From 1f91205f54652588d4d1a4f052a814212f95f6fc Mon Sep 17 00:00:00 2001
From: Ruchika Modi <106240341+ruchimo@users.noreply.github.com>
Date: Fri, 19 Jan 2024 21:46:43 +0530
Subject: [PATCH] Update module to use the new container insights with CW for
EKS (#252)
* Adding Module and Example for ECS cluster monitoring with ecs_observer
* Adding Module and Example for ECS cluster monitoring with ecs_observer
* Incorporating PR comments
* Restructuring Examples and modules folder for ECS, Added content in main Readme
* Fixing path as per PR comments
* Parameterzing the config files, incorporated PR review comments
* Adding condition for AMP WS and fixing AMP endpoint
* Adding Document for ECS Monitoring and parameterized some variables
* Added sample dashboard
* Adding Document for ECS Monitoring and parameterized some variables
* Fixing failures detected by pre-commit
* Fixing failures detected by pre-commit
* Fixing failures detected by pre-commit
* Pre-commit fixes
* Fixing failures detected by pre-commit
* Fixing failures detected by pre-commit
* Pre-commit
* Fixing HIGH security alerts detected by pre-commit
* Fixing HIGH security alerts detected by pre-commit
* Fixing HIGH security alerts detected by pre-commit, 31stOct
* Add links after merge
* 2ndNov - Added condiotnal creation for Grafana WS and module versions for AMG, AMP
* Module to use the new container insights with CW for EKS
* Module to use the new container insights with CW for EKS
* Fixing precommit error
* Updating EKS container insights to replace deamonset with tf resource
* Updating EKS container insights to replace deamonset with tf resource
* Updating EKS container insights to replace deamonset with tf resource
* Updating EKS container insights to replace deamonset with tf resource
* Updating EKS container insights- Adding doc and fixing pre-commit errors
* Update Images in the doc
* Update data.tf pre-commit error
* Apply suggestions from code review
* fixing broken hyperlink
* EKS Container Insights - updating docs and few varibaleable names, definitions
---
docs/container-insights/eks.md | 49 ++++++++++++--
examples/eks-container-insights/README.md | 16 ++---
examples/eks-container-insights/data.tf | 7 ++
examples/eks-container-insights/locals.tf | 22 +++++--
examples/eks-container-insights/main.tf | 38 ++---------
examples/eks-container-insights/variables.tf | 21 ++++--
examples/eks-container-insights/versions.tf | 20 ------
modules/eks-container-insights/README.md | 36 +++++------
modules/eks-container-insights/data.tf | 7 ++
modules/eks-container-insights/locals.tf | 67 +-------------------
modules/eks-container-insights/main.tf | 63 +++++++++++-------
modules/eks-container-insights/values.yaml | 20 ------
modules/eks-container-insights/variables.tf | 67 +++++++++-----------
modules/eks-container-insights/versions.tf | 12 ----
14 files changed, 190 insertions(+), 255 deletions(-)
create mode 100644 examples/eks-container-insights/data.tf
create mode 100644 modules/eks-container-insights/data.tf
delete mode 100644 modules/eks-container-insights/values.yaml
diff --git a/docs/container-insights/eks.md b/docs/container-insights/eks.md
index 104b6739..05689361 100644
--- a/docs/container-insights/eks.md
+++ b/docs/container-insights/eks.md
@@ -1,8 +1,9 @@
# Setting Up Container Insights for your EKS Cluster
-This example deploys AWS Distro of OpenTelemetry on your EKS cluster as a Daemonset which will enable
-Container Insights metrics Dashboard on Amazon CloudWatch.
+This example deploys CloudWatch Observability EKS add-on on an exisiting Amazon EKS cluster, which enables Container Insights enhanced observability for Amazon EKS and CloudWatch Application Signals by default.
+1. Enables the CloudWatch Observability Add-on on EKS using the IAM service account role
+2. Creates an IAM Service Linked role for enabling Application Signals
## Prerequisites
@@ -34,6 +35,16 @@ Specify the EKS Cluster Name where the resources will be deployed:
export TF_VAR_eks_cluster_id=xxx
```
+### 3. Disable creation of `Cloudwatch Application Signals Service-linked Role`
+If you already have Application Signals deployed in your AWS account, please set the value of this variable to `false`
+```
+variable "create_cloudwatch_application_signals_role" {
+ type = bool
+ default = true
+ description = "Create a Cloudwatch Application Signals service-linked role"
+}
+```
+
## Deploy
Simply run this command to deploy the example
@@ -42,12 +53,40 @@ Simply run this command to deploy the example
terraform apply
```
-## Visualization
+## Enabling Application Signals (preview) for your services
+CloudWatch Application Signals (preview) is currenlty supported for **Java** applications running on your Amazon EKS cluster.
+
+Next, you have to update your Application to `Configure application metrics and trace sampling`. For this, you must add an annotation to a manifest YAML in your cluster. Adding this annotation auto-instruments the application to send metrics, traces, and logs to Application Signals. You have two options for the annotation:
+
+1. **Annotate Workload** auto-instruments a single workload in the cluster.
+ - Paste the below line into the PodTemplate section of the workload manifest.
+ ```
+ annotations: instrumentation.opentelemetry.io/inject-java: "true"
+ ```
+ - In your terminal, enter `kubectl apply -f your_deployment_yaml` to apply the change.
+
+2. **Annotate Namespace** auto-instruments all workloads deployed in the selected namespace.
+ - Paste the below line into the metadata section of the namespace manifest.
+ ```
+ annotations: instrumentation.opentelemetry.io/inject-java: "true"
+ ```
+ - In your terminal, enter `kubectl apply -f your_namespace_yaml` to apply the change.
+ - In your terminal, enter a command to restart all pods in the namespace. An example command to restart deployment workloads is `kubectl rollout restart deployment -n namespace_name`
+
+## Visualization of Container Insights data
+
+After `terraform apply` is successful, open your Amazon CloudWatch console in the same region as your EKS cluster, then from the left hand side choose `Insights -> Container Insights`, there choose the `EKS` from the drop down and you will see the metrics shown on the dashboard:
+
+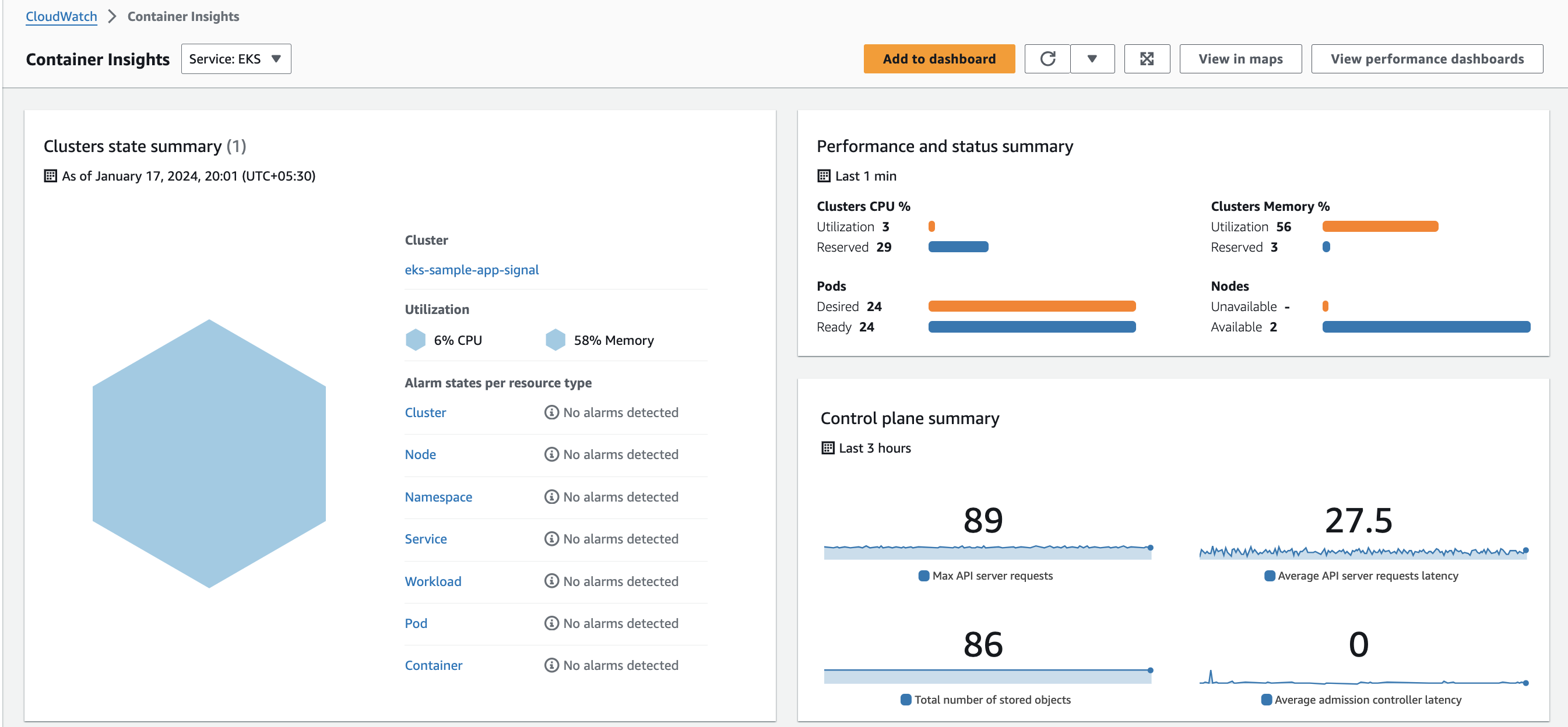 +
+
+## Visualization of CloudWatch Application Signals (preview) data
-After apply, open your Amazon CloudWatch console in the same region as your EKS cluster, then from the left hand side choose `Insights -> Container Insights`, there choose the `Performance montoring` from the drop down, choose the `cluster name` and you will see the metrics shown on the dashboard:
+After enabling your Application to pass metrics and traces by following [the steps provided above](#enabling-application-signals-preview-for-your-services), open your Amazon CloudWatch console in the same region as your EKS cluster, then from the left hand side choose `Application Signals -> Services` and you will see the metrics shown on the sample dashboard below:
-
+
+
+
+## Visualization of CloudWatch Application Signals (preview) data
-After apply, open your Amazon CloudWatch console in the same region as your EKS cluster, then from the left hand side choose `Insights -> Container Insights`, there choose the `Performance montoring` from the drop down, choose the `cluster name` and you will see the metrics shown on the dashboard:
+After enabling your Application to pass metrics and traces by following [the steps provided above](#enabling-application-signals-preview-for-your-services), open your Amazon CloudWatch console in the same region as your EKS cluster, then from the left hand side choose `Application Signals -> Services` and you will see the metrics shown on the sample dashboard below:
-
+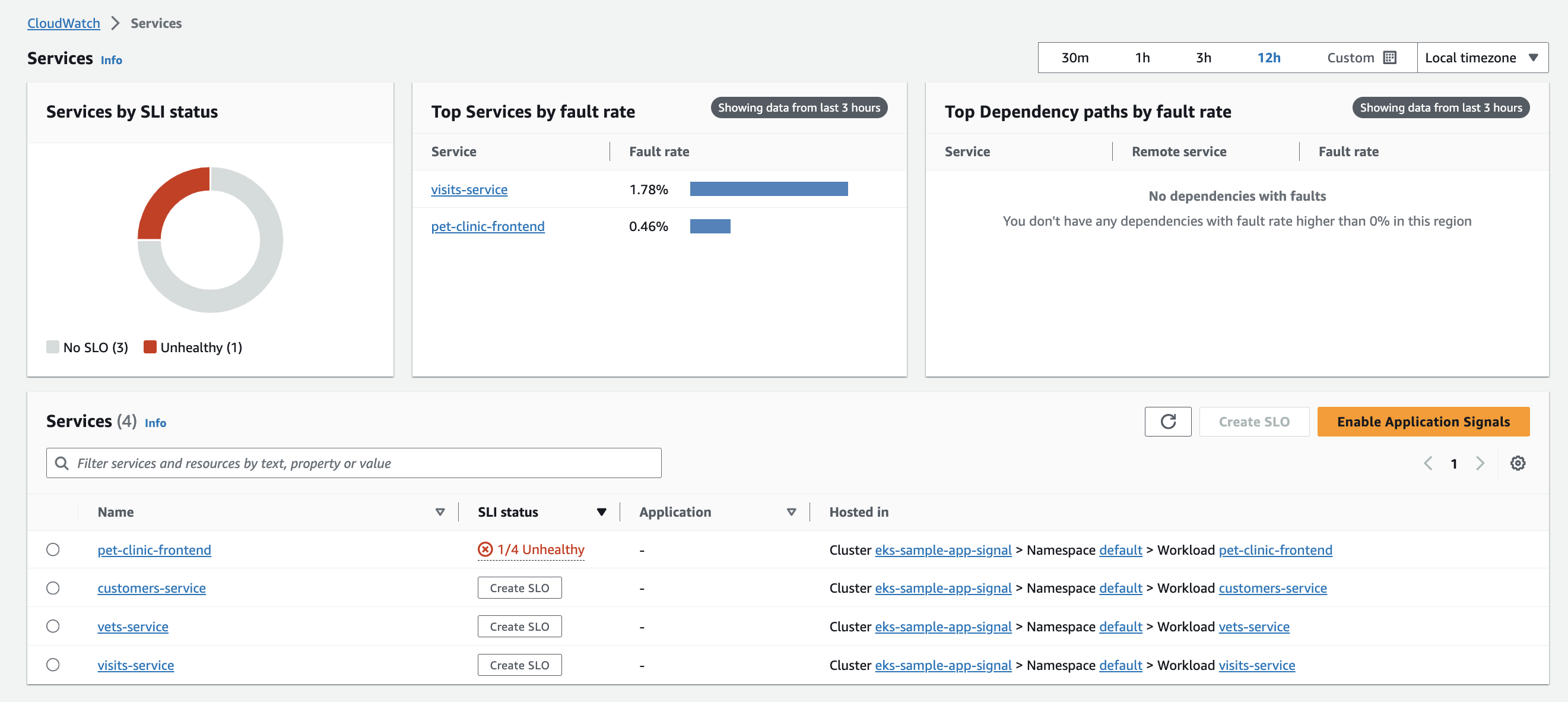 +
+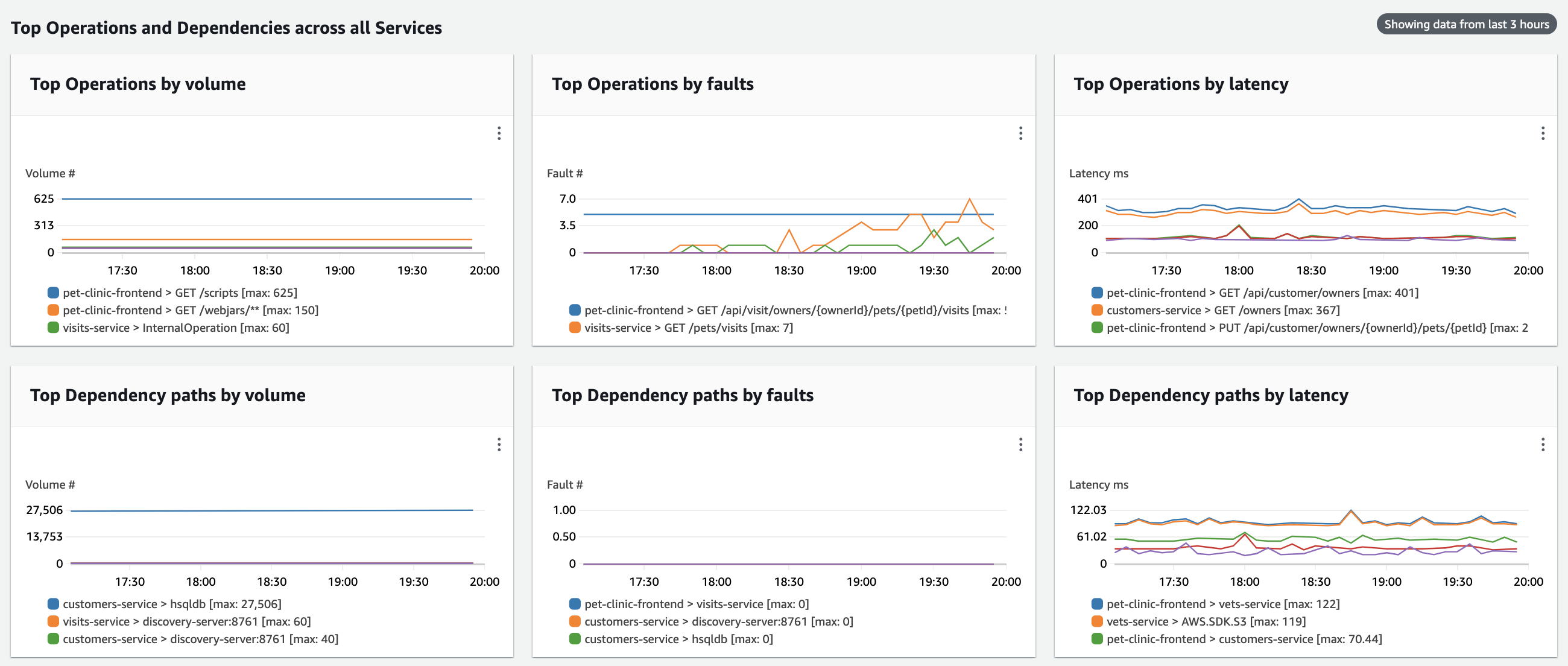 ## Cleanup
diff --git a/examples/eks-container-insights/README.md b/examples/eks-container-insights/README.md
index 3d78f9c9..95e4be75 100644
--- a/examples/eks-container-insights/README.md
+++ b/examples/eks-container-insights/README.md
@@ -1,10 +1,8 @@
# Enable Container Insights for EKS cluster
-This example deploys ADOT as a daemonset on your EKS cluster which enables Container Insights metrics on CloudWatch.
-
-Step-by-step instructions available on our [docs site](https://aws-observability.github.io/terraform-aws-observability-accelerator/)
-under **Amazon CloudWatch Container Insights**
+This example enables enhanced CloudWatch Container Insights for EKS and CloudWatch Application Signals (preview) through our CloudWatch EKS add-ons, providing comprehensive metrics, logs, and insights for cluster and application monitoring.
+Step-by-step instructions available on our [docs site](https://aws-observability.github.io/terraform-aws-observability-accelerator/container-insights/eks/)
## Requirements
@@ -13,9 +11,6 @@ under **Amazon CloudWatch Container Insights**
|------|---------|
| [terraform](#requirement\_terraform) | >= 1.1.0 |
| [aws](#requirement\_aws) | >= 5.0.0 |
-| [helm](#requirement\_helm) | >= 2.4.1 |
-| [kubectl](#requirement\_kubectl) | >= 2.0.3 |
-| [kubernetes](#requirement\_kubernetes) | >= 2.10 |
## Providers
@@ -42,10 +37,11 @@ under **Amazon CloudWatch Container Insights**
| Name | Description | Type | Default | Required |
|------|-------------|------|---------|:--------:|
-| [aws\_region](#input\_aws\_region) | EKS cluster region | `string` | n/a | yes |
+| [eks\_cluster\_domain](#input\_eks\_cluster\_domain) | The domain for the EKS cluster | `string` | `""` | no |
| [eks\_cluster\_id](#input\_eks\_cluster\_id) | EKS cluster name | `string` | n/a | yes |
-| [irsa\_iam\_permissions\_boundary](#input\_irsa\_iam\_permissions\_boundary) | IAM permissions boundary for IRSA roles | `string` | `null` | no |
-| [irsa\_iam\_role\_path](#input\_irsa\_iam\_role\_path) | IAM role path for IRSA roles | `string` | `"/"` | no |
+| [eks\_cluster\_version](#input\_eks\_cluster\_version) | The Kubernetes version for the cluster | `string` | `"1.28"` | no |
+| [eks\_oidc\_provider](#input\_eks\_oidc\_provider) | The OpenID Connect identity provider (issuer URL without leading `https://`) | `string` | `null` | no |
+| [eks\_oidc\_provider\_arn](#input\_eks\_oidc\_provider\_arn) | The OpenID Connect identity provider ARN | `string` | `null` | no |
| [tags](#input\_tags) | Additional tags (e.g. `map('BusinessUnit`,`XYZ`) | `map(string)` | `{}` | no |
## Outputs
diff --git a/examples/eks-container-insights/data.tf b/examples/eks-container-insights/data.tf
new file mode 100644
index 00000000..89c9d09a
--- /dev/null
+++ b/examples/eks-container-insights/data.tf
@@ -0,0 +1,7 @@
+data "aws_partition" "current" {}
+data "aws_caller_identity" "current" {}
+data "aws_region" "current" {}
+
+data "aws_eks_cluster" "eks_cluster" {
+ name = var.eks_cluster_id
+}
diff --git a/examples/eks-container-insights/locals.tf b/examples/eks-container-insights/locals.tf
index f5007a9b..7d265d22 100644
--- a/examples/eks-container-insights/locals.tf
+++ b/examples/eks-container-insights/locals.tf
@@ -1,9 +1,19 @@
-data "aws_partition" "current" {}
+locals {
+ name = "amazon-cloudwatch-observability"
+ eks_oidc_issuer_url = replace(data.aws_eks_cluster.eks_cluster.identity[0].oidc[0].issuer, "https://", "")
-data "aws_caller_identity" "current" {}
+ addon_context = {
+ aws_caller_identity_account_id = data.aws_caller_identity.current.account_id
+ aws_caller_identity_arn = data.aws_caller_identity.current.arn
+ aws_partition_id = data.aws_partition.current.partition
+ aws_region_name = data.aws_region.current.name
+ eks_oidc_provider_arn = "arn:${data.aws_partition.current.partition}:iam::${data.aws_caller_identity.current.account_id}:oidc-provider/${local.eks_oidc_issuer_url}"
+ eks_cluster_id = data.aws_eks_cluster.eks_cluster.id
+ tags = var.tags
+ }
-data "aws_region" "current" {}
-
-data "aws_eks_cluster" "eks_cluster" {
- name = var.eks_cluster_id
+ addon_config = {
+ kubernetes_version = var.eks_cluster_version
+ most_recent = true
+ }
}
diff --git a/examples/eks-container-insights/main.tf b/examples/eks-container-insights/main.tf
index fc05843c..e47777cd 100644
--- a/examples/eks-container-insights/main.tf
+++ b/examples/eks-container-insights/main.tf
@@ -1,34 +1,8 @@
-provider "aws" {
- region = var.aws_region
-}
-
-provider "kubernetes" {
- host = local.eks_cluster_endpoint
- cluster_ca_certificate = base64decode(data.aws_eks_cluster.eks_cluster.certificate_authority[0].data)
- exec {
- api_version = "client.authentication.k8s.io/v1beta1"
- args = ["eks", "get-token", "--cluster-name", var.eks_cluster_id]
- command = "aws"
- }
-}
-
-provider "helm" {
- kubernetes {
- host = local.eks_cluster_endpoint
- cluster_ca_certificate = base64decode(data.aws_eks_cluster.eks_cluster.certificate_authority[0].data)
- exec {
- api_version = "client.authentication.k8s.io/v1beta1"
- args = ["eks", "get-token", "--cluster-name", var.eks_cluster_id]
- command = "aws"
- }
- }
-}
-
-
-# Deploy the ADOT Container Insights
-
module "eks_container_insights" {
- source = "../../modules/eks-container-insights"
- # source = "github.com/aws-observability/terraform-aws-observability-accelerator//modules/eks-container-insights?ref=v2.5.4"
- eks_cluster_id = var.eks_cluster_id
+ source = "../../modules/eks-container-insights"
+ eks_cluster_id = var.eks_cluster_id
+ enable_amazon_eks_cw_observability = true
+ create_cloudwatch_observability_irsa_role = true
+ eks_oidc_provider_arn = local.addon_context.eks_oidc_provider_arn
+ create_cloudwatch_application_signals_role = true
}
diff --git a/examples/eks-container-insights/variables.tf b/examples/eks-container-insights/variables.tf
index 36319c1a..2e9ff5cd 100644
--- a/examples/eks-container-insights/variables.tf
+++ b/examples/eks-container-insights/variables.tf
@@ -3,23 +3,30 @@ variable "eks_cluster_id" {
type = string
}
-variable "aws_region" {
- description = "EKS cluster region"
+variable "eks_cluster_domain" {
+ description = "The domain for the EKS cluster"
type = string
+ default = ""
}
-variable "irsa_iam_role_path" {
- description = "IAM role path for IRSA roles"
+variable "eks_oidc_provider" {
+ description = "The OpenID Connect identity provider (issuer URL without leading `https://`)"
type = string
- default = "/"
+ default = null
}
-variable "irsa_iam_permissions_boundary" {
- description = "IAM permissions boundary for IRSA roles"
+variable "eks_oidc_provider_arn" {
+ description = "The OpenID Connect identity provider ARN"
type = string
default = null
}
+variable "eks_cluster_version" {
+ description = "The Kubernetes version for the cluster"
+ type = string
+ default = "1.28"
+}
+
variable "tags" {
description = "Additional tags (e.g. `map('BusinessUnit`,`XYZ`)"
type = map(string)
diff --git a/examples/eks-container-insights/versions.tf b/examples/eks-container-insights/versions.tf
index a64bfa8e..e426124f 100644
--- a/examples/eks-container-insights/versions.tf
+++ b/examples/eks-container-insights/versions.tf
@@ -6,25 +6,5 @@ terraform {
source = "hashicorp/aws"
version = ">= 5.0.0"
}
- kubernetes = {
- source = "hashicorp/kubernetes"
- version = ">= 2.10"
- }
- kubectl = {
- source = "alekc/kubectl"
- version = ">= 2.0.3"
- }
- helm = {
- source = "hashicorp/helm"
- version = ">= 2.4.1"
- }
}
-
- # ## Used for end-to-end testing on project; update to suit your needs
- # backend "s3" {
- # bucket = "aws-observability-accelerator-terraform-states"
- # region = "us-west-2"
- # key = "e2e/eks_container_insights/terraform.tfstate"
- # }
-
}
diff --git a/modules/eks-container-insights/README.md b/modules/eks-container-insights/README.md
index b6a67d8d..d0a900f2 100644
--- a/modules/eks-container-insights/README.md
+++ b/modules/eks-container-insights/README.md
@@ -1,10 +1,10 @@
-# Container Insights ADOT implementation for EKS Cluster Observability
+# Container Insights CloudWatch implementation for EKS Cluster Observability
-This module provides an automated experience around enabling Container Insights for your EKS cluster using ADOT (AWS Distro for OpenTelemetry).
-It provides the following resources:
+This module configures AWS CloudWatch Agent used for CloudWatch Application signals and Container Insights.
-- ADOT Collector Deployment to your EKS cluster
-- Enabling Container Insights on CloudWatch
+Use CloudWatch Application Signals to automatically instrument your applications on AWS so that you can monitor current application health and track long-term application performance against your business objectives. Application Signals provides you with a unified, application-centric view of your applications, services, and dependencies, and helps you monitor and triage application health.
+
+Use CloudWatch Container Insights to collect, aggregate, and summarize metrics and logs from your containerized applications and microservices. CloudWatch automatically collects metrics for many resources, such as CPU, memory, disk, and network. Container Insights also provides diagnostic information, such as container restart failures, to help you isolate issues and resolve them quickly. You can also set CloudWatch alarms on metrics that Container Insights collects.
@@ -14,9 +14,6 @@ It provides the following resources:
|------|---------|
| [terraform](#requirement\_terraform) | >= 1.1.0 |
| [aws](#requirement\_aws) | >= 5.0.0 |
-| [helm](#requirement\_helm) | >= 2.4.1 |
-| [kubectl](#requirement\_kubectl) | >= 2.0.3 |
-| [kubernetes](#requirement\_kubernetes) | >= 2.10 |
## Providers
@@ -28,15 +25,17 @@ It provides the following resources:
| Name | Source | Version |
|------|--------|---------|
-| [helm\_addon](#module\_helm\_addon) | github.com/aws-ia/terraform-aws-eks-blueprints//modules/kubernetes-addons/helm-addon | v4.32.1 |
+| [cloudwatch\_observability\_irsa\_role](#module\_cloudwatch\_observability\_irsa\_role) | terraform-aws-modules/iam/aws//modules/iam-role-for-service-accounts-eks | v5.33.0 |
## Resources
| Name | Type |
|------|------|
+| [aws_eks_addon.amazon_cloudwatch_observability](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/eks_addon) | resource |
+| [aws_iam_service_linked_role.application_signals_cw](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/iam_service_linked_role) | resource |
| [aws_caller_identity.current](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/caller_identity) | data source |
+| [aws_eks_addon_version.eks_addon_version](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/eks_addon_version) | data source |
| [aws_eks_cluster.eks_cluster](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/eks_cluster) | data source |
-| [aws_iam_policy.irsa](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/iam_policy) | data source |
| [aws_partition.current](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/partition) | data source |
| [aws_region.current](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/region) | data source |
@@ -44,15 +43,14 @@ It provides the following resources:
| Name | Description | Type | Default | Required |
|------|-------------|------|---------|:--------:|
-| [adot\_otel\_helm\_chart\_verison](#input\_adot\_otel\_helm\_chart\_verison) | ADOT collector helm chart version | `string` | `"0.17.0"` | no |
-| [eks\_cluster\_id](#input\_eks\_cluster\_id) | EKS Cluster Id | `string` | n/a | yes |
-| [helm\_config](#input\_helm\_config) | Helm provider config for adot-exporter-for-eks-on-ec2 | `any` | `{}` | no |
-| [irsa\_iam\_permissions\_boundary](#input\_irsa\_iam\_permissions\_boundary) | IAM permissions boundary for IRSA roles | `string` | `null` | no |
-| [irsa\_iam\_role\_path](#input\_irsa\_iam\_role\_path) | IAM role path for IRSA roles | `string` | `"/"` | no |
-| [irsa\_policies](#input\_irsa\_policies) | Additional IAM policies for a IAM role for service accounts | `list(string)` | `[]` | no |
-| [manage\_via\_gitops](#input\_manage\_via\_gitops) | Determines if the add-on should be managed via GitOps. | `bool` | `false` | no |
-| [service\_exporters](#input\_service\_exporters) | exporter for adot-ci setup | `string` | `"awsemf"` | no |
-| [service\_receivers](#input\_service\_receivers) | receiver for adot-ci setup | `string` | `"awscontainerinsightreceiver"` | no |
+| [addon\_config](#input\_addon\_config) | Amazon EKS Managed CloudWatch Observability Add-on config | `any` | `{}` | no |
+| [create\_cloudwatch\_application\_signals\_role](#input\_create\_cloudwatch\_application\_signals\_role) | Create a Cloudwatch Application Signals service-linked role | `bool` | `true` | no |
+| [create\_cloudwatch\_observability\_irsa\_role](#input\_create\_cloudwatch\_observability\_irsa\_role) | Create a Cloudwatch Observability IRSA | `bool` | `true` | no |
+| [eks\_cluster\_id](#input\_eks\_cluster\_id) | Name of the EKS cluster | `string` | `"eks-cw"` | no |
+| [eks\_oidc\_provider\_arn](#input\_eks\_oidc\_provider\_arn) | The OIDC Provider ARN of AWS EKS cluster | `string` | `""` | no |
+| [enable\_amazon\_eks\_cw\_observability](#input\_enable\_amazon\_eks\_cw\_observability) | Enable Amazon EKS CloudWatch Observability add-on | `bool` | `true` | no |
+| [kubernetes\_version](#input\_kubernetes\_version) | Kubernetes version | `string` | `"1.28"` | no |
+| [most\_recent](#input\_most\_recent) | Determines if the most recent or default version of the addon should be returned. | `bool` | `false` | no |
| [tags](#input\_tags) | Additional tags (e.g. `map('BusinessUnit`,`XYZ`) | `map(string)` | `{}` | no |
## Outputs
diff --git a/modules/eks-container-insights/data.tf b/modules/eks-container-insights/data.tf
new file mode 100644
index 00000000..89c9d09a
--- /dev/null
+++ b/modules/eks-container-insights/data.tf
@@ -0,0 +1,7 @@
+data "aws_partition" "current" {}
+data "aws_caller_identity" "current" {}
+data "aws_region" "current" {}
+
+data "aws_eks_cluster" "eks_cluster" {
+ name = var.eks_cluster_id
+}
diff --git a/modules/eks-container-insights/locals.tf b/modules/eks-container-insights/locals.tf
index 3246dbec..98e169c9 100644
--- a/modules/eks-container-insights/locals.tf
+++ b/modules/eks-container-insights/locals.tf
@@ -1,77 +1,14 @@
-data "aws_partition" "current" {}
-
-data "aws_caller_identity" "current" {}
-
-data "aws_region" "current" {}
-
-data "aws_eks_cluster" "eks_cluster" {
- name = var.eks_cluster_id
-}
-
-data "aws_iam_policy" "irsa" {
- arn = "arn:aws:iam::aws:policy/CloudWatchAgentServerPolicy"
-}
-
locals {
- name = "adot-exporter-for-eks-on-ec2"
- service_account = try(var.helm_config.service_account, "${local.name}-sa")
-
- set_values = [
- {
- name = "serviceAccount.name"
- value = local.service_account
- },
- {
- name = "serviceAccount.create"
- value = false
- }
- ]
- # https://github.com/aws-observability/aws-otel-helm-charts/tree/main/charts/adot-exporter-for-eks-on-ec2
- default_helm_config = {
- name = local.name
- chart = "adot-exporter-for-eks-on-ec2"
- repository = "https://aws-observability.github.io/aws-otel-helm-charts"
- version = var.adot_otel_helm_chart_verison
- namespace = "amazon-metrics"
- values = local.default_helm_values
- description = "ADOT Helm Chart Deployment Configuration for Container Insights"
- }
-
- helm_config = merge(
- local.default_helm_config,
- var.helm_config
- )
-
- default_helm_values = [templatefile("${path.module}/values.yaml", {
- aws_region = local.addon_context.aws_region_name
- cluster_name = local.addon_context.eks_cluster_id
- service_receivers = format("[\"%s\"]", var.service_receivers)
- service_exporters = format("[\"%s\"]", var.service_exporters)
- service_account = local.service_account
- })]
-
- irsa_config = {
- kubernetes_namespace = local.helm_config["namespace"]
- kubernetes_service_account = local.service_account
- create_kubernetes_namespace = try(local.helm_config["create_namespace"], true)
- create_kubernetes_service_account = true
- create_service_account_secret_token = try(local.helm_config["create_service_account_secret_token"], false)
- irsa_iam_policies = concat([data.aws_iam_policy.irsa.arn], var.irsa_policies)
- }
-
+ kubernetes_version = var.kubernetes_version
eks_oidc_issuer_url = replace(data.aws_eks_cluster.eks_cluster.identity[0].oidc[0].issuer, "https://", "")
addon_context = {
aws_caller_identity_account_id = data.aws_caller_identity.current.account_id
aws_caller_identity_arn = data.aws_caller_identity.current.arn
- aws_eks_cluster_endpoint = data.aws_eks_cluster.eks_cluster.endpoint
aws_partition_id = data.aws_partition.current.partition
aws_region_name = data.aws_region.current.name
- eks_cluster_id = var.eks_cluster_id
- eks_oidc_issuer_url = replace(data.aws_eks_cluster.eks_cluster.identity[0].oidc[0].issuer, "https://", "")
eks_oidc_provider_arn = "arn:${data.aws_partition.current.partition}:iam::${data.aws_caller_identity.current.account_id}:oidc-provider/${local.eks_oidc_issuer_url}"
+ eks_cluster_id = data.aws_eks_cluster.eks_cluster.id
tags = var.tags
- irsa_iam_role_path = var.irsa_iam_role_path
- irsa_iam_permissions_boundary = var.irsa_iam_permissions_boundary
}
}
diff --git a/modules/eks-container-insights/main.tf b/modules/eks-container-insights/main.tf
index d4c11538..e48c1cee 100644
--- a/modules/eks-container-insights/main.tf
+++ b/modules/eks-container-insights/main.tf
@@ -1,30 +1,47 @@
-provider "kubernetes" {
- host = data.aws_eks_cluster.eks_cluster.endpoint
- cluster_ca_certificate = base64decode(data.aws_eks_cluster.eks_cluster.certificate_authority[0].data)
- exec {
- api_version = "client.authentication.k8s.io/v1beta1"
- args = ["eks", "get-token", "--cluster-name", local.addon_context.eks_cluster_id]
- command = "aws"
- }
+locals {
+ name = "amazon-cloudwatch-observability"
}
-provider "helm" {
- kubernetes {
- host = data.aws_eks_cluster.eks_cluster.endpoint
- cluster_ca_certificate = base64decode(data.aws_eks_cluster.eks_cluster.certificate_authority[0].data)
- exec {
- api_version = "client.authentication.k8s.io/v1beta1"
- args = ["eks", "get-token", "--cluster-name", local.addon_context.eks_cluster_id]
- command = "aws"
+module "cloudwatch_observability_irsa_role" {
+ count = var.create_cloudwatch_observability_irsa_role ? 1 : 0
+
+ source = "terraform-aws-modules/iam/aws//modules/iam-role-for-service-accounts-eks"
+ version = "v5.33.0"
+ role_name = "cloudwatch-observability"
+ attach_cloudwatch_observability_policy = true
+
+ oidc_providers = {
+ ex = {
+ provider_arn = var.eks_oidc_provider_arn
+ namespace_service_accounts = ["amazon-cloudwatch:cloudwatch-agent"]
}
}
}
-module "helm_addon" {
- source = "github.com/aws-ia/terraform-aws-eks-blueprints//modules/kubernetes-addons/helm-addon?ref=v4.32.1"
- manage_via_gitops = var.manage_via_gitops
- set_values = local.set_values
- helm_config = local.helm_config
- irsa_config = local.irsa_config
- addon_context = local.addon_context
+data "aws_eks_addon_version" "eks_addon_version" {
+ addon_name = local.name
+ kubernetes_version = try(var.addon_config.kubernetes_version, var.kubernetes_version)
+ most_recent = try(var.addon_config.most_recent, true)
+}
+
+resource "aws_eks_addon" "amazon_cloudwatch_observability" {
+ count = var.enable_amazon_eks_cw_observability ? 1 : 0
+
+ cluster_name = var.eks_cluster_id
+ addon_name = local.name
+ addon_version = try(var.addon_config.addon_version, data.aws_eks_addon_version.eks_addon_version.version)
+ resolve_conflicts_on_create = try(var.addon_config.resolve_conflicts_on_create, "OVERWRITE")
+ service_account_role_arn = try(module.cloudwatch_observability_irsa_role[0].iam_role_arn, null)
+ preserve = try(var.addon_config.preserve, true)
+ configuration_values = try(var.addon_config.configuration_values, null)
+
+ tags = merge(
+ # var.addon_context.tags,
+ try(var.addon_config.tags, {})
+ )
+}
+
+resource "aws_iam_service_linked_role" "application_signals_cw" {
+ count = var.create_cloudwatch_application_signals_role ? 1 : 0
+ aws_service_name = "application-signals.cloudwatch.amazonaws.com"
}
diff --git a/modules/eks-container-insights/values.yaml b/modules/eks-container-insights/values.yaml
deleted file mode 100644
index d6a22ae9..00000000
--- a/modules/eks-container-insights/values.yaml
+++ /dev/null
@@ -1,20 +0,0 @@
-
-awsRegion: ${aws_region}
-clusterName: ${cluster_name}
-
-
-adotCollector:
- daemonSet:
- serviceAccount:
- create: false
- name: ${service_account}
- createNamespace: false
- extensions:
- sigv4auth:
- region: ${aws_region}
- service:
- metrics:
- receivers: ${service_receivers}
- exporters: ${service_exporters}
- sidecar:
- regionS3: ${aws_region}
diff --git a/modules/eks-container-insights/variables.tf b/modules/eks-container-insights/variables.tf
index 039a7bd5..94c85b0c 100644
--- a/modules/eks-container-insights/variables.tf
+++ b/modules/eks-container-insights/variables.tf
@@ -1,42 +1,49 @@
-variable "helm_config" {
- description = "Helm provider config for adot-exporter-for-eks-on-ec2"
- type = any
- default = {}
+variable "eks_cluster_id" {
+ description = "Name of the EKS cluster"
+ default = "eks-cw"
+ type = string
}
-variable "manage_via_gitops" {
+variable "enable_amazon_eks_cw_observability" {
+ description = "Enable Amazon EKS CloudWatch Observability add-on"
type = bool
- description = "Determines if the add-on should be managed via GitOps."
- default = false
+ default = true
}
-variable "service_receivers" {
- type = string
- description = "receiver for adot-ci setup"
- default = "awscontainerinsightreceiver"
+variable "addon_config" {
+ description = "Amazon EKS Managed CloudWatch Observability Add-on config"
+ type = any
+ default = {}
}
-variable "service_exporters" {
+variable "kubernetes_version" {
+ description = "Kubernetes version"
type = string
- description = "exporter for adot-ci setup"
- default = "awsemf"
+ default = "1.28"
}
-variable "irsa_policies" {
- description = "Additional IAM policies for a IAM role for service accounts"
- type = list(string)
- default = []
+variable "most_recent" {
+ description = "Determines if the most recent or default version of the addon should be returned."
+ type = bool
+ default = false
}
-variable "eks_cluster_id" {
- description = "EKS Cluster Id"
+variable "eks_oidc_provider_arn" {
+ description = "The OIDC Provider ARN of AWS EKS cluster"
type = string
+ default = ""
}
-variable "adot_otel_helm_chart_verison" {
- description = "ADOT collector helm chart version"
- type = string
- default = "0.17.0"
+variable "create_cloudwatch_observability_irsa_role" {
+ type = bool
+ default = true
+ description = "Create a Cloudwatch Observability IRSA"
+}
+
+variable "create_cloudwatch_application_signals_role" {
+ type = bool
+ default = true
+ description = "Create a Cloudwatch Application Signals service-linked role"
}
variable "tags" {
@@ -44,15 +51,3 @@ variable "tags" {
type = map(string)
default = {}
}
-
-variable "irsa_iam_role_path" {
- description = "IAM role path for IRSA roles"
- type = string
- default = "/"
-}
-
-variable "irsa_iam_permissions_boundary" {
- description = "IAM permissions boundary for IRSA roles"
- type = string
- default = null
-}
diff --git a/modules/eks-container-insights/versions.tf b/modules/eks-container-insights/versions.tf
index ea7a421f..e426124f 100644
--- a/modules/eks-container-insights/versions.tf
+++ b/modules/eks-container-insights/versions.tf
@@ -6,17 +6,5 @@ terraform {
source = "hashicorp/aws"
version = ">= 5.0.0"
}
- kubernetes = {
- source = "hashicorp/kubernetes"
- version = ">= 2.10"
- }
- kubectl = {
- source = "alekc/kubectl"
- version = ">= 2.0.3"
- }
- helm = {
- source = "hashicorp/helm"
- version = ">= 2.4.1"
- }
}
}
## Cleanup
diff --git a/examples/eks-container-insights/README.md b/examples/eks-container-insights/README.md
index 3d78f9c9..95e4be75 100644
--- a/examples/eks-container-insights/README.md
+++ b/examples/eks-container-insights/README.md
@@ -1,10 +1,8 @@
# Enable Container Insights for EKS cluster
-This example deploys ADOT as a daemonset on your EKS cluster which enables Container Insights metrics on CloudWatch.
-
-Step-by-step instructions available on our [docs site](https://aws-observability.github.io/terraform-aws-observability-accelerator/)
-under **Amazon CloudWatch Container Insights**
+This example enables enhanced CloudWatch Container Insights for EKS and CloudWatch Application Signals (preview) through our CloudWatch EKS add-ons, providing comprehensive metrics, logs, and insights for cluster and application monitoring.
+Step-by-step instructions available on our [docs site](https://aws-observability.github.io/terraform-aws-observability-accelerator/container-insights/eks/)
## Requirements
@@ -13,9 +11,6 @@ under **Amazon CloudWatch Container Insights**
|------|---------|
| [terraform](#requirement\_terraform) | >= 1.1.0 |
| [aws](#requirement\_aws) | >= 5.0.0 |
-| [helm](#requirement\_helm) | >= 2.4.1 |
-| [kubectl](#requirement\_kubectl) | >= 2.0.3 |
-| [kubernetes](#requirement\_kubernetes) | >= 2.10 |
## Providers
@@ -42,10 +37,11 @@ under **Amazon CloudWatch Container Insights**
| Name | Description | Type | Default | Required |
|------|-------------|------|---------|:--------:|
-| [aws\_region](#input\_aws\_region) | EKS cluster region | `string` | n/a | yes |
+| [eks\_cluster\_domain](#input\_eks\_cluster\_domain) | The domain for the EKS cluster | `string` | `""` | no |
| [eks\_cluster\_id](#input\_eks\_cluster\_id) | EKS cluster name | `string` | n/a | yes |
-| [irsa\_iam\_permissions\_boundary](#input\_irsa\_iam\_permissions\_boundary) | IAM permissions boundary for IRSA roles | `string` | `null` | no |
-| [irsa\_iam\_role\_path](#input\_irsa\_iam\_role\_path) | IAM role path for IRSA roles | `string` | `"/"` | no |
+| [eks\_cluster\_version](#input\_eks\_cluster\_version) | The Kubernetes version for the cluster | `string` | `"1.28"` | no |
+| [eks\_oidc\_provider](#input\_eks\_oidc\_provider) | The OpenID Connect identity provider (issuer URL without leading `https://`) | `string` | `null` | no |
+| [eks\_oidc\_provider\_arn](#input\_eks\_oidc\_provider\_arn) | The OpenID Connect identity provider ARN | `string` | `null` | no |
| [tags](#input\_tags) | Additional tags (e.g. `map('BusinessUnit`,`XYZ`) | `map(string)` | `{}` | no |
## Outputs
diff --git a/examples/eks-container-insights/data.tf b/examples/eks-container-insights/data.tf
new file mode 100644
index 00000000..89c9d09a
--- /dev/null
+++ b/examples/eks-container-insights/data.tf
@@ -0,0 +1,7 @@
+data "aws_partition" "current" {}
+data "aws_caller_identity" "current" {}
+data "aws_region" "current" {}
+
+data "aws_eks_cluster" "eks_cluster" {
+ name = var.eks_cluster_id
+}
diff --git a/examples/eks-container-insights/locals.tf b/examples/eks-container-insights/locals.tf
index f5007a9b..7d265d22 100644
--- a/examples/eks-container-insights/locals.tf
+++ b/examples/eks-container-insights/locals.tf
@@ -1,9 +1,19 @@
-data "aws_partition" "current" {}
+locals {
+ name = "amazon-cloudwatch-observability"
+ eks_oidc_issuer_url = replace(data.aws_eks_cluster.eks_cluster.identity[0].oidc[0].issuer, "https://", "")
-data "aws_caller_identity" "current" {}
+ addon_context = {
+ aws_caller_identity_account_id = data.aws_caller_identity.current.account_id
+ aws_caller_identity_arn = data.aws_caller_identity.current.arn
+ aws_partition_id = data.aws_partition.current.partition
+ aws_region_name = data.aws_region.current.name
+ eks_oidc_provider_arn = "arn:${data.aws_partition.current.partition}:iam::${data.aws_caller_identity.current.account_id}:oidc-provider/${local.eks_oidc_issuer_url}"
+ eks_cluster_id = data.aws_eks_cluster.eks_cluster.id
+ tags = var.tags
+ }
-data "aws_region" "current" {}
-
-data "aws_eks_cluster" "eks_cluster" {
- name = var.eks_cluster_id
+ addon_config = {
+ kubernetes_version = var.eks_cluster_version
+ most_recent = true
+ }
}
diff --git a/examples/eks-container-insights/main.tf b/examples/eks-container-insights/main.tf
index fc05843c..e47777cd 100644
--- a/examples/eks-container-insights/main.tf
+++ b/examples/eks-container-insights/main.tf
@@ -1,34 +1,8 @@
-provider "aws" {
- region = var.aws_region
-}
-
-provider "kubernetes" {
- host = local.eks_cluster_endpoint
- cluster_ca_certificate = base64decode(data.aws_eks_cluster.eks_cluster.certificate_authority[0].data)
- exec {
- api_version = "client.authentication.k8s.io/v1beta1"
- args = ["eks", "get-token", "--cluster-name", var.eks_cluster_id]
- command = "aws"
- }
-}
-
-provider "helm" {
- kubernetes {
- host = local.eks_cluster_endpoint
- cluster_ca_certificate = base64decode(data.aws_eks_cluster.eks_cluster.certificate_authority[0].data)
- exec {
- api_version = "client.authentication.k8s.io/v1beta1"
- args = ["eks", "get-token", "--cluster-name", var.eks_cluster_id]
- command = "aws"
- }
- }
-}
-
-
-# Deploy the ADOT Container Insights
-
module "eks_container_insights" {
- source = "../../modules/eks-container-insights"
- # source = "github.com/aws-observability/terraform-aws-observability-accelerator//modules/eks-container-insights?ref=v2.5.4"
- eks_cluster_id = var.eks_cluster_id
+ source = "../../modules/eks-container-insights"
+ eks_cluster_id = var.eks_cluster_id
+ enable_amazon_eks_cw_observability = true
+ create_cloudwatch_observability_irsa_role = true
+ eks_oidc_provider_arn = local.addon_context.eks_oidc_provider_arn
+ create_cloudwatch_application_signals_role = true
}
diff --git a/examples/eks-container-insights/variables.tf b/examples/eks-container-insights/variables.tf
index 36319c1a..2e9ff5cd 100644
--- a/examples/eks-container-insights/variables.tf
+++ b/examples/eks-container-insights/variables.tf
@@ -3,23 +3,30 @@ variable "eks_cluster_id" {
type = string
}
-variable "aws_region" {
- description = "EKS cluster region"
+variable "eks_cluster_domain" {
+ description = "The domain for the EKS cluster"
type = string
+ default = ""
}
-variable "irsa_iam_role_path" {
- description = "IAM role path for IRSA roles"
+variable "eks_oidc_provider" {
+ description = "The OpenID Connect identity provider (issuer URL without leading `https://`)"
type = string
- default = "/"
+ default = null
}
-variable "irsa_iam_permissions_boundary" {
- description = "IAM permissions boundary for IRSA roles"
+variable "eks_oidc_provider_arn" {
+ description = "The OpenID Connect identity provider ARN"
type = string
default = null
}
+variable "eks_cluster_version" {
+ description = "The Kubernetes version for the cluster"
+ type = string
+ default = "1.28"
+}
+
variable "tags" {
description = "Additional tags (e.g. `map('BusinessUnit`,`XYZ`)"
type = map(string)
diff --git a/examples/eks-container-insights/versions.tf b/examples/eks-container-insights/versions.tf
index a64bfa8e..e426124f 100644
--- a/examples/eks-container-insights/versions.tf
+++ b/examples/eks-container-insights/versions.tf
@@ -6,25 +6,5 @@ terraform {
source = "hashicorp/aws"
version = ">= 5.0.0"
}
- kubernetes = {
- source = "hashicorp/kubernetes"
- version = ">= 2.10"
- }
- kubectl = {
- source = "alekc/kubectl"
- version = ">= 2.0.3"
- }
- helm = {
- source = "hashicorp/helm"
- version = ">= 2.4.1"
- }
}
-
- # ## Used for end-to-end testing on project; update to suit your needs
- # backend "s3" {
- # bucket = "aws-observability-accelerator-terraform-states"
- # region = "us-west-2"
- # key = "e2e/eks_container_insights/terraform.tfstate"
- # }
-
}
diff --git a/modules/eks-container-insights/README.md b/modules/eks-container-insights/README.md
index b6a67d8d..d0a900f2 100644
--- a/modules/eks-container-insights/README.md
+++ b/modules/eks-container-insights/README.md
@@ -1,10 +1,10 @@
-# Container Insights ADOT implementation for EKS Cluster Observability
+# Container Insights CloudWatch implementation for EKS Cluster Observability
-This module provides an automated experience around enabling Container Insights for your EKS cluster using ADOT (AWS Distro for OpenTelemetry).
-It provides the following resources:
+This module configures AWS CloudWatch Agent used for CloudWatch Application signals and Container Insights.
-- ADOT Collector Deployment to your EKS cluster
-- Enabling Container Insights on CloudWatch
+Use CloudWatch Application Signals to automatically instrument your applications on AWS so that you can monitor current application health and track long-term application performance against your business objectives. Application Signals provides you with a unified, application-centric view of your applications, services, and dependencies, and helps you monitor and triage application health.
+
+Use CloudWatch Container Insights to collect, aggregate, and summarize metrics and logs from your containerized applications and microservices. CloudWatch automatically collects metrics for many resources, such as CPU, memory, disk, and network. Container Insights also provides diagnostic information, such as container restart failures, to help you isolate issues and resolve them quickly. You can also set CloudWatch alarms on metrics that Container Insights collects.
@@ -14,9 +14,6 @@ It provides the following resources:
|------|---------|
| [terraform](#requirement\_terraform) | >= 1.1.0 |
| [aws](#requirement\_aws) | >= 5.0.0 |
-| [helm](#requirement\_helm) | >= 2.4.1 |
-| [kubectl](#requirement\_kubectl) | >= 2.0.3 |
-| [kubernetes](#requirement\_kubernetes) | >= 2.10 |
## Providers
@@ -28,15 +25,17 @@ It provides the following resources:
| Name | Source | Version |
|------|--------|---------|
-| [helm\_addon](#module\_helm\_addon) | github.com/aws-ia/terraform-aws-eks-blueprints//modules/kubernetes-addons/helm-addon | v4.32.1 |
+| [cloudwatch\_observability\_irsa\_role](#module\_cloudwatch\_observability\_irsa\_role) | terraform-aws-modules/iam/aws//modules/iam-role-for-service-accounts-eks | v5.33.0 |
## Resources
| Name | Type |
|------|------|
+| [aws_eks_addon.amazon_cloudwatch_observability](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/eks_addon) | resource |
+| [aws_iam_service_linked_role.application_signals_cw](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/iam_service_linked_role) | resource |
| [aws_caller_identity.current](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/caller_identity) | data source |
+| [aws_eks_addon_version.eks_addon_version](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/eks_addon_version) | data source |
| [aws_eks_cluster.eks_cluster](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/eks_cluster) | data source |
-| [aws_iam_policy.irsa](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/iam_policy) | data source |
| [aws_partition.current](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/partition) | data source |
| [aws_region.current](https://registry.terraform.io/providers/hashicorp/aws/latest/docs/data-sources/region) | data source |
@@ -44,15 +43,14 @@ It provides the following resources:
| Name | Description | Type | Default | Required |
|------|-------------|------|---------|:--------:|
-| [adot\_otel\_helm\_chart\_verison](#input\_adot\_otel\_helm\_chart\_verison) | ADOT collector helm chart version | `string` | `"0.17.0"` | no |
-| [eks\_cluster\_id](#input\_eks\_cluster\_id) | EKS Cluster Id | `string` | n/a | yes |
-| [helm\_config](#input\_helm\_config) | Helm provider config for adot-exporter-for-eks-on-ec2 | `any` | `{}` | no |
-| [irsa\_iam\_permissions\_boundary](#input\_irsa\_iam\_permissions\_boundary) | IAM permissions boundary for IRSA roles | `string` | `null` | no |
-| [irsa\_iam\_role\_path](#input\_irsa\_iam\_role\_path) | IAM role path for IRSA roles | `string` | `"/"` | no |
-| [irsa\_policies](#input\_irsa\_policies) | Additional IAM policies for a IAM role for service accounts | `list(string)` | `[]` | no |
-| [manage\_via\_gitops](#input\_manage\_via\_gitops) | Determines if the add-on should be managed via GitOps. | `bool` | `false` | no |
-| [service\_exporters](#input\_service\_exporters) | exporter for adot-ci setup | `string` | `"awsemf"` | no |
-| [service\_receivers](#input\_service\_receivers) | receiver for adot-ci setup | `string` | `"awscontainerinsightreceiver"` | no |
+| [addon\_config](#input\_addon\_config) | Amazon EKS Managed CloudWatch Observability Add-on config | `any` | `{}` | no |
+| [create\_cloudwatch\_application\_signals\_role](#input\_create\_cloudwatch\_application\_signals\_role) | Create a Cloudwatch Application Signals service-linked role | `bool` | `true` | no |
+| [create\_cloudwatch\_observability\_irsa\_role](#input\_create\_cloudwatch\_observability\_irsa\_role) | Create a Cloudwatch Observability IRSA | `bool` | `true` | no |
+| [eks\_cluster\_id](#input\_eks\_cluster\_id) | Name of the EKS cluster | `string` | `"eks-cw"` | no |
+| [eks\_oidc\_provider\_arn](#input\_eks\_oidc\_provider\_arn) | The OIDC Provider ARN of AWS EKS cluster | `string` | `""` | no |
+| [enable\_amazon\_eks\_cw\_observability](#input\_enable\_amazon\_eks\_cw\_observability) | Enable Amazon EKS CloudWatch Observability add-on | `bool` | `true` | no |
+| [kubernetes\_version](#input\_kubernetes\_version) | Kubernetes version | `string` | `"1.28"` | no |
+| [most\_recent](#input\_most\_recent) | Determines if the most recent or default version of the addon should be returned. | `bool` | `false` | no |
| [tags](#input\_tags) | Additional tags (e.g. `map('BusinessUnit`,`XYZ`) | `map(string)` | `{}` | no |
## Outputs
diff --git a/modules/eks-container-insights/data.tf b/modules/eks-container-insights/data.tf
new file mode 100644
index 00000000..89c9d09a
--- /dev/null
+++ b/modules/eks-container-insights/data.tf
@@ -0,0 +1,7 @@
+data "aws_partition" "current" {}
+data "aws_caller_identity" "current" {}
+data "aws_region" "current" {}
+
+data "aws_eks_cluster" "eks_cluster" {
+ name = var.eks_cluster_id
+}
diff --git a/modules/eks-container-insights/locals.tf b/modules/eks-container-insights/locals.tf
index 3246dbec..98e169c9 100644
--- a/modules/eks-container-insights/locals.tf
+++ b/modules/eks-container-insights/locals.tf
@@ -1,77 +1,14 @@
-data "aws_partition" "current" {}
-
-data "aws_caller_identity" "current" {}
-
-data "aws_region" "current" {}
-
-data "aws_eks_cluster" "eks_cluster" {
- name = var.eks_cluster_id
-}
-
-data "aws_iam_policy" "irsa" {
- arn = "arn:aws:iam::aws:policy/CloudWatchAgentServerPolicy"
-}
-
locals {
- name = "adot-exporter-for-eks-on-ec2"
- service_account = try(var.helm_config.service_account, "${local.name}-sa")
-
- set_values = [
- {
- name = "serviceAccount.name"
- value = local.service_account
- },
- {
- name = "serviceAccount.create"
- value = false
- }
- ]
- # https://github.com/aws-observability/aws-otel-helm-charts/tree/main/charts/adot-exporter-for-eks-on-ec2
- default_helm_config = {
- name = local.name
- chart = "adot-exporter-for-eks-on-ec2"
- repository = "https://aws-observability.github.io/aws-otel-helm-charts"
- version = var.adot_otel_helm_chart_verison
- namespace = "amazon-metrics"
- values = local.default_helm_values
- description = "ADOT Helm Chart Deployment Configuration for Container Insights"
- }
-
- helm_config = merge(
- local.default_helm_config,
- var.helm_config
- )
-
- default_helm_values = [templatefile("${path.module}/values.yaml", {
- aws_region = local.addon_context.aws_region_name
- cluster_name = local.addon_context.eks_cluster_id
- service_receivers = format("[\"%s\"]", var.service_receivers)
- service_exporters = format("[\"%s\"]", var.service_exporters)
- service_account = local.service_account
- })]
-
- irsa_config = {
- kubernetes_namespace = local.helm_config["namespace"]
- kubernetes_service_account = local.service_account
- create_kubernetes_namespace = try(local.helm_config["create_namespace"], true)
- create_kubernetes_service_account = true
- create_service_account_secret_token = try(local.helm_config["create_service_account_secret_token"], false)
- irsa_iam_policies = concat([data.aws_iam_policy.irsa.arn], var.irsa_policies)
- }
-
+ kubernetes_version = var.kubernetes_version
eks_oidc_issuer_url = replace(data.aws_eks_cluster.eks_cluster.identity[0].oidc[0].issuer, "https://", "")
addon_context = {
aws_caller_identity_account_id = data.aws_caller_identity.current.account_id
aws_caller_identity_arn = data.aws_caller_identity.current.arn
- aws_eks_cluster_endpoint = data.aws_eks_cluster.eks_cluster.endpoint
aws_partition_id = data.aws_partition.current.partition
aws_region_name = data.aws_region.current.name
- eks_cluster_id = var.eks_cluster_id
- eks_oidc_issuer_url = replace(data.aws_eks_cluster.eks_cluster.identity[0].oidc[0].issuer, "https://", "")
eks_oidc_provider_arn = "arn:${data.aws_partition.current.partition}:iam::${data.aws_caller_identity.current.account_id}:oidc-provider/${local.eks_oidc_issuer_url}"
+ eks_cluster_id = data.aws_eks_cluster.eks_cluster.id
tags = var.tags
- irsa_iam_role_path = var.irsa_iam_role_path
- irsa_iam_permissions_boundary = var.irsa_iam_permissions_boundary
}
}
diff --git a/modules/eks-container-insights/main.tf b/modules/eks-container-insights/main.tf
index d4c11538..e48c1cee 100644
--- a/modules/eks-container-insights/main.tf
+++ b/modules/eks-container-insights/main.tf
@@ -1,30 +1,47 @@
-provider "kubernetes" {
- host = data.aws_eks_cluster.eks_cluster.endpoint
- cluster_ca_certificate = base64decode(data.aws_eks_cluster.eks_cluster.certificate_authority[0].data)
- exec {
- api_version = "client.authentication.k8s.io/v1beta1"
- args = ["eks", "get-token", "--cluster-name", local.addon_context.eks_cluster_id]
- command = "aws"
- }
+locals {
+ name = "amazon-cloudwatch-observability"
}
-provider "helm" {
- kubernetes {
- host = data.aws_eks_cluster.eks_cluster.endpoint
- cluster_ca_certificate = base64decode(data.aws_eks_cluster.eks_cluster.certificate_authority[0].data)
- exec {
- api_version = "client.authentication.k8s.io/v1beta1"
- args = ["eks", "get-token", "--cluster-name", local.addon_context.eks_cluster_id]
- command = "aws"
+module "cloudwatch_observability_irsa_role" {
+ count = var.create_cloudwatch_observability_irsa_role ? 1 : 0
+
+ source = "terraform-aws-modules/iam/aws//modules/iam-role-for-service-accounts-eks"
+ version = "v5.33.0"
+ role_name = "cloudwatch-observability"
+ attach_cloudwatch_observability_policy = true
+
+ oidc_providers = {
+ ex = {
+ provider_arn = var.eks_oidc_provider_arn
+ namespace_service_accounts = ["amazon-cloudwatch:cloudwatch-agent"]
}
}
}
-module "helm_addon" {
- source = "github.com/aws-ia/terraform-aws-eks-blueprints//modules/kubernetes-addons/helm-addon?ref=v4.32.1"
- manage_via_gitops = var.manage_via_gitops
- set_values = local.set_values
- helm_config = local.helm_config
- irsa_config = local.irsa_config
- addon_context = local.addon_context
+data "aws_eks_addon_version" "eks_addon_version" {
+ addon_name = local.name
+ kubernetes_version = try(var.addon_config.kubernetes_version, var.kubernetes_version)
+ most_recent = try(var.addon_config.most_recent, true)
+}
+
+resource "aws_eks_addon" "amazon_cloudwatch_observability" {
+ count = var.enable_amazon_eks_cw_observability ? 1 : 0
+
+ cluster_name = var.eks_cluster_id
+ addon_name = local.name
+ addon_version = try(var.addon_config.addon_version, data.aws_eks_addon_version.eks_addon_version.version)
+ resolve_conflicts_on_create = try(var.addon_config.resolve_conflicts_on_create, "OVERWRITE")
+ service_account_role_arn = try(module.cloudwatch_observability_irsa_role[0].iam_role_arn, null)
+ preserve = try(var.addon_config.preserve, true)
+ configuration_values = try(var.addon_config.configuration_values, null)
+
+ tags = merge(
+ # var.addon_context.tags,
+ try(var.addon_config.tags, {})
+ )
+}
+
+resource "aws_iam_service_linked_role" "application_signals_cw" {
+ count = var.create_cloudwatch_application_signals_role ? 1 : 0
+ aws_service_name = "application-signals.cloudwatch.amazonaws.com"
}
diff --git a/modules/eks-container-insights/values.yaml b/modules/eks-container-insights/values.yaml
deleted file mode 100644
index d6a22ae9..00000000
--- a/modules/eks-container-insights/values.yaml
+++ /dev/null
@@ -1,20 +0,0 @@
-
-awsRegion: ${aws_region}
-clusterName: ${cluster_name}
-
-
-adotCollector:
- daemonSet:
- serviceAccount:
- create: false
- name: ${service_account}
- createNamespace: false
- extensions:
- sigv4auth:
- region: ${aws_region}
- service:
- metrics:
- receivers: ${service_receivers}
- exporters: ${service_exporters}
- sidecar:
- regionS3: ${aws_region}
diff --git a/modules/eks-container-insights/variables.tf b/modules/eks-container-insights/variables.tf
index 039a7bd5..94c85b0c 100644
--- a/modules/eks-container-insights/variables.tf
+++ b/modules/eks-container-insights/variables.tf
@@ -1,42 +1,49 @@
-variable "helm_config" {
- description = "Helm provider config for adot-exporter-for-eks-on-ec2"
- type = any
- default = {}
+variable "eks_cluster_id" {
+ description = "Name of the EKS cluster"
+ default = "eks-cw"
+ type = string
}
-variable "manage_via_gitops" {
+variable "enable_amazon_eks_cw_observability" {
+ description = "Enable Amazon EKS CloudWatch Observability add-on"
type = bool
- description = "Determines if the add-on should be managed via GitOps."
- default = false
+ default = true
}
-variable "service_receivers" {
- type = string
- description = "receiver for adot-ci setup"
- default = "awscontainerinsightreceiver"
+variable "addon_config" {
+ description = "Amazon EKS Managed CloudWatch Observability Add-on config"
+ type = any
+ default = {}
}
-variable "service_exporters" {
+variable "kubernetes_version" {
+ description = "Kubernetes version"
type = string
- description = "exporter for adot-ci setup"
- default = "awsemf"
+ default = "1.28"
}
-variable "irsa_policies" {
- description = "Additional IAM policies for a IAM role for service accounts"
- type = list(string)
- default = []
+variable "most_recent" {
+ description = "Determines if the most recent or default version of the addon should be returned."
+ type = bool
+ default = false
}
-variable "eks_cluster_id" {
- description = "EKS Cluster Id"
+variable "eks_oidc_provider_arn" {
+ description = "The OIDC Provider ARN of AWS EKS cluster"
type = string
+ default = ""
}
-variable "adot_otel_helm_chart_verison" {
- description = "ADOT collector helm chart version"
- type = string
- default = "0.17.0"
+variable "create_cloudwatch_observability_irsa_role" {
+ type = bool
+ default = true
+ description = "Create a Cloudwatch Observability IRSA"
+}
+
+variable "create_cloudwatch_application_signals_role" {
+ type = bool
+ default = true
+ description = "Create a Cloudwatch Application Signals service-linked role"
}
variable "tags" {
@@ -44,15 +51,3 @@ variable "tags" {
type = map(string)
default = {}
}
-
-variable "irsa_iam_role_path" {
- description = "IAM role path for IRSA roles"
- type = string
- default = "/"
-}
-
-variable "irsa_iam_permissions_boundary" {
- description = "IAM permissions boundary for IRSA roles"
- type = string
- default = null
-}
diff --git a/modules/eks-container-insights/versions.tf b/modules/eks-container-insights/versions.tf
index ea7a421f..e426124f 100644
--- a/modules/eks-container-insights/versions.tf
+++ b/modules/eks-container-insights/versions.tf
@@ -6,17 +6,5 @@ terraform {
source = "hashicorp/aws"
version = ">= 5.0.0"
}
- kubernetes = {
- source = "hashicorp/kubernetes"
- version = ">= 2.10"
- }
- kubectl = {
- source = "alekc/kubectl"
- version = ">= 2.0.3"
- }
- helm = {
- source = "hashicorp/helm"
- version = ">= 2.4.1"
- }
}
}