" Disclaimer section appears that the OWF does not support the work of the SIGs
+- No alternative language has been suggested
+- We will look at approving this next week
+
+
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting September 4, 2024
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-09-04
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- OWF Wiki Update: Sean Bohan (OWF Staff) is testing now
+
+
+-
+
Review action items from last meeting
+
+- Create plan for the future of the Credential Formats Comparison SIG and the Digital Wallets and Agents Overview SIG - Mirko
+
+
+-
+
Safe Wallet SIG Update
+
+- Andy provided background on the SIG and and update of what has been done to date with the SIG
+- Andy will be stepping down after the completion of the blog and ask me anything session
+- Need to see if there is anyone who would like to lead this group going forward, if the SIG will go on haitus, or be disbanded
+
+
+-
+
Project Annual Reviews
+
+
+-
+
Publishing Deliverables in the OWF Community
+
+- Is it needed?
+- Possible options:
+- These materials are a deliverable of the sig name SIG and were created by the contributors to that SIG. It has not been reviewed, approved, or endorsed by the OpenWallet Foundation ("OWF") and its members.
+- These materials are a deliverable of the sig name SIG and were created by the contributors to that SIG. It does not necessarily reflect the official policies, positions, views or opinions of the OpenWallet Foundation ("OWF") and its members.
+- These materials are a deliverable of the OWF community. If you have concerns or suggestions regarding the content, please file a pull request.
+
+
+- Option #3 is the preferred disclaimer for deliverables
+-
+
Changes requested to ensure that this process also applies to projects
+
+-
+
RESOLVED: That the Deliverables Lifecycle governance document is hereby confirmed, approved, and adopted.
+
+- With the above changes (option #3 and applies to projects)
+- Stavros motioned; Wenjing seconded
+- Unanimously approved by all present TAC members
+
+
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting September 18, 2024
+- Discussed license issue raised on project-proposals repo
+- Discussed how to make it clearer that we have two separate organizations (openwallet-foundation and openwallet-foundation-labs) in GitHub
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-09-18
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Onboard new projects
+- Stephen to update SIG proposal for discussion at next meeting
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- Housekeeping:
+- Sept 24th: OpenWallet Foundation Multistakeholder Technical Meeting on the EUDI Wallet
+- Wiki has been updated by LFIT and has some final edits this week
+- OOTO/Holidays Poll to all TAC members this week
+- Linux Foundation Maintainer Survey
+
+
+
+
+-
+
Review action items from last meeting
+
+- Update the Deliverables lifecycle to include option #3 and to ensure that this applies to projects too - Tracy - completed
+- Respond to issue on project-proposal repo regarding licensing - Tracy - completed
+
+
+-
+
Project Proposals
+
+- Stephen Curran presented an overview of the project proposals and SIGs
+- General question regarding existing dependencies and if moving this project will break those dependencies
+- There's really not that much of a risk just simply moving the namespaces from Hyperledger to OpenWallet. There will be challanges, but they are independent of one another. All of the projects are independent and have operated independently for a number of years. Where they come together is in the Aries working group and the interop-profiles, which will hopefully continue under the interoperability special interest group. Each project has more or less separate maintainers.
+
+
+- ACA-Py
+
+- Askar
+- How easy is it to extend to a third database?
+- Not sure. SQLx provides the abstraction and that is how it would be extended further, but we have not had anyone add another database. It currently supports SQLlite and Postgres. There has been work to expand it to do things like paging.
+
+
+- Does this focus more on mobile or server environments?
+- This supports both. Used for enterprise data applications as well as Bifold Wallet.
+
+
+- RESOLVED: That the Askar (FKA Aries Askar) project proposal is hereby confirmed, approved, and adopted as an Impact project.
+- Wenjing motioned; Rolson seconded
+- Unanimously approved by the present TAC voting members
+
+
+
+
+- Name TBD - Aries Agent Test Harness
+- Have all three projects agreed to come under one umbrella?
+
+- Will BC Gov continue to run an instance of the test harness?
+
+- RESOLVED: That the TBD (FKA Aries Agent Test Harness) project proposal is hereby confirmed, approved, and adopted as an Growth project.
+- Wenjing motioned; Stavros seconded
+- Unanimously approved by the present TAC voting members
+
+
+
+
+- DIDComm Mediator Service
+- Will we want the community to run and operate a mediator?
+- Indicio is currently running a mediator that is being used by the community. Running software within a foundation will be difficult.
+
+
+- RESOLVED: That the DIDComm Mediator Service project proposal is hereby confirmed, approved, and adopted as a Growth project.
+- Wenjing motioned; Stavros seconded
+- Unanimously approved by the present TAC voting members
+
+
+
+
+
+
+-
+
SIG Proposal - Wallet Interoperability - MOVED TO NEXT MEETING
+
+-
+
Project Annual Reviews - SD-JWT Kotlin Annual Review - MOVED TO NEXT MEETING
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting October 2, 2024
+- Architecture SIG Update
+- VC-API Annual Project Review
+- SD-JWT Kotlin Annual Project Review
+- Wallet Interoperability SIG Proposal
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-10-02
+
+Agenda
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Review Annual Reviews offline - all
+- Onboard new lab
+- Onboard new SIG
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- Housekeeping:
+- Update email
+- Sept 24th: OpenWallet Foundation Multistakeholder Technical Meeting on the EUDI Wallet update
+- Wiki has been updated by LFIT and has some final edits this week
+- Thanks to TAC members who filled out the OOTO/Holidays Poll
+- Safe Wallet SIG AMA
+
+
+- Question asked about whether we would consider entire wallet contributions in addition to the libraries and SDKs that we have in the foundation.
+- Anything related to wallets are definitely fair game for the OpenWallet Foundation and contributions of the source projects. This would include entire wallets.
+
+
+
+
+-
+
Welcome new TAC members
+
+- Stephen Curran was welcomed as the ACA-Py project representative
+
+
+-
+
Moving Askar to Growth from Impact
+
+- Given the administrative overhead of needing a TAC representative, the Askar project requested that they be moved to Growth from Impact
+- RESOLVED: That the Askar project be moved to Growth from Impact stage
+- Wenjing motioned; Pete seconded
+- Five approved; Stephen and Ace abstained; one absent
+
+
+
+
+-
+
Review action items from last meeting
+
+- Onboard new projects - in progress
+- Stephen to update SIG proposal for discussion at next meeting - completed
+
+
+-
+
SIG Proposal - Wallet Interoperability
+
+- Stephen provided an overview of the SIG
+- Stavros mentioned a similar effort in the EUDI space that could complement this SIG
+- Discussion about scope and a desire that this cover wallet ecosystems instead of just wallets. This is as planned.
+- RESOLVED: That the Wallet Interoperability SIG proposal is hereby confirmed, approved, and adopted.
+- Wenjing motioned; Ace seconded
+- 6 approved; Stephen abstained; one absent
+
+
+
+
+-
+
Project Proposal - Solid Data Wallet
+
+- Hadrian Zbarcea provided an overview of the proposal
+- Questions asked to clarify the scope of the project. Currently proposed as a wallet that uses Solid for storage, but may evolve based on the direction that the OWF community might bring to the efforts
+- Suggestion that there might be some good collaboration with Askar to integrate Solid pods
+- Project is open to new contributors that may end up becoming maintainers of the project
+- GitHub does not seem to be appropriately recognizing that this is an Apache 2.0 only licensed project. We will need to resolve this before bringing the code over. Hadrian has taken an action to determine what is happening there
+- RESOLVED: That the Solid Data Wallet proposal is hereby confirmed, approved, and adopted as a Growth project.
+- Wenjing motioned; Stavros seconded
+- Unanimously approved by the present TAC voting members
+
+
+
+
+-
+
Project Annual Reviews
+
+
+-
+
Open discussion and next steps
+
+- Next TAC Meeting October 16, 2024
+- Architecture SIG Update
+- Credential Format Comparison SIG Q4 Update
+- Wallet Framework .NET Annual Review
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024-10-16
+
+Agenda
+
+- Announcements
+- Review action items from last meeting
+- Project Annual Reviews
+
+- Architecture SIG Q4 Update
+- Credential Format Comparison SIG Q4 Update
+- Open discussion and next steps
+
+Links
+
+TAC Voting Members
+
+Action Items
+
+- Reach out to Wallet Framework .NET maintainers about annual review - Tracy
+
+Meeting Minutes
+
+-
+
Announcements
+
+- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
+- OpenWallet Foundation Newsletter: Coming soon
+- ACA-Py Overview Meetup: in progress
+- October IIW Attendance - if you will not be able to attend the TAC meeting on October 30th due to IIW attendance, please let us know
+- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
+- Brian informed the TAC that he would be moving on from the OpenWallet Foundation at the end of this month
+
+
+-
+
Review action items from last meeting
+
+- Review Annual Reviews offline - all
+- Onboard new lab - working with the project formation team on naming and project charter
+- Onboard new SIG - working with the co-chairs to get the meeting set up on the OWF calendar for the week of November 4
+
+
+-
+
Project Annual Reviews
+
+
+-
+
Architecture SIG Q4 Update
+
+- Tracy provided an update on the Architecture SIG progress
+- The main progress is the merge of the Universal Wallet Architecture Whitepaper, which Tracy quickly highlighted
+- Next steps are to complete the project mappings for Credo and Bifold
+
+
+-
+
Credential Format Comparison SIG Q4 Update
+
+- Mirko provided an update on the Credential Format Comparison SIG
+- There is not much interest in the SIG with attendees at the meeting
+- The Wallet and Agents Overview SIG depends on the content from this SIG
+- A couple of suggestions were made:
+- Disband the SIG - This was not desired given the dependency on the content from the Wallet and Agents Overview SIG
+- Combine the two SIGs - Ecosystem Comparison SIG
+- Convert the SIGs into a lab so that the work on the contents of these two SIGs could be merged into a single project
+
+
+
+
+-
+
Open discussion and next steps
+
+-
+
Next TAC Meeting October 30, 2024
+
+- Wallet Framework .NET Annual Review
+- Identity Library Annual Review
+
+
+-
+
November 13, 2024 Meeting
+
+- Wallet and Agents Overview SIG Q4 Update
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+YYYY-mm-dd
+
+Agenda
+
+- Include agenda items here.
+
+TAC Voting Members
+
+Notes
+
+- Include discussion notes here.
+
+Recording
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+TAC Meetings
+TAC meetings are intended to be open to observe by Sponsors, contributors to any TAC Project, and others in the general public interested in the OpenWallet Foundation.
+The meetings will be held bi-weekly starting Wednesday, March 8, 2023 at 7:00am PT.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Bifold
+Project Description
+Bifold is an open-source project designed to enhance the way we interact with digital identities, making the process both secure and user-friendly. It is based on React Native, which lets it run smoothly on different devices and platforms, such as iOS, and Android. It is a leading example of digital wallets, with a focus on making verifiable credentials (VCs) simple and convenient for everyone. Our mission is to create a collaborative community that enhances the way digital credentials are handled, making them accessible and straightforward for all.
+Key Features and Benefits:
+
+-
+
Unified Digital Identity Management: Emphasizing security and user-friendliness, Bifold excels in consolidating and managing digital identities across various standards like AnonCreds and W3C VC Data Model. This capability positions Bifold as a pivotal resource for secure and private handling of digital identities, accessible to all.
+
+-
+
Seamless Multi-Platform Use: Thanks to its React Native architecture, Bifold delivers a smooth experience on any device, enabling users to manage their digital identities whether they are using a phone or a tablet. This cross-platform flexibility means that developers can create applications once and deploy them on both iOS and Android, ensuring a consistent and accessible user experience.
+
+-
+
Community-Driven Development: Bifold is more than a tool; it's a community initiative aimed at fostering collaboration and sharing innovations. By bringing together diverse groups, from organizations to individuals, Bifold encourages the pooling of resources and knowledge to facilitate the broader adoption and understanding of verifiable credentials.
+
+-
+
Widespread Adoption and Trust: With a growing list of users around the globe, including governmental bodies in Canada and teams in Brazil, Bifold has proven its reliability and relevance. Its international use showcases the platform's adaptability to various needs and its role in advancing digital identity management on a global scale.
+
+-
+
Adaptability to Diverse Needs: Bifold's design caters to a wide range of project types and complexities, offering tailored solutions for managing digital identities. This adaptability ensures that users can streamline their processes related to verifiable credentials, improving efficiency and simplification in digital identity initiatives.
+
+
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Credhub
+Project Description
+When talking about wallets for natural persons, a lot of people think that a smartphone based wallet is the only way to go. The user should feel the security and privacy by being independent from an external provider. But we are forgetting that online based services have a great user experience in daily life:
+- As a user I can use multiple clients where my data is synced, we do not have to care about backups or data recovery.
+- As a developer I can implement the business logic into the cloud and only need the rendering on the client side.
+Yes, when I am offline, I do not have access to my data anymore. But beside that the user experience is great!
+The credhub project is a typescript based monorepo, using nx to manage multiple components. Compared to other approaches, it also comes with an issuer and verifier service to issue and verify credentials.
+Clients
+There are two clients that can be used to interact with a cloud wallet
+- a PWA based on Angular
+- a Chrome Browser Extension based on Angular
+While the PWA is using the camera to scan QR codes, the browser extension is scanning the opened taps for QR codes and is able to show a little button next to the QR code to interact with the wallet. This approach was inspired by password managers like 1Password. In the daily use, People do not want to take out their smartphone to scan a QR code, they want an easy one click solution.
+By implementing the whole business logic in the cloud, the client is only responsible for the rendering. Therefore building new clients in other programming languages is easy by using the OpenAPI endpoints. For authentication the OpenID Connect protocol is used, the project is using the Keycloak server for that.
+Issuer and Verifier
+Both relying parties are implemented as separate services, each of them comes with a web client for demo purposes. Further integration like webhooks or other services can be implemented in the future. The authentication is done by using the OpenID Connect protocol.
+Modular approach
+The usage of NX allows reusable components with a modular approach. Each backend implementation supports low security key management by storing the keys in the filesystem or the database, or the integration with Hashicorp Vault for high security key management. Other implementations are possible.
+Identity Stack
+By validating existing SSI frameworks like Credo or Veramo, this project should primary focus on the architecture reference framework of the EU. Therefore other credential formats, transport protocols or key managements like multiple DIDs methods are not supported.
+Credential Profile:
+
+- Credential Format: SD-JWT-VC
+- Key Management (issuer): VC-ISSUER Meta data, DID, X509
+- Key Management (holder): CNF (json web key)
+- Transport Protocol: OID4VC
+- Signature Algorithm: P-256
+- Status Management: OAUTH Status List
+
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Credo
+Project Description
+Credo has evolved significantly since its inception as a Hyperledger Aries project. Initially, it heavily relied on Hyperledger standards such as DIDComm, Indy, and AnonCreds. However, with advancements in verifiable credential technology and the emergence of new standards, the framework underwent multiple refactoring and modularization processes to maintain interoperability.
+This allowed for the inclusion of non-Hyperledger standards like W3C Verifiable Credentials with Data Integrity Proofs, DIF Presentation Exchange, OpenID4VC, and SD-JWT integration. As industry requirements shifted towards greater modularity, it became apparent that a unified framework may be better.
+The future direction for Credo involves adopting a compartmentalized approach consisting of single-purpose libraries designed to work together seamlessly, building on what is already out there. This transition will take considerable effort and will, therefore, be gradual.
+In order to expand the framework's support for standards beyond the Hyperledger ecosystem, a reassessment of its governance was necessary. The OpenWallet Foundation (OWF) was chosen as a steward due to its commitment to promoting interoperability without directly developing or maintaining standard protocols.
+
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+OpenWallet Foundation Dashboards
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+openwallet-foundation-labs Dashboard
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+openwallet-foundation Dashboard
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
\ No newline at end of file
diff --git a/projects/fwos/index.html b/projects/fwos/index.html
new file mode 100644
index 00000000..6ba234c6
--- /dev/null
+++ b/projects/fwos/index.html
@@ -0,0 +1,4776 @@
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+ Farmworker Wallet OS - Technical Advisory Council
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Farmworker Wallet OS
+
+Project Description
+The Farmworker Wallet OS project is a community of contribution led by Entidad and the United Farm Workers Foundation (UFWF) with the goal of furthering the adoption of an open, secure, interoperable digital wallet engine that makes it easier for farmworker communities to access an ecosystem of life-altering social and human services.
+Farmworkers are the backbone of global food supply chains, yet they remain one of the most underserved segments of our population. Governments around the world deemed them ‘Essential’ during the recent pandemic. While services and programs exist to help, it’s challenging and costly for organizations that provide them to securely collect and verify the information needed to prove applicant eligibility claims. As a result, most farmworkers forego services and resources they need, even though they’re eligible for them.
+Over the last three years, Entidad and the UFW Foundation have been exploring digital trust technologies to solve this problem. We’ve developed PrepareseTM, a digital infrastructure solution that lets farmworker organizations securely reuse verified farmworker information, eliminating the need for repetitive collection. The solution layers didcomm, wallet, decentralized identifiers, and verifiable credential technologies with a low-code application development platform, Mendix.
+Mendix has been a key component in making the PrepareseTM solution possible. Low-code software development has been growing in popularity and bringing new audiences to the practice. Mendix, one of the more popular platforms with over 300K active developers and 50M users, has enabled Entidad and the UFW Foundation to develop, launch, and maintain enterprise-grade digital trust enabled solutions that solve real world problems.
+We’ve built two products, using this technology. For organizations we’ve built Preparese PlatformTM, it allows them to quickly develop and launch digital trust enabled services and programs. For farmworkers, we’ve developed Preparese MobileTM which combines a verifiable digital profile with a suite of tools that simplify interactions with organizations on the platform.
+The Preparese PlatformTM is being used by 9 organizations and has 5 digital services in production. The most recent service launched is being used to process and distribute $80 million in one-time relief payments to over 125,000 workers, under the United States Department of Agriculture’s Farm and Food Workers Relief Program (FFWR).
+The second product, Preparese MobileTM, is designed around the unique needs of farmworkers. We’ve developed a react native mobile app that lets farmworkers store, manage, and exchange their verified information. Engagement with organizations is made easier with DIDComm-based communication capabilities such as text and video chat.
+One of the cornerstone technologies of the solution is an interoperable Mendix enabled digital wallet. The wallet components need to be able to engage with various non-profit, government, and philanthropic sources, each with their own technology stacks. For this reason, interoperability and working with open standard frameworks has been a priority. The project team members have participated in TrustOverIP Foundation, Hyperledger Aries JS Working Group, and various other communities, including DID Communication Working Group and OpenWallet Foundation of late, to ensure we adhere to best practices and standards.
+While currently focused on farmworkers, the Mendix digital wallet engine can be used to help others. There are many other underserved communities that could benefit greatly from the privacy, accessibility, and security digital wallets can provide. With this social impact purpose in mind and spirit of further collaboration, Entidad and the UFW Foundation propose to open source the digital wallet engine used in their PrepareseTM solution. By making these resources available, we hope to facilitate a wide variety of social impact.
+Additionally, the project allows us to bridge and advance the interest of both the OpenWallet Foundation and Mendix communities. By collaborating with the Mendix community, we not only have the ability to grow the number of digital trust technology practitioners, we also tap into a community with an established customer base. By making digital wallets components that can be easily integrated into their existing solutions, the project can drive further adoption and usage of interoperable, secure and privacy preserving digital wallets.
+Origin & History
+The origins of the Farmworker Wallet OS project align with those of Entidad. What began as a volunteering effort by three college friends, was formalized in 2018 with the founding of Entidad as a public benefit corporation. We have primarily been working with leading farm worker-serving organizations to develop technology that leverages growing digital literacy in their communities to scale their impact.
+The first digital service launched supported the UFW Foundation’s emergency relief efforts during the height of the COVID-19 pandemic. The solution was used to plan, manage and operate over 500 in-person community events where over $15 million in resources were distributed to over 40K families. Additionally, it has allowed us to better understand the unique challenges of building for underserved communities and why interoperable, secure, and privacy preserving technologies are key to addressing these challenges.
+You can read more about our journey on our blog.
+External Dependencies
+Mendix is a low-code application platform provider so its terms of service cover usage of Mendix services and resources by Mendix developers (organizations and/or individual contributors). The Application model for a standards compliant wallet engine will be the primary focus for the contributors of this project. The Mendix terms of service do protect the IP rights to these App models in Section 3 with reference to "Customer Data" definition in section 17.
+There are design-time and runtime aspects of app development but one of the great things about this tooling is that there is clean separation between the two.
+The following captures the developer's "design-time" perspective. We hope that the diagram helps to clarify the software components that would fall under the scope of this OWF project and distinguishes PrepareseTM as an example of a closed (proprietary) application that embeds core Farmworker WalletOS components. We plan on documenting a similar diagram to aid in understanding the "runtime" perspective soon.
+
+
+- Mendix Studio Pro v9.24.4 (integrated developer environment)
+- Eclipse Temurin JDK 11 (x64)
+- Mendix Native Template v7.0.1
+- React Native v0.70.7
+- Hyperledger / Aries-Framework-Javascript v0.4.0
+- Development instance of an Aries Mediator Service
+- Development instance of an Aries Cloud Agent
+
+Infrastructure
+The Farmworker Wallet OS will be organized and published as a suite of software modules that can be imported into any existing Mendix app code repository. The Mendix software modules effectively serve as a digital wallet SDK that can be embedded into any Mendix application to enhance the user experience. The code repository for this project is itself a Mendix app repository and as such can be executed locally on any supported developer workstation.
+The initial version of the digital wallet SDK is being built on top of Aries Framework Javascript, an open-source framework maintained by the Hyperledger Aries developer community helping to foster participation with the Aries digital trust ecosystem. Over time, the digital wallet SDK will be extended to support other digital trust open standards such as OpenID for Verifiable Credentials (OID4VC).
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Identity Credential
+Project Description
+Libraries and reference applications for working with real-world identity.
+The initial focus for this work was mdoc/mDL according to ISO/IEC 18013-5:2021
+and related standards (mainly ISO 23220 series and ISO 18013-7) on Android. Current focus
+includes other credential formats and operating environments.
+Libraries
+The project includes two libraries written in Java and Kotlin. The
+first is identity which provides the core building blocks and which
+can also be used on server-side environments. The other is identity-android
+which provides Android-specific extensions to the former. It is designed to
+run on Android (API 24 or later) and will take advantage of Android-specific
+features including hardware-backed Keystore, NFC, Bluetooth
+Low Energy, and so on.
+The libraries are intended to be used by Wallet Applications (mobile
+applications on the credential holder's device), Reader Applications (applications
+operated on device controlled by the verifier), and Issuance Systems (applications
+operated by the credential issuer or their agent). They provide the following
+building blocks
+
+- A light-weight Secure Area abstraction for hardware-backed keystore
+- Applications can create hardware-backed Elliptic Curve Cryptography
+ keys which can be used for creating Signatures or performing Key Agreement.
+ Each key will have an attestation which can be used to prove to Relying Parties
+ (such as a credential issuer) that the private part of the key only exists
+ in a Secure Area.
+- The
identity-android library includes an implementation based on
+ Android Keystore
+ with support for requiring user authentication (biometric or lock-screen knowledge
+ factor, e.g. system PIN) for unlocking the key and also can use
+ StrongBox
+ if available on the device. This is appropriate to use in Android applications
+ implementing ISO/IEC 18013-5:2021 for storing DeviceKey.
+- The
identity library includes an implementation backed by BouncyCastle
+ with support for passphrase-protected keys. This isn't suitable for use
+ in Mobile Applications as its not backed by Secure Hardware.
+- Applications can supply their own Secure Area implementations for e.g.
+ externally attached dongles, cloud based HSMs, or whatever the issuer
+ deems appropriate to protect key material associated with their credential.
+
+
+- A Credential Store for storage of one or more Credentials
+- Each Credential has a Credential Key which can be used by the issuer
+ to bind a credential to a specific device which is useful when
+ issuing updates or refreshing a credential.
+- Additionally, each Credential has one or more Authentication Keys which
+ can be endorsed by the issuer and used at presentation time.
+- Finally, namespaced data and arbitrary key/value pairs can be stored
+ in a Credential which can be used for credential data and claims. This
+ data is stored encrypted at rest.
+
+
+- Data structures and code for provisioning of mdoc/mDLs
+- This code can can be used both on the device and issuer side. No networking
+ protocol is defined, the application has to define its own.
+
+
+- Parsers and generators for all data structures used in ISO/IEC 18013-5:2021
+ presentations, including
DeviceResponse, DeviceRequest, MobileSecurityObject
+ and many other CBOR data structures.
+- An implementation of the ISO/IEC 18013-5:2021 presentation flows including
+ QR engagement, NFC engagement (both static and negotiated), device retrieval
+ (BLE, Wifi Aware, and NFC)
+
+Wallet and Reader Android applications
+This repository also contains two Android applications using this library
+in the appholder and appverifier modules. The Wallet application is a simple
+self-contained application which allows creating a number of mdoc credentials
+using four different mdoc Document Types:
+
+org.iso.18013.5.1.mDL: Mobile Driving Licenseorg.micov.1: mdoc for eHealth (link)nl.rdw.mekb.1: mdoc for Vehicle Registration (link)eu.europa.ec.eudiw.pid.1: mdoc for Personal Identification
+and their associated mdoc name spaces. The first one is defined in
+ISO/IEC 18013-5:2021 and the other three have been used at mdoc/mDL
+test events organized by participants of the ISO/IEC JTC1 SC17 WG10
+working group.
+ISO 18013-7 Reader Website
+The wwwverifier module contains the source code for a website acting as an
+mdoc reader according to the latest ISO 18013-7 working draft (as of Sep 2023)
+and it's implementing the so-called REST API. There is currently a test instance
+of this application available at https://mdoc-reader-external.uc.r.appspot.com/.
+The Wallet Android application also has support for the REST API and registers
+on Android for the mdoc:// URI scheme. This can be tested end-to-end by going
+to the reader website (URL above) and clicking on one of the "Request" buttons,
+and then hitting the mdoc:// link presented on the site. This will cause the
+browser to invoke the Wallet app which will then connect to the reader and send
+the credential after user consent.
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Projects
+Projects in the OpenWallet Foundation follow the project lifecycle. This page lists the active projects within the OpenWallet Foundation and their current lifecycle stage.
+Active Projects
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+MDL JavaScript
+Project Description
+This is a Typescript(Javascript) implementation of the ISO 18013-5:2021 (MDL) specification. This project aims to provide a platform agnostic implementation of the MDL specification.
+To provide MDL features to Biggest Wallet SDKs like Credo or Veramo, the direction of the project will be:
+Provide a platform agnostic implementation of the MDL specification
+- Bring your own crypto
+- Modular approach
+- Provide platform specific helper implementations for developers to use easily
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Project Description
+Pure Swift package for creating Verifiable Credentials (VCs) in multiple formats
+
+Support for multiple data types for disclosed values including
+
+- String
+- Int
+- Boolean
+- Array of Strings - [String]
+- Dictionary of String keys and String values - [String:String]
+
+This project is a contribution of the work done at Ping Identity to test and establish interoperability of the various formats representing the Verifiable Credentials Data Model https://www.w3.org/TR/vc-data-model/. Along with the SD-JWT VC and JWT VC formats described above, Ping Identity has also participated in the interoperability event for OpenID4VP to present a VC JWT. That code will also be released as a part of this project.
+Source Repositories
+openwallet-foundation-labs/multiformat-vc-ios
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+YYYY PROJECT NAME
+
+
Info
+
Copy this template to the subdirectory for the current year and name the file YYYY-project-name-annual.md (e.g., 2024-amazingproj-annual.md). Update the title above to replace YYYY with the year of the annual review and PROJECT NAME with the name of the project. Update the index.md file in the current year to include a link to the markdown file. These blocks are instructions. Please remove when section has been completed.
+
Project Health
+
+
Info
+
Include information about your project's contributions and activity. You can find information within GitHub by looking at the Insights tab. We will be looking for signs of consistent or increasing contribution activity. Please feel free to add commentary to add color to this information.
+
Maintainer Diversity
+
+
Info
+
How many maintainers do you have, and which organisations are they from? How has the maintainers and diversity of your maintainers changed in the past year? Has the number of active maintainers increased/decreased? Has the diversity of maintainers increased/decreased? Please include a link to your existing MAINTAINERS file and the MAINTAINERS file from last year (if appropriate). This is a good opportunity to ensure that your MAINTAINERS file is up to date and to retire any maintainers.
+
Project Adoption
+
+
Info
+
What do you know about adoption, and how has this changed since your last review or since being accepted into OpenWallet Foundation? If you can list companies that are adopters of your project, please do so. Feel free to link to an existing ADOPTERS file if appropriate.
+
Goals
+
+
+
Info
+
Include information about the goals that you previously set for the project in the last review or since the project proposal has been approved. How has the project performed against these goals? If your goals changed from your previous annual report, let us know what changed and why. If you have not achieved the goals that you set out, that is okay. We want to know what you have accomplished and what challenges the project is having in meeting the goals.
+
Next Year's Goals
+
+
Info
+
What are the goals for the next year of the project? The goals should list what you want to achieve, not just what you know you can achieve. Feel free to include stretch goals and things that you are looking to explore in the next year. For example, are you working on major new features? Or are you concentrating on adoption, community growth, or documentation?
+
Help Required
+
+
Info
+
How can the OpenWallet Foundation or the TAC help you achieve your upcoming goals?
+
Project Lifecycle Stage Recommendation
+
+
Info
+
What stage do you think the project should be? If you you think that your project meets the criteria for another stage, please explain why.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024 Farmworker Wallet OS (FWOS)
+Project Health
+The Farmworker Wallet OS is an ecosystem of modules that enable the development of a Native Wallet Agent and a Cloud Wallet Agent in the low-code platform Mendix. The FWOS project remains healthy and active with one reference implementation deployed to a production environment and a second implementation soon to be released in Q3. As noted in our original project proposal, the FWOS project has been focused on building interoperability with Aries digital trust ecosystems. We continue to build our low-code SDK components on top of Credo and have completed ~90% coverage of Aries Interoperability Profiles 1 and 2. To date, the project has successfully completed 4 upgrades of the Credo toolkit (v0.4.2, v0.5.3, v0.5.6, v0.5.9) and are actively working on the upgrade to v0.5.10. This is important as it highlights the ability for this project to stay up to speed with the rapid rate of change of the underlying standards and open-source toolkits that this project depends on.
+Maintainer Diversity
+Contributions to the FWOS have been primarily from the Entidad development team. A couple of inquiries have come in via the project Discord channel with interest in participation but we have no concrete knowledge of any work done outside of the contributions from the project maintainers. We did add a new maintainer internally who helped us with the implementation of the DIDComm Survey protocol recently submitted as a proposal. This demonstrates that an experienced Mendix developer is able to learn and understand the underlying Aries and DIDComm architectures and contribute to the implementation of a new DIDComm protocol after only a few weeks of knowledge transfer and experimentation.
+Project Adoption
+The FWOS project has one reference implementation deployed to a production environment in February 2024. This release consisted of a mobile agent implemented on version 0.4.2 of the open-source Aries Framework JavaScript (AFJ) toolkit. Note that AFJ rebranded to Credo after it was accepted into the OpenWallet Foundation. Although no digital trust interactions were enabled outside of wallet onboarding and agent initialization, this first release was significant as it allowed us to demonstrate the viability of having the FWOS wallet engine running at scale within the target end-user community.
+Goals
+
+The goal of the Farmworker Wallet OS project is to promote the adoption of mobile (native) and cloud wallets. We are proud of the progress achieved to date in producing a stable production ready wallet holder toolkit that enables Mendix developers to jumpstart the integration of digital trust technologies with their Mendix native apps. The following collection of trust protocols have been implemented this year:
+
+For the remainder of the 2024 year, the project hopes to commence implementing support for AnonCreds presentation exchange over Bluetooth supported by:
+
+Additionally, the project hopes to initiate exploration and prototyping of a mobile driver's license verifier component (ISO mDL 18013-5 and ISO 18013-7: mdoc + OID4VP or Digital Credentials API).
+FWOS Native Agent Architecture
+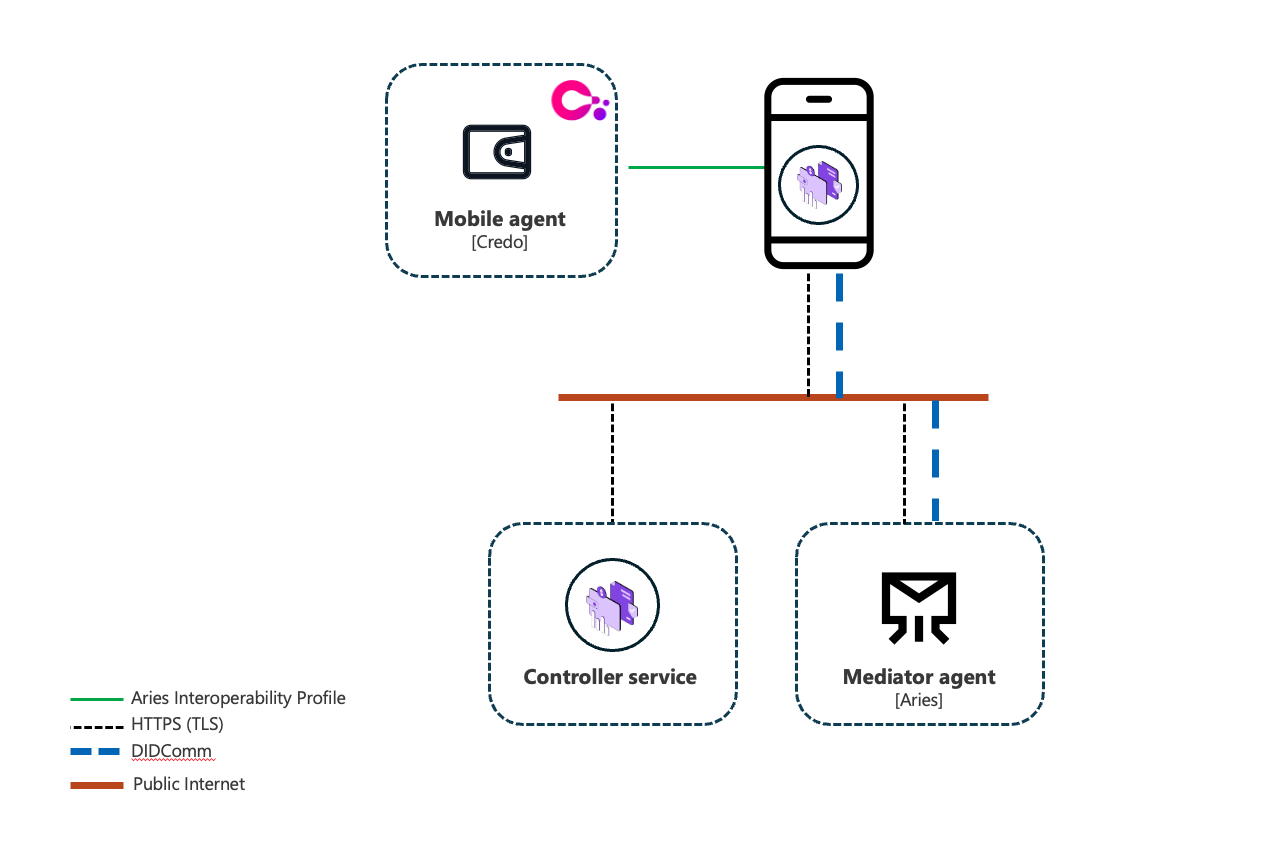
+Next Year's Goals
+For the next year, the FWOS project aims to introduce cloud agent components to support credential Issuer and Verifier use cases. This work is already in-progress and will be integrated formerly into the FWOS toolkit:
+
+FWOS Cloud Agent Architecture
+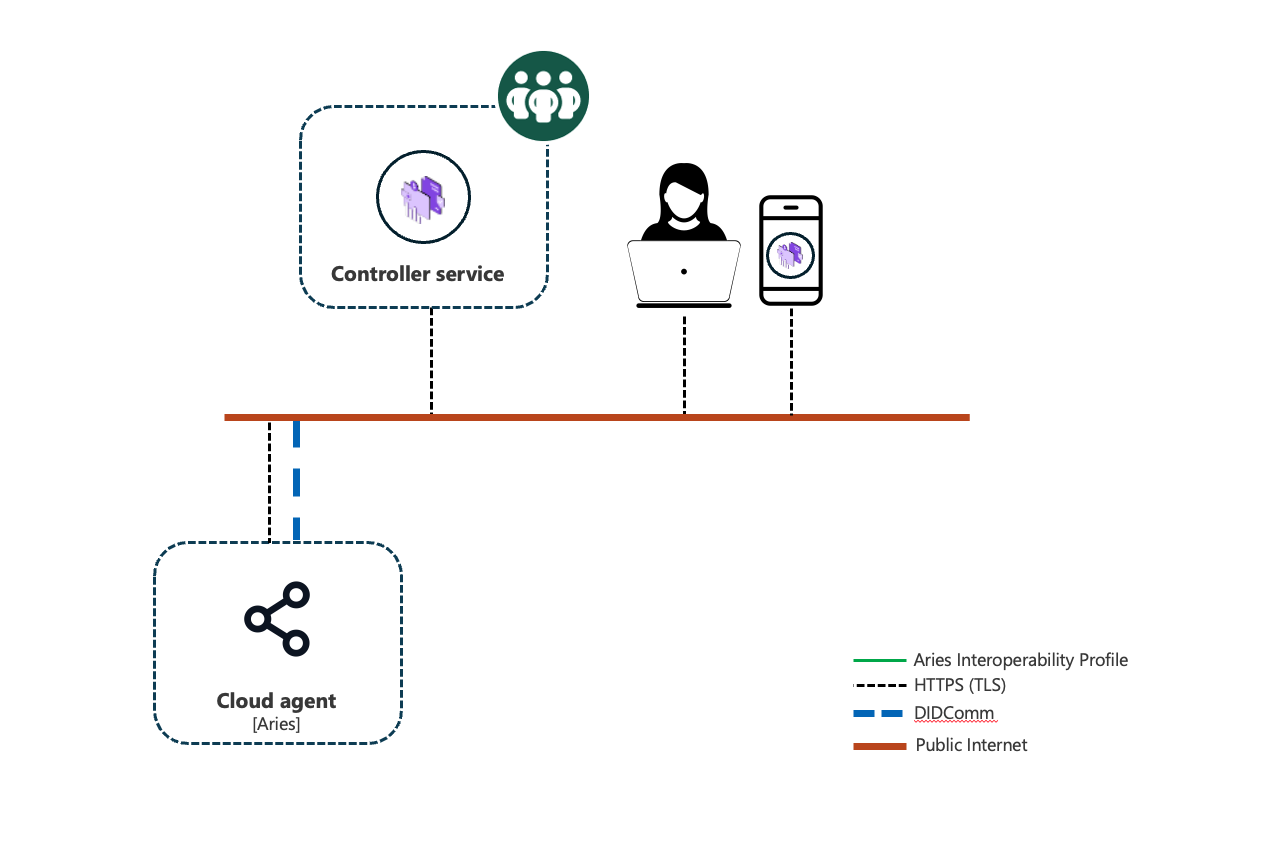
+Help Required
+The project is advancing steadily and does not require any help at the moment.
+Project Lifecycle Stage Recommendation
+The project is recommended to remain in the Labs stage.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024 sd-jwt-python (SD-JWT Reference Implementation)
+Project Health
+The main focus of this project is to provide a reference implementation for the
+IETF SD-JWT draft. As such, the code has reflected the developments in the
+specification over the last year and is up to date with the latest version of
+the draft. Since the draft is approaching a stable state (and hopefully a final
+RFC soon-ish), no drastic changes are expected in the codebase.
+Maintainer Diversity
+As before, the project is maintained by a single maintainer, an editor of the
+SD-JWT draft. Two developers have contributed code, one editor of the draft and
+one external contributor.
+Project Adoption
+The main task of the project is to provide a reference implementation for the
+SD-JWT draft. The project is in use
+
+- by the editors of the draft to test new developments and to produce examples for the specification,
+- by external contributors to understand testdrive SD-JWT, and
+- as a reference for testing and validation of other implementations.
+
+Goals
+
+The project has met its goals for the last year, which were to keep the codebase
+up to date with the latest version of the draft and to provide a reference
+implementation for the draft.
+Next Year's Goals
+As before, the main goal of the project is to provide a reference implementation
+for the SD-JWT draft. The project will continue to track the development of the
+draft, including a potential transition to an RFC. The project will also continue
+to exist as a reference for SD-JWT implementations.
+Help Required
+The project is in good shape and does not require any help at the moment.
+Project Lifecycle Stage Recommendation
+The project is recommended to remain in the Labs stage.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024 VC API Implementation
+Project Health
+The project remains healthy.
+Contributions for the initial portions of the year were focused on housekeeping items, however the project currently has development activity for functional and non-functional changes to increase the likelihood of further adoption and impact in the year ahead.
+Contributions have been made by two organizations, Energy Web and Impactility.
+Several forks have been made in the past year, suggesting some initial community attention.
+The underlying VC API specification (currently developed in the context of the W3C Credentials Community Group) is active and the specification group has the intention of bringing the specification to a W3C standards track in the months ahead.
+Maintainer Diversity
+The project currently has four maintainers, from two organizations, Energy Web & Impactility.
+Project Adoption
+The project currently has one primary adoption organization, Elia Group. Elia continues to showcase the VC API project on their SSI demonstration site (https://ssi4energy.eliagroup.eu/en).
+This is roughly the same amount of adoption as when accepted into the OpenWallet Foundation last year.
+Goals
+
+The project proposal mentioned the following aims in the "Alignment with the OpenWallet Foundation Mission" section:
+- Advance the adoption of interoperable and privacy enhancing digital wallets.
+- Promote the development and proliferation of the VC API specification itself
+Progress towards the above objectives has been small over the past year.
+However, the main functional enhancement undertaken in recent months (the migration of core key & credential operations to Credo) sets up the project well for progress on the objectives in the year ahead.
+For example, listing in the VC Playground (https://vcplayground.org/) is an opportunity to further both of the above objectives, however this was blocked by that lack of flexibility with JSON-LD context document loading in the implementation prior to the Credo integration.
+Next Year's Goals
+The current goals of the project are to:
+1. Increase use and adoption of the project, both by existing user organizations (Elia and Energy Web) and new organizations. The target metric is between 1 and 5 new organizations using the app in projects within the year.
+2. Support the development of the VC API specification.
+3. Provide feedback into the development of other OWF projects.
+On-going and planned work items which further these goals are detailed below.
+Migrating to Credo for key and credential operations
+GitHub Issue: https://github.com/openwallet-foundation-labs/vc-api/issues/20
+The benefits of this item include:
+- Synergy with an existing OWF project, allowing work on the VC API implementation to feed back into other OWF work
+ - Examples of this are the following GitHub issues:
+ - Credo Issue #2038- Make verifiableCredential property on W3cPresentation optional
+ - Credo Issue #2043 - Fix W3cCredentialsApi verifyCredential types
+ - Having a VC API wrapper for Credo would provide Credo with the interface for the VC Data Model 2.0 test suite
+ - A note that ACA Py already offers VC API issuance and verification endpoints
+- The ability to use load additional JSON LD contexts, unlocking new use cases
+- A clearer path to supporting further VC technology such as SD-JWT and BBS signatures
+Work on this item can be seen in the following PR: https://github.com/openwallet-foundation-labs/vc-api/pull/36
+Improving documentation for technology adoption decision makers
+GitHub Issue: https://github.com/openwallet-foundation-labs/vc-api/issues/29
+This item aims to improve the ability of technology selection decision makers, such as CTOs or Software Architects, to assess whether or not the VC API implementation is suitable for their use cases and technology context.
+The key output is a new documentation site.
+Listing in the VC Playground
+GitHub Issue: https://github.com/openwallet-foundation-labs/vc-api/issues/28
+The VC Playground is a demonstration application for Verifiable Credential issuance and verification: https://vcplayground.org.
+Listing in the VC Playground is an opportunity to gain visibility on the project and test interoperability.
+Help Required
+The following actions from the OWF would likely be helpful in achieving the upcoming goals:
+- Advice on future architectural directions, such as transforming the project into a Credo plugin
+- Notification on any publicity opportunities for the project
+Project Lifecycle Stage Recommendation
+Our recommendation is to remain a Labs project.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2024 Project Annual Reviews
+Projects must provide an annual review to the TAC to ensure that the project is still active and in the correct lifecycle stage. The following calendar provides the timing for when these reviews are required to be presented to the TAC:
+
+
+
+| Project |
+Stage |
+Date Accepted |
+2024 Review |
+
+
+
+
+| SD-JWT Python |
+Labs |
+May 27, 2023 |
+Jun 12, 2024 |
+
+
+| SD-JWT Kotlin |
+Labs |
+May 27, 2023 |
+Jun 12, 2024 |
+
+
+| Farmworker Wallet OS |
+Labs |
+Aug 9, 2023 |
+Aug 21, 2024 |
+
+
+| VC-API |
+Labs |
+Sep 28, 2023 |
+Oct 2, 2024 |
+
+
+| Wallet Framework .NET |
+Labs |
+Oct 4, 2023 |
+Oct 16, 2024 |
+
+
+| Android Identity Library |
+Labs |
+Oct 18, 2023 |
+Oct 30, 2024 |
+
+
+| SD-JWT JavaScript |
+Labs |
+Nov 1, 2023 |
+Nov 13, 2024 |
+
+
+| SD-JWT Rust |
+Labs |
+Nov 15, 2023 |
+Nov 27, 2024 |
+
+
+| Credo |
+Growth |
+Nov 29, 2023 |
+Dec 11, 2024 |
+
+
+| SD-JWT .NET |
+Labs |
+Nov 29, 2023 |
+Dec 11, 2024 |
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+2025 Project Annual Reviews
+Projects must provide an annual review to the TAC to ensure that the project is still active and in the correct lifecycle stage. The following calendar provides the timing for when these reviews are required to be presented to the TAC:
+
+
+
+| Project |
+Stage |
+Date Accepted |
+2025 Review |
+
+
+
+
+| Multiformat VC for iOS |
+Labs |
+Jan 24, 2024 |
+Feb 5, 2025 |
+
+
+| Bifold |
+Growth |
+Feb 21, 2024 |
+Mar 5, 2025 |
+
+
+| EUDI Wallet Kit React Native |
+Labs |
+Apr 17, 2024 |
+Apr 30, 2025 |
+
+
+| Trust Spanning Protocol |
+Labs |
+May 15, 2024 |
+May 14, 2025 |
+
+
+| Tuvali |
+Labs |
+May 15, 2024 |
+May 14, 2025 |
+
+
+| Credhub |
+Labs |
+May 29, 2024 |
+May 28, 2025 |
+
+
+| MDL JavaScript |
+Labs |
+Jun 12, 2024 |
+Jun 11, 2025 |
+
+
+| SD-JWT Python |
+Labs |
+May 27, 2023 |
+ |
+
+
+| SD-JWT Kotlin |
+Labs |
+May 27, 2023 |
+ |
+
+
+| Farmworker Wallet OS |
+Labs |
+Aug 9, 2023 |
+ |
+
+
+| VC-API |
+Labs |
+Sep 28, 2023 |
+ |
+
+
+| Wallet Framework .NET |
+Labs |
+Oct 4, 2023 |
+ |
+
+
+| Android Identity Library |
+Labs |
+Oct 18, 2023 |
+ |
+
+
+| SD-JWT JavaScript |
+Labs |
+Nov 1, 2023 |
+ |
+
+
+| SD-JWT Rust |
+Labs |
+Nov 15, 2023 |
+ |
+
+
+| Credo |
+Growth |
+Nov 29, 2023 |
+ |
+
+
+| SD-JWT .NET |
+Labs |
+Nov 29, 2023 |
+ |
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+SD-JWT .NET
+Project Description
+A .NET implementation of the Selective Disclosure for JWTs (SD-JWT) specification.
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+SD-JWT JavaScript
+Project Description
+A JavaScript implementation of the Selective Disclosure for JWTs (SD-JWT) specification.
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+SD-JWT Kotlin
+Project Description
+A Kotlin implementation of the Selective Disclosure for JWTs (SD-JWT) specification.
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+SD-JWT Python
+Project Description
+This is the reference implementation of the IETF SD-JWT specification maintained by the editors of the specification together with other contributors. It is written in Python.
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+SD-JWT Rust
+Project Description
+A Rust implementation of the Selective Disclosure for JWTs (SD-JWT) specification.
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Trust Spanning Protocol
+Project Description
+This project is an early impementation of the draft Trust Spanning Protocol (TSP).
+According to the above referenced specification, "The Trust Spanning Protocol (TSP) facilitates secure communication between endpoints with potentially different identifier types, using message-based exchanges. As long as these endpoints use identifiers based on public key cryptography (PKC) with a verifiable trust root, TSP ensures their messages are authentic and, if optionally chosen, confidential. Moreover, it presents various privacy protection measures against metadata-based correlation exploitations. These attributes of TSP together allow endpoints to form authentic relationships rooted in their respective verifiable identifiers (VIDs), viewing TSP messages as virtual channels for trustworthy communication."
+A shorter introduction of TSP can be found in this blog post.
+This project's current code includes a Rust implementation of all TSP features. We also plan to incorporate/develop related features such as additional Verifiable Identifier types, additional transport layer mechanisms, different language bindings as needed and integration modules needed to be compatible with other OpenWallet projects.
+In addition, we may add and welcome trust task or application specific extensions.
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Tuvali
+Project Description
+A library which implements the OpenID4BLE specification for Android and IOS. It's written in Kotlin and Swift.
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+VC API
+Project Description
+The VC API is specification for a set of APIs for VC lifecycle management (https://w3c-ccg.github.io/vc-api/). This includes operations such as credential issuance, verification, and exchange. It is a W3C CCG work item and, as of the submission of this proposal, it is in “draft community report” status.
+The VC API’s design is informed by use cases across a range of domains. Several of these use cases are collected in a working group note (https://w3c-ccg.github.io/vc-api-use-cases/).
+This project is an implementation of the VC API. The implementation aims to enable organizations and individuals to effortlessly conduct SSI operations over HTTP without requiring technical expertise, making it seamless to integrate into existing projects.
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Wallet Framework .NET
+Project Description
+The wallet-framework-dotnet is a framework designed for .NET, focusing on providing a multi-platform wallet framework. Initially a part of the Hyperledger Aries project (Aries Framework .NET), this initiative has now branched out to cater to a broader audience. The primary aim is to create a multiprotocol wallet framework enabling implementations of OpenID4VC and SD-JWT VC, in accordance to the European Identity Wallet initiative's objectives.
+Currently, the framework supports DidComm v1 and AnonCreds. There is an active intention to extend support for other promising protocols, notably DidComm v2, to ensure the framework remains at the forefront of digital identity solutions.
+Furthermore, the team is considering the development of SD-JWT credentials as a standalone library. This might transition into a separate project proposal in the future, underscoring the commitment to modular and reusable components in the digital identity space.
+Source Repositories
+
+Chat Channel
+
+History
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
Welcome to the OpenWallet Foundation's (OWF) Technical Advisory Council (TAC) website. Here you will find:
-
What is the TAC
Learn more about the Technical Advisory Council's role, responsibilities, and voting members
-
Governing Documents
Review the OpenWallet Foundation TAC Governing Documents
-
TAC Meetings
See meeting invite details and meeting notes from past meetings
-
Projects
Explore the OpenWallet Foundation Projects
-
Special Interest Groups
Join an OpenWallet Foundation Special Interest Groups (SIGs)
-
Task Forces
Work on an OpenWallet Foundation Task Forces
"},{"location":"SIGs/","title":"Special Interest Groups (SIGs)","text":"A special interest group (SIG) under the Technical Advisory Council (TAC) is a group with a shared interest in advancing a specific area of knowledge, learning, or technology related to the mission of the OpenWallet Foundation where members cooperate to affect or to produce solutions within their particular field. Unlike a task force, SIGs are typically long running and may or may not produce any deliverables. A SIG can be created by anyone in the OpenWallet Foundation community and must be proposed to and approved by the TAC.
Tip
If you would like to propose a Special Interest Group, please see the SIG proposal process.
"},{"location":"SIGs/#active-sigs","title":"Active SIGs","text":" - Architecture
- Credential Format Comparison
- Digital Wallet and Agent Overviews
- Safe Wallet
- Wallet Interoperability
"},{"location":"SIGs/architecture/","title":"Architecture Special Interest Group (SIG)","text":"This SIG is focused on conversations related to the architecture of digital wallet engines.
This SIG was accepted by the TAC on April 5, 2023.
"},{"location":"SIGs/architecture/#participating","title":"Participating","text":"This SIG is an open group. Anyone in the OpenWallet Foundation community can join and participate. There is no formal sign up process. Just show up and participate.
"},{"location":"SIGs/architecture/#meetings","title":"Meetings","text":"The architecture SIG meets weekly on Mondays at 11:00 AM US/Pacific time. For details, see architecture SIG meeting details. For past notes and recordings, see the architecture SIG wiki.
"},{"location":"SIGs/architecture/#discord","title":"Discord","text":"Please join the OpenWallet Foundation Discord and participate in the discussion in the #architecture-sig channel.
"},{"location":"SIGs/credential-format-comparison/","title":"Credential Format Comparison Special Interest Group (SIG)","text":"This SIG is dedicated to maintaining information about available credential formats for the benefit of OWF projects and the wider community. The topic is more complex than one might assume on first sight, since there are more than 14 formats for representing digital credentials and most of those formats can be combined with different signature algorithms, ways to represent cryptographic keys (with alone more than a hundred DID methods), status management methods, trust management methods and so on.
There is pre-existing work started at Internet Identity Workshop (IIW 34, Spring 2022) and extended and augmented during Rebooting the Web of Trust (RWOT-XI, The Hague, Sept 2022).
It consists of a \u201ccredential format comparison matrix\u201d, containing information about the technical options in the different dimensions (formats, signature algorithms, \u2026) as well as known credential profiles, i.e. concrete combinations used in implementations and an article explaining the \u201cmatrix\u201d.
- Article: https://github.com/WebOfTrustInfo/rwot11-the-hague/blob/master/final-documents/credential-profile-comparison.pdf
- Source Code: https://github.com/openwallet-foundation/credential-format-comparison-sig
- Rendered Matrix: https://openwallet-foundation.github.io/credential-format-comparison-sig/#/
This SIG was accepted by the TAC on May 31, 2023. See Credential Format Comparison SIG Proposal for more details.
"},{"location":"SIGs/credential-format-comparison/#participating","title":"Participating","text":"This SIG is an open group. Anyone in the OpenWallet Foundation community can join and participate. There is no formal sign up process. Just show up and participate.
If you are interested in participating, please join the OpenWallet Foundation Discord and participate in the discussion in the #credential-format-comparison-sig channel.
"},{"location":"SIGs/digital-wallet-and-agent-overviews/","title":"Digital Wallet and Agent Overviews Special Interest Group (SIG)","text":"The objectives of this SIG is to further develop and maintain the Digital Wallet Overview and making a similar overview for digital identity agents/SDKs. These overviews should provide transparency of the characteristics of wallets and agents in order to allow for comparison and effective decision making on which wallet is applicable for your use case. By creating awareness of these overviews, this work can lead to less fragmentation of the SSI playing field and increase adoption.
This SIG was accepted by the TAC on September 20, 2023. See Digital Wallet and Agent Overviews SIG Proposal for more details.
"},{"location":"SIGs/digital-wallet-and-agent-overviews/#participating","title":"Participating","text":"This SIG is an open group. Anyone in the OpenWallet Foundation community can join and participate. There is no formal sign up process. Just show up and participate.
If you are interested in participating, please join the OpenWallet Foundation Discord and participate in the discussion in the #digital-wallet-and-agent-overviews-sig channel.
"},{"location":"SIGs/safe-wallet/","title":"Safe Wallet Special Interest Group (SIG)","text":"This SIG will create, distribute and promote a set of material that will become the de-facto way to determine how \"safe\" the new breed of digital wallets is, and be able to compare them effectively. This will increase the visibility of the solutions to correlation and profiling issues that could be introduced with digital wallet deployments.
This SIG was accepted by the TAC on September 20, 2023. See Safe Wallet SIG Proposal for more details.
"},{"location":"SIGs/safe-wallet/#participating","title":"Participating","text":"This SIG is an open group. Anyone in the OpenWallet Foundation community can join and participate. There is no formal sign up process. Just show up and participate.
If you are interested in participating, please join the OpenWallet Foundation Discord and participate in the discussion in the #safe-wallet-sig channel.
"},{"location":"SIGs/wallet-interoperability/","title":"Wallet Interoperability Special Interest Group (WISIG)","text":"The WISIG will focus on defining, publishing, and testing wallet interoperability profiles (WIPs). The WISIG will define how to create wallet interoperability profiles, and create WIPs for different wallet technical stacks, ensuring that digital wallets implementations adhere to the global standards referenced in the profile and can interact seamlessly with one another. The group will start by taking over maintenance of the existing AIP 2.0 profile, and create additional, parallel Wallet Interoperability Profiles that cover other technical stacks, such as OpenID4VCs, mDL/mDocs and so on. The group will also develop tools and guidance for testing the profiles to enable demonstrations of compliance and interoperability, leveraging existing test suites where available, and developing new test suites as needed.
This SIG was accepted by the TAC on October 2, 2024. See Wallet Interoperability SIG Proposal for more details.
"},{"location":"SIGs/wallet-interoperability/#participating","title":"Participating","text":"This SIG is an open group. Anyone in the OpenWallet Foundation community can join and participate. There is no formal sign up process. Just show up and participate.
If you are interested in participating, please join the OpenWallet Foundation Discord and participate in the discussion in the #wallet-interoperability-sig channel.
"},{"location":"SIGs/updates/2024/","title":"2024 Quarterly Updates","text":"The Special Interest Groups (SIGs) must provide a quarterly update to the TAC to ensure that the SIG is still active and that there is still value in hosting the special interest group. The following calendar provides the timing for when these updates are required to be presented to the TAC:
Quarter Special Interest Group TAC Meeting Q1 Architecture SIG 2024-01-10 Q1 Credential Format Comparison SIG 2024-02-07 Q1 Digital Wallet and Agent Overviews SIG 2024-02-21 Q1 Safe Wallet SIG 2024-03-06 Q2 Architecture SIG 2024-04-03 Q2 Credential Format Comparison SIG 2024-05-01 Q2 Digital Wallet and Agent Overviews SIG 2024-05-29 Q2 Safe Wallet SIG 2024-06-12 Q3 Architecture SIG 2024-07-10 Q3 Credential Format Comparison SIG 2024-07-24 Q3 Digital Wallet and Agent Overviews SIG 2024-08-07 Q3 Safe Wallet SIG 2024-09-04 Q4 Architecture SIG 2024-10-02 Q4 Credential Format Comparison SIG 2024-10-16 Q4 Digital Wallet and Agent Overviews SIG 2024-11-13 Q4 Safe Wallet SIG 2024-11-13"},{"location":"governance/","title":"Governing Documents","text":"The following are the governing documents used by the OpenWallet Foundation's Technical Advisory Council.
"},{"location":"governance/#foundation-governance","title":"Foundation Governance","text":"The OpenWallet Foundation is governed by the following documents, of which the Technical Advisory Council follows:
- Charter
- Antitrust Policy
- Code of Conduct
"},{"location":"governance/#technical-advisory-council-governance","title":"Technical Advisory Council Governance","text":"The Technical Advisory Council is governed with the following documents:
- Roles and Responsibilities
- TAC Alternate Policy
- Elections
- Project Lifecycle
- Special Interest Groups
- Task Forces
- Deliverable Lifecycle
- Composition
"},{"location":"governance/#project-requirements","title":"Project Requirements","text":"The Technical Advisory Council has created the following requirements for projects:
- Project Annual Review Process
- Common Repository Structure
- MAINTAINERS.md File Contents
- Maintainer Inactivity
- Security Policy
- Release Taxonomy
- Archiving Inactive Repositories
"},{"location":"governance/#project-resources","title":"Project Resources","text":"The Technical Advisory Council offers the following services and tooling to projects:
- Paid Tooling Policy
- Project and Lab Services
- Content Plan
"},{"location":"governance/alternate-policy/","title":"TAC Alternate Policy","text":"A TAC voting member may designate an alternate for a specific meeting, and must notify the chair in advance of the meeting. The TAC voting member is responsible for ensuring that the named alternate has enough information to represent the TAC voting member in all matters that will be covered in the meeting. The named alternate will participate in any votes that occur during the meeting for which they were named an alternate, and their vote will count as if it were cast by the TAC voting member.
Warning
If a TAC voting member regularly names an alternate and
- is a TAC Premier Sponsor Representative, then that TAC voting member should consider whether they should replace themselves with the alternate, or
- is a TAC \"At Large\" Representative, then that TAC voting member should consider whether they should resign.
"},{"location":"governance/antitrust/","title":"Antitrust Policy","text":"The LF Europe Antitrust Policy listed at http://lfeurope.be/policies will apply for all Collaborators in the Project.
"},{"location":"governance/archiving-inactive-repositories/","title":"Archiving Inactive Repositories","text":"OpenWallet Foundation very much appreciates the contributions of the community; however, it is important to archive source repositories that have become inactive in order to ensure that others in the community are not using code or reporting issues on a repository that is not being maintained.
Any repository that has not had a release for 12 months or that has had no commits for 6 months may be archived.
Projects will be notified via a PR in the appropriate repository, as well as a notice in the project appropriate Discord channel and mailing list, if they exist.
Generally speaking if the project's maintainers request to keep the repository active, the request will be honored. However if the repository has a lot of out of date dependencies, particulaly ones relating to security vulnerabilites, this request may not be honored.
A request by the project's maintainers to un-archive a repository for the purposes of active contribution will be honored, unless the project is in an emeritus stage. In those cases the project lifecycle issues will need to be resolved first.
"},{"location":"governance/charter/","title":"OpenWallet Foundation Charter","text":"Exhibit B
The OpenWallet Foundation Charter
Linux Foundation Europe
Effective May 22, 2023
-
Mission and Scope of the OpenWallet Foundation.
The purpose of the OpenWallet Foundation (the \u201cOWF\u201d) is to support various open source, open data and/or other open projects relating to or supporting development of digital wallets, including infrastructure and support initiatives related thereto (each such project, a \u201cTechnical Project\u201d) , in accordance with the provisions of this Charter. The governance of each Technical Project is as set forth in the charter for that Technical Project.
The OWF aims to enable entities to transact securely, and in a privacy enhancing fashion, in- person and on-line where attributes stored in, and managed by, the wallet. The OWF will:
- develop and maintain open source code for wallets to enable and ensure wallet interoperability,
- advocate for the adoption of the interoperable digital wallet technology, and
- collaborate with Standards Development Organizations (SDOs) in the development and proliferation of open standards related to digital wallets
The OWF will not publish a publicly available wallet (including into any application stores).
The OWF supports the Technical Projects. The OWF operates under the guidance of the Governing Board of the OWF (the \u201cGoverning Board\u201d) and Linux Foundation Europe (the \u201cLFEU\u201d) as may be consistent with Linux Foundation Europe\u2019s tax-exempt status.
The Governing Board manages the OWF. The Governing Board may establish other committees and other working groups (collectively, and including the Technical Advisory Council, \u201cCommittees\u201d) which will report to the Governing Board.
-
Sponsorship.
- The OWF will be composed of Premier, General and Associate Sponsors (each, a \u201cSponsor\u201d and, collectively, the \u201cSponsors\u201d) in Good Standing. All Sponsors must be current Sponsors of LFEU (at any level) to participate in the OWF as a Sponsor. All sponsors in the OWF, enjoy the privileges and undertake the obligations described in this Charter, as from time-to-time amended by the Governing Board, with the approval of LFEU. During the term of their sponsorship, all Participants will comply with all such policies as the LFEU Board of Directors and/or the OWF may adopt with notice to Sponsors.
- Premier Sponsors will be entitled to appoint a representative to the Governing Board and any Committee.
- General Sponsors, acting as a class, will be entitled to annually elect one representative to the Governing Board for every ten General Sponsors, up to a maximum of three total representatives, provided that there will always be at least one General Sponsor representative, even if there are less than ten General Sponsors. The Governing Board determines the General Sponsor representative election process.
- The Associate Sponsor category of sponsorship is limited to Associate Sponsors of LFEU. The Governing Board may set additional criteria for sponsoring the OWF as an Associate Sponsor. If the Associate Sponsor is itself a membership or participation organization, Associate Sponsorship in the OWF does not confer any privileges or rights to the members or participants of the Associate Sponsor.
- Sponsors will be entitled to:
- participate in OWF general meetings, initiatives, events and any other activities; and
- identify themselves as sponsors of the OWF supporting the OWF community.
-
Governing Board
-
The Governing Board voting members will consist of:
- one representative appointed by each Premier Sponsor;
- the TAC Representative (as defined below), or, in the absence of a chair and with the approval of the Governing Board, any active contributor to a Technical Project so designated by the TAC (such chair or designee the \u201cTAC Representative\u201d); and
- the elected General Sponsor representative or representatives.
-
The Governing Board will also include nonvoting members consisting of the GAC Representative (defined in Section 4) and Associate Representative.
- The Associate Representative will be chosen based on their efforts and potential to advance the OWF mission. The Associate Representative will be selected by the Governing Board voting representatives through a process determined by the Governing Board.
-
Only one Sponsor that is part of a group of Related Companies (as defined in Section 7) may appoint, or nominate for a sponsorship class election, a representative on the Governing Board. No single Sponsor, company or set of Related Companies will be entitled to: (i) appoint or nominate for sponsorship class election more than one representative for the Governing Board, or (ii) have more than two representatives on the Governing Board.
- The only path to two representatives from the same group of Related Companies that will be acceptable will be for one Sponsor to appoint or nominate a representative to the Governing Board and have another of its employees, or an employee of one of its Related Companies, serve as the TAC Representative on the Governing Board.
-
Conduct of Meetings
- Governing Board meetings will be limited to the Governing Board representatives, the Outreach Committee Chair, invited guests and OWF staff.
- Governing Board meetings follow the requirements for quorum and voting outlined in this Charter. The Governing Board may decide whether to allow named representatives (one per Sponsor per Governing Board and per Committee) to attend as an alternate.
- The Governing Board meetings will be private unless decided otherwise by the Governing Board. The Governing Board may invite guests to participate in consideration of specific Governing Board topics (but such guests may not participate in any vote on any matter before the Governing Board).
-
Officers
- The officers (\u201cOfficers\u201d) of the OWF as of the first meeting of the Governing Board will be a Chairperson (\u201cChair\u201d) and a Treasurer. Additional Officer positions may be created by the Governing Board.
- The Chair will preside over meetings of the Governing Board, manage any day-to-day operational decisions, and will submit minutes for Governing Board approval.
- The Treasurer will assist in the preparation of budgets for Governing Board approval, monitor expenses against the budget and authorize expenditures approved in the budget.
-
The Governing Board will be responsible for overall oversight of the OWF, including:
- approve a budget directing the use of funds raised by the OWF from all sources of sponsorship or other revenue, including to pay for the hiring of OWF leadership and staff;
- vet and select a qualified leadership team to run the day-to-day management activities of the organization and evaluate the performance of the team;
- provide feedback and input to the OWF leadership team responsible for planning and managing the day-to-day operation of the OWF;
- maintain, if desired, a guiding principles document;
- nominate and elect Officers of the OWF;
- supervise and support the leadership team on OWF business and community outreach matters;
- work with the LFEU on any legal matters that arise;
- adopt and maintain policies or rules and procedures for the OWF (subject to LFEU\u2019s approval);
- establish advisory bodies, committees, programs or councils to resolve any particular matter or in support of the mission of the OWF and/or its Technical Projects including in support of end-users and ambassadors for the project any Technical Project;
- establish any OWF conformance programs for its trademarks and solicit input (including testing tools) if deemed necessary from the applicable oversight body of any Technical Project for defining and administering any programs related to conformance with such Technical Project (each, a \u201cConformance Program\u201d);
- publish use cases, user stories, websites and priorities to help inform the ecosystem and technical community;
- approve procedures for the nomination and election of any representative of the General Sponsors to the Governing Board and any Officer or other positions created by the Governing Board; and
- vote on all decisions or matters coming before the Governing Board.
-
Government Advisory Council
- The Government Advisory Council (the \u201cGAC\u201d) will provide the OWF advice from government entities approved to participate by the Governing Board. Members of the GAC must be national governments, multinational governmental organizations and treaty organizations, or public authorities. Each may appoint one representative and one alternate representative to the GAC. There are no fees to participate in the GAC.
- The GAC will provide advice to OWF on issues of public policy, and especially where there may be an interaction between OWF's activities and national policies, laws or international agreements.
- The Governing Board may appoint a chairperson of the GAC or delegate responsibility for selecting a chairperson to the GAC. The GAC chairperson or another person chosen by the GAC chairperson will serve as the \u201cGAC Representative\u201d responsible for reporting progress back to the Governing Board and interfacing with the TAC. The GAC Representative may attend meetings of the Governing Board and TAC as a non-voting member.
-
Technical Advisory Council
-
The role of the TAC is to facilitate communication and collaboration among the Technical Projects. The TAC will be responsible for:
- maintaining an overall strategic vision for technical collaboration and coordinating collaboration among Technical Projects, including development of an overall technical vision for the community;
- making recommendations to the Budget Committee of resource priorities for Technical Projects;
- electing annually a chairperson to preside over meetings, set the agenda for meetings, ensure meeting minutes are taken and who will also serve on the Governing Board as the TAC\u2019s representative (the \u201cTAC Representative\u201d);
- creating, maintaining and amending project lifecycle procedures and processes, deciding where Technical Projects fall within that lifecycle;
- determining when a technical project should be admitted as a Technical Project or any Technical Project should be considered a TAC Project; and
- such other matters related to the technical role of the TAC as may be communicated to the TAC by the Governing Board.
-
The voting members of the TAC consist of:
- one representative appointed by each Premier Sponsor;
- up to two \u201cat large\u201d representatives appointed by vote of the TAC; and
- one representative appointed by the technical oversight body (e.g., a technical steering committee) of each TAC Project (as defined herein).
-
TAC meetings are intended to be open to observe by Sponsors, contributors to any TAC Project and others in the general public interested in the OpenWallet Foundation. The TAC may decide whether to allow named representatives (one per voting member) to attend as an alternate.
- At the start of the OWF, \u201cTAC Projects\u201d are those Technical Projects listed as having voting representatives on the TAC on the Directed Fund\u2019s web site. Thereafter, any Technical Project can become a TAC Project through the approval of the Technical Project\u2019s technical oversight body and the TAC (by a two-third\u2019s vote). The TAC may approve and modify a project lifecycle policy that will address the incubation, archival and other stages of TAC Projects.
- The TAC representatives will elect a chair to preside over meetings, ensure minutes are taken and drive the TAC agenda with input from the TAC representatives.
-
Voting
- Quorum for Governing Board and Committee meetings will require at least fifty percent of the voting representatives. If advance notice of the meeting has been given per normal means and timing, the Governing Board may continue to meet even if quorum is not met, but will be prevented from making any decisions at the meeting.
- Ideally decisions will be made based on consensus. If, however, any decision requires a vote to move forward, the representatives of the Governing Board or Committee, as applicable, will vote on a one vote per voting representative basis.
- Except as provided in Section 14.a. or elsewhere in this Charter, decisions by vote at a meeting will require a simple majority vote, provided quorum is met. Except as provided in Section 14.a. or elsewhere in this Charter, decisions by electronic vote without a meeting will require a majority of all voting representatives.
- In the event of a tied vote with respect to an action that cannot be resolved by the Governing Board, the Chair may refer the matter to the LFEU for assistance in reaching a decision. If there is a tied vote in any Committee that cannot be resolved, the matter may be referred to the Governing Board.
-
Subsidiaries and Related Companies
-
Definitions:
- \u201cSubsidiaries\u201d means any entity in which a Sponsor owns, directly or indirectly, more than fifty percent of the voting securities or participation interests of the entity in question;
- \u201cRelated Company\u201d means any entity which controls or is controlled by a Sponsor or which, together with a Sponsor, is under the common control of a third party, in each case where such control results from ownership, either directly or indirectly, of more than fifty percent of the voting securities or participation interests of the entity in question; and
- \u201cRelated Companies\u201d are entities that are each a Related Company of a Sponsor.
-
Only the legal entity which has executed a Project Sponsorship Agreement and its Subsidiaries will be entitled to enjoy the rights and privileges of such sponsorship; provided, however, that such Sponsor and its Subsidiaries will be treated together as a single Sponsor.
- If a Sponsor is itself a foundation, association, consortium, open source project, membership organization, participation organization, user group or other entity that has members or sponsors, then the rights and privileges granted to such Sponsor will extend only to the employee-representatives of such Sponsor, and not to its members or sponsors, unless otherwise approved by the Governing Board in a specific case.
- OWF sponsorship is non-transferable, non-salable and non-assignable, except a Sponsor may transfer its current sponsorship privileges and obligations to a successor of substantially all of its business or assets, whether by merger, sale or otherwise; provided that the transferee agrees to be bound by this Charter and the Bylaws and policies required by LFEU sponsorship.
-
Good Standing
- Linux Foundation Europe\u2019s Good Standing Policy is available at https://linuxfoundation.eu/policies and will apply to all Sponsors of this OWF.
-
Trademarks
- Any trademarks relating to the OWF or any Technical Project, including without limitation any mark relating to any conformance program, must be transferred to and held by LFEU or an entity in LFEU\u2019s control and available for use pursuant to LFEU\u2019s trademark usage policy, available at https://linuxfoundation.eu/policies.
-
Antitrust Guidelines
- All Sponsors must abide by Linux Foundation Europe\u2019s Antitrust Policy available at https://linuxfoundation.eu/policies.
- All Sponsors must encourage open participation from any organization able to meet the sponsorship requirements, regardless of competitive interests. Put another way, the Governing Board will not seek to exclude any Sponsor based on any criteria, requirements or reasons other than those that are reasonable and applied on a non- discriminatory basis to all Sponsors.
-
Budget
- The Governing Board will approve an annual budget and never commit to spend in excess of funds raised. The budget and the purposes to which it is applied must be consistent with both (a) the non-profit and tax-exempt mission of LFEU and (b) the goals of any Technical Project.
- LFEU will provide the Governing Board with regular reports of spend levels against the budget. Under no circumstances will LFEU have any expectation or obligation to undertake an action on behalf of the OWF or otherwise related to the OWF that is not covered in full by funds raised by the OWF.
- In the event an unbudgeted or otherwise unfunded obligation arises related to the OWF, LFEU will coordinate with the Governing Board to address gap funding requirements.
-
General & Administrative Expenses
- LFEU will have custody of and final authority over the usage of any fees, funds, and other cash receipts.
- A General & Administrative (G&A) fee will be applied by LFEU to funds raised to cover sponsorship records, finance, accounting, and human resources operations. The G&A fee will be 9% of the OWF\u2019s first EUR 1,000,000 of gross receipts each year and 6% of the OWF\u2019s gross receipts each year over EUR 1,000,000.
-
General Rules and Operations.
The OWF activities must:
- engage in the work of the project in a professional manner consistent with maintaining a cohesive community, while also maintaining the goodwill and esteem of LFEU in the open source community;
- respect the rights of all trademark owners, including any branding and usage guidelines;
- engage or coordinate with LFEU on all outreach, website and marketing activities regarding the OWF or on behalf of any Technical Project that invoke or associate the name of any Technical Project or LFEU; and
- operate under such rules and procedures as may be approved by the Governing Board and confirmed by LFEU.
-
Amendments
- This Charter may be amended by a two-thirds vote of the entire Governing Board, subject to approval by LFEU.
"},{"location":"governance/code-of-conduct/","title":"Code of Conduct","text":"The TAC may adopt a code of conduct (\u201cCoC\u201d) for the Project, which is subject to approval by LF Europe. In the event that a Project-specific CoC has not been approved, the LF Europe Code of Conduct listed at http://lfeurope.be/policies will apply for all Collaborators in the Project.
"},{"location":"governance/common-repository-structure/","title":"Common Repository Structure","text":"OpenWallet Foundation projects are required to maintain a standard set of files in each repository. This document describes the required and recommended files.
"},{"location":"governance/common-repository-structure/#required-files-with-specified-content","title":"Required Files with Specified Content","text":"Repositories MUST have these files with the specific content in the linked files, or a file with a link to the specified content with minimal exposition. These files MUST be at the root of the repository.
"},{"location":"governance/common-repository-structure/#required-files-with-variable-content","title":"Required Files with Variable Content","text":"Repositories MUST have these files. Named files MUST be at the root of the repository, and may have format suffixes such as .md, .rst, or .txt.
README - A description of the project that contains information or links to information such as: - A reference to the Apache license (required).
- The current and important past releases
- Documentation for developers and users
MAINTAINERS - A list of all current maintainers with contact info. A separate document covers the specifics.CONTRIBUTING - Directions on how to contribute code to the project, or a link to a page with that information.CHANGELOG - A human readable list of recent changes. Changes should at least include the current release. This file may be maintainer curated or mechanically produced.- Continuous Integration / Continuous Delivery (CICD) configurations - Configurations needed to run CICD on OpenWallet Foundation provided systems (e.g., .github/workflows).
"},{"location":"governance/common-repository-structure/#recommended","title":"Recommended","text":"Repositories SHOULD have these files. Named files SHOULD be at the root of the repository
NOTICE - As per section 4 subsection d of the Apache License, Version 2- Apache License Header information in each source code file. For new files added to OpenWallet Foundation repositories they SHOULD include the snippet
SPDX-License-Identifier: Apache-2.0 as part of the header. - Build files consistent with the implementation language, such as:
- For JavaScript/Node.js a
package.json file - For Ruby a
Gemfile file - For Java one of a Maven
pom.xml, an Apache Ant build.xml, or a Gralde build.gradle - file
- For Python
setup.py and requirements.txt files - For Go
go.mod and optionally go.sum - For Rust a
cargo.toml file - For multi-lingual repositories a
Makefile or executable build.sh script - For other languages, other standard build files a practitioner of the language would expect.
-
Testing code - Code to test the code in the repository (such as unit tests), in a location appropriate for the language.
Why not a MUST?
Not all repositories can be tested (homebrew, docs), which is the only reason this is a SHOULD.
"},{"location":"governance/common-repository-structure/#prohibited","title":"Prohibited","text":"Repositories MUST NOT have these files
- Executable binaries and shared library files built by code in the repository. This includes
.exe, .dll, .so, .a and .dylib files not otherwise part of a third party library.
"},{"location":"governance/common-repository-structure/#credits","title":"Credits","text":"This document is based on the Hyperledger Foundation's Common Respository Structure guideline.
"},{"location":"governance/content-plan/","title":"Content Plan","text":"This document provides details about the different channels that we have within the OpenWallet Foundation and what we expect each to be used for.
Channel
What
Roles
Discord
- Real-Time Communication: Chat services facilitate real-time, synchronous communication among users. Messages are sent and received instantly, enabling quick exchanges and conversations.
- Interactive Collaboration: Chat services are well-suited for interactive collaboration, allowing users to engage in live discussions, share files, collaborate on documents, and even conduct video calls in some cases.
Staff: Administers, creates new channels, and moderates
Community: Sends messages and monitors
Mailing Lists
- Asynchronous Communication: Mailing lists are primarily used for asynchronous communication. Users send messages to a central email address, which are then distributed to all subscribers. Subscribers can read and respond to messages at their convenience.
- Broadcasting Information: Mailing lists are effective for broadcasting information to a group of subscribers. They are commonly used for announcements, discussions, and sharing updates within a community or organization.
- Archiving: Mailing lists typically archive messages, allowing subscribers to access past discussions and reference previous communications. This archival feature can be valuable for maintaining a record of conversations and facilitating knowledge sharing.
Staff: Administers, creates new lists, and moderates
Community: Sends messages and monitors
GitHub
- Project-Based Source Code and User Documentation: Any source code for projects should utilize GitHub. GitHub pages should be used for hosting user documentation.
- TAC Governance Documentation and Other Relevant Information: Governance documentation for the TAC must be version controlled. As such, GitHub is the appropriate place to store this information in addition to other relevant TAC materials. Currently https://tac.openwallet.foundation is generated from markdown files in GitHub.
- SIG or Task Force Deliverables: A separate repo can be set up for SIGs and Task Forces so that they can have versioned control support for their deliverables.
Staff: Administers, creates new repos and teams
Maintainers: Reviews and handles issues and pull requests
Community: Use source,create issues, fork code, and contribute
Website
- Blogs
- Announcements
- Native content
- Events and Conferences
Staff: Administers and determines contents
Community: Visit and contribute blog posts
Wiki
- Project Meeting Minutes
- SIG Meeting Minutes
- Task Force Meeting Minutes
- Collaborative Editing
Staff: Administers and creates new spaces
Community: Creates and edits pages
LFX Meetings (Zoom)
- Project, SIG, and TAC meetings: All project, SIG, and TAC meetings must be held using LFX meetings. This ensures that a recording of the meeting is captured and available for people to catch up on what they may have missed. Send an email to operations@openwallet.foundation to get your meetings scheduled.
Staff: Administers and creates new meetings
Community: Attends meetings and listen to recordings
YouTube
- Community meeting recordings
- Webinar recordings
- Event recordings
Staff: Administers and adds videos and playlists
Community: Watch videos
Social Media
- Posts about activities and events that the community may be interested in
- Posts to announce new projects, SIGs, Task Forces, blog posts
Staff: Administers and posts content
Community: Reads content
"},{"location":"governance/deliverable-lifecycle/","title":"Publishing Deliverables in the OpenWallet Foundation Community","text":""},{"location":"governance/deliverable-lifecycle/#overview","title":"Overview","text":"This document outlines the process for publishing deliverables in the OpenWallet Foundation technical community. These deliverables will be created by task forces, special interest groups, or projects. The types of deliverables they can create depend on their goals, objectives, and scope. Here are some examples:
- Reports: Summarize findings or recommendations. These might be formal or informal.
- Action Plans: Outline the steps necessary to address a particular challenge or problem. These plans might include specific tasks, timelines, and responsible individuals.
- Recommendations: Provide guidance or proposals for solving problems, improving processes, or addressing gaps.
- Guidelines: Outline best practices or procedures for a specific industry, domain, or project.
- Templates and Tools: Serve as a starting point for creating new content and help users complete tasks, solve problems, or achieve specific goals frameworks that can be used by others.
- Whitepapers: Provide detailed analysis, data, or insights to help others understand a particular issue or opportunity. These are typically in-depth reports on complex topics.
- Case Studies: Illustrate the impact of real-world examples or hypothetical scenarios, including recommendations or findings.
- Frameworks and Models: Describe how to approach a particular problem or challange through conceptual frameworks, models, or architectures.
- Surveys and Research Reports: Gather data or validate hypotheses via surveys, interviews, or research studies, culminating in reports summarizing findings.
- Best Practices and Playbooks: Outline best practices for specific scenarios, industries, or processes, providing guidance on how to navigate complex situations.
- Metrics and KPIs: Determine how to measure progress toward goals or track the effectiveness of initiatives.
- Process Improvements: Identify areas for process improvement and develop new procedures, workflows, or tools to streamline operations or enhance efficiency.
- Training and Education Materials: Equip others with the knowledge and skills needed to tackle a specific challenge. Might include items such as curricula, tutorials, or guides.
- Scoping Documents: Outline the scope, objectives, and deliverables of a project, ensuring everyone is on the same page.
- Lessons Learned Reports: Summarize learnings, what worked well, and what didn't.
"},{"location":"governance/deliverable-lifecycle/#process","title":"Process","text":"There are three stages of an OWF deliverable -- draft, review, and released.
flowchart\n d[Draft]\n r[Review]\n c{Ready for Release?}\n v[Released]\n\n d -->|Submission| r\n r --> c\n c -->|Make Changes| d\n c -->|Create Release| v
A deliverable begins as a \"draft\" and retains this status until submitted to the community for review. At this point, the deliverable will be considered to be in the \"review\" stage and retains this status until the review period has ended. After the review period has ended, the task force, special interest group, or project will determine if the deliverable is ready for release. If the task force, special interest group, or project chooses to make changes, the deliverable will return to a \"draft\" stage where they can address the concerns of the community. The task force, special interest group, or project can also determine that the deliverable is ready for release. In which case, a \"released\" version can be created. See required contents for more information on what should be included within a \"released\" deliverable.
"},{"location":"governance/deliverable-lifecycle/#draft","title":"Draft","text":"During the \"draft\" stage, the deliverable is being prepared by the task force, special interest group, or project. This includes writing the technical content and ensuring that it meets the standards of the OWF technical community. If there are any concerns about the technical content that cannot be addressed by consensus of the task force, special interest group, or project members, then the community may address these concerns during the \"review\" stage.
"},{"location":"governance/deliverable-lifecycle/#submission","title":"Submission","text":"The task force, special interest group, or project lead may submit a version of their deliverable to the community for review. They can do this by sending an email to the TAC mailing list. The email should include the following information:
- A brief description of the deliverable.
- A link to the deliverable. Ideally, this should be a link to a pull request that contains the version of the deliverable where people in the community will be able to provide their feedback.
- A link to the task force, special interest group, or project that submitted the deliverable.
"},{"location":"governance/deliverable-lifecycle/#review","title":"Review","text":"The applicable period to review a submitted deliverable will be no shorter than four weeks. The community will make reasonable efforts to provide feedback on the submitted version during the review period and provide any critical comments or objections, with sufficient specificity for the task force, special interest group, or project members to respond and, if required, to facilitate resolution.
Info
Comments and feedback can be provided by anyone in the OWF community.
"},{"location":"governance/deliverable-lifecycle/#ready-for-release","title":"Ready for Release","text":"After the applicable review period has elapsed, the task force, special interest group, or project members can review the feedback received and determine if the deliverable is ready for review. If the task force, special interest group, or project chooses to make changes, the deliverable will return to a \"draft\" stage where they can address the concerns of the community. The task force, special interest group, or project can also determine that the deliverable is ready for release. In which case, a \"released\" version can be created.
"},{"location":"governance/deliverable-lifecycle/#released","title":"Released","text":"The task force, special interest group, or project should ensure that the required contents are included in any release.
"},{"location":"governance/deliverable-lifecycle/#required-contents","title":"Required Contents","text":""},{"location":"governance/deliverable-lifecycle/#copyright-notice","title":"Copyright Notice","text":"Important
If the deliverable originated from an external entity that has already provided a copyright notice, there is no need to replace that notice.
The copyright notice must be included in all versions of the deliverable. The copyright notice should include the OpenWallet Foundation as well as the year of publication.
Quote
Copyright \u00a9 2024 OpenWallet Foundation.
"},{"location":"governance/deliverable-lifecycle/#license-notice","title":"License Notice","text":"The license notice must be included in all versions of the deliverable. The license notice should include a reference to the CC-BY-4.0 license.
Quote
These materials are made available under and are subject to the Creative Commons Attribution 4.0 International license (http://creativecommons.org/licenses/by/4.0/legalcode).
"},{"location":"governance/deliverable-lifecycle/#disclaimer","title":"Disclaimer","text":"A disclaimer should be included in all versions of the deliverable. The disclaimer should include the following text:
Quote
These materials are a deliverable of the OWF community. If you have concerns or suggestions regarding the content, please file a pull request.
"},{"location":"governance/elections/","title":"Elections","text":""},{"location":"governance/elections/#electing-a-chair","title":"Electing a Chair","text":"From the OWF Charter
The TAC is responsible for ... electing annually a chairperson to preside over meetings, set the agenda for meetings, ensure meeting minutes are taken and who will also serve on the Governing Board as the TAC\u2019s representative (the \u201cTAC Representative\u201d).
The TAC voting members (as defined by the charter) will elect a chair on a yearly basis. Only TAC voting members are eligible to run for the TAC chair seat. Electing a chair will be completed through the voting process outlined below. If the TAC chair must leave their position during their term or is otherwise unable to fulfill their duties, they should submit a resignation and allow the TAC to fill the vacancy using the process outlined below.
"},{"location":"governance/elections/#electing-a-vice-chair","title":"Electing a Vice Chair","text":"The TAC voting members (as defined by the charter) will elect a vice chair on a yearly basis. Only TAC voting members are eligible to run for the TAC vice chair seat. Electing a vice chair will be held in conjunction with the chair election using the voting process outlined below. The person with the second highest number of votes will serve as the vice chair. If the TAC vice chair must leave their position during their term or is otherwise unable to fulfill their duties, they should submit a resignation and allow the TAC to fill the vacancy using the process outlined below.
"},{"location":"governance/elections/#electing-at-large-representatives","title":"Electing \"At Large\" Representatives","text":"Implied from the OWF Charter
The TAC is responsible for ... appointing up to two \"at large\" representatives to the TAC.
The TAC voting members (as defined by the charter) can appoint up to two \"at large\" representatives to the TAC. The election process for \"at large\" representatives will occur on a yearly basis. Members of the community can nominate themselves for the position. Alternatively, a TAC voting member can nominate a member of the community; however, the nominee must actively affirm their candidacy. Electing \"at large\" representatives will be completed through the voting process outlined below. If the \"at large\" representative must leave their position during their term or is otherwise unable to fulfill their duties, they should submit a resignation. \"At large\" vacancies will be handled using the process outlined below.
"},{"location":"governance/elections/#voting-process","title":"Voting Process","text":""},{"location":"governance/elections/#voting-tool","title":"Voting Tool","text":"Voting occurs by a time-limited Helios Voting ballot.
"},{"location":"governance/elections/#voting-schedule","title":"Voting Schedule","text":"The following is the default timeline for voting. The times can be adjusted to avoid weekends and holidays, but it is essential that the final schedule be published in advance and adhered to.
- Call for nominations: Noon PT, E-16 days
- End of call for nominations: Noon PT, E-9 days
- A ballot will be distributed on: E-7 days
- The election will be completed on: Noon PT, E-day and election results are announced
Nominations
Nominees should outline their qualifications and provide a statement explaining why they would be a good choice for the seat.
"},{"location":"governance/elections/#vacancies","title":"Vacancies","text":""},{"location":"governance/elections/#tac-chair-vacancy","title":"TAC Chair Vacancy","text":"Should the TAC Chair seat become vacant, the vacancy will be filled by the vice chair who will serve the remainder of the original term.
"},{"location":"governance/elections/#tac-vice-chair-vacancy","title":"TAC Vice Chair Vacancy","text":"Should the TAC Vice Chair seat become vacant, the vacancy will be filled by using the voting process outlined above and the replacement will serve the remainder of the original term.
"},{"location":"governance/elections/#tac-at-large-representative-vacancy","title":"TAC \"At Large\" Representative Vacancy","text":"Should a TAC \"at large\" representative seat become vacant, the vacancy will be filled at the next indicative election, by electing a person for a full new term, not by serving out the vacant term.
Why?
A TAC \"at large\" vacancy is not filled immediately because the charter does not specify a lower limit for TAC \"at large\" representatives; it only specifies an upper limit.
"},{"location":"governance/elections/#tac-premier-sponsor-representative-vacancy","title":"TAC Premier Sponsor Representative Vacancy","text":"Should a TAC premier sponsor representative seat become vacant, the premier sponsor will immediately appoint a new representative.
"},{"location":"governance/elections/#tac-project-representative-vacancy","title":"TAC Project Representative Vacancy","text":"Should a TAC Project representative seat become vacant, the technical oversight body (e.g., a technical steering committee) for the TAC project will immediately appoint a new representative.
"},{"location":"governance/maintainer-inactivity/","title":"Maintainer Inactivity Policy","text":"Note
This policy applies to projects that do not have an explicit maintainer inactivity policy. Where a project has an established and functioning policy, only that project's policy will apply.
OpenWallet Foundation very much appreciates the contributions of all maintainers but removing write privileges is in the interest of an orderly and secure project.
Activity can be code contributions, code reviews, issue reporting, or any other such activity trackable by GitHub attributed to a OpenWallet Foundation repository.
When a maintainer has not had any activity in a particular project for three months they will receive a notification informing them of the inactivity policies. The means and manner of notification (email, github mentions, etc.) will be at the discretion of the TAC Chair or who the TAC Chair designates.
When a maintainer has not had any activity in a particular project for six months a proposal will be opened up to move the maintainer from active status to emeritus status. A member of the TAC or a OpenWallet Foundation staff member will open this proposal. Any permissions to approve pull requests or commit code and any other such privileges associated with maintainer status will be removed.
The proposal will be in the form of a pull request (PR) to the relevant project repositories updating their maintainer lists. The inactive maintainer will be notified of this via an \"at\" @ mention in the PR. The PR will be open for at least one week to allow time for the project and maintainer to comment.
Inactive maintainers who express an intent to continue contributing may request a three-month extension. This request shall be made in the pull request updating their active maintainer status. Typically, only one such extension will be granted.
Maintainers who have been moved to emeritus status may return to active status when their activity within the project resumes and the current maintainers of the project approve their reactivation.
An OpenWallet Foundation Foundation staff member will provide a report (or maintain an automated means to generate a report) of the most recent GitHub tracked actions for contributors at regular intervals to the TAC. It will be the TAC's responsibility to act on the data.
"},{"location":"governance/maintainer-inactivity/#credits","title":"Credits","text":"This document is based on the Hyperledger Foundation's Inactivity policy
"},{"location":"governance/maintainers-file-content/","title":"MAINTAINERS.md File Contents","text":"All OpenWallet Foundation projects MUST have a MAINTAINERS file (MAINTAINERS.md or MAINTAINERS.rst) at the top-level directory of the source code. This document will provide specifics on what to include in the MAINTAINERS file.
"},{"location":"governance/maintainers-file-content/#list-of-project-maintainers","title":"List of Project Maintainers","text":"The first thing that MUST be included in the MAINTAINERS file is a list of the project's maintainers, both active and emeritus.
It is recommended that the lists be sorted alphabetically and contain the maintainers name, GitHub ID, LFID, Chat ID, Email, Company Affiliation, and Scope.
Important
- The email for a maintainer MUST be specified and be a reliable mechanism to contact the maintainer.
- Scope is dependent on the project and may not exist for a given project. Scope could be the whole project, a specific repository, specific directories in a repository, or high-level description of responsibility (e.g., Documentation).
The following shows the suggested format for the information:
Example
Active Maintainers
Maintainer GitHub ID LFID Email Chat ID Company Affiliation Scope Emeritus Maintainers
Maintainer GitHub ID LFID Email Chat ID Company Affiliation Scope"},{"location":"governance/maintainers-file-content/#what-does-being-a-maintainer-entail","title":"What Does Being a Maintainer Entail","text":"The MAINTAINERS file SHOULD contain information about the different types of maintainers that exist (whole project, repo, part of repo) and what their duties are (e.g., maintainers calls, quarterly reports, code reviews, issue cleansing).
"},{"location":"governance/maintainers-file-content/#how-to-become-a-maintainer","title":"How to Become a Maintainer","text":"The MAINTAINERS file SHOULD contain information about how to become a maintainer for the project. This section SHOULD list specific information about what is required. Information that SHOULD be included in this section:
- What is required before someone can be considered to become a maintainer
- Consider whether there should be different requirements based on the scope (whole project, repo, part of repo) of maintainership
- Whether sponsorship by an existing maintainer is required
- How maintainers are proposed to the community. A number of open source projects require that a PR be done against the
MAINTAINERS file to make this proposal - How many maintainers must approve the proposed maintainer. This should include information about what happens if someone vetoes the proposal
- How long the existing maintainers have to respond to the proposal
"},{"location":"governance/maintainers-file-content/#how-maintainers-are-removed-or-moved-to-emeritus-status","title":"How Maintainers are Removed or Moved to Emeritus Status","text":"The MAINTAINERS file SHOULD contain information about how a maintainer is removed from the list of active maintainers. Information that SHOULD be included in this section:
- What are the reasons a maintainer would be removed from the list of active maintainers
- How this is proposed; similar to the way in which maintainers are added, one way to do this is via a PR against the
MAINTAINERS file - How an emeritus maintainer becomes active again
"},{"location":"governance/maintainers-file-content/#credits","title":"Credits","text":"This document is based on the Hyperledger Foundation's MAINTAINERS guideline.
"},{"location":"governance/paid-tooling-policy/","title":"Paid Tooling Policy","text":"OpenWallet Foundation (OWF) provides a number of paid developer tools for projects. Below, we list the ones that our projects currently have access to and are supported by the OWF staff. We emphasize that just because a tool is not on this list does not mean projects cannot use it; it just means that the project maintainers may have to support it themselves and may need to pay for the tooling. The Governing Board has final say over the budget for tooling and its support.
OWF recommends the following tools that should be optimal for most projects:
-
Technical Documentation: markdown, GitHub pages, and Material for MkDocs.
-
Informal documentation and details (e.g. meeting notes, meeting agendas, long-term planning documentation, etc.): GitHub
-
CI: GitHub Actions
-
Artifact Storage: GitHub Packages
-
Communication: Discord
-
Bug Tracking: GitHub Issues and GitHub Projects
-
Mailing Lists: Groups.io
-
Meetings: Zoom via LFX Meetings
Finally we emphasize that this list does not cover security-related tools or services.
"},{"location":"governance/project-and-lab-services/","title":"Project and Lab Services","text":"This document provides details about what resources are available for OpenWallet Foundation projects and labs. If there are any questions about anything on the document or if you'd like to leverage any of these resources for your project or lab, feel free to reach out to community-architects at openwallet dot foundation.
Service Lab Growth Project Impact Project Infrastructure Github repos Yes Yes Yes Chat channel Yes Yes Yes Mailing list Optional Yes Yes Paid tooling Yes (with some restrictions at the discretion of OpenWallet Foundation staff) Yes Yes Marketing Access to OpenWallet Foundation's channels (social, newsletters, blogs, meetups, etc) Yes (with some restrictions at the discretion of the Marketing lead) Yes Yes Page on the OpenWallet Foundation site Yes Yes Creation of an official project name and logo Yes Yes Coordinate promotion of major project milestones and releases Yes Yes Option to create a Twitter account Yes Yes Priority placement on site Yes Swag (stickers and potentially other items with the project logo) Yes Onboarding New Users and Contributors Able to take part in OpenWallet Foundation's annual Mentorship program TBD TBD TBD Able to have project/lab featured in a contribution campaign Yes (at the discretion of OpenWallet Foundation staff) TBD TBD Workshops Yes Documentation and Translation support TBD TBD TBD Training/Certification LF created training course Yes (at the discretion of LF Training) Yes (at the discretion of LF Training) LF created certification Yes (at the discretion of LF Training) Other License scanning Yes Yes Security audits Not usually (although this can be done at the discretion of staff) Yes (at the discretion of OpenWallet Foundation staff)"},{"location":"governance/project-annual-review-process/","title":"Project Annual Review Process","text":""},{"location":"governance/project-annual-review-process/#overview","title":"Overview","text":"The TAC will undertake an annual review of all OpenWallet Foundation projects. This annual review will include an assessment as to whether:
- each Lab is active
- each Growth Stage project is making adequate progress towards the Impact Stage
- each Impact Stage project is maintaining progress to remain at the Impact Stage
Reviews will start on the yearly anniversary of the project being accepted or moving to a new stage. The review will include a set of recommendations for each project to improve and/or recommendation to move a project across stages.
Projects can be provided with an extension of time in their current stage (up to the discretion of the TAC).
The project lifecycle contains Acceptance Criteria for moving a project to a new stage.
"},{"location":"governance/project-annual-review-process/#filing-an-annual-review","title":"Filing an Annual Review","text":"OpenWallet Foundation staff will notify the project maintainers when the project review is due.
Project maintainers are responsible for agreeing between them who will complete the annual review. One of the maintainers should create the review in GitHub under openwallet-foundation/tac/docs/projects/reviews.
- Raise a PR titled [Project name] [year] Annual Review (e.g., Amazing Project 2024 Annual Review)
- The PR should include a file called
<year>-<project name>-annual.md (e.g., 2024-amazingproj-annual.md) with the contents described below - Send an email to the TAC mailing list so that the community knows the PR is there and can comment on it
If your annual review is not submitted within two months of notification, we will take this as a sign that the project is not under active maintenance and the TAC is likely to decide to archive the project and move it to Emeritus status.
Success
If a project has genuinely stalled we can save everyone\u2019s time and effort by archiving it.
"},{"location":"governance/project-annual-review-process/#annual-review-contents","title":"Annual Review Contents","text":"Your annual review should answer the following questions:
- Include information about your project's contributions and activity. We will be looking for signs of consistent or increasing contribution activity. Please feel free to add commentary to add colour to the numbers and graphs we will see on Insights.
- How many maintainers do you have, and which organisations are they from? (Feel free to link to an existing MAINTAINERS file if appropriate.)
- What do you know about adoption, and how has this changed since your last review or since being accepted into OWF? If you can list companies that are adopters of your project, please do so. (Feel free to link to an existing ADOPTERS file if appropriate.
- How has the project performed against its goals since the last review? (We won't penalize you if your goals changed for good reasons.)
- What are the current goals of the project? For example, are you working on major new features? Or are you concentrating on adoption or documentation?
- How can the OpenWallet Foundation help you achieve your upcoming goals?
- Do you think that your project meets the criteria for another stage (see Project Lifecycle Acceptance Criteria for the different stages)?
A template has been provided for your use.
"},{"location":"governance/project-annual-review-process/#annual-review-by-the-tac","title":"Annual Review by the TAC","text":"Annual reviews are performed in order to check in with projects, ascertain their progress, and address any outstanding questions.
- A TAC representative volunteers to lead the review once the project files a PR.
- The assigned TAC member reviews the content of the PR and analyzes the project for community health indicators, their findings are placed within a thread in the private TAC channel for discussion.
- findings should highlight important facts about the project that could influence the TACs decision around the future of the project, its current stage, and path to other stages, etc.
- the thread should always include whether the project's view of themselves is accurate and the ask of the TAC is reasonable to assist the project moving forward.
- The project's maintainers are invited to the public TAC meeting to engage in TAC led discussion around the project. Project maintainers are not obligated to attend.
- The assigned TAC member provides a summary of the project and leverages the thread's content as the basis of discussion.
- discussion typically focuses on what is going well with the project and areas to improve.
- The project's maintainers are invited to use this time to voice any concerns and requests for help they may have that are not captured in the PR (or highlight asks within the PR).
- At the conclusion of the public meeting, the TAC votes to approve the annual review. Should a concern be registered on a project, the vote will be held separately.
- After the meeting wraps up, the assigned TAC member may summarize the discussion on the PR in the form of a comment to document information for the project and community.
"},{"location":"governance/project-annual-review-process/#review-outcomes","title":"Review Outcomes","text":"The outcome of the annual review is either:
- At least two-thirds of the TAC members agree to continue to sponsor the project at its current stage, or
-
If enough TAC members do not agree to continue to sponsor the project at its current stage, we will discuss with you what stage might be the appropriate next stage, including Emeritus stage.
Info
If the TAC members recommend moving to a new stage, additional work may be required to provide details on how the project meets the new stage's acceptance criteria.
"},{"location":"governance/project-annual-review-process/#credits","title":"Credits","text":"Ideas were taken from CNCF's Sandbox Annual Review Process.
"},{"location":"governance/project-lifecycle/","title":"Project Lifecycle","text":""},{"location":"governance/project-lifecycle/#overview","title":"Overview","text":"This governance policy describes how an open source project can formally join the OpenWallet Foundation via the Project Proposal Process and how an existing project within the OpenWallet Foundation can move through the lifecycle via the Project Stage Change Proposal Process. It describes the Stages a project may be admitted under and what the criteria and expectations are for a given stage, as well as the acceptance criteria for a project to move from one stage to another. It also describes the Annual Review Process through which those changes will be evaluated and made.
Project progression - movement from one stage to another - allows projects to participate at the level that is most appropriate for them given where they are in their lifecycle. Regardless of stage, all OpenWallet Foundation projects benefit from a deepened alignment with existing projects, and access to mentorship, support, and Foundation resources.
Info
Capitalized terms not otherwise defined in this Project Lifecycle Policy have the meanings ascribed to them in the Charter of the OpenWallet Foundation.
"},{"location":"governance/project-lifecycle/#project-proposal-process","title":"Project Proposal Process","text":""},{"location":"governance/project-lifecycle/#introduction","title":"Introduction","text":"This governance policy sets forth the proposal process for projects to be accepted into the OpenWallet Foundation. The process is the same for both existing projects which seek to move into the OpenWallet Foundation and new projects to be formed within the OpenWallet Foundation.
"},{"location":"governance/project-lifecycle/#project-proposal-requirements","title":"Project Proposal Requirements","text":"Projects must be formally proposed via GitHub. Project proposals submitted to the OpenWallet Foundation should provide the following information to the best of their ability:
- name of project
- preferred maturity level (see stages below)
- project description (what it does, why it is valuable, origin and history)
- statement on alignment with the OpenWallet Foundation mission
- link to current Code of Conduct (if one is adopted already)
- sponsor from the TAC, if identified (a sponsor helps mentor projects)
- project license (OSI-approved permissive open source licenses, Apache 2.0 by default)
- source control (OpenWallet Foundation GitHub by default)
- issue tracker (OpenWallet Foundation GitHub by default)
- external dependencies (including licenses)
- release methodology and mechanics
- names of initial maintainers, if different from those submitting proposal
- existing financial sponsorship (if exists)
- infrastructure needs or requests (OpenWallet Foundation provides a set of services for projects and labs. Please note which of these you will utilize and what else is required)
"},{"location":"governance/project-lifecycle/#project-acceptance-process","title":"Project Acceptance Process","text":" - Impact stage and Growth stage projects are required to present their proposal at a TAC meeting. Labs will be reviewed and approved directly via the project proposal PR. Labs may present at a TAC meeting if they would like to gain visibility from other community members, and the proposer should note this in the proposal.
-
The TAC may ask for changes to bring the project into better alignment with the OpenWallet Foundation (adding a governance document to a repository or adopting a Code of Conduct, for example).
Warning
The project will need to make these changes in order to progress further.
-
Impact stage and Growth stage projects are accepted via a two-thirds supermajority vote of the TAC. Labs are accepted via a simple majority of the TAC.
- Satisfaction of the requirements of the initial stage of the project. The TAC will determine the appropriate initial stage for the project. The project can apply for a different stage via the review process.
- If the project is accepted by the TAC, a project charter and contribution agreement (if necessary) can be obtained by completing this form. Here is sample project charter that you can review. A collaboration agreement is needed for existing projects and provides an agreement to transfer the project name, trademarks, and electronic account assets (github repo, social media accounts, domain names, etc.) to Linux Foundation Europe for the benefit of the OpenWallet Foundation.
"},{"location":"governance/project-lifecycle/#project-stage-change-proposal-process","title":"Project Stage Change Proposal Process","text":""},{"location":"governance/project-lifecycle/#introduction_1","title":"Introduction","text":"This governance policy sets forth the proposal process for projects within the OpenWallet Foundation that are seeking to move to another stage in the project lifecycle.
"},{"location":"governance/project-lifecycle/#proposal-process","title":"Proposal Process","text":"The project's current proposal located in Project Proposals GitHub Repository must be updated via a PR. The project proposal should be updated to reflect the latest template, as well as any updates to the sections to reflect why the project should be considered for a new stage.
"},{"location":"governance/project-lifecycle/#project-stage-change-acceptance-process","title":"Project Stage Change Acceptance Process","text":"The same acceptance project outlined above will be used for projects wishing to change lifecycle stage.
"},{"location":"governance/project-lifecycle/#stages","title":"Stages","text":"Every OpenWallet Foundation project has an associated maturity level. Proposed projects should state their preferred maturity level.
All projects may attend TAC meetings and contribute work regardless of their stage.
flowchart\n p[Proposal]\n subgraph as[Active Stages]\n l[Labs]\n g[Growth]\n i[Impact]\n end\n subgraph is[Inactive Stages]\n e[Emeritus]\n end\n p --> as\n l <--> g\n l <--> i\n g <--> i\n as --> is
"},{"location":"governance/project-lifecycle/#labs","title":"Labs","text":"Definition
Labs are those which the TAC believes are, or have the potential to be, important to the ecosystem of Technical Projects or the open wallet ecosystem as a whole. They may be early-stage code just getting started, or they may be long-established projects with minimal resource needs. The Labs stage provides a beneficial, neutral home for these projects in order to foster collaborative development and provide a path to deeper alignment with other OpenWallet Foundation projects via the project lifecycle process.
Examples
- Experimental code that is designed to extend one or more OpenWallet Foundation projects with functionality or interoperability libraries.
- Independent code that fits within the Foundation's mission and provides potential to meet an unfulfilled need.
- Code commissioned or sanctioned by the OpenWallet Foundation.
- Any code that intends to join the Growth or later stages in the future and wishes to lay the foundation for that transition.
Expectations
End users should evaluate Labs with care, as this stage does not set requirements for community size, governance, or production readiness. Labs will receive minimal support from the Foundation. Labs will be reviewed on an annual basis; they may also request a status review by submitting a report to the TAC.
Acceptance Criteria
To be considered for the Labs Stage, the project must meet the following requirements:
- Submit a project proposal.
Upon acceptance, Labs must list their status prominently on their website/README (e.g., PROJECT, an OpenWallet Foundation Lab).
"},{"location":"governance/project-lifecycle/#growth-stage","title":"Growth Stage","text":"Definition
The Growth Stage is for projects that are interested in reaching the Impact Stage, and have identified a growth plan for doing so. Growth Stage projects will receive mentorship from the TAC and are expected to actively develop their community of contributors, governance, project documentation, roadmap, and other variables identified in the growth plan that factor into broad success and adoption.
In order to support their active development, projects in the Growth stage have a higher level of access to Foundation resources, which will be agreed upon and reviewed on a yearly basis. A project's progress toward its growth plan goals will be reviewed on a yearly basis, and the TAC may ask the project to move to the Labs stage if progress on the plan drops off or stalls.
Examples
- Projects that are on their way or very likely to become Growth or Impact projects.
- Projects that have developed new growth targets or other community metrics for success.
- Projects that are looking to create a lifecycle plan (maintainership succession, contributor programs, version planning, etc.).
- Projects that need more active support from the Foundation or TAC mentorship in order to reach their goals.
Expectations
Projects in the Growth stage are generally expected to move out of the Growth stage within two years. Depending on their growth plans, projects may cycle through Labs, Growth, or Impact stage as needed.
Acceptance Criteria
To be considered for Growth Stage, the project must meet the Labs requirements as well as the following:
- A presentation at the meeting of the TAC.
- 2 TAC sponsors to champion the project and provide mentorship as needed.
- Development of a growth plan, to be done in conjunction with their project mentor(s) at the TAC.
- Development of a project roadmap that provides differentiated features and capabilities and the timeframe for completion.
- Document that it is being used successfully in either proof of concepts or pilots by at least two independent end users which, in the TAC\u2019s judgment, are of adequate quality and scope.
- Demonstrate a substantial ongoing flow of commits and merged contributions.
- Demonstrate that the current level of community participation is sufficient to meet the goals outlined in the growth plan and roadmap.
- Since these metrics can vary significantly depending on the type, scope and size of a project, the TAC has final judgment over the level of activity that is adequate to meet these criteria.
- Demonstrates how this project differs from existing projects in the Growth and Impact stages.
- Receive a two-thirds supermajority vote of the TAC to move to Growth Stage.
Upon acceptance, Growth projects must list their status prominently on their website/README (e.g., PROJECT, an OpenWallet Foundation Project).
"},{"location":"governance/project-lifecycle/#impact-stage","title":"Impact Stage","text":"Definition
The Impact Stage is for projects that have reached their growth goals and are now on a sustaining cycle of development, maintenance, and long-term support. Impact Stage projects are used commonly in enterprise production environments and have large, well-established project communities.
Examples
- Projects that have publicly documented release cycles and plans for Long Term Support (\"LTS\").
- Projects that have themselves become platforms for other projects.
- Projects that are able to attract a healthy number of committers on the basis of its production usefulness (not simply 'developer popularity').
- Projects that have several, high-profile or well known end-user implementations.
Expectations
Impact Stage projects are expected to participate actively in TAC proceedings, and as such have a binding vote on TAC matters requiring a formal vote, such as the election of a TAC representative. They receive ongoing financial and marketing support from the Foundation, and are expected to cross promote the Foundation along with their activities.
Acceptance Criteria
To move from Labs or Growth status, or for a new project to join as an Impact project, a project must meet the Growth stage criteria plus:
- Have a defined governing body of at least 5 or more members (owners and core maintainers), of which no more than one-third is affiliated with the same employer. In the case there are 5 governing members, 2 may be from the same employer.
- Have a documented and publicly accessible description of the project's governance, decision-making, and release processes.
- Have a healthy number of maintainers from at least two organizations. A maintainer is defined as someone with the commit bit; i.e., someone who can accept contributions to some or all of the project.
- Have a Code of Conduct in a form acceptable to the OpenWallet Foundation.
- Explicitly define a project governance and maintainer process. This is preferably laid out in a
GOVERNANCE.md file and references a CONTRIBUTING.md and MAINTAINERS.md file showing the current and emeritus maintainers (see MAINTAINERS.md File Contents for more information). - Document that it is being used successfully in production by at least two independent end users which, in the TAC\u2019s judgment, are of adequate quality and scope.
- Have a public list of project adopters for at least the primary repo (e.g.,
ADOPTERS.md or logos on the project website). - Have a good standing with respect to security.
- Other metrics as defined by the applying Project during the application process in cooperation with the TAC.
- Receive a supermajority vote from the TAC to move to Impact stage. Projects can move directly from Labs to Impact, if they can demonstrate sufficient maturity and have met all requirements.
Upon acceptance, Impact projects must list their status prominently on their website/README (e.g., PROJECT, an OpenWallet Foundation Project).
"},{"location":"governance/project-lifecycle/#emeritus-stage","title":"Emeritus Stage","text":"Definition
Emeritus projects are projects which the maintainers feel have reached or are nearing end-of-life. Emeritus projects have contributed to the ecosystem, but are not necessarily recommended for modern development as there may be more actively maintained choices. The Foundation appreciates the contributions of these projects and their communities, and the role they have played in moving the ecosystem forward.
Examples
- Projects that are \"complete\" by the maintainers' standards.
- Projects that do not plan to release major versions in the future.
Expectations
Projects in this stage are not in active development. Their maintainers may infrequently monitor their repositories, and may only push updates to address security issues, if at all. Emeritus projects should clearly state their status and what any user or contributor should expect in terms of response or support. If there is an alternative project the maintainers recommend, it should be listed as well. The Foundation will continue to hold the IP and any trademarks and domains, but the project does not draw on Foundation resources.
Acceptance Criteria
Projects may be granted Emeritus status via a two-thirds vote from the TAC and with approval from project ownership. In cases where there is a lack of project ownership, only a two-thirds vote from the TAC is required.
Upon acceptance, Emeritus projects must list their status prominently on their website/README.
Info
If members of the community would like to re-active a project that has been granted Emeritus status, the community must start the lifecycle over again by submitting a new proposal to the TAC.
"},{"location":"governance/project-lifecycle/#annual-review-process","title":"Annual Review Process","text":"Each project will undergo an annual review process to determine whether projects are in the stage that accurately reflects their needs and goals.
"},{"location":"governance/release-taxonomy/","title":"Release Taxonomy","text":"Note
This policy is not about exiting project stages.
Releases at OpenWallet Foundation must be done according to the SemVer taxonomy. In addition to the semantic versioning scheme, where we use MAJOR.MINOR.PATCH numbering, following the established guidance given in the semver specification, it is also strongly encouraged that projects should use the following tags, as permitted by semver:
- preview
- alpha
- beta
- rcN (release candidate N - where N is 1-n incremented for each candidate)
-
snapshot-<sha> for interim, possible unstable builds
Note
Further, for interim, possibly unstable builds working towards a tagged release, we will append the first seven (7) characters of the SHA-1 hash of the latest commit for the branch from which the build is produced, so that we can identify the commit level of a given test, etc. e.g. 0.6-snapshot-36e99cd
"},{"location":"governance/release-taxonomy/#preview","title":"preview","text":"Not feature complete, but most functionality is implemented. Any missing functionality that is committed to the production release is identified, and there are specific people working on those features. Not heavily performance tuned, but performance testing has started with the first few hotspots identified and perhaps even addressed. No highest priority issues are in an open state. First-level developer documentation provided to help new developers with the learning curve.
"},{"location":"governance/release-taxonomy/#alpha","title":"alpha","text":"Feature complete, for all features committed to the production release. Ready for Proof of Concept-level deployments. Performance can be characterized in a predictable way, so that basic PoC's can be done within the bounds of published expectations. APIs are documented. First attempts at end-user documentation have been made. Developer documentation is further advanced. No highest priority issues are in an open state.
"},{"location":"governance/release-taxonomy/#beta","title":"beta","text":"Feature complete for all features committed to the production release, perhaps with optional features when safe to add. Ready for Pilot-level engagements. Performance is very well characterized and active optimizations are being done, with a target set for the Production release. No highest priority or high priority bugs are in an open state. Developer documentation is complete; end-user documentation is mostly done.
"},{"location":"governance/release-taxonomy/#rcn","title":"rcN","text":"For a forthcoming production release, we will prepare multiple candidate releases intended to be heavily tested by the community. As we cycle through resolving uncovered issues, we will issue another when no remaining highest or high priority issues remain, and repeat until we feel confident in releasing a production release, with no qualifier. e.g. 1.0.
"},{"location":"governance/release-taxonomy/#credits","title":"Credits","text":"This document is based on the Hyperledger Foundation's Release Taxonomy policy.
"},{"location":"governance/roles-and-responsibilities/","title":"Roles and Responsibilities","text":""},{"location":"governance/roles-and-responsibilities/#technical-advisory-council","title":"Technical Advisory Council","text":"The OpenWallet Foundation charter states that the TAC is responsible for:
Quote
- maintaining an overall strategic vision for technical collaboration and coordinating collaboration among Technical Projects, including development of an overall technical vision for the community;
- making recommendations to the Budget Committee of resource priorities for Technical Projects;
- electing annually a chairperson to preside over meetings, set the agenda for meetings, ensure meeting minutes are taken and who will also serve on the Governing Board as the TAC\u2019s representative (the \u201cTAC Representative\u201d);
- creating, maintaining and amending project lifecycle procedures and processes, deciding where Technical Projects fall within that lifecycle;
- determining when a technical project should be admitted as a Technical Project or any Technical Project should be considered a TAC Project; and
- such other matters related to the technical role of the TAC as may be communicated to the TAC by the Governing Board.
"},{"location":"governance/roles-and-responsibilities/#tac-members","title":"TAC Members","text":"TAC members are expected to:
- Subscribe to the TAC mailing list and the OpenWallet Github organization to stay aware of the TAC related updates and issues
- Regularly participate in the TAC meetings
- Bring up and help resolve any issues related to the needs of the OpenWallet technical community
- Participate in, and optionally chair, the Task Forces set up by the TAC to address specific issues
- Act as stewards for OpenWallet Foundation promoting and helping grow the organization and its activities by engaging of their own accord in activities such as posting on social media, responding to questions raised in forums, helping new community members find their way around, and giving talks at conferences on OpenWallet Foundation related topics
- Participate in the appointment and election of \"at large\" representatives
"},{"location":"governance/roles-and-responsibilities/#tac-chair","title":"TAC Chair","text":"The TAC chair has the following additional responsibilities:
- Running the TAC meetings, such as the TAC calls per the agreed upon schedule. This includes: setting up and publishing an agenda, running the meeting, and ensuring any outcome is duly recorded
- Representing the TAC, and more broadly the OpenWallet Foundation technical community, on the Governing Board, and giving updates to the Governing Board on TAC activities
"},{"location":"governance/roles-and-responsibilities/#tac-vice-chair","title":"TAC Vice Chair","text":"The TAC vice chair has the following additional responsibilities:
- Running the TAC meetings when the TAC Chair is unable, including setting up and publishing an agenda and ensuring any outcome is duly recorded
- Helping to marshall people who want to talk during a meeting
"},{"location":"governance/security-template/","title":"PROJECT Security Policy","text":""},{"location":"governance/security-template/#instructions","title":"Instructions","text":"The following is the best practices template security vulnerability disclosure policy for OpenWallet Foundation's projects. Please copy the text below, place it into the SECURITY.md file for the primary repository of your project, and adjust it as necessary for your project. Notably:
- Remove this \"Instructions\" section.
- Replace PROJECT in the title of this page with the name of your project.
- Populate the Security Team section with maintainers who have agreed to be on the security team.
- See the \"Alternative\" notes in the OpenWallet Foundation's security vulnerability disclosure policy document for how the \"best practices\" in this document can be changed to meet the needs of your project while still adhering to the OpenWallet Foundation's policies.
Once your project's security vulnerability disclosure policy document is published, place a copy of it into each of your project's repositories (or link to the main repository's SECURITY.md).
"},{"location":"governance/security-template/#about-this-document","title":"About this Document","text":"This document document defines how security vulnerability reporting is handled in this project. The approach aligns with the OpenWallet Foundation's security vulnerability disclosure policy. Please review that document to understand the basis of the security reporting for this project
This policy borrows heavily from the recommendations of the OpenSSF Vulnerability Disclosure working group. For up-to-date information on the latest recommendations related to vulnerability disclosures, please visit the GitHub of that working group.
If you are already familiar with what a security vulnerability disclosure policy is and are ready to report a vulnerability, please jump to Report Intakes.
"},{"location":"governance/security-template/#what-is-a-vulnerability-disclosure-policy","title":"What Is a Vulnerability Disclosure Policy?","text":"No piece of software is perfect. All software (at least, all software of a certain size and complexity) has bugs. In open source development, members of the community or the public find bugs and report them to the project. A vulnerability disclosure policy explains how this process functions from the perspective of the project.
This vulnerability disclosure policy explains the rules and guidelines for this project. It is intended to act as both a reference for outsiders\u2013including both bug reporters and those looking for information on the project\u2019s security practices\u2013as well as a set of rules that maintainers and contributors have agreed to follow.
"},{"location":"governance/security-template/#report-intakes","title":"Report Intakes","text":"This project uses the following mechanism to submit security vulnerabilities. While the security team members will do their best to respond to bugs disclosed in all possible ways, it is encouraged for bug finders to report through the following approved channel:
- Open a GitHub security vulnerability report: Open a draft security advisory on the \"Security\" tab of this GitHub repository. See GitHub Security Advisories to learn more about the security infrastructure in GitHub.
"},{"location":"governance/security-template/#security-team","title":"Security Team","text":"The current security team is:
Name Email ID Chat ID Area/Specialty <> <> <> <> <> <> <> <> <> <> <> <> The security team for this project must include at least three project Maintainers that agree to carry out the following duties and responsibilities. Members are added and removed from the team via approved Pull Requests to this repository. For additional background into the role of the security team, see the People Infrastructure section of the OpenWallet Foundation's security vulnerability disclosure policy.
Responsibilities:
-
Acknowledge receipt of the issue (see Report Intakes) to the reporter within 2 business days.
-
Assess the issue. Engage with the reporter to ask any outstanding questions about the report and how to reproduce it. If the report is not considered a vulnerability, then the reporter should be informed and this process can be halted. If the report is still a regular bug (just not a security vulnerability), the reporter should be informed (if necessary) of the regular process for reporting bugs.
-
Some issues may require more time and resources to correct. If a particular report is more complex, discuss an embargo period with the reporter. The embargo period should be negotiated with the reporter and must not be longer than 90 days.
-
Create a patch for the issue (see Private Patch Deployment Infrastructure).
-
Request a CVE for the issue (see CNA/CVE Reporting).
-
Decide the date of public release.
-
If applicable, notify members of the embargo list of the upcoming patch and release, as described above.
-
Cut a new (software) release in which the bug is fixed.
-
Publicly disclose the issue within 48 hours after the release (see GitHub Security Advisories).
"},{"location":"governance/security-template/#discussion-forum","title":"Discussion Forum","text":"Discussions about each reported vulnerability are carried out in the private GitHub security advisory about the vulnerability. If necessary, a private channel specific to the issue may be created on the OpenWallet Foundation's Discord server with invited participants added to the discussion.
"},{"location":"governance/security-template/#cnacve-reporting","title":"CNA/CVE Reporting","text":"This project maintains a list of Common Vulnerabilities and Exposures (CVE) and uses GitHub as its CVE numbering authority (CNA) for issuing CVEs.
"},{"location":"governance/security-template/#embargo-list","title":"Embargo List","text":"This project maintains a private embargo list. If you wish to be added to the embargo list for a project, please email the [OpenWallet Foundation's security list], including the project name and reason for being added to the embargo list. Requests will be assessed by the security team in conjunction with the appropriate OpenWallet Foundation staff, and a decision will be made whether to accommodate the request.
"},{"location":"governance/security-template/#github-security-advisories","title":"GitHub Security Advisories","text":"This project uses GitHub security advisories and the GitHub security process for handling security vulnerabilities.
"},{"location":"governance/security-template/#private-patch-deployment-infrastructure","title":"Private Patch Deployment Infrastructure","text":"In creating patches and new releases that address security vulnerabilities, this project uses the private development features of GitHub for security vulnerabilities. GitHub has extensive documentation about these features.
"},{"location":"governance/security/","title":"Security Vulnerability Disclosure Policy","text":"This document outlines the OpenWallet Foundation's security vulnerability disclosure policy that all OpenWallet Foundation projects MUST follow. The associated security template file is a \"best practices\" security vulnerability disclosure policy that project Maintainers SHOULD use for publishing the security policy and procedures for their project by copying the file into their project repositories and updating it according to the instructions in the document. This document includes the \"best practices\" text, and defines how project Maintainers can use alternatives to the best practices for their project. A project's resulting alternative policy MUST adhere to the OpenWallet Foundation's security vulnerability disclosure policy.
All project repositories MUST have a published security vulnerability disclosure policy or have link to a common policy document for the project. In rare cases, a repository within a project MAY have a policy different from the project, as long as the repository policy also adheres to this OpenWallet Foundation's security vulnerability disclosure policy.
"},{"location":"governance/security/#about-this-document","title":"About This Document","text":"This policy borrows heavily from the recommendations of the OpenSSF Vulnerability Disclosure working group. For up-to-date information on the latest recommendations related to vulnerability disclosures, please visit the GitHub of that working group.
In each of the document's sections, and in the associated security template, the current OpenWallet Foundation's \"best practices\" are defined.
Alternative
Alternatives that a project may use exist for some sections and are contained in these \"Alternative boxes\". When projects vary from the current OpenWallet Foundation's best practices, the documented alternatives MUST adhere to this policy.
"},{"location":"governance/security/#what-is-a-vulnerability-disclosure-policy","title":"What Is a Vulnerability Disclosure Policy?","text":"No piece of software is perfect. All software (at least, all software of a certain size and complexity) has bugs. In open source development, members of the community or the public find bugs and report them to the project. A vulnerability disclosure policy explains how this process functions from the perspective of the project.
This vulnerability disclosure policy explains the rules and guidelines for OpenWallet Foundation's projects. It is intended to act as both a reference for outsiders\u2013including both bug reporters and those looking for information on the project\u2019s security practices\u2013as well as a set of rules that maintainers and contributors have agreed to follow.
"},{"location":"governance/security/#vulnerability-disclosure-process-and-associated-rules","title":"Vulnerability Disclosure Process and Associated Rules","text":"All OpenWallet Foundation's projects, including this project, follow the associated process and rules for vulnerability disclosures. We note that this outline is derived from the OpenSSF maintainers guide.
Each project will have a security team. The security team will be comprised of maintainers or contributors to the project who are knowledgeable about security and is responsible for responding to and helping to fix security vulnerabilities.
The security team for this project will do the following for each reported vulnerability:
-
Acknowledge receipt of the issue (see Report Intakes) to the reporter within 2 business days.
-
Assess the issue. Engage with the reporter to ask any outstanding questions about the report and how to reproduce it. If the report is not considered a vulnerability, then the reporter should be informed and this process can be halted. If the report is still a regular bug (just not a security vulnerability), the reporter should be informed (if necessary) of the regular process for reporting bugs.
-
Some issues may require more time and resources to correct. If a particular report is more complex, discuss an embargo period with the reporter. The embargo period should be negotiated with the reporter and must not be longer than 90 days.
-
Create a patch for the issue (see Private Patch Deployment Infrastructure).
-
Request a CVE for the issue (see CNA/CVE Reporting).
-
Decide the date of public release.
-
If applicable, notify members of the embargo list of the upcoming patch and release, as described above.
-
Cut a new (software) release in which the bug is fixed.
-
Publicly disclose the issue within 48 hours after the release (see GitHub Security Advisories).
"},{"location":"governance/security/#report-intakes","title":"Report Intakes","text":"OpenWallet Foundation's projects use the following mechanism to submit security vulnerabilities. While the security team members will do their best to respond to bugs disclosed in all possible ways, it is encouraged for bug finders to report through the following approved channel:
- Open a GitHub security vulnerability report: Open a draft security advisory on the \"Security\" tab of this GitHub repository. See GitHub Security Advisories to learn more about the security infrastructure in GitHub.
Alternative Projects MAY publish in their security policy that they accept security vulnerability disclosures via other mechanism. The policy MUST document the necessary details in using the alternate reporting mechanism(s). Projects MUST accept reports via the recommended GitHub security vulnerability process.
"},{"location":"governance/security/#people-infrastructure","title":"\u201cPeople\u201d Infrastructure","text":"This section details the required basic vulnerability disclosure infrastructure for all OpenWallet Foundation's projects. There are quite a few necessary pieces of infrastructure, and we go through them in detail here.
"},{"location":"governance/security/#security-team","title":"Security Team","text":"Projects MUST have a security response team of at least three maintainers. This response team shall be set up BEFORE incidents happen so that people know who to contact and how to contact them when an emergency issue arises. It can be difficult to track down someone with unique knowledge (e.g. in a particular area of cryptography) who is capable of fixing a problem in a short period of time.
-
Each security team member will be a member of any OpenWallet Foundation-wide security infrastructure.
-
If a project has specialized code related to certain aspects of security or cryptography (e.g. consensus algorithms or cryptographic algorithms), then a corresponding specialist should be on the response team (e.g. someone knowledgeable in consensus or cryptography, respectively). If a specialist is not on the team, then the individual who is responsible for contacting or engaging the specialists should be designated in their stead. We emphasize that projects should have access to specialists in an area for which they maintain code while recognizing that it may not be practical for these experts to be on the response team.
Each project/repository must have a table in the security document listing the team members in the following format.
Name Email ID Chat ID Area/Specialty <> <> <> <> <> <> <> <> <> <> <> <>"},{"location":"governance/security/#discussion-forum","title":"Discussion Forum","text":"Discussions about each reported vulnerability SHOULD be carried out in the private GitHub security advisory about the vulnerability. If necessary, a private channel specific to the issue MAY be created on the OpenWallet Foundation's Discord server with invited participants added to the discussion.
Alternative Projects MAY document on their security policy that they use other forums for private discussion forums for approved maintainers and security team participants to discuss vulnerabilities. If other forum(s) are used, details about them MUST be included.
"},{"location":"governance/security/#cnacve-reporting","title":"CNA/CVE Reporting","text":"OpenWallet Foundation's projects maintain a list of Common Vulnerabilities and Exposures (CVE) and use GitHub as its CVE numbering authority (CNA) for issuing CVEs.
Alternative A project MAY document in its security policy that it uses a different CVE numbering authority. For example, the project might add the following text to this section of their security policy document:
This project uses the following CNA(s) in the following situations:\n1. `CNA_1`: `situation_1, can just state \u201cdefault\u201d if only one CNA`\n2. `CNA_2`: `situation_2`\n
"},{"location":"governance/security/#embargo-list","title":"Embargo List","text":"An embargo list is a list of known, trusted entities that run large deployments of a given OpenWallet Foundation's project. These entities are notified ahead of time when important security patches are incoming to minimize potential security risks to large deployments of projects. Embargo lists are maintained by the security team for a given project/repository.
Parties are on an embargo list for (usually) one of two reasons, because they can either help fix the problem (perhaps through testing a fix at scale) or they need extra time to help prepare their ecosystem to roll out fixes quickly. Approval is not given lightly: project leadership (maintainers) must be convinced that institutions on the list \u201cneed to know\" about issues in advance.
Participation in an embargo list should not be taken lightly. List members are expected to respect the materials shared through it and not disclose any information to unauthorized parties until the public disclosure date. Institutions are on this list because their presence helps the project and its users; if their actions do not help the project and its users, they can expect to be removed from the list.
The list itself is private in order to make it slightly more difficult for attackers with vulnerabilities to find systems to attack. Entities may be added to the embargo list by a majority vote of the project security response team and should request to join the embargo list by contacting one or more of the members of the security response team. If there is an issue about embargo list membership where an entity feels like they are being dealt with unfairly by the security response team, then they are encouraged to bring up the issue in front of the OpenWallet Foundation's TAC, who can act as moderators.
OpenWallet Foundation's projects maintain private embargo lists. If you wish to be added to the embargo list for a project, please email the [OpenWallet Foundation's security list], including the project name and reason for being added to the embargo list. Requests will be assessed by the respective OpenWallet Foundation's security team in conjunction with the appropriate OpenWallet Foundation staff, and a decision will be made to accommodate or not the request.
Alternative Projects MAY choose to document in their security document that they do not have an embargo list. The reason for not having an embargo list SHOULD be included when a project chooses not to have an embargo list.
"},{"location":"governance/security/#github-security-advisories","title":"GitHub Security Advisories","text":"OpenWallet Foundation's projects use GitHub security advisories and the GitHub security process for handling security vulnerabilities. In particular, this best practice is strongly recommended for projects that do not have a large number of security experts as the features serve as a nice set of guardrails to help make sure that things are done correctly.
Alternative Projects MAY document in their security policy document that they use a security advisory mechanism other than GitHub to publish their disclosures. The alternate mechanism MUST be documented sufficiently for users to understand how to monitor the security advisories published by the project.
"},{"location":"governance/security/#private-patch-deployment-infrastructure","title":"Private Patch Deployment Infrastructure","text":"Patches to fix OpenWallet Foundation's project security vulnerabilities are typically developed without public visibility by using the private development features of GitHub. Projects with maintainers that are not familiar with these capabilities are encouraged to contact the OpenWallet Foundation Community Architects to learn more.
Alternative Projects MAY document in their security policy document that they do use a service other than GitHub for private patch deployment infrastructure, or that they don't use any private patch deployment infrastructure at all. In either case, the document MUST include the details of what is used instead.
"},{"location":"governance/special-interest-group-process/","title":"Special Interest Group","text":"A special interest group (SIG) under the Technical Advisory Council (TAC) is a group with a shared interest in advancing a specific area of knowledge, learning, or technology related to the mission of the OpenWallet Foundation where members cooperate to affect or to produce solutions within their particular field. Unlike a task force, SIGs are typically long running and may or may not produce any deliverables. A SIG can be created by anyone in the OpenWallet Foundation community and must be proposed to and approved by the TAC.
"},{"location":"governance/special-interest-group-process/#propose-a-special-interest-group","title":"Propose a Special Interest Group","text":"To propose a special interest group, create an issue in the TAC GitHub repository using the Special Interest Group template. The issue should be named \"Special Interest Group Proposal: \\<name of special interest group>\". The issue should include the following information:
- Introduction/background material
- Objectives of the special interest group
- List of deliverables or work products (optional)
- Leader(s)
- Initial participant list
"},{"location":"governance/special-interest-group-process/#approval-process","title":"Approval Process","text":"The TAC will review the special interest group proposal first by providing comments in the issue and secondly by bringing the special interest group proposal to a discussion and vote in a TAC meeting.
The decision of the vote will be documented in the issue. If the special interest group is approved, a discussion channel in Discord will be created. In addition, we will work with the OpenWallet Foundation operations team to schedule a meeting on the OpenWallet Foundation calendar. If necessary, a GitHub repository and/or mailing list will also be created at the request of the special interest group leader(s).
"},{"location":"governance/special-interest-group-process/#special-interest-group-procedures","title":"Special Interest Group Procedures","text":"The special interest group can decide on the mechanism for running the SIG. Meeting minutes and a log of decisions that have been made should be kept for ensuring continuity of the special interest group. The special interest group should update the issue to reflect where the meeting notes and log of decisions is kept or use the issue directly to capture this information.
"},{"location":"governance/special-interest-group-process/#reporting-on-special-interest-group-activities","title":"Reporting on Special Interest Group Activities","text":"Every quarter the special interest group leader should report on the activities of the SIG at a TAC meeting. This will ensure that the SIG is still active and that there is still value in hosting the special interest group. Please see the schedule for when these updates should occur.
"},{"location":"governance/tac/","title":"OpenWallet Foundation TAC composition","text":""},{"location":"governance/tac/#current-composition","title":"Current Composition","text":"Member (alphabetical by first name) Representing David Zeuthen Google Jaehoon (Ace) Shim At Large Pete Cooling Visa Rolson Quadras Gen Stavros Kounis (vice chair) At Large Stephen Curran Impact (ACA-Py) Tracy Kuhrt (chair) Accenture Wenjing Chu FutureWei Technologies"},{"location":"governance/tac/#history","title":"History","text":""},{"location":"governance/tac/#2023-03-08","title":"2023-03-08","text":" - Tracy Kuhrt is running unopposed for TAC Chair
- Composition
- Accenture - Tracy Kuhrt
- Futurewei - Wenjing Chu
- Gen Digital - Drummond Reed
- Visa - Marie Austenaa
"},{"location":"governance/tac/#2023-04-05","title":"2023-04-05","text":" - TAC \"at large\" election results
- Jeremie Miller
- Stavros Kounis
"},{"location":"governance/tac/#2023-06-28","title":"2023-06-28","text":" - Pete Cooling was introduced as Visa's TAC voting representative.
"},{"location":"governance/tac/#2023-08-09","title":"2023-08-09","text":" - RESOLVED: That Stavros Kounis is hereby confirmed and approved as the TAC Vice Chair
"},{"location":"governance/tac/#2023-09-06","title":"2023-09-06","text":" - We welcomed David Zeuthen, Google premier member representative
"},{"location":"governance/tac/#2023-10-18","title":"2023-10-18","text":" - Mike Varley will represent Gen Digital moving forward.
"},{"location":"governance/tac/#2024-04-03","title":"2024-04-03","text":" - TAC \"at large\" election results
"},{"location":"governance/tac/#2024-04-17","title":"2024-04-17","text":" - Chair/Vice Chair Results
- Stavros, vice chair
- Tracy, chair
"},{"location":"governance/tac/#2024-05-15","title":"2024-05-15","text":" - Rolson Quadras will represent Gen Digital moving forward
"},{"location":"governance/tac/#2024-10-02","title":"2024-10-02","text":" - Stephen Curran was welcomed as the ACA-Py project representative
"},{"location":"governance/task-force-process/","title":"Task Force","text":"A task force is a group that is focused on a task with limited scope and fixed time to complete. Unlike a special interest group, a task force will have a specific set of deliverables or work products that it will create and be limited in time to completion. A task force can be created by anyone in the OpenWallet Foundation community and must be proposed to and approved by the TAC.
"},{"location":"governance/task-force-process/#propose-a-task-force","title":"Propose a Task Force","text":"To propose a task force, create an issue in the TAC GitHub repository. The issue should be named \"Task Force Proposal: \\<name of task force>\". The issue should include the following information:
- Introduction/background material
- Objectives of the task force
- List of deliverables or work products
- Time to complete (no more than 6 months)
- Leader(s)
- Initial participant list
"},{"location":"governance/task-force-process/#approval-process","title":"Approval Process","text":"The TAC will review the task force proposal first by providing comments in the issue and secondly by bringing the task force proposal to a discussion and vote in a TAC meeting.
The decision of the vote will be documented in the issue. If the task force is approved, a discussion channel in Discord will be created. In addition, we will work with the OpenWallet Foundation operations team to schedule a meeting on the OpenWallet Foundation calendar. If necessary, a GitHub repository and/or mailing list will also be created at the request of the task force leader(s).
"},{"location":"governance/task-force-process/#task-force-procedures","title":"Task Force Procedures","text":"The task force can decide on the mechanism for creating the deliverables. Meeting minutes and a log of decisions that have been made should be kept for ensuring continuity of the task force. The task force should update the issue to reflect where the meeting notes and log of decisions is kept or use the issue directly to capture this information.
"},{"location":"governance/task-force-process/#reporting-on-task-force-completion-of-deliverables","title":"Reporting on Task Force Completion of Deliverables","text":"Upon completion of the task force's deliverables, the task force should arrange a time with the TAC chair to present the deliverables at a TAC meeting. This can be accomplished by sending an email to the TAC mailing list at tac@lists.openwallet.foundation.
"},{"location":"governance/task-force-process/#requesting-an-extension-on-completion-date","title":"Requesting an Extension on Completion Date","text":"If the task force is not able to complete the deliverables by the specified completion date, then the leader of the task force should arrange a time with the TAC chair to discuss the extension at a TAC meeting. This discussion should include information on the current status, the delays, and the expected updates to the schedule. This can be accomplished by sending an email to the TAC mailing list at tac@lists.openwallet.foundation.
"},{"location":"meetings/","title":"TAC Meetings","text":"TAC meetings are intended to be open to observe by Sponsors, contributors to any TAC Project, and others in the general public interested in the OpenWallet Foundation.
The meetings will be held bi-weekly starting Wednesday, March 8, 2023 at 7:00am PT.
- Join link with meeting ID and passcode embedded: https://zoom-lfx.platform.linuxfoundation.org/meeting/94569749258?password=68170ae3-3074-45fb-9b2e-4c479ed7d8d7
"},{"location":"meetings/YYYY-mm-dd/","title":"YYYY-mm-dd","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/YYYY-mm-dd/#agenda","title":"Agenda","text":" - Include agenda items here.
"},{"location":"meetings/YYYY-mm-dd/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Mike Varley
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/YYYY-mm-dd/#notes","title":"Notes","text":" - Include discussion notes here.
"},{"location":"meetings/YYYY-mm-dd/#recording","title":"Recording","text":""},{"location":"meetings/2023/2023-03-08/","title":"2023-03-08","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-03-08/#agenda","title":"Agenda","text":" - Welcome and intros of TAC
- Reminder of TAC Charter
- TAC Chair election
- TAC \"at large\" seats
- Call for code from the Community
- Open Discussion and Next Steps
"},{"location":"meetings/2023/2023-03-08/#recording","title":"Recording","text":""},{"location":"meetings/2023/2023-03-08/#actions","title":"Actions","text":" - Tracy Kuhrt is running unopposed for TAC Chair. Can the 4 TAC Representatives please +1 this to formalize.
- Review proposed TAC Website and Governance Policies as detailed at https://lists.openwallet.foundation/g/TAC/message/3
- Review https://github.com/openwallet-foundation/project-proposals
"},{"location":"meetings/2023/2023-03-08/#minutes","title":"Minutes","text":" - TAC Charter
- The TAC is responsible for maintaining an overall strategic vision for technical collaboration and coordinating collaboration among Technical Projects, including development of an overall technical vision for the community.
- Section 5 of https://cdn.platform.linuxfoundation.org/agreements/openwalletfoundation.pdf
- TAC Chair Election
- Tracy Kuhrt is running unopposed \u2013 will move to email vote to formalize
- Composition
- Accenture - Tracy Kuhrt
- Futurewei - Wenjing Chu
- Gen Digital - Drummond Reed
- Visa - Marie Austenaa
- \u201cat large\u201d representative #1 appointed by vote of the TAC
- \u201cat large\u201d representative #2 appointed by vote of the TAC
- one representative appointed by the technical oversight body (e.g., a technical steering committee) of each TAC Project
- Call for Code
- Please review https://github.com/openwallet-foundation/project-proposals
- Governance rules
- Tracy gave an overview of a proposed website and policies for the TAC at https://github.com/openwallet-foundation/tac
- Open Discussion
- The Governing Board met yesterday and appointed Daniel Goldscheider as Interim Executive Director. Daniel introduced himself and provided his thoughts on the future of OWF.
- A suggestion was made for a landscape review. A comment was made that that work has begun here.
"},{"location":"meetings/2023/2023-03-22/","title":"2023-03-22","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-03-22/#agenda","title":"Agenda","text":" - Review and approve TAC Governance documents
- TAC \"at large\" elections
- Call for code from the Community
- Open Discussion and Next Steps
"},{"location":"meetings/2023/2023-03-22/#links","title":"Links","text":""},{"location":"meetings/2023/2023-03-22/#action-items","title":"Action Items","text":" - Conduct an email vote for the Governance documents approval and adoption.
- Conduct an email vote for the TAC \"at large\" schedule and process.
- Todd to confirm whether the TAC can create an alternate policy or whether the Governing Board will need to update the charter to reflect.
- Tracy to create a pull request to update the project proposal template to include links to the mission and project lifecycle.
- Create a GitHub organization (openwallet-foundation-labs) to host incoming labs.
"},{"location":"meetings/2023/2023-03-22/#minutes","title":"Minutes","text":" - No comments on the TAC Governance documents. Will conduct an email vote to adopt.
- Discussed TAC \"at large\" election process. Will conduct an email vote to adopt.
- Reviewed project proposal process and instructions and went through the template. Two suggested changes:
- Include a link to the mission.
- Include a link to the project lifecycle for stage information.
- Next steps
- Create a labs organization (openwallet-foundation-labs) to host any lab proposals.
"},{"location":"meetings/2023/2023-04-05/","title":"2023-04-05","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-04-05/#agenda","title":"Agenda","text":" - Review action items from last meeting
- TAC \"at large\" election results
- Architecture SIG update
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-04-05/#links","title":"Links","text":""},{"location":"meetings/2023/2023-04-05/#action-items","title":"Action Items","text":" - Tracy to rename the architecture-task-force GitHub repo to architecture-sig - completed
- Jenn to rename the meeting invite for the Outside Architecture Special Interest Group to reflect that the name should be the Architecture SIG
- Jenn to add Stavros to the TAC meeting invite - completed
- Jenn to add Jeremie to the TAC meeting invite
- Create a GitHub organization (openwallet-foundation-labs) to host incoming labs
"},{"location":"meetings/2023/2023-04-05/#meeting-minutes","title":"Meeting Minutes","text":" - Review action items from last meeting
- Conduct an email vote for the Governance documents approval and adoption - results 3 TAC members voted in favor; 1 TAC member abstained
- Conduct an email vote for the TAC \"at large\" schedule and process - results 3 TAC members voted in favor; 1 TAC member abstained
- Todd to confirm whether the TAC can create an alternate policy or whether the Governing Board will need to update the charter to reflect - currently no policy for TAC alternates; if we want this, we would need to present this to the GB to get a charter update
- The TAC would like to recommend that the board create an alternate policy for the TAC.
- The language will be similar to the following \"A TAC member can designate an alternate for a specific meeting, and has to notify the chair in advance.\"
- Tracy to create a pull request to update the project proposal template to include links to the mission and project lifecycle - pull request created and merged
- Create a GitHub organization (openwallet-foundation-labs) to host incoming labs - not yet completed
- TAC \"at large\" election results
- Jeremie Miller
- Stavros Kounis
- Architecture SIG update
- Digital wallet engine architecture topics brainstorm - please add any topics that you think we missed
- Discussion on MOST important architecture topic - please add to the discussion
- A question was brought up about the status of this group and whether it is a task force or a special interest group. The TAC formalized the group as a special interest group under the TAC.
- Call for code from the community
- Next steps
- Discussion regarding the upcoming conference season, including IIW, EIC, and others.
- Suggestion was made to create an OpenWallet Foundation event calendar.
- Next meeting is April 19, 2023.
"},{"location":"meetings/2023/2023-04-19/","title":"2023-04-19","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-04-19/#agenda","title":"Agenda","text":" - Review action items from last meeting
- Priorities
- Internet Identity Workshop (IIW) updates
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-04-19/#links","title":"Links","text":""},{"location":"meetings/2023/2023-04-19/#action-items","title":"Action Items","text":" - Document process for creating a task force - pull request
"},{"location":"meetings/2023/2023-04-19/#meeting-minutes","title":"Meeting Minutes","text":" - Review action items from last meeting
- Tracy to rename the architecture-task-force GitHub repo to architecture-sig - completed
- Jenn to rename the meeting invite for the Outside Architecture Special Interest Group to reflect that the name should be the Architecture SIG - completed
- Jenn to add Stavros to the TAC meeting invite - completed
- Jenn to add Jeremie to the TAC meeting invite - completed
- Create a GitHub organization (openwallet-foundation-labs) to host incoming labs - completed
- Priorities
- Projects
- Pipeline of projects
- Getting a method of tracking and accessing projects
- Rule book / guide on the evaluation process and criteria for new projects
- Technical Focus
- Cloud based, edge based, and hybrid wallets
- Common components for wallets
- Specific components for money, identity, and object wallets
- Collaboration between OWF and European Commission
- Tracking changes in the next European Digital Identity Wallet Architecture and Reference Framework (ARF) and making sure it lines up with OWF thinking
- Maintaining dialog and exploring alignment
- Internet Identity Workshop (IIW) updates
- Topics on digital wallets, credentials, and interoperability
- Sessions on EUDI and the ARF
- A number of OpenWallet topics will be discussed on day 2 and 3
- Discussions about the Linux Foundation Trust umbrella
- Call for code from the community
- Completing the assessment framework may allow people to better understand what type of projects should be considered for contribution
- Next steps
- Next meeting is May 3, 2023
"},{"location":"meetings/2023/2023-05-03/","title":"2023-05-03","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-05-03/#agenda","title":"Agenda","text":" - Review action items from last meeting
- Welcome new TAC member
- Task Force Proposal
- Assessment Framework - How do we want to assess incoming projects?
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-05-03/#links","title":"Links","text":""},{"location":"meetings/2023/2023-05-03/#action-items","title":"Action Items","text":" - Update Task Force process to include information on optional mailing lists and capturing meeting notes -- commit -- completed
- Create process for Special Interest Groups similar to Task Force process and cross link the two processes together
"},{"location":"meetings/2023/2023-05-03/#meeting-minutes","title":"Meeting Minutes","text":""},{"location":"meetings/2023/2023-05-17/","title":"2023-05-17","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-05-17/#agenda","title":"Agenda","text":" - Review action items from last meeting
- New lab proposals
- SD-JWT Kotlin
- SD-JWT Python
- Special Interest Group process proposal
- OID4VCI and OID4VP Due Diligence Task Force
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-05-17/#links","title":"Links","text":""},{"location":"meetings/2023/2023-05-17/#tac-voting-members","title":"TAC Voting Members","text":" - Jeremie Miller
- Marie Austenaa (Trevor Crooks attended and voted in Marie's place)
- Stavros Kounis
- Tracy Kuhrt
- Troy Ronda
- Wenjing Chu
"},{"location":"meetings/2023/2023-05-17/#action-items","title":"Action Items","text":" - Work with Fabian to transfer SD-JWT Kotlin repo to openwallet-foundation-labs organization
- Work with Daniel to transfer SD-JWT Python repo to openwallet-foundation-labs organization
- Comment on OID4VCI and OID4VP Due Diligence Task Force proposal and update to reflect comments. We will bring this to a vote at the next TAC meeting
"},{"location":"meetings/2023/2023-05-17/#meeting-minutes","title":"Meeting Minutes","text":" -
Review action items from last meeting
- Update Task Force process to include information on optional mailing lists and capturing meeting notes -- commit -- completed
- Create process for Special Interest Groups similar to Task Force process and cross link the two processes together -- PR -- completed
-
New lab proposals
- SD-JWT Kotlin Library
- RESOLVED: That the SD-JWT Kotlin Library lab is hereby confirmed, approved, and adopted.
- Unanimously approved by the present TAC voting members.
- SD-JWT Python Reference Implementation
- RESOLVED: That the SD-JWT Python Reference Implementation lab is hereby confirmed, approved, and adopted.
- Unanimously approved by the present TAC voting members.
-
Special Interest Group process proposal
- RESOLVED: That the special interest group (SIG) process documented in this pull request and rendered on this page and using this issue template is hereby confirmed, approved, and adopted.
- Unanimously approved by the present TAC voting members.
-
OID4VCI and OID4VP Due Diligence Task Force
- Support exists for this task force, but we ran out of time to conclude the discussion.
- Request for comments on OID4VCI and OID4VP Due Diligence Task Force proposal and +1 if you are interested in participating.
- Hakan will update to reflect comments so that we can bring this to a vote at the next TAC meeting.
-
Call for code from the community
-
Next steps
- Next meeting is May 31, 2023
"},{"location":"meetings/2023/2023-05-31/","title":"2023-05-31","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-05-31/#agenda","title":"Agenda","text":" - Review action items from last meeting
- Update on TAC alternates
- OID4VC Due Diligence Task Force
- Credential Format Comparison SIG
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-05-31/#links","title":"Links","text":""},{"location":"meetings/2023/2023-05-31/#tac-voting-members","title":"TAC Voting Members","text":" - Jeremie Miller
- Marie Austenaa
- Stavros Kounis
- Tracy Kuhrt
- Troy Ronda
- Wenjing Chu
"},{"location":"meetings/2023/2023-05-31/#action-items","title":"Action Items","text":""},{"location":"meetings/2023/2023-05-31/#meeting-minutes","title":"Meeting Minutes","text":" -
Review action items from last meeting
- Work with Fabian to transfer SD-JWT Kotlin repo to openwallet-foundation-labs organization -- completed SD-JWT-Kotlin
- Work with Daniel to transfer SD-JWT Python repo to openwallet-foundation-labs organization -- in progress
- Comment on OID4VC Due Diligence Task Force proposal and update to reflect comments -- in progress
-
Update on TAC alternates
-
The Governing Board agreed to modify the Charter to include the following language:
Updated Language
5.c) TAC meetings are intended to be open to observe by Sponsors, contributors to any TAC Project and others in the general public interested in the OpenWallet Foundation. The TAC may decide whether to allow named representatives (one per voting member) to attend as an alternate.
-
OID4VC Due Diligence Task Force
- Unanimously approved by the present TAC voting members.
-
Credential Format Comparison SIG
- Unanimously approved by the present TAC voting members.
-
Call for code from the community
-
Next steps
- Next meeting is June 14, 2023
"},{"location":"meetings/2023/2023-06-14/","title":"2023-06-14","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-06-14/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- TAC alternates policy
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-06-14/#links","title":"Links","text":""},{"location":"meetings/2023/2023-06-14/#tac-voting-members","title":"TAC Voting Members","text":" - Jeremie Miller
- Marie Austenaa
- Stavros Kounis
- Tracy Kuhrt
- Troy Ronda
- Wenjing Chu
"},{"location":"meetings/2023/2023-06-14/#action-items","title":"Action Items","text":""},{"location":"meetings/2023/2023-06-14/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- OID4VC Due Diligence Task Force kickoff meeting \u2013 Wednesday, the 21st at 5pm CEST
- Architecture SIG merged Key Management Services conceptual architecture
- Credential Format Comparison SIG will meet on Wednesdays at 5pm CEST on alternate weeks to the OID4VC Due Diligence Task Force. Kickoff meeting planned for June 28th
-
Review action items from last meeting
-
TAC Alternates Policy
- RESOLVED: That the TAC Alternates Policy is hereby confirmed, approved, and adopted.
- Unanimously approved by the present TAC voting members.
-
Call for code from the community
- A question was asked whether we were tracking a wishlist for potential projects
- In general, we are looking for projects that fit with the vision of the OpenWallet Foundation. Those that are focused on wallet engine related to identity, money, and objects
- We previously were capturing potential code projects using this Google sheet
- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Open discussion and next steps
- Relative to the Credential Format Comparison SIG, the ToIP Foundation has just started a task force on the same thing for credential exchange protocols. See this spreadsheet
- David Alexander will present on wallets and personal data stores at the next meeting and we will discuss further
- Background blog post
- Thread from Architecture SIG on personal data
- There\u2019s also the Decentralized Web Node project that Block is leading at the Decentralized Identity Foundation
- Next meeting is June 28, 2023
"},{"location":"meetings/2023/2023-06-28/","title":"2023-06-28","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-06-28/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Vice chair seat and responsibilities
- Wallets and personal data stores presentation and discussion
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-06-28/#links","title":"Links","text":""},{"location":"meetings/2023/2023-06-28/#tac-voting-members","title":"TAC Voting Members","text":" - Jeremie Miller
- Marie Austenaa
- Stavros Kounis
- Tracy Kuhrt
- Troy Ronda
- Wenjing Chu
"},{"location":"meetings/2023/2023-06-28/#action-items","title":"Action Items","text":" - Work with Daniel to transfer SD-JWT Python repo to openwallet-foundation-labs organization -- in progress
- Credential Format Comparison SIG: Work with Torsten to get GitHub repo transferred to OpenWallet Foundation -- in progress
- Review Farmworker Wallet OS project proposal - all
"},{"location":"meetings/2023/2023-06-28/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC. Kickoff meeting planned for July 7th.
- OID4VC Due Diligence task force will meet weekly on Wednesdays at 5pm CEST.
- Pete Cooling was introduced as Visa's TAC voting representative.
-
Review action items from last meeting
- Determine vice chair language -- completed
- Work with Daniel to transfer SD-JWT Python repo to openwallet-foundation-labs organization -- in progress
- Credential Format Comparison SIG: Work with Torsten to get GitHub repo transferred to OpenWallet Foundation -- in progress
-
Vice chair seat and responsibilities
- RESOLVED: That the Vice Chair Seat and Responsibilities is hereby confirmed, approved, and adopted.
- Unanimously approved by the present TAC voting members.
- Voting schedule
- Call for nominations: June 28
- End of call for nominations: July 5, Noon PT
- A ballot will be distributed on: July 5 by end of day PT
- The election will be completed on: July 11, Noon PT
- Election results are announced at the July 12 meeting
- If you would like to submit your nomination for TAC Vice Chair, please create an issue at https://github.com/openwallet-foundation/tac/issues
- Title of issue: [NOMINATION]: 2023 Vice Chair - Name
- Include a short bio, outline your qualifications, and provide a statement explaining why you would be a good choice for the seat
-
Wallets and personal data stores
- Background blog post
- Thread from Architecture SIG on personal data
- Presentation by David Alexander
-
Call for code from the community
- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Open discussion and next steps
- Next meeting is July 12, 2023
"},{"location":"meetings/2023/2023-07-12/","title":"2023-07-12","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-07-12/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Vice Chair
- Farmworker Wallet OS project proposal
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-07-12/#links","title":"Links","text":""},{"location":"meetings/2023/2023-07-12/#tac-voting-members","title":"TAC Voting Members","text":" - Jeremie Miller
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Troy Ronda
- Wenjing Chu
"},{"location":"meetings/2023/2023-07-12/#action-items","title":"Action Items","text":" - Review Farmworker Wallet OS project proposal - all
- Review the proposed license of Farmworker Wallet OS project with LF legal - Jenn
"},{"location":"meetings/2023/2023-07-12/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC
- Data moved from spreadsheet to github.io site
- OID4VC Due Diligence task force will meet weekly on Wednesdays at 5pm CEST
- Architecture SIG meets weekly on Mondays at 11am US/Pacific
- Invitation to fully remote ISO/IEC JTC 1/SC 17 18013-7 Interoperability Event
- For Associate non-profit members of the OpenWallet Foundation: voting is now open to select the Associate Representative for the Governing Board. Please email operations@openwallet.foundation if you have any questions about your organization's participation in this vote.
-
Review action items from last meeting
- Work with Daniel to transfer SD-JWT Python repo to openwallet-foundation-labs organization -- in progress
- Credential Format Comparison SIG: Work with Torsten to get GitHub repo transferred to OpenWallet Foundation -- completed (new repo created)
- Review Farmworker Wallet OS project proposal - all
-
Vice Chair
- RESOLVED: That the voting schedule for vice chair is hereby revised, approved, and adopted as specified.
- Revised voting schedule
- Call for nominations: July 12
- End of call for nominations: August 2, Noon PT
- A ballot will be distributed on: August 2 by end of day PT
- The election will be completed on: August 8, Noon PT
- Election results are announced at the August 9 meeting
- Unanimously approved by the present TAC voting members.
-
Farmworker Wallet OS project proposal
- Video shared on Discord
- Question asking for clarification of the scope of the contribution
- Concerns raised about the licensing terms of the generated output from Mendix
- Mendix does not make any intellectual property claims on the output
- Question raised about the proposed license that will need to be run past LF legal and the Governing Board
- Need to consider naming of the repos to ensure that it allows people to determine that they are part of the same project
- Question raised about the difference between the Aries SDK proposed to be part of this project and the one in Hyperledger
- The one in this project is a wrapper around the SDK in Hyperledger that can be used by Mendix developers
- Continue conversation on the pull request
-
Call for code from the community
- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Open discussion and next steps
- Next meeting is July 26, 2023
"},{"location":"meetings/2023/2023-07-26/","title":"2023-07-26","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-07-26/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Materials for MkDocs Insiders version
- Farmworker Wallet OS project proposal
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-07-26/#links","title":"Links","text":""},{"location":"meetings/2023/2023-07-26/#tac-voting-members","title":"TAC Voting Members","text":" - Jeremie Miller
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Troy Ronda
- Wenjing Chu
"},{"location":"meetings/2023/2023-07-26/#action-items","title":"Action Items","text":" - Develop list of budget line items needed by the TAC
- Work with Jorge on the item of whether aries-sdk-mendix makes sense within Hyperledger
"},{"location":"meetings/2023/2023-07-26/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC
- OID4VC Due Diligence task force will meet weekly on Wednesdays at 5pm CEST
- Architecture SIG meets weekly on Mondays at 11am US/Pacific
- Vice chair nomination period open until August 2nd. Please submit your nominations
- TAC website now available at https://tac.openwallet.foundation
- OpenWallet Foundation Discord has a custom invite link: https://discord.gg/openwalletfoundation
-
Review action items from last meeting
- Work with Daniel to transfer SD-JWT Python repo to openwallet-foundation-labs organization -- in progress
- Review Farmworker Wallet OS project proposal -- in progress
- Review the proposed license of Farmworker Wallet OS project with LF legal -- completed
-
Materials for MkDocs Insiders version
- RESOLVED: That the TAC recommends to the Governing Board the sponsorship of Material for MkDocs to obtain access to the Insiders Version is hereby confirmed, approved, and adopted.
- Proposed resolution was not voted on. It was suggested that we develop a proposal that would include other tools that the technical community would need to limit the number of requests to the Governing Board.
-
Farmworker Wallet OS project proposal
- Discussion items
- Code of Conduct
- plan to change to use OWF\u2019s CoC
- we may need to consider changing the template since it asks for the current CoC
- License
- change to use Apache 2.0 license
- Project Governance
- no change needed at this point
- Repo names
- Discussion was had to make sure that we are prefixing repo names with the project name to ensure that it is easy for someone to find all repos associated with a single project
- Interoperable roadmap
- No limit on what will be supported
- Hosting Aries-specific stuff at OWF
- TAC considers wrappers of other projects to be better suited to be included with the parent project
- Tracy to work with Jorge on creating a lab proposal for Hyperledger for the Aries-specific wrappers
- Jorge to update proposal to reflect the above recommendation
-
Call for code from the community
- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Open discussion and next steps
- Next meeting is August 9, 2023
"},{"location":"meetings/2023/2023-08-09/","title":"2023-08-09","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-08-09/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Farmworker Wallet OS project proposal
- Budget Request to Governing Board
- Vice Chair
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-08-09/#links","title":"Links","text":""},{"location":"meetings/2023/2023-08-09/#tac-voting-members","title":"TAC Voting Members","text":" - Jeremie Miller
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Troy Ronda
- Wenjing Chu
"},{"location":"meetings/2023/2023-08-09/#action-items","title":"Action Items","text":" - Continue to work on budget line items
- Jorge to update code of conduct on Farmworker Wallet OS proposal -- completed
- Create repositories for the Farmworker Wallet OS Lab
- Share document with governance best practices -- completed
- OWF Project Guidance -- this document assumes a fairly mature project that consists of a technical steering committee and maintainers for the project. Please comment and add your thoughts/suggestions.
- Hyperledger's Project Best Practices
- Comment on OWF Project Guidance - all
"},{"location":"meetings/2023/2023-08-09/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC
- OID4VC Due Diligence task force will meet weekly on Tuesdays at 5pm CEST
- Architecture SIG meets weekly on Mondays at 11am US/Pacific
- sd-jwt-python source is now available
-
Review action items from last meeting
- Work with Daniel to transfer SD-JWT Python repo to openwallet-foundation-labs organization -- completed
- Review Farmworker Wallet OS project proposal -- in progress
- Tracy to work with Jorge on creating a lab proposal for Hyperledger for the Aries-specific wrappers -- completed
- Develop list of budget line items needed by the TAC \u2013 in progress
-
Farmworker Wallet OS project proposal
- RESOLVED: That the Farmworker Wallet OS lab is hereby confirmed, approved, and adopted.
- Unanimously approved by the present TAC voting members.
-
Budget Request to Governing Board
- Thread started on Discord
- Sponsorship of Material for MkDocs to obtain access to the Insiders Version at $125/month to support the TAC website
- Wiki (Confluence or similar)
- License Scanning
- Package Hosting - GitHub? ghcr.io? Is there a package hosting solution for all technologies that exists?
- Playground/Sandbox Hosting
- Others?
-
Vice Chair
- RESOLVED: That Stavros Kounis is hereby confirmed and approved as the TAC Vice Chair
- Approved by the present TAC voting members with Stavros abstaining.
-
Call for code from the community
- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- Question asked about code proposal that depends on Aries/Bifold and whether that could be submitted to OWF?
- If the project is only dependent on Aries/Bifold, then it can be submitted to OWF.
- If, however the project is a wrapper of Aries/Bifold, then that should probably be submitted to Hyperledger.
- Question about project governance best practices and whether we could document these best practices for new projects.
- OWF Project Guidance -- this document assumes a fairly mature project that consists of a technical steering committee and maintainers for the project. Please comment and add your thoughts/suggestions.
- In addition, we can look at Hyperledger's Project Best Practices for additional thoughts on guiding OpenWallet Foundation projects.
-
Open discussion and next steps
- Next meeting is August 23, 2023
"},{"location":"meetings/2023/2023-08-23/","title":"2023-08-23","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-08-23/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Budget Request to Governing Board
- OWF Project Governance Guidance
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-08-23/#links","title":"Links","text":""},{"location":"meetings/2023/2023-08-23/#tac-voting-members","title":"TAC Voting Members","text":" - Jeremie Miller
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Troy Ronda
- Wenjing Chu
"},{"location":"meetings/2023/2023-08-23/#action-items","title":"Action Items","text":" - Review, comment, and add feedback to OWF Project Governance Guidance - all
- Review, comment, and add feedback to VC-API prject proposal - all
- Provide infrastructure costs for the European Interoperability Test Bed - Harm Jan Arendshorst
"},{"location":"meetings/2023/2023-08-23/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC
- OID4VC Due Diligence task force will meet weekly on Tuesdays at 5pm CEST
- Architecture SIG meets weekly on Mondays at 11am US/Pacific
- Farmworker Wallet OS repositories created
- Project pages created for each approved project on the TAC website
- Slide deck available covering the OWF Project Proposal Process
-
Review action items from last meeting
- Continue to work on budget line items -- all
- Jorge to update code of conduct on Farmworker Wallet OS proposal -- completed
- Create repositories for the Farmworker Wallet OS Lab -- completed
- Share document with governance best practices -- completed
- Comment on OWF Project Guidance - all
-
Budget Request to Governing Board
- Sponsorship of Material for MkDocs to obtain access to the Insiders Version at $125/month to support the TAC website
- Wiki
- Options:
- Dokuwiki is currently included in our current LFIT budget
- Confluence would be an additional $800/month
- Continue utilizing GitHub wiki
- Update the TAC website as necessary
- Discussion:
- Confluence is nice to allow for the ability to search across the entire foundation
- Consider the migration costs
- Confluence has a lot of nice features that GitHub wiki and Dokuwiki do not have
- It is easier to bring markdown files into Confluence than to export to markdown
- Most documentation for projects will be captured within projects as markdown files and hosted using something like ReadTheDocs.io or GitHub Pages
- We do not currently have anyone that is asking for Confluence
- If we sponsor Material for Mkdocs insiders version, then all OpenWallet Foundation projects will be able to utilize
- Outcome: We will postpone asking for budget until we have a need
- License Scanning
- Another project within the Linux Foundation cost is $65,000/year
- We should ask for this as it allows us to remain compliant with the open licenses
- Package Hosting - GitHub? ghcr.io? Is there a package hosting solution for all technologies that exists?
- ghcr.io (GitHub Packages) is free for all public GitHub repositories \u2013 recommend we start there
- Support for Package Registries
- The only thing that we have currently that is not supported by GitHub Packages is Python
- Playground/Sandbox Hosting
- We do not yet have a price for this, but following are some of the things that we could see needing a sandbox
- Accessing server-side APIs
- Deployment of server-based reference wallet
- Interop testing
- Reference implementation of data objects that a wallet contain - example VC issuance and verification
- Harm mentioned that he has some information on the infrastructure costs for hosting the European Interoperability Test Bed, which was presented to the architecture SIG on March 27, 2023. Harm will provide information on these costs
- Harm is also interested in bringing the Interoperability Test Bed as a project to the OWF
- DevSecOps
- The Linux Foundation is recommending that projects use GH Actions
- Automated security/code scanning
- SonarQube - Static code analysis
-
OWF Project Governance Guidance
- Request to review, add comments and feedback
- David Alexander recommended that we include information about momentum and duty of care and working across the foundation
- Stavros asked if a TSC is required for projects
- No, a TSC is not mandatory. The idea is that if a project gets big enough where all the maintainers cannot get together easily and make decisions, more governance framework is needed, and this is the way to go in that case.
- As such, we should make sure that this document provides the right level of guidance for projects at different stages in their lifecycle
-
Call for code from the community
- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- Next time we meet, we will be reviewing the VC-API prject proposal
-
Open discussion and next steps
- Next meeting is September 6, 2023
"},{"location":"meetings/2023/2023-09-06/","title":"2023-09-06","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-09-06/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Welcome new TAC member
- VC-API Project Proposal
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-09-06/#links","title":"Links","text":""},{"location":"meetings/2023/2023-09-06/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Troy Ronda
- Wenjing Chu
"},{"location":"meetings/2023/2023-09-06/#action-items","title":"Action Items","text":" - Create recommendation for governing board for licenses that are compatible with Apache 2.0 to be approved -- Tracy
- Update PR to answer questions asked during the meeting -- John
- Determine if Energy Web Foundation is willing to relicense VC-API -- John
"},{"location":"meetings/2023/2023-09-06/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC (next call September 13)
- OID4VC Due Diligence task force will meet bi-weekly on Tuesdays at 5pm CEST (next call September 12)
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call September 11)
-
Review action items from last meeting
- Review, comment, and add feedback to OWF Project Governance Guidance - all
- Review, comment, and add feedback to VC-API prject proposal - all
- Provide infrastructure costs for the European Interoperability Test Bed - Harm Jan Arendshorst
-
Welcome new TAC member
- We welcomed David Zeuthen, Google premier member representative
-
VC-API Project Proposal
- How does this codebase relate to the energywebfoundation/ssi?
- Does this proposal refer to the ssi repository OR only to work under the /vc-api path?
- The intention is to bring over only the /vc-api path. We could consider whether it makes sense to bring over the other application, but it would require a separate proposal.
- Are there dependencies or references to any implementation outside this folder that need attention if it is the latter?
- Refer to the \"Source Control\" section of the proposal for information on what the dependencies are for the VC-API
- Could we prepare a list of all the single repositories the vc-api needs and will be part of this proposal? I would also suggest supplementing this list with the purpose of these additional repos and their relationship/dependencies to vc-api.
- This is captured in the \"Source Control\" section of the proposal.
- For licensing purposes, will we leave related repositories in the organization they currently are? Should we expect a licensing conflict in this case?
- John will follow up on the license with Energy Web Foundation.
- What referenced tutorials and documentation will moved from energywebfoundation GitHub organization to the OWF?
- Yes, we can move the tutorials and documentation into OWF.
- Is this project an implementation of a VC API server or also client/wallet libraries?
- Is this project based on the latest version of the CCG VC API? Does it already implement the full community report?
- It implements the latest published version of the CCG VC API. It may be missing one or two endpoints. I don't think that we have implemented derived presentation.
- Which credential formats and signature formats are supported?
- Those that are supported by SpruceID's DIDKit
- How have you tested interop?
- We have not yet tested interop. The testing that we have done is with the available test suites.
- What will be the prefix for this project?
- We need to determine a way in which projects can be separated if they implement the same specification. Project prefixes are a way to do this and will allow us to trademark them in the future.
- License
- John to follow up with Energy Web Foundation about the possibility or re-licensing
- Develop recommendation for the OWF governing board on licenses that are compatible with Apache 2.0
- Missing DCO on existing repository
-
Call for code from the community
- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Open discussion and next steps
- Next meeting is September 20, 2023
"},{"location":"meetings/2023/2023-09-20/","title":"2023-09-20","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-09-20/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- SIG Proposal - SSI Wallet and Agent Overviews
- SIG Proposal - Anti-Correlation and Anti-Profiling
- VC-API Project Proposal
- Intellectual Property Policy
- Call for code from the community
- Open discussion and next steps
"},{"location":"meetings/2023/2023-09-20/#links","title":"Links","text":""},{"location":"meetings/2023/2023-09-20/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Troy Ronda
- Wenjing Chu
"},{"location":"meetings/2023/2023-09-20/#action-items","title":"Action Items","text":" - Review, comment, and add feedback to the Wallet Framework .NET project proposal - all
- Review, comment, and add feedback to the Intellectual Property Proposal - all
- Digital Wallet and Agent Overview SIG
- Create Discord channel - Tracy
- Add information to the TAC website regarding the SIG - Tracy
- Add link to the above to the OpenWallet Foundation GitHub Profile - Tracy
- Work with Maaike on infrastructure requirements (repo, mailing list) - Tracy/Maaike
- Anti-Correlation and Anti-Profiling SIG
- Create Discord channel - Tracy
- Add information to the TAC website regarding the SIG - Tracy
- Add link to the above to the OpenWallet Foundation GitHub Profile - Tracy
- Work with Andy on infrastructure requirements (repo, mailing list) - Tracy/Andy
- Conduct email vote for VC-API project approval - Tracy - completed
"},{"location":"meetings/2023/2023-09-20/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Credential Format Comparison SIG will meet on Wednesdays at 4pm CEST on alternate weeks to the TAC (next call September 27)
- OID4VC Due Diligence task force will meet bi-weekly on Tuesdays at 5pm CEST (next call September 26)
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call September 25)
- New Project Proposal - Wallet Framework .NET - Please review
- Suggested Future Project - Support the Apple pass format
-
Review action items from last meeting
- Review, comment, and add feedback to OWF Project Governance Guidance by October 4th - all
- Review, comment, and add feedback to VC-API project proposal - all
- Provide infrastructure costs for the European Interoperability Test Bed - Harm Jan Arendshorst
- Create recommendation for governing board for intellectual property policy -- Tracy -- completed
- Update VC-API PR to answer questions asked during the meeting -- John \u2013 completed
- Determine if Energy Web Foundation is willing to relicense VC-API -- John \u2013 completed
-
SIG Proposal - SSI Wallet and Agent Overviews
- RESOLVED: That the SSI Wallet and Agent Overviews special interest group is hereby confirmed, approved, and adopted.
- Unanimously approved by the present TAC voting members
-
SIG Proposal - Anti-Correlation and Anti-Profiling
- RESOLVED: That the Anti-Correlation and Anti-Profiling special interest group is hereby confirmed, approved, and adopted.
- Unanimously approved by the present TAC voting members
-
VC-API Project Proposal
- Discussion
- RESOLVED: That the VC-API lab is hereby confirmed, approved, and adopted.
- Since we did not have enough TAC voting members to meet the \u2154 supermajority vote, we will conduct an email vote.
-
Intellectual Property Policy
- Apache 2.0 for source code
- CC-BY-4.0 for documentation
- Allowed Third Party License Policy
- RESOLVED: That the proposed Intellectual Property Policy will be forwarded to the Governing Board for consideration.
- Please review and provide your feedback
- We will vote on this next time we meet
-
Call for code from the community
- If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Open discussion and next steps
- Next meeting is October 4, 2023
- Discussed whether to move to weekly meetings to support influx of project proposals. It was determined that we could be more efficient on these calls if we commented on the PRs when they are submitted to get questions answered that may delay the vote.
"},{"location":"meetings/2023/2023-10-04/","title":"2023-10-04","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-10-04/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Project Proposal - Wallet Framework .NET
- Project Proposal - Android Identity Library
- Intellectual Property Policy
- Open discussion and next steps
"},{"location":"meetings/2023/2023-10-04/#links","title":"Links","text":""},{"location":"meetings/2023/2023-10-04/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Drummond Reed (alternate for Troy Ronda)
- Wenjing Chu
"},{"location":"meetings/2023/2023-10-04/#action-items","title":"Action Items","text":" - Conduct email vote on the Intellectual Property Policy
- Add project page for the Wallet Framework .NET project
- Work with Sebastian to transfer Wallet Framework .NET project code to OWF
- Review, comment, and add feedback to Android Identity Library project proposal - all
"},{"location":"meetings/2023/2023-10-04/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CEST on alternate weeks to the TAC (next call October 11)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CEST (next call October 24)
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call October 16)
- Please submit any code proposals using the process defined at openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up.
- Pre-IIW Developer Face-to-Face October 9
-
Review action items from last meeting
- Review, comment, and add feedback to OWF Project Governance Guidance - all
- Review, comment, and add feedback to the Intellectual Property Proposal - all
- Review, comment, and add feedback to the Wallet Framework .NET project proposal - all
- Provide infrastructure costs for the European Interoperability Test Bed - Harm Jan Arendshorst
- Digital Wallet and Agent Overviews SIG onboarding - completed
- Anti-Correlation and Anti-Profiling SIG Onboarding - completed
- Conduct email vote for VC-API project approval - Tracy - completed and approved
-
Project Proposal - Wallet Framework .NET
- RESOLVED: That the Wallet Framework .NET proposal is hereby confirmed, approved, and adopted.
- Unanimously approved by the present TAC voting members.
-
Project Proposal - Android Identity Library
- RESOLVED: That the Android Identity Library proposal is hereby confirmed, approved, and adopted.
-
Intellectual Property Policy
- Apache 2.0 for source code
- CC-BY-4.0 for documentation
- Allowed Third Party License Policy
- Open Standards and Specifications
- RESOLVED: That the proposed Intellectual Property Policy will be forwarded to the Governing Board for consideration.
-
Open discussion and next steps
- Discussion regarding conflict of the Safe Wallet SIG with other meetings
- Standing agenda items that we might want to add:
- Socialization of what others in the community are doing
- Project, SIG, Task Force updates
- Next meeting is October 20 2023
"},{"location":"meetings/2023/2023-10-18/","title":"2023-10-18","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-10-18/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Welcome new TAC member (hold for next meeting)
- Legal Discussion - Project Charters
- Project Proposal - Android Identity Library
- Project Proposal: SD-JWT JS
- Open discussion and next steps
"},{"location":"meetings/2023/2023-10-18/#links","title":"Links","text":""},{"location":"meetings/2023/2023-10-18/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Drummond Reed (alternate for Mike Varley)
- Wenjing Chu
"},{"location":"meetings/2023/2023-10-18/#action-items","title":"Action Items","text":" - Update project proposal template to make it easier for people to understand what the TAC is expecting for answers related to each question -- Tracy
- Update project lifecycle to reflect project charters -- Tracy
- Document the desire for OWF to utilize permissive licenses in the project lifecycle -- Tracy
- Review, comment, and add feedback to SD-JWT JS lab proposal -- all
"},{"location":"meetings/2023/2023-10-18/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call October 30)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CEST (next call October 24)
- Safe Wallet SIG meets weekly on Tuesdays at 8am US/Pacific (next call October 24)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CEST on alternate weeks to the TAC (next call October 25)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CEST on alternate weeks to the TAC (next meeting October 26)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up.
-
Review action items from last meeting
- Conduct email vote on the Intellectual Property Policy \u2013 completed
- Add project page for the Wallet Framework .NET project \u2013 completed
- Work with Sebastian to transfer Wallet Framework .NET project code to OWF \u2013 completed
- Review, comment, and add feedback to Android Identity Library project proposal - all
- Provide infrastructure costs for the European Interoperability Test Bed - Harm Jan Arendshorst
-
Welcome New TAC Member
- Mike Varley will represent Gen Digital moving forward.
- Hold for next meeting as Mike could not attend today.
-
Legal Discussion
- Discuss project charters
- Sample charter
- Intake form
- Copyleft vs. Permissive licenses (LF allows any OSI license. The OWF can decide on whether they only want permissive license.)
-
Project Proposal - Android Identity Library
- RESOLVED: That the Android Identity Library proposal is hereby confirmed, approved, and adopted.
-
6* Approve, 1 Abstain (David) - Project accepted
Info (*)
During the meeting, Pete abstained. After the meeting, Pete changed his vote via email from Abstain to Approve.
-
Project Proposal - SD-JWT JS
- RESOLVED: That the SD-JWT JS lab proposal is hereby confirmed, approved, and adopted.
- Some discussion about why a new project is needed instead of utilizing existing typescript implementations.
-
Open discussion and next steps
- David Alexander suggested that the OpenWallet Foundation work closely with MyData.
- Next meeting is November 1, 2023
"},{"location":"meetings/2023/2023-11-01/","title":"2023-11-01","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-11-01/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Welcome new TAC member
- Resolution: SD-JWT JS Project Proposal
- Resolution: SD-JWT Rust Project Proposal
- Resolution: Proposal Process Updates
- Clarify Template Instructions
- Update Process
- Resolution: Project Services and Paid Tooling
- Open discussion and next steps
"},{"location":"meetings/2023/2023-11-01/#links","title":"Links","text":""},{"location":"meetings/2023/2023-11-01/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Mike Varley
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2023/2023-11-01/#action-items","title":"Action Items","text":" - Update \"permissive license\" to \"OSI-approved permissive license\" in the project lifecycle and template PRs
- Update Paid Tooling PR to reflect other requests require the Governing Board approval
- Onboarding SD-JWT JS lab
- Create sd-jwt-js repo in OpenWallet Foundation Labs GitHub
- Create sd-jwt-js Discord channel
- Complete intake form to create project charter
"},{"location":"meetings/2023/2023-11-01/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call November 6)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CEST (next call November 7)
- Safe Wallet SIG meets weekly on Tuesdays at 8am US/Pacific (next call November 7)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CEST on alternate weeks to the TAC (next call November 8)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CEST on the same weeks as the TAC (next meeting November 2)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up.
-
Review action items from last meeting
- Update project proposal template to make it easier for people to understand what the TAC is expecting for answers related to each question -- Tracy -- completed
- Update project lifecycle to reflect project charters -- Tracy -- completed
- Document the desire for OWF to utilize permissive licenses in the project lifecycle -- Tracy -- completed
- Review, comment, and add feedback to SD-JWT JS lab proposal -- all
- Work with John Henderson to transfer VC-API project to OpenWallet Foundation Labs
- Work with David Zeuthen to transfer Android Identity Library project to OpenWallet Foundation Labs
-
Welcome New TAC Member
- Mike Varley will represent Gen Digital moving forward.
-
Resolution: SD-JWT JS Project Proposal
- RESOLVED: That the SD-JWT JS lab proposal is hereby confirmed, approved, and adopted.
- APPROVED with six yea, one absent
-
Resolution: SD-JWT Rust Project Proposal
- RESOLVED: That the SD-JWT Rust lab proposal is hereby confirmed, approved, and adopted.
-
Resolution: Proposal Process Updates
- RESOLVED: That the changes suggested in Clarify Template Instructions and Update Process are hereby confirmed, approved, and adopted.
- APPROVED with six yea, one absent
-
Resolution: Project Services and Paid Tooling
- RESOLVED: That the Project Services and Paid Tooling is hereby confirmed, approved, and adopted.
- APPROVED with six yea, one absent
-
Open discussion and next steps
- Next meeting is November 15, 2023
"},{"location":"meetings/2023/2023-11-15/","title":"2023-11-15","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-11-15/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Task force update: OID4VC Due Diligence
- Resolution: SD-JWT Rust Project Proposal
- Resolution: SD-JWT .NET Project Proposal
- Open discussion and next steps
"},{"location":"meetings/2023/2023-11-15/#links","title":"Links","text":""},{"location":"meetings/2023/2023-11-15/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Mike Varley
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2023/2023-11-15/#action-items","title":"Action Items","text":" - Onboarding SD-JWT Rust lab
- Create sd-jwt-rust repo in OpenWallet Foundation Labs GitHub
- Create sd-jwt-rust Discord channel
- Complete intake form to create project charter -- follow up with LF Legal on status
"},{"location":"meetings/2023/2023-11-15/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call November 27; skipping week of US Thanksgiving)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call November 21)
- Safe Wallet SIG meets weekly on Tuesdays at 8am US/Pacific (next call November 21)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call November 22)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting November 16)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up.
- SIG quarterly updates will begin in January 2024
-
Review action items from last meeting
- Update \"permissive license\" to \"OSI-approved permissive license\" in the project lifecycle and template PRs \u2013 completed and merged (lifecycle PR 69 and template PR 22)
- Update Paid Tooling PR to reflect other requests require the Governing Board approval \u2013 completed and merged
- Onboarding SD-JWT JS lab
- Create sd-jwt-js repo in OpenWallet Foundation Labs GitHub \u2013 completed
- Create sd-jwt-js Discord channel \u2013 completed (#sd-jwt-js)
- Complete intake form to create project charter
- Work with John Henderson to transfer VC-API project to OpenWallet Foundation Labs
- Work with David Zeuthen to transfer Android Identity Library project to OpenWallet Foundation Labs
- Working on name of the project
- David has been working with the downstream dependencies to make them aware of changes that will be coming
-
Task Force Update: OID4VC Due Diligence
- Update Slide Deck
- Discussion about whether this task force should become a SIG
- At this time, we will leave this as a task force
- The task force members will decide on the expanded time that is needed
- At some point in the future, this may become an OID4VC Implementers SIG
-
Resolution: SD-JWT Rust Project Proposal
- RESOLVED: That the SD-JWT Rust lab proposal is hereby confirmed, approved, and adopted.
- Unanimously approved by the present TAC voting members.
-
Resolution: SD-JWT .NET Project Proposal
- RESOLVED: That the SD-JWT .NET lab proposal is hereby confirmed, approved, and adopted.
-
Open discussion and next steps
- Next meeting is November 29, 2023
"},{"location":"meetings/2023/2023-11-29/","title":"2023-11-29","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-11-29/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Resolution: SD-JWT .NET Project Proposal
- Resolution: Agent Framework JavaScript Proposal
- Open discussion and next steps
"},{"location":"meetings/2023/2023-11-29/#links","title":"Links","text":""},{"location":"meetings/2023/2023-11-29/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Mike Varley
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2023/2023-11-29/#action-items","title":"Action Items","text":" - Onboard SD-JWT .NET
- Transfer sd-jwt-dotnet repo to OpenWallet Foundation Labs GitHub
- Create sd-jwt-dotnet Discord channel
- Follow up with LF Legal on project intake form
- Onboard Agent Framework JavaScript
- Transfer repos to OpenWallet Foundation Labs GitHub
- Create agent-framework-js Discord channel
- Follow up with LF Legal on project intake form
"},{"location":"meetings/2023/2023-11-29/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call December 4)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call December 5)
- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call December 5)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call December 6)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting November 30)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- SIG quarterly updates will begin in January 2024
-
Review action items from last meeting
- Onboarding SD-JWT Rust lab
- Create sd-jwt-rust repo in OpenWallet Foundation Labs GitHub \u2013 completed
- Create sd-jwt-rust Discord channel \u2013 completed (#sd-jwt-rust)
- Complete intake form to create project charter -- follow up with LF Legal on status
- Work with John Henderson to transfer VC-API project to OpenWallet Foundation Labs
- Work with David Zeuthen to transfer Android Identity Library project to OpenWallet Foundation Labs
-
Resolution: SD-JWT .NET Project Proposal
- RESOLVED: That the SD-JWT .NET lab proposal is hereby confirmed, approved, and adopted.
- Approved by role call vote; 7 aye, 0 nay, 0 abstain
-
Resolution: Agent Framework JavaScript Project Proposal
- RESOLVED: That the Agent Framework JavaScript Project proposal is hereby confirmed, approved, and adopted.
- Stavros Kounis agreed to be the second sponsor to bring the project in at growth stage
- Approved by role call vote; 7 aye, 0 nay, 0 abstain
-
Open discussion and next steps
- Should we cancel the December 27, 2023 call?
- Next meeting is December 13, 2023
- First GAC meeting held
- Request for feedback: https://gitlab.opencode.de/bmi/eudi-wallet/eidas-2.0-architekturkonzept-v1/
"},{"location":"meetings/2023/2023-12-13/","title":"2023-12-13","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2023/2023-12-13/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Moving to LFX Meetings
- Resolution: Add Schedule for Quarterly SIG Updates
- 2023 Retrospective
- Open discussion and next steps
"},{"location":"meetings/2023/2023-12-13/#links","title":"Links","text":""},{"location":"meetings/2023/2023-12-13/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Mike Varley
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2023/2023-12-13/#action-items","title":"Action Items","text":" - Create Vulnerability Disclosure Policy
"},{"location":"meetings/2023/2023-12-13/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call January 8)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call December 19)
- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call December 19)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call December 20)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting December 14)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Review action items from last meeting
- Onboard SD-JWT .NET \u2013 completed
- Transfer sd-jwt-dotnet repo to OpenWallet Foundation Labs GitHub \u2013 completed
- Create sd-jwt-dotnet Discord channel \u2013 completed
- Follow up with LF Legal on project intake form \u2013 completed
- Onboard Agent Framework JavaScript \u2013 completed
- Transfer repos to OpenWallet Foundation GitHub \u2013 completed
- Create agent-framework-js Discord channel \u2013 completed
- Follow up with LF Legal on project intake form \u2013 completed
- Work with John Henderson to transfer VC-API project to OpenWallet Foundation Labs \u2013 in progress
- Work with David Zeuthen to transfer Android Identity Library project to OpenWallet Foundation Labs \u2013 completed
-
Moving to LFX Meetings
- Reviewed LFX Meetings
- See LFX Meetings Management Guide
-
Resolution: Add Schedule for Quarterly SIG Updates
- RESOLVED: That the pull request \"Resolution: Add Schedule for Quarterly SIG Updates\" is hereby confirmed, approved, and adopted.
- Motion Wenjing, second Jeremie
- Resolution passed with no objections or abstentions
-
2023 Retrospective
- Reviewed accomplishments
- Also include in the accomplishments the face-to-face and the discussion with LF Legal on project charters
- Retrospective
- Shoutouts?
- Google for hosting us at our face-to-face in Mountain View
- Tracy for leading meetings
- SIG and Task Force leaders
- What went well?
- Good structure on the TAC
- Opportunity to collaborate
- Consistency of how TAC meetings are managed and the access to the information needed so that you can do prep
- Transparency
- Inclusiveness
- Team spirit
- Advocacy
- Provided confidence to move from being a consumer of open source to actually publishing open source at OWF
- Learning process of what's involved in open source has been incredibly useful
- Collaboration
- Donation
- Strong community engagement
- Support OpenWallet has received in terms of projects, sponsors and Governmental Advisory Council members
- What could we do differently next year?
- Include voting members on the agenda and let people know who can vote at these meetings
- Recommendations for next year
- List of events for next year -- include in the #events channel on Discord
- Creating a resource of slides that others have presented at conferences to present OWF
- Challenge: helping projects grow within the OWF
- Challenge: helping projects collaborate and work with one another
- Engaging with the EUDI and bringing projects into OWF
- Interoperability is a topic for us to focus on next year. Not just for the same protocols, but also across protocols. SIDI is also something that we should work closely with
- Publish a white paper documenting our overall architectural considerations for open wallets (started already in the Architecture SIG)
- Engaging with Trust Over IP
-
Open discussion and next steps
- Vulnerability Disclosure Policy
- Look at creating this next year
- Resources:
- OpenSSF Guide to implementing a coordinated vulnerability disclosure process for open source projects
- Hyperledger Foundation Security Policy
- Hyperledger Foundation Security Template
- EU Digital Green Certificates Security Policy
- Next meeting is January 10, 2024
- Architecture SIG Quarterly Update
- Using LFX Meetings
"},{"location":"meetings/2024/2024-01-10/","title":"2024-01-10","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-01-10/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Architecture SIG Update
- Discuss Drafted Vulnerability Disclosure Policy
- Goals for 2024 (time permitting)
- Open discussion and next steps
"},{"location":"meetings/2024/2024-01-10/#links","title":"Links","text":""},{"location":"meetings/2024/2024-01-10/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Rolson Quadras (alternate for Mike Varley)
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-01-10/#action-items","title":"Action Items","text":" - List of TAC goals from other LF projects - Brian
- Update Vulnerability Disclosure Pull Request - Tracy
"},{"location":"meetings/2024/2024-01-10/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call January 15)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call January 17)
- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call January 16)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call January 17)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting January 11)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Review action items from last meeting
- Work with John Henderson to transfer VC-API project to OpenWallet Foundation Labs \u2013 completed
- Create Vulnerability Disclosure Policy \u2013 drafted
-
Architecture SIG Update
- See Architecture SIG Q1 2024 Update for the answers to the following questions:
- What is the Architecture SIG?
- What has the Architecture SIG accomplished?
- What is next for the Architecture SIG?
- Where can I get information on the Architecture SIG?
- How do I participate in the Architecture SIG?
- Discussion on how the Architecture SIG should work with projects
- In general, people see the role of the architecture SIG as a group that provides information on the state of the digital wallet architectues that can be used to provide insight into projects that may be missing from the OWF and in the long term a place that will help projects work more closely together.
-
Discuss Drafted Vulnerability Disclosure Policy
- Discuss pull request
- Rework to consider the following audiences: reporters, people using the code, and maintainers
- Separate out standard text from project-specific text
-
Goals for 2024
- What specific goals does the TAC have for 2024?
- Brian suggested looking at what other TAC goals have been
- Information for new submitters
- Updates on existing projects
-
Open discussion and next steps
"},{"location":"meetings/2024/2024-01-24/","title":"2024-01-24","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-01-24/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Project Proposal: Multi-format Verifiable Credentials for iOS
- Discuss Vulnerability Disclosure Policy
- Elections
- Goals for 2024
- Open discussion and next steps
"},{"location":"meetings/2024/2024-01-24/#links","title":"Links","text":""},{"location":"meetings/2024/2024-01-24/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Mike Varley
- Marie Austenaa (alternate for Pete Cooling)
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-01-24/#action-items","title":"Action Items","text":" - Onboard new lab
- Create Discord channel
- Create GitHub repo
- Open discussion item for 2024 Goals -- completed
- Provide thoughts on the 2024 TAC Goals and upvote any items that you think has importance -- All
"},{"location":"meetings/2024/2024-01-24/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call January 29)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call January 30)
- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call January 30)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call January 31)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting January 25)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Review action items from last meeting
- List of TAC goals from other LF projects \u2013 Brian
- Other projects at the LF only have a responsiblities list with the main goal of the TAC, TOC, or TSC to successfully carry out these responsibilities
- Hyperledger Foundation has been putting together goals for the last couple of years (2023 Goals, 2024 Goals)
- Update Vulnerability Disclosure Policy \u2013 drafted
-
Project Proposal: Multi-format VC for iOS
- RESOLVED: That the Multi-format Verifiable Credentials for iOS lab is hereby confirmed, approved, and adopted.
-
Discuss Vulnerability Disclosure Policy
- Discuss pull request
- RESOLVED: That the Vulnerability Disclosure Policy is hereby confirmed, approved, and adopted.
-
Elections
-
Goals for 2024
- What specific goals does the TAC have for 2024?
- Discussed at the 2023-12-13 meeting
- Will open a discussion item on GitHub for offline conversation
-
Open discussion and next steps
- Next TAC Meeting February 7, 2024
- Credential Format Comparison SIG Update
"},{"location":"meetings/2024/2024-02-07/","title":"2024-02-07","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-02-07/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Credential Format Comparison SIG Update
- Open discussion and next steps
"},{"location":"meetings/2024/2024-02-07/#links","title":"Links","text":""},{"location":"meetings/2024/2024-02-07/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Mike Varley
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-02-07/#action-items","title":"Action Items","text":" - Sean to work with Mirko on a blog post on the Credential Format Comparison SIG
"},{"location":"meetings/2024/2024-02-07/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call February 12)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call February 13)
- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call February 13)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call February 14)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting February 8)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Review action items from last meeting
- Onboard new lab
- Create Discord channel -- completed (#multiformat-vc-ios)
- Create GitHub repo -- ticket created
- Open discussion item for 2024 Goals -- completed
- Provide thoughts on the 2024 TAC Goals and upvote any items that you think has importance -- All
-
Credential Format Comparison SIG Update
-
Open discussion and next steps
- Next TAC Meeting February 21, 2024
- Digital Wallets and Agents Overview SIG Update
"},{"location":"meetings/2024/2024-02-21/","title":"2024-02-21","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-02-21/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Digital Wallets and Agents Overviews SIG Update
- Bifold Project Proposal
- Project Promotion Process
- Open discussion and next steps
"},{"location":"meetings/2024/2024-02-21/#links","title":"Links","text":""},{"location":"meetings/2024/2024-02-21/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Mike Varley
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-02-21/#action-items","title":"Action Items","text":" - Create a PR against the project lifecycle to include information on transitioning through the lifecycle stages -- Tracy
- Work with Bifold to onboard project into OWF
"},{"location":"meetings/2024/2024-02-21/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call February 26)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call February 27)
- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call February 27)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call February 28)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting February 22)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Review action items from last meeting
- Sean to work with Mirko on a blog post on the Credential Format Comparison SIG \u2013 in progress
-
Digital Wallets and Agents Overviews SIG Update
- Information included in the slides on the work that is being done.
-
Bifold Project Proposal
- RESOLVED: That the Bifold project proposal is hereby confirmed, approved, and adopted as a growth project.
- Wenjing volunteered to be second sponsor for the project
- Jeremie motion; Wenjing seconded; Unanimously approved
-
Project Promotion Process
- Our current project lifecycle does not clearly outline the steps necessary for projects to progress in the lifecycle.
- Suggested changes to the lifecycle to create a PR to update the original project proposal to include the new stage and other information relevant to meet the proposed stage\u2019s criteria.
- Upside: This process is similar to the original project proposal process.
- Possible Downside: This will overwrite the original proposal but might not be a concern given the history in GitHub on the file.
- If we do a PR to the original proposal, we will need to make sure that we can have links to the previous versions that were approved.
- We can possibly do this via the project pages by adding a new section
- Action: Tracy to create a PR to provide details on what this will look like.
-
Open discussion and next steps
- Next TAC Meeting March 6, 2024
"},{"location":"meetings/2024/2024-03-06/","title":"2024-03-06","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-03-06/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Safe Wallet SIG Update
- OWF Wallet Stacks
- Project Promotion Process
- Open discussion and next steps
"},{"location":"meetings/2024/2024-03-06/#links","title":"Links","text":""},{"location":"meetings/2024/2024-03-06/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Rolson Quadras (alternate for Mike Varley)
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-03-06/#action-items","title":"Action Items","text":" - Create discussion item to continue discussion on Wallet Stacks - Tracy -- completed
"},{"location":"meetings/2024/2024-03-06/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call March 11)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call March 12)
- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call March 12)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call March 13)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting March 7)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- Reminder: Elections are coming up starting March 20, 2024; we will be accepting TAC \u201cat large\u201d nominations
- Join the OpenWallet Foundation for our 1 year anniversary webinar on March 14, 9am PDT / 1700 CET / 9:30pm IST https://zoom.us/webinar/register/WN_MiUSaLFgQFOhVdTBMtlLuA#/registration
-
Review action items from last meeting
- Create a PR against the project lifecycle to include information on transitioning through the lifecycle stages \u2013 complete
- Work with Bifold to onboard project into OWF \u2013 completed
-
Safe Wallet SIG Update
- Information included in the slides on the updates.
-
OWF Wallet Stacks
- Brian presented the idea of Wallet Stacks as outlined in the slides
- Discussion ensued
- A discussion item in the TAC GitHub will be created to continue discussions and feedback on the idea
-
Project Promotion Process
- RESOLVED: That the project promotion process is hereby confirmed, approved, and adopted.
- Moved to the next meeting
- Request that TAC members review the PR and provide any feedback
-
Open discussion and next steps
- Next TAC Meeting March 20 2024
"},{"location":"meetings/2024/2024-03-20/","title":"2024-03-20","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-03-20/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Project Promotion Process
- TAC \u201cAt Large\u201d Nomination Process and Voting Schedule
- Open discussion and next steps
"},{"location":"meetings/2024/2024-03-20/#links","title":"Links","text":""},{"location":"meetings/2024/2024-03-20/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jeremie Miller
- Rolson Quadras (alternate for Mike Varley)
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-03-20/#action-items","title":"Action Items","text":" - Determine way to get the sample project charter more visible on the website.
"},{"location":"meetings/2024/2024-03-20/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call March 25)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call March 26)
- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call March 26)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call March 27)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting March 21)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Review action items from last meeting
- Create discussion item to continue discussion on Wallet Stacks - Tracy -- completed
-
Project Promotion Process
- RESOLVED: That the project promotion process is hereby confirmed, approved, and adopted.
- Motion - David Z; Seconded - Jeremie M
- Unanimously approved
-
TAC \u201cAt Large\u201d Nomination Process
- Submit nominations via a GitHub issue at 2024 \"At Large\" Nomination
- Title of issue: [NOMINATION]: 2024 \u201cat large\u201d Name
- Include a short bio, outline your qualifications, and provide a statement explaining why you would be a good choice for the seat
-
TAC \"At Large\" Voting Schedule
- 2024-03-20 Nomination Period Begins
- 2024-03-27 Noon PT Nomination Period Ends
- 2024-03-27 Helios Voting Ballot Distributed to Existing TAC Members
- 2024-04-02 Noon PT Voting Ends
- 2024-04-02 Results Announced on the TAC mailing list
- 2024-04-03 New \u201cat large\u201d representatives begin their term
-
Open discussion and next steps
- Next TAC Meeting April 3 2024
- Architecture SIG Q2 Update
- Question asked about the OWF Developer Day on April 15 - should have more details early next week
- Question asked about making it easier to find the sample project charter on the TAC website
- Question asked about how to get sponsors for the SD-JWT JavaScript project to move to Growth - reach out to the TAC members (individually, on the #tac Discord channel, or on the TAC mailing list)
- Question asked about how to find out what was going on in the community and how to get involved:
- Walked therough the TAC website
- Walked through the OpenWallet Foundation Participate page
"},{"location":"meetings/2024/2024-04-03/","title":"2024-04-03","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-04-03/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Welcome New \u201cAt Large\u201d Representatives
- Architecture SIG Q2 Update
- TAC Chair/Vice Chair Nomination Process and Voting Schedule
- Wiki Update
- The Wallet Stack (and next steps)
- Open discussion and next steps
"},{"location":"meetings/2024/2024-04-03/#links","title":"Links","text":""},{"location":"meetings/2024/2024-04-03/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Mike Varley
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-04-03/#action-items","title":"Action Items","text":" - Create a content plan for where stuff should live and who should control the content
"},{"location":"meetings/2024/2024-04-03/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call April 8)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call April 9)
- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call April 9)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call April 10)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting April 4)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- Jorge Flores (Co-Founder & CTO of Entidad) and Jesus Torres (Co-Founder & CEO of Entidad): How an Aries digital trust ecosystem helped distribute $60M USD (& counting) to essential workers - Presenting at the Hyperledger Identity Special Interest Group on Thursday, April 4 @ 3PM UTC, 8AM PDT, 9AM MDT, 11AM EDT. Join on Zoom: https://zoom.us/j/93003523877?pwd=Q3VvMnJ1N0lSUEZSc283SmFGRk9SQT09
- IIW Planning discussion taking place on Discord in the #iiw-planning channel
- EIC Planning discussions taking place on Discord in the #eic-planning channel
-
Review action items from last meeting
- Determine way to get the sample project charter more visible on the website -- completed
-
Welcome New \u201cAt Large\u201d Representatives
- Thank you to all the nominees.
- Welcome back, Stavros!
- Welcome, Ace!
- Thank you for your service, Jeremie!
-
Architecture SIG Q2 Update
-
TAC Chair/Vice Chair Nomination Process
- Only TAC voting members are eligible to run for the TAC chair and vice chair seats
- Electing a vice chair will be held in conjunction with the chair election; the person with the second highest number of votes will serve as the vice chair
- Submit nominations via a GitHub issue at 2024 Chair/Vice Chair Nomination
- Title of issue: [NOMINATION]: 2024 Chair/Vice Chair Name
- Include a short bio, outline your qualifications, and provide a statement explaining why you would be a good choice for the seat
- See Elections for more information
-
TAC Chair/Vice Chair Voting Schedule
- 2024-04-03 Nomination Period Begins
- 2024-04-10 Noon PT Nomination Period Ends
- 2024-04-10 Helios Voting Ballot Distributed to Existing TAC Members
- 2024-04-16 Noon PT Voting Ends
- 2024-04-16 Results Announced on the TAC mailing list
- 2024-04-17 New Chair and Vice Chair begin their term
-
Wiki Update
- https://wiki.openwallet.foundation
- Discussion about content plan. Where should information live? Who is responsible for changes?
- TAC website makes sense for things that the TAC is responsible for
- The maintainers should be responsible for project information
- The LF Staff is responsible for the openwallet.foundation website content
-
The Wallet Stack (and next steps)
- Formation of a Secure Hardware SIG
- Looking for interested parties
-
Open discussion and next steps
- Next TAC Meeting April 17, 2024
"},{"location":"meetings/2024/2024-04-17/","title":"2024-04-17","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-04-17/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Chair/Vice Chair Results
- Project Proposal: React Native Kit for EUDI Wallet Reference Implementation
- OWF Naming Policy Update
- Content Plan
- Open discussion and next steps
"},{"location":"meetings/2024/2024-04-17/#links","title":"Links","text":""},{"location":"meetings/2024/2024-04-17/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Mike Varley
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-04-17/#action-items","title":"Action Items","text":" - Set up new lab eudi-wallet-kit-react-native
- Discord channel
- GitHub repo
"},{"location":"meetings/2024/2024-04-17/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call April 22)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call April 23)
- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call April 23)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call April 24)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting April 18)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- EIC Planning discussions taking place on Discord in the #eic-planning channel
- The Hyperledger Identity SIG (ID SIG) recently hosted Jorge and Jesus from Entidad for \"How The Aries Digital Trust Ecosystem Helped Distribute $60M USD (and counting) to Essential Workers. You can check out the recording on YouTube.
- Michel Sahli is our GAC representative
-
Review action items from last meeting
- Create a content plan for where stuff should live and who should control the content -- in progress
-
Chair/Vice Chair Results
- Thank you to all nominees
- Stavros, vice chair
- Tracy, chair
-
Project Proposal: React Native Kit for EUDI Wallet Reference Implementation
- RESOLVED: That the React Native Kit for EUDI Wallet Reference Implementation lab proposal is hereby confirmed, approved, and adopted.
- Stavros motion; Ace seconded; Approved unanimously by the present TAC members
-
OWF Naming Policy Update
- Reviewed Project Naming Policy
- Request that the community provide suggested edits and comments
- After incoming feedback, Sean will work with the LF Staff prior to bringing back to the TAC for approval
-
Content Plan
- Quickly reviewed Content Plan
- Request that the community provide suggested edits and comments
- Determine where source of truth is for certain items, like the project list
-
Open discussion and next steps
- Next TAC Meeting May 1, 2024
"},{"location":"meetings/2024/2024-05-01/","title":"2024-05-01","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-05-01/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Credential Format Comparison SIG Q2 Update
- Content Plan
- Reference Architecture contribution
- Open discussion and next steps
"},{"location":"meetings/2024/2024-05-01/#links","title":"Links","text":""},{"location":"meetings/2024/2024-05-01/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quandras (alternate for Mike Varley)
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-05-01/#action-items","title":"Action Items","text":" - Update Content Plan PR to include links
"},{"location":"meetings/2024/2024-05-01/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call May 6)
- OID4VC Due Diligence task force meets bi-weekly on Tuesdays at 5pm CET (next call May 7)
- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call May 7)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call May 8)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting May 2)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- EIC Planning discussions taking place on Discord in the #eic-planning channel
-
Review action items from last meeting
- Set up new lab eudi-wallet-kit-react-native - complete
- Discord channel
- GitHub repo
-
Content Plan
- RESOLVED: That the Content Plan is hereby confirmed, approved, and adopted.
- Wenjing motion; Rolson seconded
- Unanimously approved by the present TAC voting members
-
Reference Architecture Contribution
- Pull Request (Rendered version)
- Proposed next steps:
- Input from community - please provide comments on the PR
- Add a heatmap that maps our current projects to the technology capabilities
- David Z is concerned that the whitepaper may conflict with existing guidance
- Request that a list of existing guidance be provided in the PR so that we may validate that the reference architecture whitepaper does not conflict with existing guidance
-
Open discussion and next steps
- Next TAC Meeting May 15 2024
- Digital Wallet and Agent Overviews SIG Update
- OID4VC Due Diligence task force update
- Project Proposal: Library for OpenID4BLE
"},{"location":"meetings/2024/2024-05-15/","title":"2024-05-15","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-05-15/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Welcome new TAC member
- Project Proposal: OpenId4BLE Library
- Project Proposal: Trust Spanning Protocol
- Project Annual Reviews
- OpenID4VC Due Diligence Task Force Update
- Open discussion and next steps
"},{"location":"meetings/2024/2024-05-15/#links","title":"Links","text":""},{"location":"meetings/2024/2024-05-15/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quadras
- Stefan Kauhaus (alternate for Pete Cooling)
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-05-15/#action-items","title":"Action Items","text":" - Onboard OpenID4BLE Library lab
- Onboard Trust Spanning Protocol lab
"},{"location":"meetings/2024/2024-05-15/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Architecture SIG meets weekly on Mondays at 11am US/Pacific (next call June 3)
- Safe Wallet SIG meets weekly on Tuesdays at 7am US/Pacific (next call June 4)
- Credential Format Comparison SIG meets bi-weekly on Wednesdays at 4pm CET on alternate weeks to the TAC (next call June 5)
- Digital Wallets and Agents Overviews SIG meets biweekly on Thursdays at 5:00pm CET on the same weeks as the TAC (next meeting May 30)
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- EIC Planning discussions taking place on Discord in the #eic-planning channel
-
Welcome new TAC member
- Rolson Quadras will represent Gen Digital moving forward
- Thank you Mike Varley for your service
-
Review action items from last meeting
- Update Content Plan PR to include links - completed
-
Project Proposal: OpenId4BLE Library
- Recommended that project come in at Labs stage
- Recommended that project move to GitHub issues (to be completed in 3-6 months)
- Recommended that project use Discord for communication instead of Slack
- Discussed governance and diversity of maintainers
- RESOLVED: That the OpenId4BLE Library lab proposal is hereby confirmed, approved, and adopted.
- Stavros motioned; David seconded
- Unanimously approved by the present TAC voting members.
-
Project Proposal: Trust Spanning Protocol
- Discussed the need for language bindings that can be used by OWF projects. Recommendation is to implement the language bindings in conjunction with the projects that will use it to ensure correctness.
- Research needs to be done on the license of https://github.com/dalek-cryptography/curve25519-dalek and whether an alternate implementation is needed
- RESOLVED: That the Trust Spanning Protocol lab proposal is hereby confirmed, approved, and adopted.
- Stavros motioned; Rolson seconded
- Unanimously approved by the present TAC voting members.
-
Project Annual Reviews
- RESOLVED: That the Project Annual Reviews pull request is hereby confirmed, approved, and adopted.
- Adds template
- Adds schedule
- Vote moved to PR review
-
OID4VC Due Diligence Task Force Update
- Torsten provided an update on the OID4VC Due Diligence task force and recommended closing the task force as it has accomplished its goals.
-
Open discussion and next steps
- Next TAC Meeting May 29, 2024
- Digital Wallet and Agent Overviews SIG Update
"},{"location":"meetings/2024/2024-05-29/","title":"2024-05-29","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-05-29/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Project Proposal: credhub
- Project Annual Reviews
- Digital Wallet and Agent Overviews SIG Update
- Open discussion and next steps
"},{"location":"meetings/2024/2024-05-29/#links","title":"Links","text":""},{"location":"meetings/2024/2024-05-29/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quadras
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-05-29/#action-items","title":"Action Items","text":" - Onboard Credhub project
- Create Discord channel
- Transfer repo
- Create project page
"},{"location":"meetings/2024/2024-05-29/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- EIC Planning discussions taking place on Discord in the #eic-planning channel
- If you are interested in participating in the architecture SIG calls, we have a when2meet survey out there to find a new meeting time
- EUDI Architecture Reference Framework v1.4 published
- OpenWallet Foundation is hosting two workshops -- one for OpenID Connect for VCI and one for OpenID Connect for VP -- on June 10th and June 12th. Please be on the lookout for registration links coming soon
-
Review action items from last meeting
- Onboard OpenID4BLE Library lab
- Created Discord channel (#tuvali) - completed
- Need to transfer repo (Issue #151) - in progress
- Working on project page (PR #149) - in progress
- Onboard Trust Spanning Protocol lab
- Created Discord channel (#tsp) - completed
- Need to transfer repo (Issue #150) - in progress
- Working on project page (PR #149) - in progress
-
Project Proposal: credhub
- RESOLVED: That the credhub lab proposal is hereby confirmed, approved, and adopted.
- Stavros motioned; Wenjing seconded
- Unanimously approved
-
Project Annual Reviews
- RESOLVED: That the Project Annual Reviews pull request is hereby confirmed, approved, and adopted.
- David Z motioned; Rolson seconded
- Unanimously approved
-
Digital Wallet and Agent Overviews SIG Update
- Mirko presented an update on the SIG
-
Open discussion and next steps
- Next TAC Meeting June 12, 2024
- SD-JWT Python Annual Review
- SD-JWT Kotlin Annual Review
- Safe Wallet SIG Update
"},{"location":"meetings/2024/2024-06-12/","title":"2024-06-12","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-06-12/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Project Proposal: mdl.js
- Project Annual Reviews
- SD-JWT Python Annual Review
- SD-JWT Kotlin Annual Review
- Safe Wallet SIG Update
- Open discussion and next steps
"},{"location":"meetings/2024/2024-06-12/#links","title":"Links","text":""},{"location":"meetings/2024/2024-06-12/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quadras
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-06-12/#action-items","title":"Action Items","text":" - Onboard mdl.js
- Reach out to Fabian regarding new maintainership - Sean/Torsten
- File PR against openwallet-foundation-labs/governance to update maintainership for sd-jwt-kotlin - Ace
"},{"location":"meetings/2024/2024-06-12/#meeting-minutes","title":"Meeting Minutes","text":""},{"location":"meetings/2024/2024-06-26/","title":"2024-06-26","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-06-26/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Project Annual Reviews
- SD-JWT Kotlin Annual Review
- Discuss approval process for SIG output
- TAC Goals 2024
- Open discussion and next steps
"},{"location":"meetings/2024/2024-06-26/#links","title":"Links","text":""},{"location":"meetings/2024/2024-06-26/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quadras
- Stefan Kauhaus (alternate for Pete Cooling)
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-06-26/#action-items","title":"Action Items","text":" - Reach out to Fabian regarding new maintainership of sd-jwt-kotlin - Sean
- Document process for SIG output approvals
- Create a presentations Drive folder for uploading OWF presentations from the community - Sean
- Create a page on the TAC site as an index for the presentations in the above Drive folder - Tracy
"},{"location":"meetings/2024/2024-06-26/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- Architecture SIG call is moving to Mondays at 8:30 AM US/Pacific starting June 17
- Safe Wallet SIG has asked us to review and approve their v1.0 release of the Wallet Safety Guide and Checklist. Please take the next couple of weeks to review and add any comments as issues in the Safe Wallet SIG repository for us to discuss at the July 10th meeting.
-
Review action items from last meeting
- Onboard mdl.js - completed
- Created Discord channel (#mdl-js)
- Repo transferred
- Project page available
- Reach out to Fabian regarding new maintainership - Sean/Torsten
- File PR against openwallet-foundation-labs/governance to update maintainership for sd-jwt-kotlin - Ace - completed
-
Project Annual Reviews
- SD-JWT Kotlin Annual Review - On hold until conversation with Fabian
-
Discuss Approval Process for SIG output
- Discussed the need for documenting and understanding the ambition of the SIG during the initial proposal process. Will the SIG want to publish documents that represent the views of the OWF, the views of the entire wallet ecosystem, or some other level
- Anything that is published from OWF SIGs will be presumed to speak on behalf of the OWF.
- Document types of approvals that have been obtained by the document. Example from OIDF
- Best practice is to include a \"Terms of Use\" section in the output. See Terms of Use section in ToIP document for an example
-
Review TAC Goals 2024
- Discussed the TAC Goals for 2024.
- List of events for next year -- include in the #events channel on Discord
- This has been pretty opportunistic so far
- Creating a resource of slides that others have presented at conferences to present OWF
- Discussed creating a Drive folder for the community to upload their presentation along with an index on the TAC website for people to update with information about the presentations uploaded.
- Challenge: helping projects collaborate and work with one another
- Identify projects with similar goals and bring the projects together in a group to discuss opportunities for collaboration and interoperability testing.
- Understanding which projects use each other.
- Newsletter similar to Hyperledger's /dev/weekly newsletters
- Engaging with the EUDI and bringing projects into OWF
- Hosted workshop with EUDI
- Interoperability is a topic for us to focus on next year. Not just for the same protocols, but also across protocols.
- Discussed possibility of holding Inter-op-athons.
- Torsten mentioned that it would be good for OWF to work with the OID4VP/VC conformance test teams.
- Wenjing mentioned that interoperability is more than just at the protocol level, we should also be thinking about global interoperability.
- Should consider an interopability landscape assessment.
- Publish a white paper documenting our overall architectural considerations for open wallets (started already in the Architecture SIG)
- Existing pull request openwallet-foundation/architecture-sig#66
-
Open discussion and next steps
- Next TAC Meeting July 10, 2024
- v1.0 release of the Wallet Safety Guide and Checklist
- Architecture SIG Update
"},{"location":"meetings/2024/2024-07-10/","title":"2024-07-10","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-07-10/#agenda","title":"Agenda","text":" - Announcements
- Update on Safe Wallet SIG whitepaper
- Review action items from last meeting
- Project Annual Reviews
- SD-JWT Kotlin Annual Review
- Publishing Papers in the OWF Community
- Architecture SIG Update
- Open discussion and next steps
"},{"location":"meetings/2024/2024-07-10/#links","title":"Links","text":""},{"location":"meetings/2024/2024-07-10/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quadras
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-07-10/#action-items","title":"Action Items","text":" - Send out email regarding summer meetings - Sean
- Review Papers Lifecycle governance document - all
- Review SD-JWT Kotlin Annual Review - all
"},{"location":"meetings/2024/2024-07-10/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
-
Update on Safe Wallet SIG Update
- The Safe Wallet SIG has taken another pass at the document and made some significant changes from the v1.0 release that was shared last week. As such, the plan is to:
- Once the SafeWallet SIG members approve their changes a final version will be created on GitHub for the TAC members to review/comment.
- SafeWallet SIG members will join the TAC Call on Wednesday, July 24th to discuss the future of the SIG and field questions from the TAC.
-
Review action items from last meeting
- Reach out to Fabian regarding new maintainership of sd-jwt-kotlin - completed Ace has reached out and confirmed transition
- Document process for SIG output approvals - drafted
- Create a presentations Drive folder for uploading OWF presentations from the community - Sean - completed
- Create a page on the TAC site as an index for the presentations in the above Drive folder - Tracy
-
Project Annual Reviews
- SD-JWT Kotlin Annual Review (if available) - PR just submitted; move discussion to next meeting
- Initial discussion about whether sd-jwt-kotlin will be a mirror of the EUDI or a fork. Concern that we may cause fragmentation if we become a fork. If we are a mirror, why should this remain in OWF?
- Discussion will continue on the PR and when we meet next
-
Publishing Papers in the OWF Community
- RESOLVED: That the Papers Lifecycle governance document is hereby confirmed, approved, and adopted. Vote not conducted this week
- Discussion regarding whether this is making OWF an SDO - no, it is not. Based on our expectation, SIGs and task forces will produce deliverables. This will ensure that people have the opportunity to review and discuss these deliverables prior to TAC approval.
- Question and discussion on whether OpenWallet Foundation should publish papers.
- Comment about ensuring that there is a workflow behind the process to ensure that papers review, approval, and publishing can be appropriately scheduled into the backlog.
- In general, there is support from non-TAC voting members about the process adding clarity on expectations for SIGs and task forces.
- Action: TAC members to review process and provide feedback for asynchronous discussion and move vote to next meeting
-
Architecture SIG Update
-
Open discussion and next steps
- Next TAC Meeting July 24, 2024
- SD-JWT Kotlin Annual Review
- Papers Lifecycle governance document
- Safe Wallet SIG Whitepaper review and vote
- Credential Format Comparison SIG update
"},{"location":"meetings/2024/2024-07-24/","title":"2024-07-24","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-07-24/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Project Proposal: Begin Wallet Core
- Credential Format Comparison SIG update
- Safe Wallet SIG deliverable - MOVED TO NEXT MEETING
- Publishing Deliverables in the OWF Community - MOVED TO NEXT MEETING
- Project Annual Reviews - MOVED TO NEXT MEETING
- SD-JWT Kotlin Annual Review
- Open discussion and next steps
"},{"location":"meetings/2024/2024-07-24/#links","title":"Links","text":""},{"location":"meetings/2024/2024-07-24/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quadras
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-07-24/#action-items","title":"Action Items","text":" - Look at updating the project proposal template PR to remove the need for a charter - Tracy
- Send email to TAC mailing list to kick off discussion about Growth acceptance criteria - Tracy
- Review Deliverables Lifecycle governance document - all
- Review SD-JWT Kotlin Annual Review - all
- Review Verifiable Credentials Wallet Lab Proposal - all
- Review Lifecycle and Project Charter changes - openwallet-foundation/project-proposals#40 and openwallet-foundation/tac#173 - all
"},{"location":"meetings/2024/2024-07-24/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- Lab Proposal: Verifiable Credentials Wallet - Please review (since it is lab, we can approve offline if we get enough votes/approvals on GitHub)
- Lifecycle and Project Charter changes - Please review the following two PRs for intake form to be completed only after acceptance of project proposal: openwallet-foundation/project-proposals#40 and openwallet-foundation/tac#173
-
Review action items from last meeting
- Create a page on the TAC site as an index for the presentations in the above Drive folder - Tracy
- Send out email regarding summer meetings - Sean \u2013 completed
- Review Deliverables Lifecycle governance document - all
- Review SD-JWT Kotlin Annual Review - all
-
Project Proposal:
- RESOLVED: That the Begin Wallet Core proposal is hereby confirmed, approved, and adopted.
- TAC recommended that this be accepted as a lab
- Discussion ensued regarding looking at the acceptance criteria for Growth projects
- Discussion also about whether we should combine the openwallet-foundation-labs and openwallet-foundation organizations in GitHub
- Action: Take the above two discussions offline in an email on the TAC mailing list
- Wenjing motioned; David seconded
- Unanimously approved
-
Credential Format Comparison SIG Q3 Update
- Mirko requested guidance in moving this SIG forward as there is little participation
- Possible suggestions:
- Move SIG to meet monthly
- Recruit co-chair
- Determine incentives that might help others to participate
- Creating good first issues or help wanted issues to help others know where they might participate
- Working closely with OIX and OIDC who is also doing similar work
-
Safe Wallet SIG Deliverable - MOVED TO NEXT MEETING
-
Publishing Deliverables in the OWF Community - MOVED TO NEXT MEETING
- RESOLVED: That the Deliverables Lifecycle governance document is hereby confirmed, approved, and adopted.
-
Project Annual Reviews - MOVED TO NEXT MEETING
- SD-JWT Kotlin Annual Review
-
Open discussion and next steps
- Next TAC Meeting August 7, 2024
- Safe Wallet SIG Deliverable
- Publishing Deliverables in the OWF Community
- Project Annual Reviews
- Digital Wallet and Agent Overviews SIG update
- TAC Meeting August 21, 2024
- Farmworker Wallet OS Project Annual Review
"},{"location":"meetings/2024/2024-08-07/","title":"2024-08-07","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-08-07/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Project Proposal: Verifiable Credential Wallet
- Remove Intake Form Requirement for Proposals
- Publishing Deliverables in the OWF Community
- Digital Wallet and Agent Overviews SIG update - MOVED TO NEXT MEETING
- Project Annual Reviews - MOVED TO NEXT MEETING
- SD-JWT Kotlin Annual Review
- Open discussion and next steps
"},{"location":"meetings/2024/2024-08-07/#links","title":"Links","text":""},{"location":"meetings/2024/2024-08-07/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quadras
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-08-07/#action-items","title":"Action Items","text":" - Verifiable Credentials Wallet lab onboarding - Sean
- Update Deliverables Lifecycle PR to remove need for TAC approval - Tracy
"},{"location":"meetings/2024/2024-08-07/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- Safe Wallet SIG Ask Me Anything webinar in two weeks; Sean will provide details on Discord
- Architecture SIG is taking a break for August and will start up again after the US Labor Day holiday in September
-
Review action items from last meeting
- Create a link on the TAC to the Community Presentations Drive folder - Tracy \u2013 completed
- Look at updating the project proposal template PR to remove the need for a charter - Tracy - completed (PRs updated)
- Send email to TAC mailing list to kick off discussion about Growth acceptance criteria - Tracy - completed
- Review Deliverables Lifecycle governance document - all
- Review SD-JWT Kotlin Annual Review - all
- Review Verifiable Credentials Wallet Lab Proposal - all
- Review Lifecycle and Project Charter changes - openwallet-foundation/project-proposals#40 and openwallet-foundation/tac#173 - all
-
Project Proposal: Verifiable Credential Wallet
- RESOLVED: That the Verifiable Credential Wallet lab proposal is hereby confirmed, approved, and adopted.
- Stavros motioned; David seconded
- Unanimously approved by the present TAC voting members
-
Remove Intake Form Requirement for Proposals
- RESOLVED: That the following PRs that remove the intake form requirement are hereby confirmed, approved, and adopted.
- openwallet-foundation/project-proposals#40
- openwallet-foundation/tac#173
- Ace motioned; David seconded
- Unanimously approved by the present TAC voting members
-
Publishing Deliverables in the OWF Community
- RESOLVED: That the Deliverables Lifecycle governance document is hereby confirmed, approved, and adopted.
- No vote taken
- Agreed to remove the need for TAC approval
- Agreed that there needs to be a review period for the community to provide feedback
- Discussed whether the current disclaimer is enough
- Requested that folks add suggested text to the PR
-
Digital Wallets and Agents Overview SIG Update
-
Project Annual Reviews - MOVED TO NEXT MEETING
- SD-JWT Kotlin Annual Review
-
Open discussion and next steps
- Next TAC Meeting August 21, 2024
- Publishing Deliverables in the OWF Community
- Project Annual Reviews
- SD-JWT Kotlin Annual Review
- Farmworker Wallet OS Project Annual Review
- Digital Wallet and Agent Overviews SIG update
"},{"location":"meetings/2024/2024-08-21/","title":"2024-08-21","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-08-21/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Digital Wallet and Agent Overviews SIG update
- Project Annual Reviews
- SD-JWT Kotlin - MOVED TO NEXT MEETING
- Farmworker Wallet OS
- Publishing Deliverables in the OWF Community
- Open discussion and next steps
"},{"location":"meetings/2024/2024-08-21/#links","title":"Links","text":""},{"location":"meetings/2024/2024-08-21/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quadras
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-08-21/#action-items","title":"Action Items","text":" - Create plan for the future of the Credential Formats Comparison SIG and the Digital Wallets and Agents Overview SIG - Mirko
"},{"location":"meetings/2024/2024-08-21/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- Safe Wallet SIG Ask Me Anything webinar in two weeks; Sean will provide details on Discord
-
Review action items from last meeting
- Update Deliverables Lifecycle governance document - Tracy - completed
-
Digital Wallets and Agents Overview SIG Update
- Still getting pull requests for new wallets
- Low participation in the bi-weekly meetings
- Possibly combine this SIG with the Credential Format Comparison SIG
- Need to socialize the overview matrix to a wider audience
- Look for ways to involve the projects and possibly to provide ownership of an entry to those that create the wallet
- Adding a comment at the top of the matrix that says that this is volunteer-maintained and you can add your own wallet
- Creation of short videos (what this is, how you can contribute)
- Next step: Mirko will work with others offline to come up with a plan and bring it back to the TAC on possibly merging the SIGs
-
Project Annual Reviews
- SD-JWT Kotlin Annual Review - MOVED TO NEXT MEETING
- Farmworker Wallet OS
- Jorge provided an overview of the progress that the community is making
- Wenjing asked if there was anything that the TAC or the OWF organization could provide
- Having people in the community use the project even if only for testing purposes
- Webinar, workshop, or meetup to allow for a presentation of how to get the project up and running
- RESOLVED: That the Farmworker Wallet OS annual review is hereby confirmed, approved, and adopted.
- Wenjing motioned; David seconded
- 4 approved; 1 abstained
-
Publishing Deliverables in the OWF Community
- RESOLVED: That the Deliverables Lifecycle governance document is hereby confirmed, approved, and adopted.
- No vote taken
- Changes since we last spoke:
- Removed the need for TAC approval, but kept the community review period
- Removed Terms of Usage section (already covered by the CC-by-4.0 text)
- Added a \u201cNon-Representative\u201d Disclaimer section
- Discussed the concerns of the Safe Wallet SIG members that the \"Non-Representative\" Disclaimer section appears that the OWF does not support the work of the SIGs
- No alternative language has been suggested
- We will look at approving this next week
-
Open discussion and next steps
- Next TAC Meeting September 4, 2024
- Project Annual Reviews
- SD-JWT Kotlin Annual Review
- Acceptance Criteria for Growth Projects
- Safe Wallet SIG update
"},{"location":"meetings/2024/2024-09-04/","title":"2024-09-04","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-09-04/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Safe Wallet SIG update
- Project Annual Reviews
- Publishing Deliverables in the OWF Community
- Acceptance Criteria for Growth Projects
- Open discussion and next steps
"},{"location":"meetings/2024/2024-09-04/#links","title":"Links","text":""},{"location":"meetings/2024/2024-09-04/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quadras
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-09-04/#action-items","title":"Action Items","text":" - Update the Deliverables lifecycle to include option #3 and to ensure that this applies to projects too - Tracy
- Respond to issue on project-proposal repo regarding licensing - Tracy
"},{"location":"meetings/2024/2024-09-04/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- OWF Wiki Update: Sean Bohan (OWF Staff) is testing now
-
Review action items from last meeting
- Create plan for the future of the Credential Formats Comparison SIG and the Digital Wallets and Agents Overview SIG - Mirko
-
Safe Wallet SIG Update
- Andy provided background on the SIG and and update of what has been done to date with the SIG
- Andy will be stepping down after the completion of the blog and ask me anything session
- Need to see if there is anyone who would like to lead this group going forward, if the SIG will go on haitus, or be disbanded
-
Project Annual Reviews
- SD-JWT Kotlin Annual Review - MOVE TO NEXT MEETING
-
Publishing Deliverables in the OWF Community
- Is it needed?
- Possible options:
- These materials are a deliverable of the sig name SIG and were created by the contributors to that SIG. It has not been reviewed, approved, or endorsed by the OpenWallet Foundation (\"OWF\") and its members.
- These materials are a deliverable of the sig name SIG and were created by the contributors to that SIG. It does not necessarily reflect the official policies, positions, views or opinions of the OpenWallet Foundation (\"OWF\") and its members.
- These materials are a deliverable of the OWF community. If you have concerns or suggestions regarding the content, please file a pull request.
- Option #3 is the preferred disclaimer for deliverables
-
Changes requested to ensure that this process also applies to projects
-
RESOLVED: That the Deliverables Lifecycle governance document is hereby confirmed, approved, and adopted.
- With the above changes (option #3 and applies to projects)
- Stavros motioned; Wenjing seconded
- Unanimously approved by all present TAC members
-
Open discussion and next steps
- Next TAC Meeting September 18, 2024
- Discussed license issue raised on project-proposals repo
- Discussed how to make it clearer that we have two separate organizations (openwallet-foundation and openwallet-foundation-labs) in GitHub
"},{"location":"meetings/2024/2024-09-18/","title":"2024-09-18","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-09-18/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Project Proposals
- ACA-Py
- Askar
- Name TBD - Aries Agent Test Harness
- DIDComm Mediator Service
- SIG Proposal - Wallet Interoperability - MOVED TO NEXT MEETING
- Project Annual Reviews - SD-JWT Kotlin - MOVED TO NEXT MEETING
- Open discussion and next steps
"},{"location":"meetings/2024/2024-09-18/#links","title":"Links","text":""},{"location":"meetings/2024/2024-09-18/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quadras
- Pete Cooling
- Stavros Kounis
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-09-18/#action-items","title":"Action Items","text":" - Onboard new projects
- Stephen to update SIG proposal for discussion at next meeting
"},{"location":"meetings/2024/2024-09-18/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- Housekeeping:
- Sept 24th: OpenWallet Foundation Multistakeholder Technical Meeting on the EUDI Wallet
- Wiki has been updated by LFIT and has some final edits this week
- OOTO/Holidays Poll to all TAC members this week
- Linux Foundation Maintainer Survey
-
Review action items from last meeting
- Update the Deliverables lifecycle to include option #3 and to ensure that this applies to projects too - Tracy - completed
- Respond to issue on project-proposal repo regarding licensing - Tracy - completed
-
Project Proposals
- Stephen Curran presented an overview of the project proposals and SIGs
- General question regarding existing dependencies and if moving this project will break those dependencies
- There's really not that much of a risk just simply moving the namespaces from Hyperledger to OpenWallet. There will be challanges, but they are independent of one another. All of the projects are independent and have operated independently for a number of years. Where they come together is in the Aries working group and the interop-profiles, which will hopefully continue under the interoperability special interest group. Each project has more or less separate maintainers.
- ACA-Py
- RESOLVED: That the ACA-Py (FKA Aries Cloud Agent Python) project proposal is hereby confirmed, approved, and adopted as an Impact project.
- Wenjing motioned; Stavros seconded
- Unanimously approved by the present TAC voting members
- Askar
- How easy is it to extend to a third database?
- Not sure. SQLx provides the abstraction and that is how it would be extended further, but we have not had anyone add another database. It currently supports SQLlite and Postgres. There has been work to expand it to do things like paging.
- Does this focus more on mobile or server environments?
- This supports both. Used for enterprise data applications as well as Bifold Wallet.
- RESOLVED: That the Askar (FKA Aries Askar) project proposal is hereby confirmed, approved, and adopted as an Impact project.
- Wenjing motioned; Rolson seconded
- Unanimously approved by the present TAC voting members
- Name TBD - Aries Agent Test Harness
- Have all three projects agreed to come under one umbrella?
- Will BC Gov continue to run an instance of the test harness?
- RESOLVED: That the TBD (FKA Aries Agent Test Harness) project proposal is hereby confirmed, approved, and adopted as an Growth project.
- Wenjing motioned; Stavros seconded
- Unanimously approved by the present TAC voting members
- DIDComm Mediator Service
- Will we want the community to run and operate a mediator?
- Indicio is currently running a mediator that is being used by the community. Running software within a foundation will be difficult.
- RESOLVED: That the DIDComm Mediator Service project proposal is hereby confirmed, approved, and adopted as a Growth project.
- Wenjing motioned; Stavros seconded
- Unanimously approved by the present TAC voting members
-
SIG Proposal - Wallet Interoperability - MOVED TO NEXT MEETING
-
Project Annual Reviews - SD-JWT Kotlin Annual Review - MOVED TO NEXT MEETING
-
Open discussion and next steps
- Next TAC Meeting October 2, 2024
- Architecture SIG Update
- VC-API Annual Project Review
- SD-JWT Kotlin Annual Project Review
- Wallet Interoperability SIG Proposal
"},{"location":"meetings/2024/2024-10-02/","title":"2024-10-02","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-10-02/#agenda","title":"Agenda","text":" - Announcements
- Welcome New TAC Members
- Review action items from last meeting
- SIG Proposal - Wallet Interoperability
- Project Proposal - Solid Data Wallet
- Project Annual Reviews
- SD-JWT Kotlin - PLEASE REVIEW OFFLINE
- VC-API - PLEASE REVIEW OFFLINE
- Architecture SIG Q4 Update
- Open discussion and next steps
"},{"location":"meetings/2024/2024-10-02/#links","title":"Links","text":""},{"location":"meetings/2024/2024-10-02/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quadras
- Pete Cooling
- Stavros Kounis
- Stephen Curran
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-10-02/#action-items","title":"Action Items","text":" - Review Annual Reviews offline - all
- Onboard new lab
- Onboard new SIG
"},{"location":"meetings/2024/2024-10-02/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- Housekeeping:
- Update email
- Sept 24th: OpenWallet Foundation Multistakeholder Technical Meeting on the EUDI Wallet update
- Wiki has been updated by LFIT and has some final edits this week
- Thanks to TAC members who filled out the OOTO/Holidays Poll
- Safe Wallet SIG AMA
- Question asked about whether we would consider entire wallet contributions in addition to the libraries and SDKs that we have in the foundation.
- Anything related to wallets are definitely fair game for the OpenWallet Foundation and contributions of the source projects. This would include entire wallets.
-
Welcome new TAC members
- Stephen Curran was welcomed as the ACA-Py project representative
-
Moving Askar to Growth from Impact
- Given the administrative overhead of needing a TAC representative, the Askar project requested that they be moved to Growth from Impact
- RESOLVED: That the Askar project be moved to Growth from Impact stage
- Wenjing motioned; Pete seconded
- Five approved; Stephen and Ace abstained; one absent
-
Review action items from last meeting
- Onboard new projects - in progress
- Stephen to update SIG proposal for discussion at next meeting - completed
-
SIG Proposal - Wallet Interoperability
- Stephen provided an overview of the SIG
- Stavros mentioned a similar effort in the EUDI space that could complement this SIG
- Discussion about scope and a desire that this cover wallet ecosystems instead of just wallets. This is as planned.
- RESOLVED: That the Wallet Interoperability SIG proposal is hereby confirmed, approved, and adopted.
- Wenjing motioned; Ace seconded
- 6 approved; Stephen abstained; one absent
-
Project Proposal - Solid Data Wallet
- Hadrian Zbarcea provided an overview of the proposal
- Questions asked to clarify the scope of the project. Currently proposed as a wallet that uses Solid for storage, but may evolve based on the direction that the OWF community might bring to the efforts
- Suggestion that there might be some good collaboration with Askar to integrate Solid pods
- Project is open to new contributors that may end up becoming maintainers of the project
- GitHub does not seem to be appropriately recognizing that this is an Apache 2.0 only licensed project. We will need to resolve this before bringing the code over. Hadrian has taken an action to determine what is happening there
- RESOLVED: That the Solid Data Wallet proposal is hereby confirmed, approved, and adopted as a Growth project.
- Wenjing motioned; Stavros seconded
- Unanimously approved by the present TAC voting members
-
Project Annual Reviews
- SD-JWT Kotlin Annual Review - PLEASE REVIEW OFFLINE
- VC-API Annual Review - PLEASE REVIEW OFFLINE
-
Open discussion and next steps
- Next TAC Meeting October 16, 2024
- Architecture SIG Update
- Credential Format Comparison SIG Q4 Update
- Wallet Framework .NET Annual Review
"},{"location":"meetings/2024/2024-10-16/","title":"2024-10-16","text":"Reminder
These meetings are covered by the Antitrust Policy and the Code of Conduct.
"},{"location":"meetings/2024/2024-10-16/#agenda","title":"Agenda","text":" - Announcements
- Review action items from last meeting
- Project Annual Reviews
- SD-JWT Kotlin
- VC-API
- Wallet Framework .NET Annual Review
- Architecture SIG Q4 Update
- Credential Format Comparison SIG Q4 Update
- Open discussion and next steps
"},{"location":"meetings/2024/2024-10-16/#links","title":"Links","text":""},{"location":"meetings/2024/2024-10-16/#tac-voting-members","title":"TAC Voting Members","text":" - David Zeuthen
- Jaehoon (Ace) Shim
- Rolson Quadras
- Pete Cooling
- Stavros Kounis
- Stephen Curran
- Tracy Kuhrt
- Wenjing Chu
"},{"location":"meetings/2024/2024-10-16/#action-items","title":"Action Items","text":" - Reach out to Wallet Framework .NET maintainers about annual review - Tracy
"},{"location":"meetings/2024/2024-10-16/#meeting-minutes","title":"Meeting Minutes","text":" -
Announcements
- Please see the OpenWallet Foundation calendar for a list of upcoming meetings
- OpenWallet Foundation Newsletter: Coming soon
- ACA-Py Overview Meetup: in progress
- October IIW Attendance - if you will not be able to attend the TAC meeting on October 30th due to IIW attendance, please let us know
- Please submit any code proposals using the process defined at https://github.com/openwallet-foundation/project-proposals. We will review proposals in the order submitted at a TAC meeting. If you know of any potential projects that might be of interest to the OpenWallet Foundation, please let a staff member know so that they can follow up
- Brian informed the TAC that he would be moving on from the OpenWallet Foundation at the end of this month
-
Review action items from last meeting
- Review Annual Reviews offline - all
- Onboard new lab - working with the project formation team on naming and project charter
- Onboard new SIG - working with the co-chairs to get the meeting set up on the OWF calendar for the week of November 4
-
Project Annual Reviews
-
Architecture SIG Q4 Update
- Tracy provided an update on the Architecture SIG progress
- The main progress is the merge of the Universal Wallet Architecture Whitepaper, which Tracy quickly highlighted
- Next steps are to complete the project mappings for Credo and Bifold
-
Credential Format Comparison SIG Q4 Update
- Mirko provided an update on the Credential Format Comparison SIG
- There is not much interest in the SIG with attendees at the meeting
- The Wallet and Agents Overview SIG depends on the content from this SIG
- A couple of suggestions were made:
- Disband the SIG - This was not desired given the dependency on the content from the Wallet and Agents Overview SIG
- Combine the two SIGs - Ecosystem Comparison SIG
- Convert the SIGs into a lab so that the work on the contents of these two SIGs could be merged into a single project
-
Open discussion and next steps
-
Next TAC Meeting October 30, 2024
- Wallet Framework .NET Annual Review
- Identity Library Annual Review
-
November 13, 2024 Meeting
- Wallet and Agents Overview SIG Q4 Update
"},{"location":"projects/","title":"Projects","text":"Projects in the OpenWallet Foundation follow the project lifecycle. This page lists the active projects within the OpenWallet Foundation and their current lifecycle stage.
"},{"location":"projects/#active-projects","title":"Active Projects","text":"Approval Date Project Name Lifecycle Stage 2023-May-17 SD-JWT Kotlin Lab 2023-May-17 SD-JWT Python Lab 2023-Aug-09 Farmworker Wallet OS Lab 2023-Sep-28 VC API Lab 2023-Oct-04 Wallet Framework .NET Lab 2023-Oct-18 Identity Credential Lab 2023-Nov-01 SD-JWT JavaScript Lab 2023-Nov-15 SD-JWT Rust Lab 2023-Nov-29 SD-JWT .NET Lab 2023-Nov-29 Credo Growth 2024-Jan-24 Multiformat VC for iOS Lab 2024-Feb-21 Bifold Growth 2024-Apr-17 EUDI Wallet Kit React Native Lab 2024-May-15 Trust Spanning Protocol Lab 2024-May-15 Tuvali Lab 2024-May-29 Credhub Lab 2024-Jun-12 MDL JavaScript Lab"},{"location":"projects/bifold/","title":"Bifold","text":""},{"location":"projects/bifold/#project-description","title":"Project Description","text":"Bifold is an open-source project designed to enhance the way we interact with digital identities, making the process both secure and user-friendly. It is based on React Native, which lets it run smoothly on different devices and platforms, such as iOS, and Android. It is a leading example of digital wallets, with a focus on making verifiable credentials (VCs) simple and convenient for everyone. Our mission is to create a collaborative community that enhances the way digital credentials are handled, making them accessible and straightforward for all.
Key Features and Benefits:
-
Unified Digital Identity Management: Emphasizing security and user-friendliness, Bifold excels in consolidating and managing digital identities across various standards like AnonCreds and W3C VC Data Model. This capability positions Bifold as a pivotal resource for secure and private handling of digital identities, accessible to all.
-
Seamless Multi-Platform Use: Thanks to its React Native architecture, Bifold delivers a smooth experience on any device, enabling users to manage their digital identities whether they are using a phone or a tablet. This cross-platform flexibility means that developers can create applications once and deploy them on both iOS and Android, ensuring a consistent and accessible user experience.
-
Community-Driven Development: Bifold is more than a tool; it's a community initiative aimed at fostering collaboration and sharing innovations. By bringing together diverse groups, from organizations to individuals, Bifold encourages the pooling of resources and knowledge to facilitate the broader adoption and understanding of verifiable credentials.
-
Widespread Adoption and Trust: With a growing list of users around the globe, including governmental bodies in Canada and teams in Brazil, Bifold has proven its reliability and relevance. Its international use showcases the platform's adaptability to various needs and its role in advancing digital identity management on a global scale.
-
Adaptability to Diverse Needs: Bifold's design caters to a wide range of project types and complexities, offering tailored solutions for managing digital identities. This adaptability ensures that users can streamline their processes related to verifiable credentials, improving efficiency and simplification in digital identity initiatives.
"},{"location":"projects/bifold/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation/bifold-wallet
- openwallet-foundation/mobile-wallet-test-harness
"},{"location":"projects/bifold/#chat-channel","title":"Chat Channel","text":" - #bifold on the OpenWallet Foundation Discord server
"},{"location":"projects/bifold/#history","title":"History","text":" - Proposal to enter Growth stage -- Approved by TAC on 2024-02-21
"},{"location":"projects/credhub/","title":"Credhub","text":""},{"location":"projects/credhub/#project-description","title":"Project Description","text":"When talking about wallets for natural persons, a lot of people think that a smartphone based wallet is the only way to go. The user should feel the security and privacy by being independent from an external provider. But we are forgetting that online based services have a great user experience in daily life: - As a user I can use multiple clients where my data is synced, we do not have to care about backups or data recovery. - As a developer I can implement the business logic into the cloud and only need the rendering on the client side.
Yes, when I am offline, I do not have access to my data anymore. But beside that the user experience is great!
The credhub project is a typescript based monorepo, using nx to manage multiple components. Compared to other approaches, it also comes with an issuer and verifier service to issue and verify credentials.
"},{"location":"projects/credhub/#clients","title":"Clients","text":"There are two clients that can be used to interact with a cloud wallet - a PWA based on Angular - a Chrome Browser Extension based on Angular
While the PWA is using the camera to scan QR codes, the browser extension is scanning the opened taps for QR codes and is able to show a little button next to the QR code to interact with the wallet. This approach was inspired by password managers like 1Password. In the daily use, People do not want to take out their smartphone to scan a QR code, they want an easy one click solution.
By implementing the whole business logic in the cloud, the client is only responsible for the rendering. Therefore building new clients in other programming languages is easy by using the OpenAPI endpoints. For authentication the OpenID Connect protocol is used, the project is using the Keycloak server for that.
"},{"location":"projects/credhub/#issuer-and-verifier","title":"Issuer and Verifier","text":"Both relying parties are implemented as separate services, each of them comes with a web client for demo purposes. Further integration like webhooks or other services can be implemented in the future. The authentication is done by using the OpenID Connect protocol.
"},{"location":"projects/credhub/#modular-approach","title":"Modular approach","text":"The usage of NX allows reusable components with a modular approach. Each backend implementation supports low security key management by storing the keys in the filesystem or the database, or the integration with Hashicorp Vault for high security key management. Other implementations are possible.
"},{"location":"projects/credhub/#identity-stack","title":"Identity Stack","text":"By validating existing SSI frameworks like Credo or Veramo, this project should primary focus on the architecture reference framework of the EU. Therefore other credential formats, transport protocols or key managements like multiple DIDs methods are not supported.
Credential Profile:
- Credential Format: SD-JWT-VC
- Key Management (issuer): VC-ISSUER Meta data, DID, X509
- Key Management (holder): CNF (json web key)
- Transport Protocol: OID4VC
- Signature Algorithm: P-256
- Status Management: OAUTH Status List
"},{"location":"projects/credhub/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/credhub
"},{"location":"projects/credhub/#chat-channel","title":"Chat Channel","text":" - #credhub on the OpenWallet Foundation Discord server
"},{"location":"projects/credhub/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2024-05-29
"},{"location":"projects/credo-ts/","title":"Credo","text":""},{"location":"projects/credo-ts/#project-description","title":"Project Description","text":"Credo has evolved significantly since its inception as a Hyperledger Aries project. Initially, it heavily relied on Hyperledger standards such as DIDComm, Indy, and AnonCreds. However, with advancements in verifiable credential technology and the emergence of new standards, the framework underwent multiple refactoring and modularization processes to maintain interoperability.
This allowed for the inclusion of non-Hyperledger standards like W3C Verifiable Credentials with Data Integrity Proofs, DIF Presentation Exchange, OpenID4VC, and SD-JWT integration. As industry requirements shifted towards greater modularity, it became apparent that a unified framework may be better.
The future direction for Credo involves adopting a compartmentalized approach consisting of single-purpose libraries designed to work together seamlessly, building on what is already out there. This transition will take considerable effort and will, therefore, be gradual.
In order to expand the framework's support for standards beyond the Hyperledger ecosystem, a reassessment of its governance was necessary. The OpenWallet Foundation (OWF) was chosen as a steward due to its commitment to promoting interoperability without directly developing or maintaining standard protocols.
"},{"location":"projects/credo-ts/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation/credo-ts
- openwallet-foundation/credo-ts-ext
- openwallet-foundation/credo-ts-docs
"},{"location":"projects/credo-ts/#chat-channel","title":"Chat Channel","text":" - #credo on the OpenWallet Foundation Discord server
"},{"location":"projects/credo-ts/#history","title":"History","text":" - Proposal to enter Growth stage -- Approved by TAC on 2023-11-29
"},{"location":"projects/eudi-wallet-kit-react-native/","title":"EUDI Wallet Kit React Native","text":""},{"location":"projects/eudi-wallet-kit-react-native/#project-description","title":"Project Description","text":"The project is a cross-platform React Native wrapper for EUDI Wallet reference implementation.
It allows building cross-platform Mobile Wallet applications compliant with Electronic Identification, Authentication and Trust Services (eIDAS) Regulation and EUDI Architecture and Reference Framework (ARF) and based on reference implementations from EUDI (Android and iOS correspondingly).
"},{"location":"projects/eudi-wallet-kit-react-native/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/eudi-wallet-kit-react-native
"},{"location":"projects/eudi-wallet-kit-react-native/#chat-channel","title":"Chat Channel","text":" - #eudi-wallet-kit-react-native on the OpenWallet Foundation Discord server
"},{"location":"projects/eudi-wallet-kit-react-native/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2024-04-17
"},{"location":"projects/fwos/","title":"Farmworker Wallet OS","text":""},{"location":"projects/fwos/#project-description","title":"Project Description","text":"The Farmworker Wallet OS project is a community of contribution led by Entidad and the United Farm Workers Foundation (UFWF) with the goal of furthering the adoption of an open, secure, interoperable digital wallet engine that makes it easier for farmworker communities to access an ecosystem of life-altering social and human services.
Farmworkers are the backbone of global food supply chains, yet they remain one of the most underserved segments of our population. Governments around the world deemed them \u2018Essential\u2019 during the recent pandemic. While services and programs exist to help, it\u2019s challenging and costly for organizations that provide them to securely collect and verify the information needed to prove applicant eligibility claims. As a result, most farmworkers forego services and resources they need, even though they\u2019re eligible for them.
Over the last three years, Entidad and the UFW Foundation have been exploring digital trust technologies to solve this problem. We\u2019ve developed PrepareseTM, a digital infrastructure solution that lets farmworker organizations securely reuse verified farmworker information, eliminating the need for repetitive collection. The solution layers didcomm, wallet, decentralized identifiers, and verifiable credential technologies with a low-code application development platform, Mendix.
Mendix has been a key component in making the PrepareseTM solution possible. Low-code software development has been growing in popularity and bringing new audiences to the practice.\u202fMendix, one of the more popular platforms with over 300K active developers and 50M users, has enabled Entidad and the UFW Foundation to develop, launch, and maintain enterprise-grade digital trust enabled solutions that solve real world problems.
We\u2019ve built two products, using this technology. For organizations we\u2019ve built Preparese PlatformTM, it allows them to quickly develop and launch digital trust enabled services and programs. For farmworkers, we\u2019ve developed Preparese MobileTM which combines a verifiable digital profile with a suite of tools that simplify interactions with organizations on the platform.
The Preparese PlatformTM is being used by 9 organizations and has 5 digital services in production. The most recent service launched is being used to process and distribute $80 million in one-time relief payments to over 125,000 workers, under the United States Department of Agriculture\u2019s Farm and Food Workers Relief Program (FFWR).
The second product, Preparese MobileTM, is designed around the unique needs of farmworkers. We\u2019ve developed a react native mobile app that lets farmworkers store, manage, and exchange their verified information. Engagement with organizations is made easier with DIDComm-based communication capabilities such as text and video chat.
One of the cornerstone technologies of the solution is an interoperable Mendix enabled digital wallet. The wallet components need to be able to engage with various non-profit, government, and philanthropic sources, each with their own technology stacks. For this reason, interoperability and working with open standard frameworks has been a priority. The project team members have participated in TrustOverIP Foundation, Hyperledger Aries JS Working Group, and various other communities, including DID Communication Working Group and OpenWallet Foundation of late, to ensure we adhere to best practices and standards.
While currently focused on farmworkers, the Mendix digital wallet engine can be used to help others. There are many other underserved communities that could benefit greatly from the privacy, accessibility, and security digital wallets can provide. With this social impact purpose in mind and spirit of further collaboration, Entidad and the UFW Foundation propose to open source the digital wallet engine used in their PrepareseTM solution. By making these resources available, we hope to facilitate a wide variety of social impact.
Additionally, the project allows us to bridge and advance the interest of both the OpenWallet Foundation and Mendix communities. By collaborating with the Mendix community, we not only have the ability to grow the number of digital trust technology practitioners, we also tap into a community with an established customer base. By making digital wallets components that can be easily integrated into their existing solutions, the project can drive further adoption and usage of interoperable, secure and privacy preserving digital wallets.
"},{"location":"projects/fwos/#origin-history","title":"Origin & History","text":"The origins of the Farmworker Wallet OS project align with those of Entidad. What began as a volunteering effort by three college friends, was formalized in 2018 with the founding of Entidad as a public benefit corporation. We have primarily been working with leading farm worker-serving organizations to develop technology that leverages growing digital literacy in their communities to scale their impact.
The first digital service launched supported the UFW Foundation\u2019s emergency relief efforts during the height of the COVID-19 pandemic. The solution was used to plan, manage and operate over 500 in-person community events where over $15 million in resources were distributed to over 40K families. Additionally, it has allowed us to better understand the unique challenges of building for underserved communities and why interoperable, secure, and privacy preserving technologies are key to addressing these challenges.\u202f
You can read more about our journey on our blog.
"},{"location":"projects/fwos/#external-dependencies","title":"External Dependencies","text":"Mendix is a low-code application platform provider so its terms of service cover usage of Mendix services and resources by Mendix developers (organizations and/or individual contributors). The Application model for a standards compliant wallet engine will be the primary focus for the contributors of this project. The Mendix terms of service do protect the IP rights to these App models in Section 3 with reference to \"Customer Data\" definition in section 17.
There are design-time and runtime aspects of app development but one of the great things about this tooling is that there is clean separation between the two.
The following captures the developer's \"design-time\" perspective. We hope that the diagram helps to clarify the software components that would fall under the scope of this OWF project and distinguishes PrepareseTM as an example of a closed (proprietary) application that embeds core Farmworker WalletOS components. We plan on documenting a similar diagram to aid in understanding the \"runtime\" perspective soon.
- Mendix Studio Pro v9.24.4 (integrated developer environment)
- Eclipse Temurin JDK 11 (x64)
- Mendix Native Template v7.0.1
- React Native v0.70.7
- Hyperledger / Aries-Framework-Javascript v0.4.0
- Development instance of an Aries Mediator Service
- Development instance of an Aries Cloud Agent
"},{"location":"projects/fwos/#infrastructure","title":"Infrastructure","text":"The Farmworker Wallet OS will be organized and published as a suite of software modules that can be imported into any existing Mendix app code repository. The Mendix software modules effectively serve as a digital wallet SDK that can be embedded into any Mendix application to enhance the user experience. The code repository for this project is itself a Mendix app repository and as such can be executed locally on any supported developer workstation.
The initial version of the digital wallet SDK is being built on top of Aries Framework Javascript, an open-source framework maintained by the Hyperledger Aries developer community helping to foster participation with the Aries digital trust ecosystem. Over time, the digital wallet SDK will be extended to support other digital trust open standards such as OpenID for Verifiable Credentials (OID4VC).
"},{"location":"projects/fwos/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/fwos-demo-app
- openwallet-foundation-labs/fwos-native-template
"},{"location":"projects/fwos/#chat-channel","title":"Chat Channel","text":" - #fwos on the OpenWallet Foundation Discord server
"},{"location":"projects/fwos/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2023-08-09
"},{"location":"projects/identity-credential/","title":"Identity Credential","text":""},{"location":"projects/identity-credential/#project-description","title":"Project Description","text":"Libraries and reference applications for working with real-world identity.
The initial focus for this work was mdoc/mDL according to ISO/IEC 18013-5:2021 and related standards (mainly ISO 23220 series and ISO 18013-7) on Android. Current focus includes other credential formats and operating environments.
"},{"location":"projects/identity-credential/#libraries","title":"Libraries","text":"The project includes two libraries written in Java and Kotlin. The first is identity which provides the core building blocks and which can also be used on server-side environments. The other is identity-android which provides Android-specific extensions to the former. It is designed to run on Android (API 24 or later) and will take advantage of Android-specific features including hardware-backed Keystore, NFC, Bluetooth Low Energy, and so on.
The libraries are intended to be used by Wallet Applications (mobile applications on the credential holder's device), Reader Applications (applications operated on device controlled by the verifier), and Issuance Systems (applications operated by the credential issuer or their agent). They provide the following building blocks
- A light-weight Secure Area abstraction for hardware-backed keystore
- Applications can create hardware-backed Elliptic Curve Cryptography keys which can be used for creating Signatures or performing Key Agreement. Each key will have an attestation which can be used to prove to Relying Parties (such as a credential issuer) that the private part of the key only exists in a Secure Area.
- The
identity-android library includes an implementation based on Android Keystore with support for requiring user authentication (biometric or lock-screen knowledge factor, e.g. system PIN) for unlocking the key and also can use StrongBox if available on the device. This is appropriate to use in Android applications implementing ISO/IEC 18013-5:2021 for storing DeviceKey. - The
identity library includes an implementation backed by BouncyCastle with support for passphrase-protected keys. This isn't suitable for use in Mobile Applications as its not backed by Secure Hardware. - Applications can supply their own Secure Area implementations for e.g. externally attached dongles, cloud based HSMs, or whatever the issuer deems appropriate to protect key material associated with their credential.
- A Credential Store for storage of one or more Credentials
- Each Credential has a Credential Key which can be used by the issuer to bind a credential to a specific device which is useful when issuing updates or refreshing a credential.
- Additionally, each Credential has one or more Authentication Keys which can be endorsed by the issuer and used at presentation time.
- Finally, namespaced data and arbitrary key/value pairs can be stored in a Credential which can be used for credential data and claims. This data is stored encrypted at rest.
- Data structures and code for provisioning of mdoc/mDLs
- This code can can be used both on the device and issuer side. No networking protocol is defined, the application has to define its own.
- Parsers and generators for all data structures used in ISO/IEC 18013-5:2021 presentations, including
DeviceResponse, DeviceRequest, MobileSecurityObject and many other CBOR data structures. - An implementation of the ISO/IEC 18013-5:2021 presentation flows including QR engagement, NFC engagement (both static and negotiated), device retrieval (BLE, Wifi Aware, and NFC)
"},{"location":"projects/identity-credential/#wallet-and-reader-android-applications","title":"Wallet and Reader Android applications","text":"This repository also contains two Android applications using this library in the appholder and appverifier modules. The Wallet application is a simple self-contained application which allows creating a number of mdoc credentials using four different mdoc Document Types:
org.iso.18013.5.1.mDL: Mobile Driving Licenseorg.micov.1: mdoc for eHealth (link)nl.rdw.mekb.1: mdoc for Vehicle Registration (link)eu.europa.ec.eudiw.pid.1: mdoc for Personal Identification
and their associated mdoc name spaces. The first one is defined in ISO/IEC 18013-5:2021 and the other three have been used at mdoc/mDL test events organized by participants of the ISO/IEC JTC1 SC17 WG10 working group.
"},{"location":"projects/identity-credential/#iso-18013-7-reader-website","title":"ISO 18013-7 Reader Website","text":"The wwwverifier module contains the source code for a website acting as an mdoc reader according to the latest ISO 18013-7 working draft (as of Sep 2023) and it's implementing the so-called REST API. There is currently a test instance of this application available at https://mdoc-reader-external.uc.r.appspot.com/. The Wallet Android application also has support for the REST API and registers on Android for the mdoc:// URI scheme. This can be tested end-to-end by going to the reader website (URL above) and clicking on one of the \"Request\" buttons, and then hitting the mdoc:// link presented on the site. This will cause the browser to invoke the Wallet app which will then connect to the reader and send the credential after user consent.
"},{"location":"projects/identity-credential/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/identity-credential
"},{"location":"projects/identity-credential/#chat-channel","title":"Chat Channel","text":" - #identity-credential on the OpenWallet Foundation Discord server
"},{"location":"projects/identity-credential/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2023-10-18
"},{"location":"projects/mdl-js/","title":"MDL JavaScript","text":""},{"location":"projects/mdl-js/#project-description","title":"Project Description","text":"This is a Typescript(Javascript) implementation of the ISO 18013-5:2021 (MDL) specification. This project aims to provide a platform agnostic implementation of the MDL specification.
To provide MDL features to Biggest Wallet SDKs like Credo or Veramo, the direction of the project will be:
Provide a platform agnostic implementation of the MDL specification - Bring your own crypto - Modular approach - Provide platform specific helper implementations for developers to use easily
"},{"location":"projects/mdl-js/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/mdl-js
"},{"location":"projects/mdl-js/#chat-channel","title":"Chat Channel","text":" - #mdl-js on the OpenWallet Foundation Discord server
"},{"location":"projects/mdl-js/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2024-06-12
"},{"location":"projects/multiformat-vc-ios/","title":"Multiformat VC for iOS","text":""},{"location":"projects/multiformat-vc-ios/#project-description","title":"Project Description","text":"Pure Swift package for creating Verifiable Credentials (VCs) in multiple formats
- SD-JWT VC: Selective Disclosure JWT based Verifiable Credentials - using the specification defined at https://datatracker.ietf.org/doc/draft-ietf-oauth-sd-jwt-vc/
- VC JWT: Verifiable Credentials as JWT - using the format defined at JWT VC Presentation Profile https://identity.foundation/jwt-vc-presentation-profile/
Support for multiple data types for disclosed values including
- String
- Int
- Boolean
- Array of Strings - [String]
- Dictionary of String keys and String values - [String:String]
This project is a contribution of the work done at Ping Identity to test and establish interoperability of the various formats representing the Verifiable Credentials Data Model https://www.w3.org/TR/vc-data-model/. Along with the SD-JWT VC and JWT VC formats described above, Ping Identity has also participated in the interoperability event for OpenID4VP to present a VC JWT. That code will also be released as a part of this project.
"},{"location":"projects/multiformat-vc-ios/#source-repositories","title":"Source Repositories","text":"openwallet-foundation-labs/multiformat-vc-ios
"},{"location":"projects/multiformat-vc-ios/#chat-channel","title":"Chat Channel","text":" - #multiformat-vc-ios on the OpenWallet Foundation Discord server
"},{"location":"projects/multiformat-vc-ios/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2024-01-24
"},{"location":"projects/sd-jwt-dotnet/","title":"SD-JWT .NET","text":""},{"location":"projects/sd-jwt-dotnet/#project-description","title":"Project Description","text":"A .NET implementation of the Selective Disclosure for JWTs (SD-JWT) specification.
"},{"location":"projects/sd-jwt-dotnet/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/sd-jwt-dotnet
"},{"location":"projects/sd-jwt-dotnet/#chat-channel","title":"Chat Channel","text":" - #sd-jwt-dotnet on the OpenWallet Foundation Discord server
"},{"location":"projects/sd-jwt-dotnet/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2023-11-29
"},{"location":"projects/sd-jwt-js/","title":"SD-JWT JavaScript","text":""},{"location":"projects/sd-jwt-js/#project-description","title":"Project Description","text":"A JavaScript implementation of the Selective Disclosure for JWTs (SD-JWT) specification.
"},{"location":"projects/sd-jwt-js/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/sd-jwt-js
"},{"location":"projects/sd-jwt-js/#chat-channel","title":"Chat Channel","text":" - #sd-jwt-js on the OpenWallet Foundation Discord server
"},{"location":"projects/sd-jwt-js/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2023-11-01
"},{"location":"projects/sd-jwt-kotlin/","title":"SD-JWT Kotlin","text":""},{"location":"projects/sd-jwt-kotlin/#project-description","title":"Project Description","text":"A Kotlin implementation of the Selective Disclosure for JWTs (SD-JWT) specification.
"},{"location":"projects/sd-jwt-kotlin/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/sd-jwt-kotlin
"},{"location":"projects/sd-jwt-kotlin/#chat-channel","title":"Chat Channel","text":" - #sd-jwt-kotlin on the OpenWallet Foundation Discord server
"},{"location":"projects/sd-jwt-kotlin/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2023-05-17
"},{"location":"projects/sd-jwt-python/","title":"SD-JWT Python","text":""},{"location":"projects/sd-jwt-python/#project-description","title":"Project Description","text":"This is the reference implementation of the IETF SD-JWT specification maintained by the editors of the specification together with other contributors. It is written in Python.
"},{"location":"projects/sd-jwt-python/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/sd-jwt-python
"},{"location":"projects/sd-jwt-python/#chat-channel","title":"Chat Channel","text":" - #sd-jwt-python on the OpenWallet Foundation Discord server
"},{"location":"projects/sd-jwt-python/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2023-05-17
"},{"location":"projects/sd-jwt-rust/","title":"SD-JWT Rust","text":""},{"location":"projects/sd-jwt-rust/#project-description","title":"Project Description","text":"A Rust implementation of the Selective Disclosure for JWTs (SD-JWT) specification.
"},{"location":"projects/sd-jwt-rust/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/sd-jwt-rust
"},{"location":"projects/sd-jwt-rust/#chat-channel","title":"Chat Channel","text":" - #sd-jwt-rust on the OpenWallet Foundation Discord server
"},{"location":"projects/sd-jwt-rust/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2023-11-15
"},{"location":"projects/tsp/","title":"Trust Spanning Protocol","text":""},{"location":"projects/tsp/#project-description","title":"Project Description","text":"This project is an early impementation of the draft Trust Spanning Protocol (TSP).
According to the above referenced specification, \"The Trust Spanning Protocol (TSP) facilitates secure communication between endpoints with potentially different identifier types, using message-based exchanges. As long as these endpoints use identifiers based on public key cryptography (PKC) with a verifiable trust root, TSP ensures their messages are authentic and, if optionally chosen, confidential. Moreover, it presents various privacy protection measures against metadata-based correlation exploitations. These attributes of TSP together allow endpoints to form authentic relationships rooted in their respective verifiable identifiers (VIDs), viewing TSP messages as virtual channels for trustworthy communication.\"
A shorter introduction of TSP can be found in this blog post.
This project's current code includes a Rust implementation of all TSP features. We also plan to incorporate/develop related features such as additional Verifiable Identifier types, additional transport layer mechanisms, different language bindings as needed and integration modules needed to be compatible with other OpenWallet projects.
In addition, we may add and welcome trust task or application specific extensions.
"},{"location":"projects/tsp/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/tsp
"},{"location":"projects/tsp/#chat-channel","title":"Chat Channel","text":" - #tsp on the OpenWallet Foundation Discord server
"},{"location":"projects/tsp/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2024-05-15
"},{"location":"projects/tuvali/","title":"Tuvali","text":""},{"location":"projects/tuvali/#project-description","title":"Project Description","text":"A library which implements the OpenID4BLE specification for Android and IOS. It's written in Kotlin and Swift.
"},{"location":"projects/tuvali/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/tuvali
"},{"location":"projects/tuvali/#chat-channel","title":"Chat Channel","text":" - #tuvali on the OpenWallet Foundation Discord server
"},{"location":"projects/tuvali/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2024-05-15
"},{"location":"projects/vc-api/","title":"VC API","text":""},{"location":"projects/vc-api/#project-description","title":"Project Description","text":"The VC API is specification for a set of APIs for VC lifecycle management (https://w3c-ccg.github.io/vc-api/). This includes operations such as credential issuance, verification, and exchange. It is a W3C CCG work item and, as of the submission of this proposal, it is in \u201cdraft community report\u201d status.
The VC API\u2019s design is informed by use cases across a range of domains. Several of these use cases are collected in a working group note (https://w3c-ccg.github.io/vc-api-use-cases/).
This project is an implementation of the VC API. The implementation aims to enable organizations and individuals to effortlessly conduct SSI operations over HTTP without requiring technical expertise, making it seamless to integrate into existing projects.
"},{"location":"projects/vc-api/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/vc-api
"},{"location":"projects/vc-api/#chat-channel","title":"Chat Channel","text":" - #vc-api on the OpenWallet Foundation Discord server
"},{"location":"projects/vc-api/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2023-09-28
"},{"location":"projects/wallet-framework-dotnet/","title":"Wallet Framework .NET","text":""},{"location":"projects/wallet-framework-dotnet/#project-description","title":"Project Description","text":"The wallet-framework-dotnet is a framework designed for .NET, focusing on providing a multi-platform wallet framework. Initially a part of the Hyperledger Aries project (Aries Framework .NET), this initiative has now branched out to cater to a broader audience. The primary aim is to create a multiprotocol wallet framework enabling implementations of OpenID4VC and SD-JWT VC, in accordance to the European Identity Wallet initiative's objectives.
Currently, the framework supports DidComm v1 and AnonCreds. There is an active intention to extend support for other promising protocols, notably DidComm v2, to ensure the framework remains at the forefront of digital identity solutions.
Furthermore, the team is considering the development of SD-JWT credentials as a standalone library. This might transition into a separate project proposal in the future, underscoring the commitment to modular and reusable components in the digital identity space.
"},{"location":"projects/wallet-framework-dotnet/#source-repositories","title":"Source Repositories","text":" - openwallet-foundation-labs/wallet-framework-dotnet
"},{"location":"projects/wallet-framework-dotnet/#chat-channel","title":"Chat Channel","text":" - #wallet-framework-dotnet on the OpenWallet Foundation Discord server
"},{"location":"projects/wallet-framework-dotnet/#history","title":"History","text":" - Proposal to enter Labs -- Approved by TAC on 2023-10-04
"},{"location":"projects/dashboards/","title":"OpenWallet Foundation Dashboards","text":""},{"location":"projects/dashboards/labs/","title":"openwallet-foundation-labs Dashboard","text":"Repo License Last Commit Commits Issues Pull Requests OpenSSF Scorecard Stars Forks Watchers .github credhub eudi-wallet-kit-react-native farmworker-wallet-os governance identity-credential multiformat-vc-ios sd-jwt-dotnet sd-jwt-js sd-jwt-kotlin sd-jwt-python sd-jwt-rust tsp vc-api wallet-framework-dotnet"},{"location":"projects/dashboards/owf/","title":"openwallet-foundation Dashboard","text":"Repo License Last Commit Commits Issues Pull Requests OpenSSF Scorecard Stars Forks Watchers .github architecture-sig bifold-wallet credential-format-comparison-sig credo-ts credo-ts-docs credo-ts-ext digital-wallet-and-agent-overviews-sig governance mobile-wallet-test-harness project-proposals safe-wallet-sig tac"},{"location":"projects/reviews/0000-template-annual/","title":"YYYY PROJECT NAME","text":"Info
Copy this template to the subdirectory for the current year and name the file YYYY-project-name-annual.md (e.g., 2024-amazingproj-annual.md). Update the title above to replace YYYY with the year of the annual review and PROJECT NAME with the name of the project. Update the index.md file in the current year to include a link to the markdown file. These blocks are instructions. Please remove when section has been completed.
"},{"location":"projects/reviews/0000-template-annual/#project-health","title":"Project Health","text":"Info
Include information about your project's contributions and activity. You can find information within GitHub by looking at the Insights tab. We will be looking for signs of consistent or increasing contribution activity. Please feel free to add commentary to add color to this information.
"},{"location":"projects/reviews/0000-template-annual/#maintainer-diversity","title":"Maintainer Diversity","text":"Info
How many maintainers do you have, and which organisations are they from? How has the maintainers and diversity of your maintainers changed in the past year? Has the number of active maintainers increased/decreased? Has the diversity of maintainers increased/decreased? Please include a link to your existing MAINTAINERS file and the MAINTAINERS file from last year (if appropriate). This is a good opportunity to ensure that your MAINTAINERS file is up to date and to retire any maintainers.
"},{"location":"projects/reviews/0000-template-annual/#project-adoption","title":"Project Adoption","text":"Info
What do you know about adoption, and how has this changed since your last review or since being accepted into OpenWallet Foundation? If you can list companies that are adopters of your project, please do so. Feel free to link to an existing ADOPTERS file if appropriate.
"},{"location":"projects/reviews/0000-template-annual/#goals","title":"Goals","text":""},{"location":"projects/reviews/0000-template-annual/#performance-against-prior-goals","title":"Performance Against Prior Goals","text":"Info
Include information about the goals that you previously set for the project in the last review or since the project proposal has been approved. How has the project performed against these goals? If your goals changed from your previous annual report, let us know what changed and why. If you have not achieved the goals that you set out, that is okay. We want to know what you have accomplished and what challenges the project is having in meeting the goals.
"},{"location":"projects/reviews/0000-template-annual/#next-years-goals","title":"Next Year's Goals","text":"Info
What are the goals for the next year of the project? The goals should list what you want to achieve, not just what you know you can achieve. Feel free to include stretch goals and things that you are looking to explore in the next year. For example, are you working on major new features? Or are you concentrating on adoption, community growth, or documentation?
"},{"location":"projects/reviews/0000-template-annual/#help-required","title":"Help Required","text":"Info
How can the OpenWallet Foundation or the TAC help you achieve your upcoming goals?
"},{"location":"projects/reviews/0000-template-annual/#project-lifecycle-stage-recommendation","title":"Project Lifecycle Stage Recommendation","text":"Info
What stage do you think the project should be? If you you think that your project meets the criteria for another stage, please explain why.
"},{"location":"projects/reviews/2024/","title":"2024 Project Annual Reviews","text":"Projects must provide an annual review to the TAC to ensure that the project is still active and in the correct lifecycle stage. The following calendar provides the timing for when these reviews are required to be presented to the TAC:
Project Stage Date Accepted 2024 Review SD-JWT Python Labs May 27, 2023 Jun 12, 2024 SD-JWT Kotlin Labs May 27, 2023 Jun 12, 2024 Farmworker Wallet OS Labs Aug 9, 2023 Aug 21, 2024 VC-API Labs Sep 28, 2023 Oct 2, 2024 Wallet Framework .NET Labs Oct 4, 2023 Oct 16, 2024 Android Identity Library Labs Oct 18, 2023 Oct 30, 2024 SD-JWT JavaScript Labs Nov 1, 2023 Nov 13, 2024 SD-JWT Rust Labs Nov 15, 2023 Nov 27, 2024 Credo Growth Nov 29, 2023 Dec 11, 2024 SD-JWT .NET Labs Nov 29, 2023 Dec 11, 2024"},{"location":"projects/reviews/2024/2024-farmworker-wallet-os-annual/","title":"2024 Farmworker Wallet OS (FWOS)","text":""},{"location":"projects/reviews/2024/2024-farmworker-wallet-os-annual/#project-health","title":"Project Health","text":"The Farmworker Wallet OS is an ecosystem of modules that enable the development of a Native Wallet Agent and a Cloud Wallet Agent in the low-code platform Mendix. The FWOS project remains healthy and active with one reference implementation deployed to a production environment and a second implementation soon to be released in Q3. As noted in our original project proposal, the FWOS project has been focused on building interoperability with Aries digital trust ecosystems. We continue to build our low-code SDK components on top of Credo and have completed ~90% coverage of Aries Interoperability Profiles 1 and 2. To date, the project has successfully completed 4 upgrades of the Credo toolkit (v0.4.2, v0.5.3, v0.5.6, v0.5.9) and are actively working on the upgrade to v0.5.10. This is important as it highlights the ability for this project to stay up to speed with the rapid rate of change of the underlying standards and open-source toolkits that this project depends on.
"},{"location":"projects/reviews/2024/2024-farmworker-wallet-os-annual/#maintainer-diversity","title":"Maintainer Diversity","text":"Contributions to the FWOS have been primarily from the Entidad development team. A couple of inquiries have come in via the project Discord channel with interest in participation but we have no concrete knowledge of any work done outside of the contributions from the project maintainers. We did add a new maintainer internally who helped us with the implementation of the DIDComm Survey protocol recently submitted as a proposal. This demonstrates that an experienced Mendix developer is able to learn and understand the underlying Aries and DIDComm architectures and contribute to the implementation of a new DIDComm protocol after only a few weeks of knowledge transfer and experimentation.
"},{"location":"projects/reviews/2024/2024-farmworker-wallet-os-annual/#project-adoption","title":"Project Adoption","text":"The FWOS project has one reference implementation deployed to a production environment in February 2024. This release consisted of a mobile agent implemented on version 0.4.2 of the open-source Aries Framework JavaScript (AFJ) toolkit. Note that AFJ rebranded to Credo after it was accepted into the OpenWallet Foundation. Although no digital trust interactions were enabled outside of wallet onboarding and agent initialization, this first release was significant as it allowed us to demonstrate the viability of having the FWOS wallet engine running at scale within the target end-user community.
"},{"location":"projects/reviews/2024/2024-farmworker-wallet-os-annual/#goals","title":"Goals","text":""},{"location":"projects/reviews/2024/2024-farmworker-wallet-os-annual/#performance-against-prior-goals","title":"Performance Against Prior Goals","text":"The goal of the Farmworker Wallet OS project is to promote the adoption of mobile (native) and cloud wallets. We are proud of the progress achieved to date in producing a stable production ready wallet holder toolkit that enables Mendix developers to jumpstart the integration of digital trust technologies with their Mendix native apps. The following collection of trust protocols have been implemented this year:
- DID Exchange v1
- Out-of-Band Protocol v1
- Issue Credential v1
- Present proof v1
- Mediator coordination protocol v1
- Message Pickup v1
- Basic Message
- Question Answer v1
- Issue Credential v2
- Mediator coordination protocol v2
- Present proof v2
- Message Pickup v2
- Out-Of-Band Protocol v2
- Basic Message v2
- Discover Features v2
- Media Sharing
- DIDComm Remote Procedure Call
- Survey protocol proposal
- did:web AnonCreds Method
- cheqd DID Method
deprecated
For the remainder of the 2024 year, the project hopes to commence implementing support for AnonCreds presentation exchange over Bluetooth supported by:
- DIDComm over Bluetooth
- Bluetooth Low Energy transport for Credo
Additionally, the project hopes to initiate exploration and prototyping of a mobile driver's license verifier component (ISO mDL 18013-5 and ISO 18013-7: mdoc + OID4VP or Digital Credentials API).
"},{"location":"projects/reviews/2024/2024-farmworker-wallet-os-annual/#fwos-native-agent-architecture","title":"FWOS Native Agent Architecture","text":""},{"location":"projects/reviews/2024/2024-farmworker-wallet-os-annual/#next-years-goals","title":"Next Year's Goals","text":"For the next year, the FWOS project aims to introduce cloud agent components to support credential Issuer and Verifier use cases. This work is already in-progress and will be integrated formerly into the FWOS toolkit:
- DigitalID SDK
- DIDComm SDK
- AnonCreds VC SDK
- Paradym Connector
"},{"location":"projects/reviews/2024/2024-farmworker-wallet-os-annual/#fwos-cloud-agent-architecture","title":"FWOS Cloud Agent Architecture","text":""},{"location":"projects/reviews/2024/2024-farmworker-wallet-os-annual/#help-required","title":"Help Required","text":"The project is advancing steadily and does not require any help at the moment.
"},{"location":"projects/reviews/2024/2024-farmworker-wallet-os-annual/#project-lifecycle-stage-recommendation","title":"Project Lifecycle Stage Recommendation","text":"The project is recommended to remain in the Labs stage.
"},{"location":"projects/reviews/2024/2024-sd-jwt-python-annual/","title":"2024 sd-jwt-python (SD-JWT Reference Implementation)","text":""},{"location":"projects/reviews/2024/2024-sd-jwt-python-annual/#project-health","title":"Project Health","text":"The main focus of this project is to provide a reference implementation for the IETF SD-JWT draft. As such, the code has reflected the developments in the specification over the last year and is up to date with the latest version of the draft. Since the draft is approaching a stable state (and hopefully a final RFC soon-ish), no drastic changes are expected in the codebase.
"},{"location":"projects/reviews/2024/2024-sd-jwt-python-annual/#maintainer-diversity","title":"Maintainer Diversity","text":"As before, the project is maintained by a single maintainer, an editor of the SD-JWT draft. Two developers have contributed code, one editor of the draft and one external contributor.
"},{"location":"projects/reviews/2024/2024-sd-jwt-python-annual/#project-adoption","title":"Project Adoption","text":"The main task of the project is to provide a reference implementation for the SD-JWT draft. The project is in use
- by the editors of the draft to test new developments and to produce examples for the specification,
- by external contributors to understand testdrive SD-JWT, and
- as a reference for testing and validation of other implementations.
"},{"location":"projects/reviews/2024/2024-sd-jwt-python-annual/#goals","title":"Goals","text":""},{"location":"projects/reviews/2024/2024-sd-jwt-python-annual/#performance-against-prior-goals","title":"Performance Against Prior Goals","text":"The project has met its goals for the last year, which were to keep the codebase up to date with the latest version of the draft and to provide a reference implementation for the draft.
"},{"location":"projects/reviews/2024/2024-sd-jwt-python-annual/#next-years-goals","title":"Next Year's Goals","text":"As before, the main goal of the project is to provide a reference implementation for the SD-JWT draft. The project will continue to track the development of the draft, including a potential transition to an RFC. The project will also continue to exist as a reference for SD-JWT implementations.
"},{"location":"projects/reviews/2024/2024-sd-jwt-python-annual/#help-required","title":"Help Required","text":"The project is in good shape and does not require any help at the moment.
"},{"location":"projects/reviews/2024/2024-sd-jwt-python-annual/#project-lifecycle-stage-recommendation","title":"Project Lifecycle Stage Recommendation","text":"The project is recommended to remain in the Labs stage.
"},{"location":"projects/reviews/2024/2024-vc-api-implementation-annual/","title":"2024 VC API Implementation","text":""},{"location":"projects/reviews/2024/2024-vc-api-implementation-annual/#project-health","title":"Project Health","text":"The project remains healthy. Contributions for the initial portions of the year were focused on housekeeping items, however the project currently has development activity for functional and non-functional changes to increase the likelihood of further adoption and impact in the year ahead.
Contributions have been made by two organizations, Energy Web and Impactility. Several forks have been made in the past year, suggesting some initial community attention.
The underlying VC API specification (currently developed in the context of the W3C Credentials Community Group) is active and the specification group has the intention of bringing the specification to a W3C standards track in the months ahead.
"},{"location":"projects/reviews/2024/2024-vc-api-implementation-annual/#maintainer-diversity","title":"Maintainer Diversity","text":"The project currently has four maintainers, from two organizations, Energy Web & Impactility.
"},{"location":"projects/reviews/2024/2024-vc-api-implementation-annual/#project-adoption","title":"Project Adoption","text":"The project currently has one primary adoption organization, Elia Group. Elia continues to showcase the VC API project on their SSI demonstration site (https://ssi4energy.eliagroup.eu/en). This is roughly the same amount of adoption as when accepted into the OpenWallet Foundation last year.
"},{"location":"projects/reviews/2024/2024-vc-api-implementation-annual/#goals","title":"Goals","text":""},{"location":"projects/reviews/2024/2024-vc-api-implementation-annual/#performance-against-prior-goals","title":"Performance Against Prior Goals","text":"The project proposal mentioned the following aims in the \"Alignment with the OpenWallet Foundation Mission\" section: - Advance the adoption of interoperable and privacy enhancing digital wallets. - Promote the development and proliferation of the VC API specification itself
Progress towards the above objectives has been small over the past year. However, the main functional enhancement undertaken in recent months (the migration of core key & credential operations to Credo) sets up the project well for progress on the objectives in the year ahead. For example, listing in the VC Playground (https://vcplayground.org/) is an opportunity to further both of the above objectives, however this was blocked by that lack of flexibility with JSON-LD context document loading in the implementation prior to the Credo integration.
"},{"location":"projects/reviews/2024/2024-vc-api-implementation-annual/#next-years-goals","title":"Next Year's Goals","text":"The current goals of the project are to: 1. Increase use and adoption of the project, both by existing user organizations (Elia and Energy Web) and new organizations. The target metric is between 1 and 5 new organizations using the app in projects within the year. 2. Support the development of the VC API specification. 3. Provide feedback into the development of other OWF projects.
On-going and planned work items which further these goals are detailed below.
"},{"location":"projects/reviews/2024/2024-vc-api-implementation-annual/#migrating-to-credo-for-key-and-credential-operations","title":"Migrating to Credo for key and credential operations","text":"GitHub Issue: https://github.com/openwallet-foundation-labs/vc-api/issues/20
The benefits of this item include: - Synergy with an existing OWF project, allowing work on the VC API implementation to feed back into other OWF work - Examples of this are the following GitHub issues: - Credo Issue #2038- Make verifiableCredential property on W3cPresentation optional - Credo Issue #2043 - Fix W3cCredentialsApi verifyCredential types - Having a VC API wrapper for Credo would provide Credo with the interface for the VC Data Model 2.0 test suite - A note that ACA Py already offers VC API issuance and verification endpoints - The ability to use load additional JSON LD contexts, unlocking new use cases - A clearer path to supporting further VC technology such as SD-JWT and BBS signatures
Work on this item can be seen in the following PR: https://github.com/openwallet-foundation-labs/vc-api/pull/36
"},{"location":"projects/reviews/2024/2024-vc-api-implementation-annual/#improving-documentation-for-technology-adoption-decision-makers","title":"Improving documentation for technology adoption decision makers","text":"GitHub Issue: https://github.com/openwallet-foundation-labs/vc-api/issues/29
This item aims to improve the ability of technology selection decision makers, such as CTOs or Software Architects, to assess whether or not the VC API implementation is suitable for their use cases and technology context. The key output is a new documentation site.
"},{"location":"projects/reviews/2024/2024-vc-api-implementation-annual/#listing-in-the-vc-playground","title":"Listing in the VC Playground","text":"GitHub Issue: https://github.com/openwallet-foundation-labs/vc-api/issues/28
The VC Playground is a demonstration application for Verifiable Credential issuance and verification: https://vcplayground.org. Listing in the VC Playground is an opportunity to gain visibility on the project and test interoperability.
"},{"location":"projects/reviews/2024/2024-vc-api-implementation-annual/#help-required","title":"Help Required","text":"The following actions from the OWF would likely be helpful in achieving the upcoming goals: - Advice on future architectural directions, such as transforming the project into a Credo plugin - Notification on any publicity opportunities for the project
"},{"location":"projects/reviews/2024/2024-vc-api-implementation-annual/#project-lifecycle-stage-recommendation","title":"Project Lifecycle Stage Recommendation","text":"Our recommendation is to remain a Labs project.
"},{"location":"projects/reviews/2025/","title":"2025 Project Annual Reviews","text":"Projects must provide an annual review to the TAC to ensure that the project is still active and in the correct lifecycle stage. The following calendar provides the timing for when these reviews are required to be presented to the TAC:
Project Stage Date Accepted 2025 Review Multiformat VC for iOS Labs Jan 24, 2024 Feb 5, 2025 Bifold Growth Feb 21, 2024 Mar 5, 2025 EUDI Wallet Kit React Native Labs Apr 17, 2024 Apr 30, 2025 Trust Spanning Protocol Labs May 15, 2024 May 14, 2025 Tuvali Labs May 15, 2024 May 14, 2025 Credhub Labs May 29, 2024 May 28, 2025 MDL JavaScript Labs Jun 12, 2024 Jun 11, 2025 SD-JWT Python Labs May 27, 2023 SD-JWT Kotlin Labs May 27, 2023 Farmworker Wallet OS Labs Aug 9, 2023 VC-API Labs Sep 28, 2023 Wallet Framework .NET Labs Oct 4, 2023 Android Identity Library Labs Oct 18, 2023 SD-JWT JavaScript Labs Nov 1, 2023 SD-JWT Rust Labs Nov 15, 2023 Credo Growth Nov 29, 2023 SD-JWT .NET Labs Nov 29, 2023"},{"location":"task-forces/","title":"Task Forces","text":"A task force is a group that is focused on a task with limited scope and fixed time to complete. Unlike a special interest group, a task force will have a specific set of deliverables or work products that it will create and be limited in time to completion. A task force can be created by anyone in the OpenWallet Foundation community and must be proposed to and approved by the TAC.
Tip
If you would like to propose a Task Force, please see the task force proposal process.
"},{"location":"task-forces/#active-task-forces","title":"Active Task Forces","text":""},{"location":"task-forces/#archived-task-forces","title":"Archived Task Forces","text":""},{"location":"task-forces/OID4VC-due-diligence/","title":"OID4VC Due Diligence Task Force","text":"Currently, the OID4VC components for implementing decentralized identities such as OID4VCI and OID4VP are gaining traction, especially in Europe. These specifications are required by the European digital identity Architectural Reference Framework but also getting significant attention outside of Europe.
This task force will investigate the specifications belonging to the OID4VC family thoroughly, check the existing implementations, and start the preliminary work for potentially creating/hosting a reference implementation or a framework that can be used by a wider community for application implementations.
This task force was accepted by the TAC on May 31, 2023. See OID4VC Due Diligence Task Force Proposal for more details.
"},{"location":"task-forces/OID4VC-due-diligence/#participating","title":"Participating","text":"This task force is an open group. Anyone in the OpenWallet Foundation community can join and participate. There is no formal sign up process. Just show up and participate.
If you are interested in participating, please join the OpenWallet Foundation Discord and participate in the discussion in the #oid4vc-due-diligence-tf channel.
"}]}
\ No newline at end of file
diff --git a/sitemap.xml b/sitemap.xml
new file mode 100644
index 00000000..0f8724ef
--- /dev/null
+++ b/sitemap.xml
@@ -0,0 +1,3 @@
+
+
+
\ No newline at end of file
diff --git a/sitemap.xml.gz b/sitemap.xml.gz
new file mode 100644
index 00000000..8f2bbf57
Binary files /dev/null and b/sitemap.xml.gz differ
diff --git a/task-forces/OID4VC-due-diligence/index.html b/task-forces/OID4VC-due-diligence/index.html
new file mode 100644
index 00000000..cc743d97
--- /dev/null
+++ b/task-forces/OID4VC-due-diligence/index.html
@@ -0,0 +1,4580 @@
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+ OID4VC Due Diligence - Technical Advisory Council
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+OID4VC Due Diligence Task Force
+Currently, the OID4VC components for implementing decentralized identities such as OID4VCI and OID4VP are gaining traction, especially in Europe. These specifications are required by the European digital identity Architectural Reference Framework but also getting significant attention outside of Europe.
+This task force will investigate the specifications belonging to the OID4VC family thoroughly, check the existing implementations, and start the preliminary work for potentially creating/hosting a reference implementation or a framework that can be used by a wider community for application implementations.
+This task force was accepted by the TAC on May 31, 2023. See OID4VC Due Diligence Task Force Proposal for more details.
+Participating
+This task force is an open group. Anyone in the OpenWallet Foundation community can join and participate. There is no formal sign up process. Just show up and participate.
+If you are interested in participating, please join the OpenWallet Foundation Discord and participate in the discussion in the #oid4vc-due-diligence-tf channel.
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+Task Forces
+A task force is a group that is focused on a task with limited scope and fixed time to complete. Unlike a special interest group, a task force will have a specific set of deliverables or work products that it will create and be limited in time to completion. A task force can be created by anyone in the OpenWallet Foundation community and must be proposed to and approved by the TAC.
+
+Active Task Forces
+
+Archived Task Forces
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
+
 +
+
+
+
+
+
+
+  +
+
+
+
+
+
+
+  +
+
+
+
+
+
+
+ 
 +
+
+
+
+
+
+
+ 






























































































































































































































































 +
+
+
+
+
+
+
+ 
